It is possible to consider misconfigurations as part of the growing pains when an organization moves to the cloud during its digital transformation. Cloud misconfigurations tend to be discovered the hard way — that is, when a cyberattack or a data breach has already occurred, leaving organizations to deal with the aftermath. How do misconfigurations leave an impact on businesses and cloud security? And what can organizations do to mitigate such effects?
Misconfigurations are costly
According to a report from 2020, cloud misconfigurations cost organizations US$5 trillion from 2018 to 2019. Most of this is due to data breaches rooted from misconfigurations. Aside from breaches, misconfigurations can also cost companies in multiple ways. Several examples include idle instances (where the service does not need to be running but is still being paid for), unused storage, and overprovisioning brought about by “the data center” or “on premises” way of thinking.
From a security perspective, misconfigurations can lead to snowballing losses and cost. Breaches —exposed records, data, and infrastructure — result in fines, penalties, loss of business, customers, and more. Ultimately, these costs can add up and create a catastrophic impact on any business.
Misconfigurations heighten risks
Encrypting online storage is as easy as flipping a switch. In contrast, not flipping this switch (as it is not typically enabled by default) can result in complete exposure of stored data. A simple act can therefore prevent a complex problem. Threat actors are aware of this and are on the lookout for these overlooked security gaps. They program their scripts and bots to search for exactly this kind of opening so that when they encounter it, they can extract every bit of data that they can.
The cost of an attack depends on the data and the underlying cloud infrastructure tied to the configuration. Lateral movement within a cloud environment is something that can be done once a misconfiguration has been exploited. To give some perspective, the cost per lost or stolen record averages at US$161 with personal identifiable information (PII) averaging at US$180.
Misconfigurations can turn into vulnerabilities
A misconfiguration is mainly the responsibility of the organization and its developers, while the fix for a vulnerability primarily relies on service providers who must release a patch. Despite these fundamental differences, both misconfigurations and vulnerabilities can lead to exposure and successful attacks. An unaddressed misconfiguration, as well as a vulnerability, can become an open invitation for threat actors who are always actively searching for these kinds of opportunities.
Misconfigurations and data breaches
In our recent report, we investigated the most common cloud misconfigurations that could lead to data breaches. Some of the common ones we saw were high-severity misconfigurations, examples of which include enabled just-in-time access for virtual machines and enabled immutable blob storage.
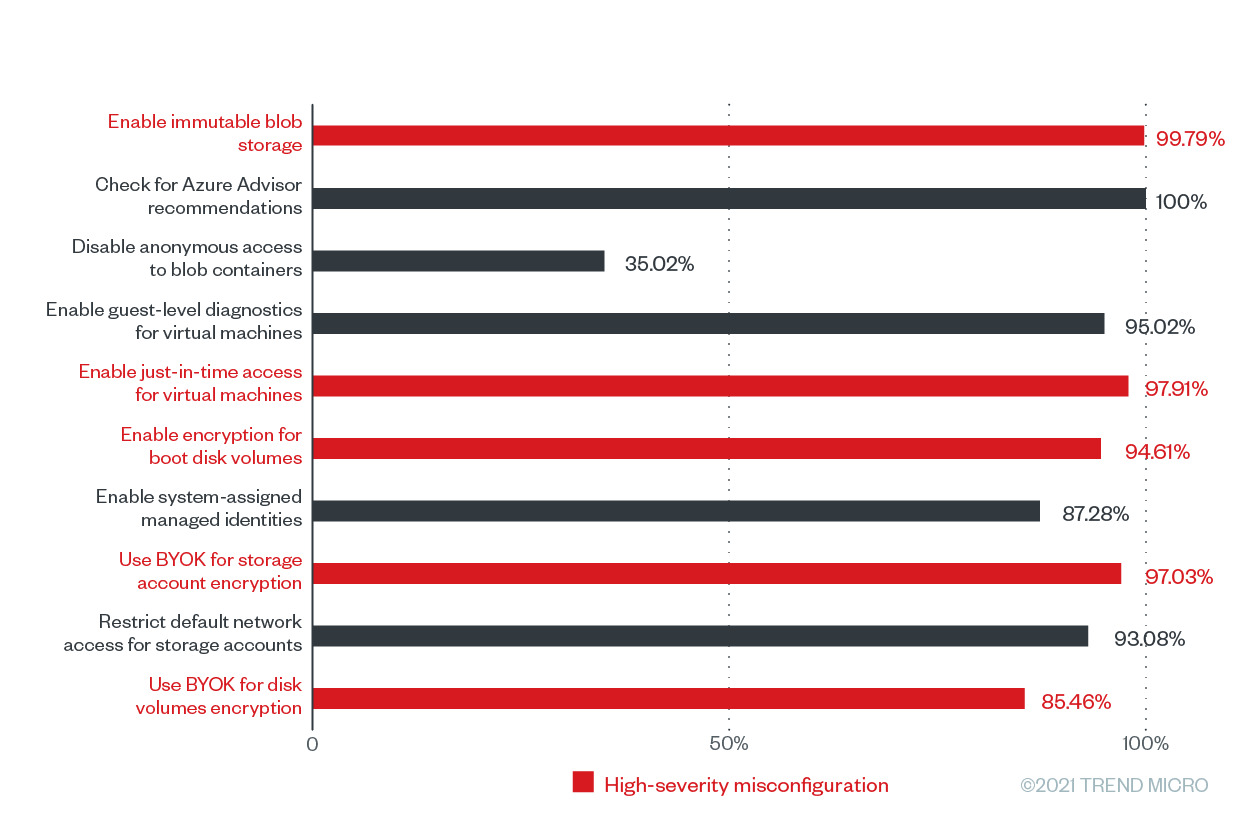
Our data also showed a high frequency of Amazon Simple Storage Service (S3) rule violations. Still, it is necessary to examine the data further before fearing for the worst. For one, not all Amazon S3 buckets are supposed to be encrypted. In some instances, encryption is not needed. These are cases where the data needs to be served in clear text such as for public sites or data that needs to be openly accessed through an application.
While encryption can be done on a case-to-case basis, data classification cannot and should be done in all instances. What are you putting into the storage container? Should it be encrypted? It is necessary to always answer these questions. Since cloud security posture management (CSPM) technologies should not have access to your data (and neither should your cloud provider), it is up to your organization to determine the encryption level of your data. It is therefore a must for organizations to review whether they do conduct such assessments, as well as if they have visibility over what is happening within their cloud.
Overall, the high-severity misconfigurations we enumerated in our report can lead to significant consequences, mostly because of their potential for data breaches. Some of the consequences of data breach include reputational damage, data privacy law violations, and operational issues.
The worst-case scenario that a data breach can have for organizations is the loss of business. Customers and businesses expect the strongest security with respect to their data and intellectual property. If any of these are violated, organizations will likely face reputational damage.
What can you do to mitigate cloud misconfigurations?
The good thing about misconfigurations is that you can do something about them. What makes attacks that stem from a misconfiguration difficult to live down is how they could have been easily avoided had the misconfiguration been noticed in the first place. Nevertheless, we still recommend learning what you can do to mitigate cloud misconfigurations.
Automating security
Automation and visibility are the number one problem we see within our customer cloud environments today. While there is indeed talent in tech to handle safely moving to the cloud, there is also a shortage of employees. DevOps teams are building at record pace and releasing applications daily or hourly, but security teams cannot always keep up. One way they can do so is to automate and augment their work. Having software-defined infrastructure (SDI), infrastructure as code (IaC), and up-to-date templates and containers assist with respect to automation and augmentation.
Automating compliance
Building compliance into the automation cycle used by the organization should be considered a baseline measure. This is an important standard set by cloud providers. With regard to the cloud, security must go beyond various global standards to include those referenced by cloud providers, in addition to best practices for an organization’s specific industry.
Upskilling the workforce
The cloud and DevOps are developing quickly. However, cybersecurity is not ingrained in students or future programmers. Programmers do not have an inherent security-driven focus when developing their work, so bugs that affect security happen constantly. IaC and SDI, as well as the integration of CSPM in the DevOps cycle, help with this challenge. In short, upskilling people can ensure security from the design phase. As the saying goes, “shifting left” is good, but “starting left” is better.
Overall, it is important to understand that the cloud is fallible. Its security is a responsibility shared by the cloud service provider (CSP) and the organization. Organizations should thus do their part and live up to their role in keeping their cloud environments secure.
This can be a daunting task, especially when organizations have had to quickly cope with the demands of a global pandemic. Still, security must be prioritized to avoid even heavier consequences and to build more confidence in cloud environments.

