Sockbot Malware Found on Google Play can Ensnare Devices to Become Part of a DDoS Botnet
 Eight applications hosted on Google Play were found infected with the Sockbot malware (detected by Trend Micro as ANDROIDOS_TAPJOY.OPD), which not only generates illicit advertising revenue for its developers but can also zombify the infected device as part of a botnet. The apps were reportedly downloaded between 600,000 and 2.6 million times, mostly by users in the U.S., followed by those in Russia, Ukraine, Brazil, and Germany.
Eight applications hosted on Google Play were found infected with the Sockbot malware (detected by Trend Micro as ANDROIDOS_TAPJOY.OPD), which not only generates illicit advertising revenue for its developers but can also zombify the infected device as part of a botnet. The apps were reportedly downloaded between 600,000 and 2.6 million times, mostly by users in the U.S., followed by those in Russia, Ukraine, Brazil, and Germany.
The apps posed as mods for the popular game Minecraft: Pocket Edition, allowing players to customize the appearance of their characters. However, the apps were found to have been surreptitiously generating ad revenue for their developer, and have since been taken down from Google Play.
[From the TrendLabs Security Intelligence Blog: GhostClicker Adware is a Phantomlike Android Click Fraud]
According to the security researchers, the app will connect covertly to a command and control (C&C) server on port 9001, which will request the app to open a socket via the Socket Secure (SOCKS) protocol. It will then connect to the IP address and port specified by the C&C server. After a connection is established, the app connects to another developer-specified server that issues a list of ads and related metadata (i.e., advertisement type, screen size name). Using the SOCKS proxy, the app will connect to an ad server and launch ad requests.
The researchers note that Sockbot’s mechanisms can be expanded to exploit network-based vulnerabilities. And with Sockbot’s hijacking capability, the infected devices can be used to launch distributed denial of service (DDoS) attacks.
[READ: Xavier: An Information-Stealing Ad Library on Android]
Sockbot’s code and key strings were obfuscated and encrypted, making it more challenging to detect. They attributed the apps to a developer going by handle FunBaster, who was said to have signed each app with different developer keys to bypass static analysis.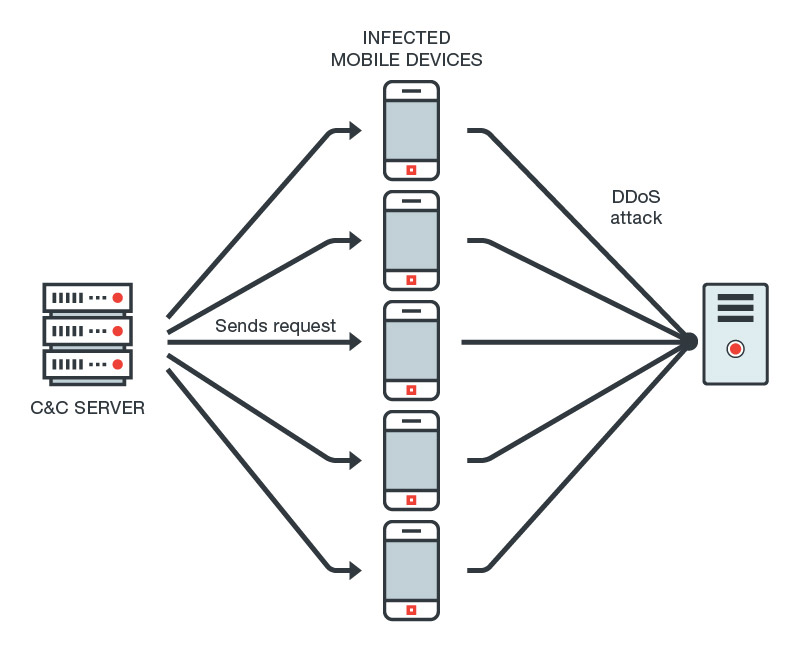
How large botnets can launch DDoS attacks via compromised devices, as exemplified by the DressCode Android malware
[READ: Android Mobile Ransomware: Bigger, Badder, Better?]
Socksbot is not the first to misuse the SOCKS protocol or make use of Android apps to generate illegitimate revenue. DressCode, a malware that emerged last September 2016, used the SOCKS proxy to access the internal, corporate networks to which compromised mobile devices connected. MilkyDoor took this up a notch in April 2017 by also abusing the SOCKS protocol, setting proxies to conduct reconnaissance when accessing the vulnerable services and networks of the affected device. MilkyDoor also integrated remote port forwarding through the Secure Shell (SSH) tunnel, enabling the malware to encrypt its malicious traffic and payloads.
At least 3,000 apps were Trojanized with DressCode, 400 of which were found on Google Play. 200 MilkyDoor-infected Android apps were also found, one of which had between 500,000 and a million Google Play downloads. Like Socksbot, both DressCode and MilkyDoor masqueraded as recreational apps—games, mods and skins, themes, phone optimization boosters, Doodle, style guides and e-books to children. They can be surmised as legitimate apps that were repackaged, Trojanized, then republished in Google Play.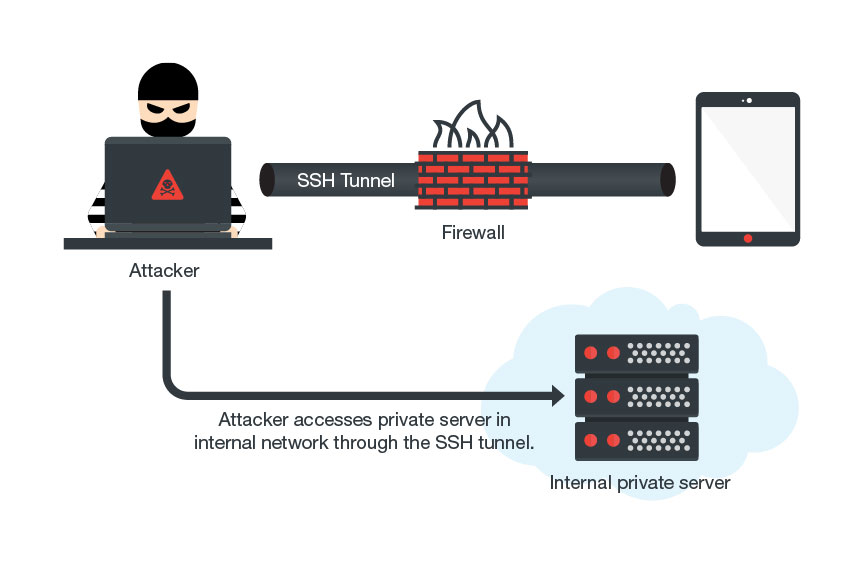
MilkyDoor’s attack chain also entails bypassing firewalls
Indeed, ensuring mobile safety is crucial given the significant impact of these types of malware. Organizations adopting Bring Your Own Device (BYOD) programs should balance maintaining flexibility in business operations and ensuring their privacy and security. Here are some best practices, especially for enterprises:
- Enable and deploy firewalls to help restrict internal systems from accessing uncommonly used ports—a key technique used by the SOCKS protocol-abusing Socksbot, DressCode and MilkyDoor
- Enforce the principle of least privilege to deter hackers from accessing internal networks
- Create stronger patch management policies
- Keep the OS and its applications patched; Android patches are fragmented so users should contact their vendor/manufacturer for their availability
- Avoid using unsecure connections; use Virtual Private Network (VPN) when remotely accessing corporate networks and assets
Trend Micro Solutions
End users and enterprises can also benefit from multilayered mobile security solutions such as Trend Micro™ Mobile Security for Android™ which is also available on Google Play. Trend Micro™ Mobile Security for Enterprise provides device, compliance and application management, data protection, and configuration provisioning, as well as protects devices from attacks that leverage vulnerabilities, preventing unauthorized access to apps, as well as detecting and blocking malware and fraudulent websites. Trend Micro’s Mobile App Reputation Service (MARS) covers Android and iOS threats using leading sandbox and machine learning technologies. It can protect users against malware, zero-day and known exploits, privacy leaks, and application vulnerability.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- The State of Criminal AI: Market Consolidation and Operational Reality
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One