What to Consider When Buying a Smart Device

Security Considerations for Consumers Buying Smart Home Devices
Geoff Grindrod, Katie Wen
Contents
Based on our continuing analyses of smart devices, we felt it would be a good idea to lay down some security ideals for consumers who are considering purchasing smart devices.
We feel it’s important for consumers like you to be able to identify and understand the criteria we’ll be discussing. Additionally, we feel that smart device vendors should pay closer attention to the default security of the devices they’re producing.
More: See how the Internet of Everything makes life a lot easier
The Scope
We’ve decided to cover the security-specific ideals or criteria for choosing smart devices that we consumers will most likely see at home now or in the near future. We’ve also focused on smart devices available in the US.Note that security-specific ideals are only one of the many things smart device buyers need to consider. A more comprehensive set of buyer’s considerations might take into account the overall daily or weekly time and effort the household’s designated “Administrator of Things” (AoT) spends on not only securing devices, but also performing other tasks to ensure these devices continue to function. Some of these tasks may include updating firmware, identifying dead devices, re-connecting and attaching devices, replacing batteries, checking connections, diagnosing technical issues, reconfiguring access, updating apps that control devices, and so forth. This set of tasks are not for the faint of heart.
For this guide, the term “smart devices” refers to the following:
- Consumer devices that aren’t traditionally considered in a security model; this is why we won’t talk about PCs, tablets, or smartphones
- Devices that have significant enough computing capabilities to allow them to operate autonomously and flexibly, and to communicate either directly or indirectly with the Internet as part of their normal operation
- Devices that are primarily intended for use in the home, as opposed to other types of less home-centric consumer smart devices, like wearables or smart cars. Some examples of smart devices for the home are: appliances (ex. smart washers, smart fridges), audiovisual equipment (ex. smart TVs, AV receivers, gaming consoles, smart speakers), security and conservation devices (ex. smart hubs and sensors), energy meters, and so forth.
Here are some security criteria that you, as a consumer, should consider when selecting a smart device for the home.
The Criteria
Username/Password Considerations

Ask Yourself: Does the smart device provide authentication?
Does the smart device, for example, require a username or password for access? Many smart devices have no means of providing authentication. A well-designed smart device will have some type of authentication capability that will let you, as the owner, properly control access to it.
Several smart device manufacturers have chosen not to provide any authentication on their products and rely instead on other means. Some manufacturers even assume that your local WiFi network should be able to provide this security. Unfortunately, this leaves smart devices significantly more susceptible to attacks, since anyone who has access to the local WiFi network can intercept, monitor, or attack devices with greater ease.
Ask Yourself: During initial installation, does the smart device require me to change my username and password?
During the initial setup, a well-designed smart device will require you to change its default access credentials. Changing the default credentials prevents an attacker from accessing your device using published default username and password combinations.
When first installing a smart device for your home, you usually need to connect it to the Internet to ensure it operates normally. This includes checking its primary and administrative functions, like firmware updates. Unfortunately, during the device’s initial setup (or even when the device is reset), the default access credentials assigned to the device are very weak. It’s common to see smart devices with a username set to “admin” and with a default blank password. In other instances, the usernames are identical to the passwords.
More: Password (In)security: How to improve security with stronger passwords
The Shodan search engine, a massive index of currently Internet-connected smart devices, reveals just how big a threat this default password problem is. By using this search engine to view connected devices, you can quickly see the prevalence of this existing security issue. Just last year, Foscam, a company specializing in IP cameras, realized that their device’s default credentials exposed their customers to potential eavesdropping. Since then, there have been several highly publicized incidents of eavesdropping exploiting this vulnerability. Though Foscam has already reported fixing the issue, the key challenge for them is getting all of their customers to apply the fix. There are still plenty of other device manufacturers who still use default credentials.
Once a device is initially deployed and operating—barring any technical issues—it’s highly likely that it won’t be reconfigured for some time. With the default weak credentials, coupled with a lack of password change enforcement during initial setup, it’s easy to understand how vulnerable these devices can be. This is why it’s critical to firm up the device access credentials at the time of initial deployment.
To understand how the device you’re considering may be affected by this problem, try the following:
- Note the default access credentials for the device you’re considering buying. Look at sites that maintain lists of usernames and passwords for specific classes of smart devices. For example, IPVM maintains a list of default credentials for specifically IP cameras.
- Go to the device manufacturer’s website and then check the device user manual to determine the default username and password.
- Google the search terms “default password for [device and="" brand="" model=""]” or “password reset [device and="" brand="" model=""]”
Ask Yourself: How strong is my password?
Make sure your password isn’t easy to guess. Good passwords should have a complex combination of alphanumeric characters (letters, numbers, punctuation marks, mathematical symbols and the like). They should be at least 8 characters in length, and should use both upper and lower case characters. Additionally, avoid reusing passwords over time, or using the same password across other devices.
Updateability

Ask Yourself: How well does the smart device keep itself updated?
Is the device able to automatically update itself? Does your device notify you that it’s out of date? How complicated is the process of updating the device? Device updates keep your smart devices functioning properly and securely, but the way you receive these updates can be a challenge. Updating a device is currently both the responsibility of device manufacturers and consumers. You have to consider how the update process will affect you, including the complexity and the time it takes to do the update.
When manufacturers produce smart devices, they’ll typically include the ability to update the device’s firmware—the OS and data that allows the device to operate.
Historically, most smart devices are equipped to let consumers manually update or patch their devices. However, it can be a great challenge for an average person to actually remember how to find the smart device on their network, use a browser and host address, or use the update feature itself. As a result, a common problem is that once a smart device is initially set up, its firmware may not be updated for a significant period of time. It’s just not convenient.
Additionally, even in cases where the device is fully updated at the time of initial setup, it’s also common for manufacturers to release new device updates without properly informing the consumers. This results in your device being out-of-date.
Considering that the use of smart devices in the household rapidly becomes a norm, the need to keep these devices always updated gets more important. Consumers like you need to ask if this process of manually applying updates to your devices is something that you do for each and every smart device in your household. This could be a challenge, and potentially even the greatest cybersecurity risk affecting the home in the future.
Smart device vendors can mitigate this device management problem by:
- Making updates more automatic
To mitigate the impact of a smart device firmware update, many vendors only implement a manual update process. This is understandable since a bad update that affects the device could make them lose customers. But perhaps a more granular approach could be used? One method is assigning different classifications to firmware updates. These classifications indicate how much each update can negatively affect a device if something goes wrong.
In the past year, we’ve seen several vendors fail to streamline their update process. They’re forced into a painful manual support process. To ensure their customers’ continued protection, they are obligated to directly notify all of their customers to deal with high-profile exploits. This approach is neither sustainable nor effective for the company and the consumer.
- Simplifying the user interface (UI)
Vendors can improve their update notification and user interface, to guarantee that you, the consumer, is made aware of available device updates. Improvements to the user interface can minimize the amount of time you need to spend applying the updates.
Several of the newer devices we have researched have made a step forward by doing away with the web-based interface. They now provide a singular configuration wizard interface through the smartphone or tablet. This approach appears to be more streamlined because:
- You’re more likely to have your cellphone or tablet on hand as opposed to your notebook or PC when a need to update arises
- The form-factor of a phone or tablet empowers the manufacturer to create a cleaner user interface
- A phone or tablet interface will save you from remembering how to find and access the device on your network
Encryption

Ask Yourself: Does the smart device properly encrypt its firmware updates and network communications?
Even though a smart device may advertise the use of encryption, some may not implement encryption properly or fully. Make sure to Google the device model for any possible historical security issues.
Many smart devices don’t properly implement the use of encryption when communicating across the network or protecting their periodic firmware updates. As an example, Belkin’s initial release of the WeMo baby monitor failed to use encryption when transmitting data. In another example, Belkin used an easily accessible global master key to encrypt their updates. These lapses left their devices open to monitoring, controlling, and even alterations by an attacker. Consumers could have been exposed to possible intrusions or other types of disruptions.
More: Securing the Internet of Everything against surveillance and attacks
Whatever the purpose of your device, it can be used to transmit the following unencrypted information across your home network and the Internet:
- Usernames and passwords that can be used to remotely access and control your household smart devices
- Live video or audio data that can be used to remotely glean live audio and visual data from your home and family
- Presence data that can be used to remotely discover the time(s) that you’re commonly at home—this can be taken from devices like door locks, window sensors, motion sensors, thermostat activations, light bulbs, DVRs, TVs, or Internet radios
- Vulnerability data that can be used to assess the vulnerability of smart devices within your home–this can be derived, for instance, from your smart devices’ firmware version checks, or from the firmware images themselves
- Medical data that can be used to remotely discover details about your health status–this can be taken from scales, blood pressure monitors, diabetes monitors, and the like
Additionally, if a given smart device doesn’t properly encrypt its updates, an attacker can disrupt or take control of the device by reconstructing and mimicking an update.
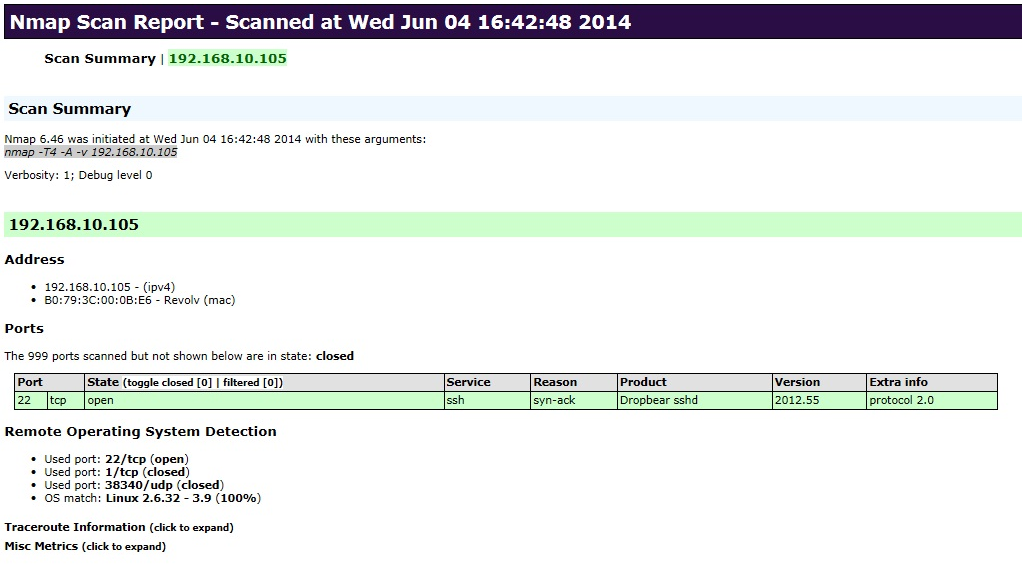
Open Ports
Ask Yourself: Does the smart device require any open ports?
Open ports increase the attack surface of a smart device. The less open ports, the better.
Think of an open port as a window or door that you've left open in your house. In the same way that it may be necessary to leave some types of entrances accessible – like a small pet door, device manufacturers need to leave some ports open to allow communication with the device as part of its normal operation. Many smart devices use open ports for commonly known service access, like Telnet and FTP, while others are for custom protocols. Since the existence of any open ports on a smart device opens up the external attack surface of the device, open ports generally increase the security risk.
In the case of a particular smart hub we looked at, we found that the Telnet port had been left open. The Telnet port used a static username and password, meaning it’s the same username/password used by other devices owned by other people. Knowing this Telnet username and password combination would allow a hacker unfettered access to all other similar devices.
More: See how new threats can take advantage of new IoE technology
To assess which ports are left open on any given smart device, you can use the popular and well-established NMAP tool. First, make sure the smart device you want to check is connected to the same network, and that you have its hostname or IP address. You’ll also need to install NMAP, if it isn’t already on your PC or notebook. Type the following NMAP command to assess the open ports on the device:
nmap [IP Address]
Power Dependency
Ask yourself: How well does my battery-powered smart device handle a low or dead battery scenario?
How aware is your smart hub that your device’s battery is running low or dead? How are you notified to change the batteries? From the notification, will you understand what needs to be done? When a smart device runs out of battery, it could stop functioning and open up consumers to physical risks.
Some types of smart devices, including peripheral devices—ones that are peripheral to a smart hub—may be dependent on batteries for their normal operation. Batteries are used to enhance the convenience of installation. They minimize the need for tedious wiring and ensure that the device can remain incognito in the home. Examples of these peripheral smart devices include security sensors on windows or drawers, smoke detectors, or smart door locks.
Though some of these battery-powered devices use efficient protocols that allow them to operate for long periods of time without draining the battery, their manufacturers have overlooked a fairly critical aspect. Due to the lack of holistic design considerations, when these peripheral devices run out of battery life, the hub, and therefore the consumer, may not be correctly informed.
Depending on its manufacturer and model, a peripheral device with a dead battery might show up as any of the following statuses on the smart hub: “forgotten state”, “device out of range”, “device open/closed”, “device [no] motion”, etc. Since this isn’t an accurate representation of the device’s actual state, the consumer is left unaware of the need to change the battery. Just imagine what would happen if a smoke detector or a smart door lock stops functioning? To an oblivious consumer dependent on these peripherals, this issue could become a physical security risk.
Vulnerabilities

Ask Yourself: How well does the manufacturer manage their device vulnerabilities?
How many published vulnerabilities does the device have? How many have the manufacturer fixed? What is the average time it takes for the vendor to respond with a fix? Vulnerabilities give malicious individuals and cybercriminals an opportunity to exploit your devices. How manufacturers and vendors resolve these issues can either save you from or expose you to further risks.
Just like with PCs, tablets, and smartphones, other types of smart devices have software vulnerabilities. We’ve already seen many published incidents of smart devices being hacked. Industry security researchers proactively identify and publish smart device vulnerabilities; some even get media coverage.
To assess the vulnerabilities of the device you are considering, you can check the commonly used CVE (Common Vulnerabilities and Exposures) database for identified vulnerabilities, along with vendor responses and other related information. Additionally, you can simply Google the manufacturer and device model to understand any potential issues relating to that device.
More: Securing the Internet of Everything
Conclusion
Security will always be a concern so long as information is involved. Having a well-chosen set of connected devices is one of the first steps users can take in keeping a secure connected environment at home. Another is to employ the Trend Micro Home Network Security solution that adds an extra layer of protection to all connected devices and helps users manage these devices from anywhere.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- The State of Criminal AI: Market Consolidation and Operational Reality
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One