Poisoned Apples: A Look Into The Recent Threats That Affected iOS Users
Apple recently rolled out iOS 8 to coincide with the launch of the newest iPhone models. Alongside this, the tech giant announced the soon-to-be launched Apple watch that excited its loyal consumer base. The amount of global buzz that the announcements generated created only affirms the popularity of the brand in the mobile arena.
While the product updates merited a huge amount of global attention, Apple still trails behind Android in its OS market share. In a report, Android dominated with a 78.9 percent share of the mobile OS market, while iOS reached 15.5 percent by the end of 2013, plummeting from its 19.4 percent reach the previous year.
The huge discrepancy supports the idea that in terms of security, Android users are more exposed to cybercriminal tactics. However, iOS users should not be lulled into a false sense of security.
While iOS users may not be as exposed to malicious apps, this does not mean that it is an impenetrable system. Beyond malware, risks and threats abound that can affect mobile experience. Such is the case with events we have recorded.
A Lot Like Phishing
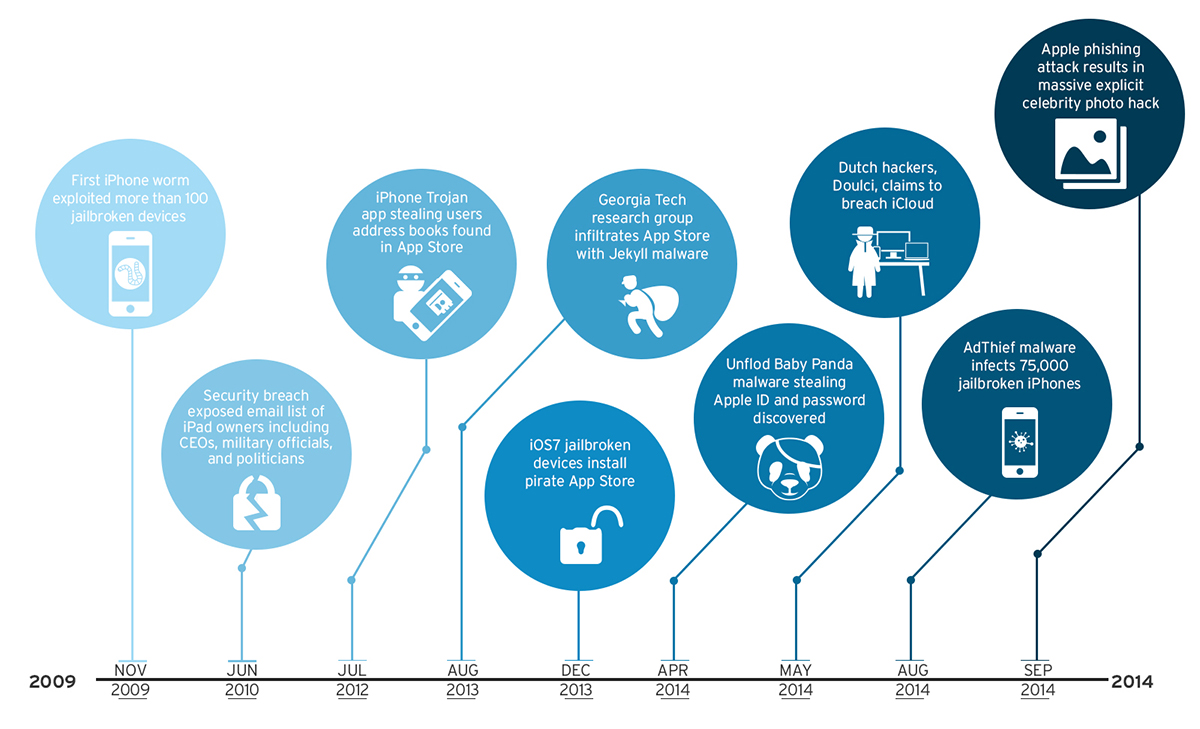
Early this September, social media was awash with news of a celebrity photo hack that resulted in the spread of explicit images of Hollywood celebrities. The culprit stated in an official Apple statement, was yet another phishing attack.
Mobile phishing has become a viable option explored by cybercriminals as they take advantage of certain limitations of the mobile platform. Spoofed versions of legitimate sites are used to bait users into divulging sensitive information like usernames, passwords, and other account details. For example, the small screen size of the device limits the mobile browser from fully displaying any anti-phishing security elements a website has. The preinstalled default browsers that automatically start up and display links also gives cybercriminals one browser to exploit instead of many. We observed that the number of mobile phishing URLs have increased this year, from 311 in July to 1,927 by the end of August.
Cybercriminals go to unbelievable lengths to gain access to vulnerable accounts. In this case, they employed standard fishing techniques to guess usernames, passwords, and answers to security questions.
Apple firmly denied that the incident stemmed from a systematic flaw of its security systems or cloud services. It stated that while accounts may have been accessed, "none of the cases resulted from any breach in any Apple systems, including iCloud or Find my iPhone." A recent investigation also revealed that "certain celebrity accounts were compromised by a very targeted attack on user names passwords, and security questions."
Trend Micro Vice President of Security Research Rik Ferguson was quoted saying that "a wide scale hack of iCloud is unlikely. Even the original poster is not claiming that." The simpler and more likely explanation can be attributed to guesswork, or authentic-looking sites that baited users into entering login credentials that were later used against them. Apple ID phishing has significantly grown from where it was when first observed. In August, Apple phishing URLs reached 26,363—a huge difference from the 1,821 seen in July. This rapid increase only signifies that it will not be the last.
Talk
While aggressively denying the idea of a wide-scale breach, it can be remembered that last May "Doulci," a Dutch team of hackers, hogged headlines with claims of being the first group ever to hack the Apple iCloud system.
De Telegraaf, a Dutch news organization, reported that the hackers enabled the hack by first purchasing locked—presumably stolen—iPhones for $50 to $150, andunlocked them by using apps on the phones to make it look like they were "communicating with actual Apple server"— the one that Apple uses to activate devices. Unlocked devices were then sold for a large profit later on. A tweet linked to the hackers said that they "processed" more than 5,700 devices within five minutes.
Reportedly, the hack was done to warn users of the security lapses on their devices and their cloud storage service. The hack was said to have been in the works for five months and was reported to Apple on March of this year, but they kept mum about the issue, prompting the hackers to go to the Dutch media to talk about the supposed server breach.
Breaking Free From Restrictions
Undoubtedly, there has been a long history of attempts to challenge Apple security measures. Cyber crooks continue to push the limits of company security, from fingerprint sensor hacks to simply trying to penetrate each version of the iOS.
In February of 2013, a popular jailbreak software called Evasion was released. Its perpetrators? Its own users. Jailbreaking is the act of modifying a device to allow it to run unsigned, and thus unauthorized, code. With Evasion, close to seven million iPhone, iPad, and iPod touch owners cracked Apple restrictions to give them the liberty to download apps and tools outside the official App Store. Aside from this, users can customize settings in ways that iOS did not allow.
A jailbroken device has the ability to download applications from alternative app stores that did not go through the regular app review process. This then means that such applications can possess and exhibit malicious behaviors. Evad3rs, the hackers behind the elaborate jailbreak, has taken advantage of unpatched bugs to take down the built-in defenses that prevented modifications to its operating system.
Jailbreaking a device could be considered similar to opening up your device to malware. Last March of this year, an iOS-based malware strain was found and said to have infected over 75,000 jailbroken iPhones. Known as AdThief, the malware has the capability to hijack major ad publication platforms on an iOS device. It made use of pop-ups to gain access to a user phone. Before this, a malware called Unflod Baby Panda, detected as IOS_UNFLOD.A, was discovered on several jailbroken devices responsible for sending Apple IDs and passwords to servers based in China. Back in 2009, jailbroken devices were also targeted by what was claimed to be the first iOS worm. Detected as IOS_IKEE.A, it affected users by replacing device passwords, resulting in the inability to gain access. It also gathers information such as device name, version, and network interface information, and transmits it to a command and control (C&C) server.
iOS 8 features updated photo editing tools, time-lapse videos, sounds and location features in its messaging apps, and an Interactive Notifications tool. Advanced users will want to explore the possibilities with the new operating system, and a new method for jailbreaking this iOS version is expected to surface soon.
Keeping Your Apple Poison-Free
Such events should serve as a reminder for Apple users to be vigilant. Here's how to improve iOS device security:
- Protect your account. Login credentials like your Apple IDs and passwords are still the lowest hanging fruit for cybercriminals to exploit. Choose strong passwords that are hard to decipher, ideally not connected to any biographical detail.
- Know your Apple. Take advantage of built-in security features found in your device (like password locks, Find my iPhone etc.). The two-factor identification option on iCloud is also an effective security feature.
- Study your apps. Never be too trusting of the apps you install on your device. Read up and familiarize yourself with security settings and the permissions that the apps asks for.
- Do not jailbreak. For a consumer, free choice is always a good idea. But there is a reason why iOS strictly regulates the data and apps that you allow. Jailbreaking your device opens it up to malicious elements.
- Install a trustworthy security solution. It is always better to be safe than sorry. Invest in a security solution that can protect your devices from elements that can harm your mobile experience.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One