The New Year Security Checklist: Security Resolutions for 2015
 2014 was a year of technological highs and lows. It was this year that brought users a number of newly released mobile devices, when students started learning code at an early age, and a year that introduced a sweeping trend of wearables and other IoE devices to the general public.
2014 was a year of technological highs and lows. It was this year that brought users a number of newly released mobile devices, when students started learning code at an early age, and a year that introduced a sweeping trend of wearables and other IoE devices to the general public.
Yet it was also in 2014 when support ended for many Windows XP users; when the JP Morgan, Kmart, Dairy Queen, and other high-profile breaches affected billions of users; when the iCloud hack leaked sensitive photos of celebrities; and when the hack of Sony Pictures caused devastating consequences for the company.
2014 was a year rich with security stories that gives users a lot to think about. It's about time for users to learn from the costs of the past year’s security lapses and gear up for a safer and more secure digital life in 2015.
Check Your Online Privacy
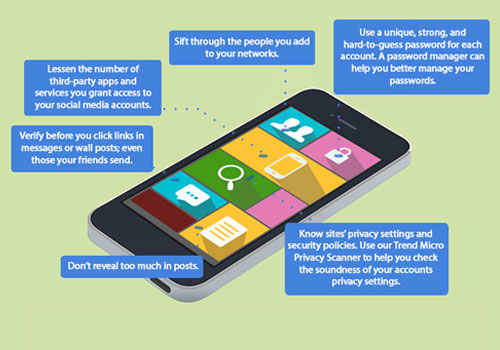
This past year, online users were exposed to privacy risks from popular online platforms such as social media and mobile apps. For a safer 2015, one of the first steps you should do is to check your social account settings and ensure that you limit the amount of personal information you share, and who you share it with.
An average person manages at least three social media accounts, the most prominent one being Facebook. Be familiar with the privacy and data use settings of each account and be updated with the latest changes in their data policies. Tweak them accordingly until you’re comfortable with whom you share which posts or updates. You can also use a privacy scanner to automatically check accounts for possible privacy issues.
[Read: Facebook Users Should Not Take Threats Lightly]
Patch and Update All Your Software
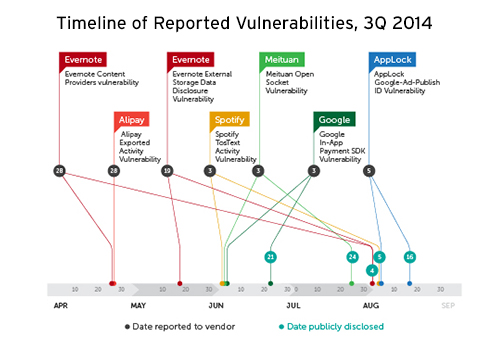
By the third quarter of 2014, we have already seen multiple vulnerabilities that affect desktop computers, mobile devices, and servers. Protect your devices and optimize your computing experience this coming 2015 by making it a habit to always update and patch your software. Remember to automate patches for all your software and uninstall those that are rarely being used to minimize the risks of exploits.
Guard Your Mobile Devices

Mobile vulnerabilities were also highlighted in 2014 with the emergence of the iOS-affecting Masque malware and the Android FakeID vulnerability. In addition, the number of mobile malware has more than doubled in the second half of 2014, just six months after hitting the two million milestone. There are now a total of 4.37 million malicious and high risk apps out there. As a result, mobile devices need to be protected from these threats to prevent data theft or loss, especially now that mobile payments are also becoming more popular.
To do this, mobile users should check for unsafe settings that are enabled or left on by default on mobile devices. Check twice if you’re comfortable with how you share data over a wireless or Bluetooth connection, which ones are allowed to access your location, which passcodes or other security measures you use to access mobile services, and others. Install mobile security software that can instantly block harmful apps, alert you to unauthorized access, and encrypts your mobile data.
Secure Your Passwords

Despite the many ways that users can now authenticate their accounts and devices, such as biometric features, passwords are not going away anytime soon. As such, properly managing passwords is part of your duty to protect your digital life. Always use strong passwords that employ a mix of alphanumeric characters and punctuations that do not include any readily available information such as your name or birthday and that only you can decipher. Remember not to recycle passwords as this will only give cybercriminals access to multiple accounts by just figuring out your credentials for one.
To make your life easier, you can also choose to use a password manager, which require you to memorize just one master password. Moreover, opt to use two-factor authentication, if available, so as to provide another layer of security for your online accounts.
[Read: Passwords: Not Going Away Anytime Soon]
Backup Your Files

There is always that story of someone who either had their hard drive fried, their mobile device stolen, or their account locked, leading them to lose their files entirely. One way to get out of this probable mess is to regularly back up files. Remember to employ the three-two-one rule when you back up files, making sure you have the following:
- At least three copies,
- In two different formats,
- With one of those copies off-site.
Bookmark Trusted Sites

Social scams and phishing sites have not stopped in 2014 and show no signs of stopping in the near future. They mostly put online banking users and online shoppers at risk of revealing financial information in phishing sites. To fight this, users should remember to bookmark trusted online banking and shopping sites. Follow only legitimate websites that use secure protocols and offer fraud protection to stay safe from cybercriminals.
Protect Your Kids

Finally, given that cybercriminals are likely to target users who may not know enough of the dangers of online computing, kids who use the Internet may put the entire family at risk. This does not include the dangers of having kids access sites that they are not ready to process yet. Parents, teachers, and guardians would do well to limit kids’ access to the Internet via parental controls and filters. Always monitor the kids’ online activity and allot a designated time for use to ensure that they get the most out of it without being exposed to individuals that may want to cause them or their families harm.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One