Magnified Losses, Amplified Need for Cyber-attack Preparedness
- 2014 ANNUAL SECURITY ROUNDUP
- 2014, THE WORST IN YEARS
- THE THREATS WE LIVE WITH
- THE COST OF COMPLACENCY
- DOWNLOAD PDF
2014, THE WORST IN YEARS
2014 was the year of mega breaches, hard-to-patch vulnerabilities, and thriving cybercriminal underground economies. It encapsulated threats of grand proportions, the consequences of which set companies back billions in losses and consumers an unknown figure in lost or stolen personally identifiable information (PII).
It was in 2014 when the world witnessed the largest reported hack that led to a staggering loss of around 100 terabytes of data and up to $100M damages for Sony Pictures Entertainment Inc. (SPE). “Unprecedented in nature” and “an unparalleled and well planned crime” were but a few phrases that described the Sony Pictures breach in an internal memo released to its employees. The incident spanned weeks of news coverage and gave birth to more stories. News updates appeared to be scenes from a movie, what with stories of Sony canceling the release of “The Interview” movie and employees filing a class action lawsuit against the company. These, in fact, formed the details of what has become a full spectrum of losses and business impact of a security breach.
The Sony Pictures breach is not only a case study for business but also one for IT professionals. It revealed the importance of detecting intruders inside networks. The malware used in the breach, WIPALL, is not highly sophisticated and the attack could have been detected by a healthy knowledge of the network and its probable anomalies. This reminds IT professionals of the crucial role that a layered, customized defense plays inside very large networks.
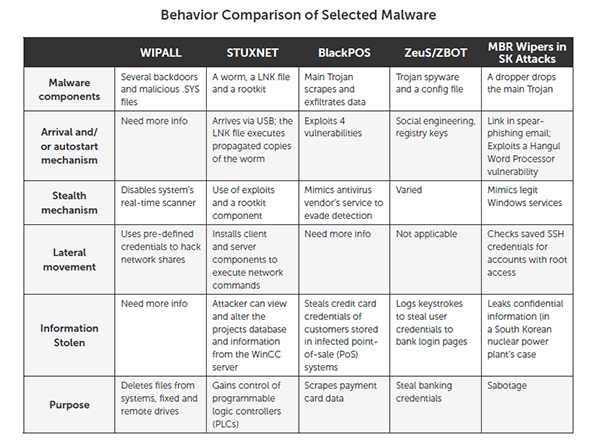
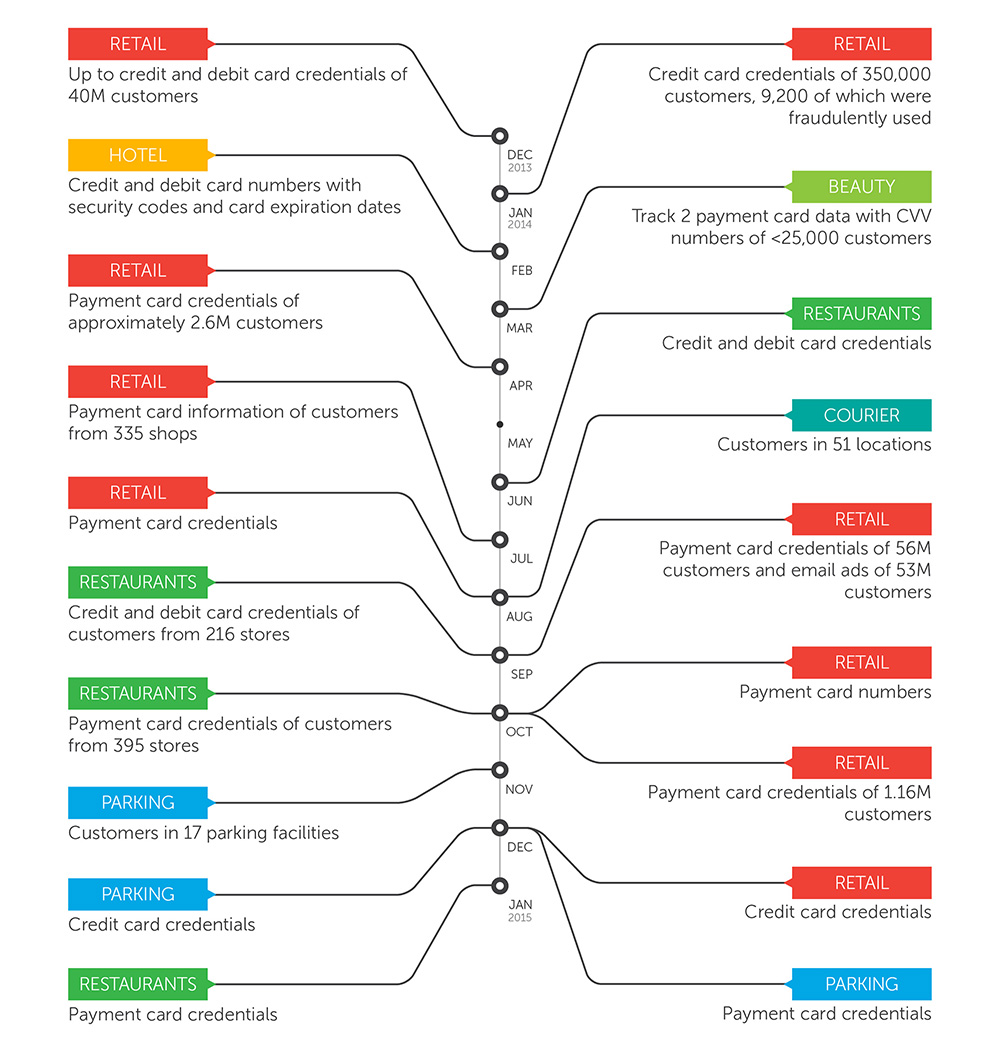
Looking back, let’s not forget how 2014 also started with the loose ends of the Target data breach in 2013 that affected more than 100 million customers. The Target breach marked the onset of a disturbing pattern in malware use that made 2014 known as the “Year of Point of Sale (PoS) malware.”
PoS breaches are close to becoming a mainstream threat, with reports of security incidents coming in at least once a month. PoS attacks flourish because of an ongoing demand for stolen credit card data in cybercriminal underground markets. New variants of PoS malware like Alina emerged as direct evolutions of older PoS RAM scraper families like Backoff. These new variants were used in attacks against the retail, shipment, travel, and transportation industries.
Timeline of PoS RAM Scraping incidents and their damage in 2014
For companies targeted by PoS-related threats, the consequences can be significant. Even before the Sony Pictures breach and thus excluding its losses, the Ponemon Institute has revealed that the cost of a data breach was already on the rise in mid-2014. The average cost paid for each lost or stolen record containing sensitive and confidential information increased more than nine percent (9%) from $136 in 2013 to $145 in 2014.
It’s not just retailers that were in trouble, though. A number of PoS-related incidents in 2014 revealed how those responsible for them have moved into targets outside of their usual shopping malls or retail shops and into airports, metro stations, and even parking lots.
It doesn’t help much that many high-profile breaches are aided and abetted by SQL Injection, cross site scripting (XSS), broken authentication, and other prevailing vulnerabilities in web applications. A majority of digital users are still vulnerable to cybercriminal attacks that abuse flaws in popular software. Nineteen critical vulnerabilities of widely-used software such as Internet Explorer, Adobe Acrobat/ Reader, Adobe Flash, and Java were found and reported in 2014.
Note that a number of diverse and hard-to-patch vulnerabilities also emerged in 2014. Newsworthy flaws like Heartbleed, Shellshock, and Poodle put users of open source software and platforms that were previously regarded as safe at risk of widespread attacks.
“Open source software is said to be inherently more secure, as it goes through more reviewers (and thus, more opportunities for any vulnerabilities to be spotted). However, that is not necessarily the case, as OpenSSL and Bash showed,” explained Pawan Kinger, director of Trend Micro Deep Security Labs.
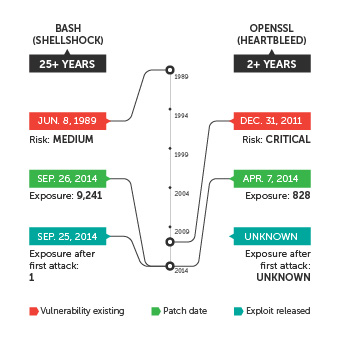 Comparison of windows of exposure of high-profile vulnerabilities disclosed in 2014
Comparison of windows of exposure of high-profile vulnerabilities disclosed in 2014
Vulnerabilities in the mobile platform have been a cause for concern as well. Last year, researchers uncovered the FakeID flaw, a vulnerability that could allow malicious apps to impersonate legitimate ones, that affected roughly 82% of Android users at the time. Similarly, all but the Android 4.4 (KitKat) version suffered a wide-reaching flaw which aids cybercriminals in bypassing Android’s Same Origin policy (SOP). This policy protects Android users from cross-site scripting (UXSS) attacks, which can steal data and cookies users input in legitimate sites. The SOP vulnerability has since been exploited in attacks targeting Facebook users.
Beyond issues of the growing number of Android vulnerabilities, iOS platform users also had their own problems to deal with. The iOS Goto Fail vulnerability exposed iOS version 7 users to cybercriminals trying to eavesdrop on mobile device sessions in shared networks.
We also saw how other mobile system weaknesses put mobile banking transactions at risk. Attacks like Operation Emmental shattered the belief that two-factor authentication via SMS is enough to protect from fraud. This specific operation targeted users in Austria, Sweden, Switzerland, other European countries, and eventually Japan.
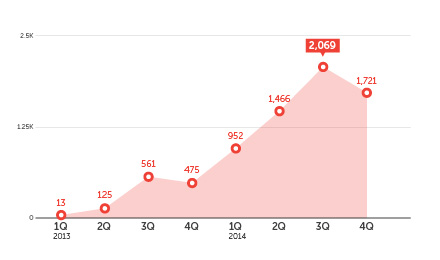 Number of Mobile Banking/Financial Malware
Number of Mobile Banking/Financial Malware
All these vulnerabilities, coupled with a cacophony of old and new malware, spam, and malicious URLs in the mix, have made it easier for cybercriminals to break into the digital lives of global Internet users. The bad guys continue to figure out what users are likely to be doing using social contexts. Increased activity during the holiday season alone sparked interesting social engineering lures, which led to a rather disturbing discovery: crypto-ransomware strains are still here, they’re spreading to more regions, and a lot of them are actually encrypting files instead of issuing empty threats. For instance, ransomware attacks in the EMEA (Europe-Middle East-Africa) region used parcel delivery as a social engineering lure during the holidays to spread a ransomware-ridden .ZIP file. Notably, the CoinVault ransomware variant was even packaged with free decryption for one file to show victims that hostaged files can be recovered upon payment.
Ransomware, online banking malware, fake apps—all these threats all point to the existence of cybercriminal underground economies that were hungry for stolen customer or enterprise information. Thriving in different parts of the world, these underground markets are where hackers and threat actors cash in on their malicious online campaigns and activities. It's a virtual cybercriminal hangout on the Internet where the bad guys converge to sell and buy different products and services.
In 2014, we saw the evolution of prices in global markets for stolen personal data. We observed how the prices range across markets as well. For instance, online account credentials in Brazil can go for as low as $50 while China offers up to $1,627.
Each underground market also offers its own specialization and standout services that are unique to them. The Brazilian underground is the most popular source of tools for bank fraud, phishing pages, and other fraud-related products and services. It even offers training services to wannabe cybercriminals. The Russian underground is known for pay-per-install services that drive traffic to malicious sites. Meanwhile, the Chinese underground Sells DDoS attack services, compromised hosts/botnets, and other products and services as well as mobile attack tools (SMS spamming software, SMS servers, and others).
THE THREATS WE LIVE WITH
We are witnesses to the dire consequences of failing to secure our digital information. It costs everyone money, time, and various other inconveniences. Familiarize yourself with the threats we live with today and know that awareness is the first step to protection.
The Trend Micro Smart Protection Network™ blocked a total of 65, 058, 972, 693 or over 65 billion threats in 2014.
Of these threats, the top three malware families were SALITY (96K), DOWNAD (80K), and GAMARUE (67K). SALITY is a known family of file infectors; DOWNAD, a family of worm malware that can exploit vulnerabilities and modify registry entries; and GAMARUE, a family with variants usually dropped by other malware.
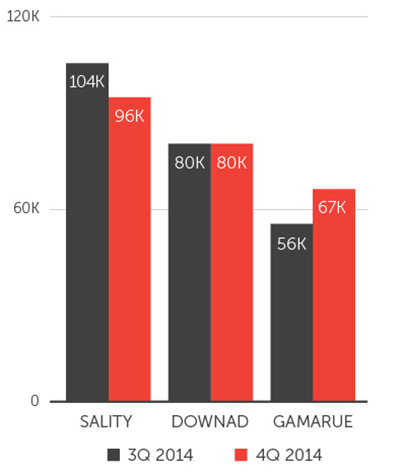 Three malware families in 3Q and 4Q 2014
Three malware families in 3Q and 4Q 2014
There are now a total of 4,258,825 or roughly 4.3 million Android malware, roughly triple the total Android malware count in 2013 (1.3 million).
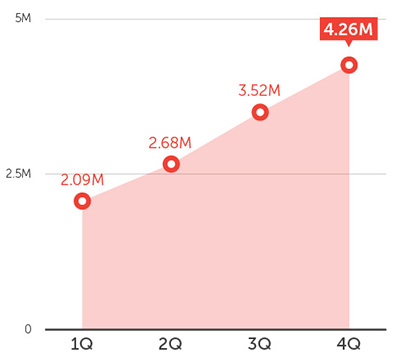 Cumulative number of Android malware per quarter
Cumulative number of Android malware per quarter
The number of iOS malware increased by 80% compared to 2013.
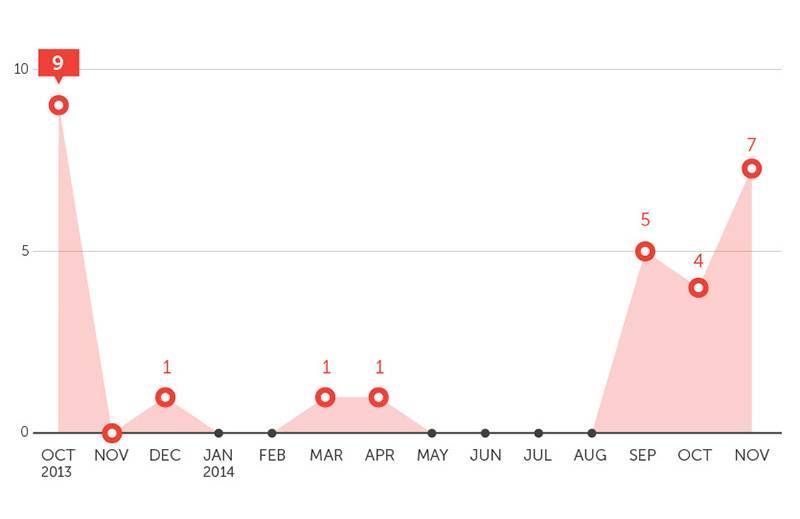 iOS malware sample count
iOS malware sample count
THE COST OF COMPLACENCY
2014 displayed worst-case scenarios because of failures in securing digitized information. Some global systems have been found to rely on a precarious foundation made of flawed software, unsafe digital habits, and lacking anti-cybercrime initiatives.
Consumers remain unperturbed. Despite exposure to news of retail breaches, consumer attitude towards security has barely changed. In an RSA survey designed to check the consumer attitude towards online shopping and mobile security, almost half (45%) revealed no change in their behavior when using credit and debit cards despite knowledge of retail breaches. Roughly 7 in 10 respondents admit to using the same password for more than one device or website.
“People may think that financial information is the most valuable information that can be lost, but that’s not always the case, says Trend Micro Chief Technology Officer (CTO) Raimund Genes, “In some ways, in fact, your personal information getting leaked is more dangerous. I can change my credit card easily, but unless I move I can’t change my address. Neither can I change my birthday. Personally identifiable information does not only identify the user, it is also frequently difficult, if not impossible, to change.”
Meanwhile, the enterprises, government agencies, and other organizations that handle large amounts of data are broad targets for attackers. Given that the cost of data breach is on the rise, companies should take the opportunity to vastly improve on their digital security.
Six months into the year, a multinational professional services provider tapped into 500 US executives, security experts, and others from the public and private sectors to find out their “cybersecurity practices and state of risk and readiness to combat evolving cyber threats and threat agents.”
The study confirmed an inconvenient truth not many executives acknowledge, that “as cybersecurity incidents multiply in frequency and cost, the cybersecurity programs of US organizations do not rival the persistence and technological prowess of their cyber adversaries.”
But, what should enterprises be doing?
“There is no one-size-fits-all solution against targeted attacks; enterprises need to arm themselves with protection that can provide sensors where needed, as well as IT personnel equipped enough to recognize anomalies within the network and to act accordingly,” says Trend Micro Director for Cyber Safety Ziv Chang.
[Read: 7 Places to Check for Signs of a Targeted Attack in Your Network]
Market forces are on the move as a result of the past year’s large-scale effects. In the U.S., reforms that would transfer the cost of liability during breaches from financial institutions to merchants are already in progress. New measures like the new the new Europay, Mastercard and Visa (EMV) standards and the PCI DSS v3.0 compliance standards are also expected to upgrade online payment systems and environments to protect them from PoS-related attacks.
In addition, repercussions of these breaches directly influence how lawmakers and customers react to businesses. Because of breaches, customers of banks and other financial institutions are said to be less loyal than before. Now that two-factor authentication is at risk, demand is increasing for banks to take additional security measures.
“Taking into consideration the evolving threat, banks should increase their verification processes for online or mobile users, and implement DMARC (domain-based message authentication, reporting and conformance,” says Tom Kellerman, Trend Micro Vice President for Cyber Security.
In addition, the Android OS fragmentation problem continues to cause delays in providing patches to mobile devices, further elongating the window of exposure for a majority of Android users.
All these discussions around digital security in 2014 have shown how bad it can get, from multinational companies like Sony Pictures to small retailers or industries. No matter the size of the data you hold, as long as it lies unprotected, it can be a cybercriminal target. The danger is real and it’s about time that companies step up.
Given how global systems involve a pool of dangerously complacent stakeholders, attacks are feared to grow even more sophisticated. That’s not to say that cybercriminals will not use old threats in their attacks, as we have seen them do in the Sony breach using the not-so-complex WIPALL malware. These days, gambling on security is not a valid option for both consumers and enterprises. Given the costs, simply being complacent isn't that different from being reckless.
Government and private sectors are already moving to enhance cybersecurity measures. Note, however, that there is no single silver bullet for blocking threats and promoting security. A custom and layered defense system that proactively understands threats to specific targets is still a consumers’ and businesses’ best way to ensure safety and security.TrendLabs 2014 Annual Security Roundup: Substantive financial losses and irreparable reputation damage as a result of losing massive amounts of confidential data to attackers ran rampant throughout 2014. The severity of the attacks and their effects revealed one thing—the risk of becoming the next cyber-attack victim has gone higher.
The 2014 security landscape appeared to be one of the toughest in terms of severity and impact. A custom and layered defense system that proactively understands threats to specific targets is still a consumers’ and businesses’ best way to ensure safety and security.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines


 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One