Ransomware saw a downturn after peaking in 2017, but serious new threats soon replaced it. This is a review of major cybersecurity stories and issues in 2018 that created a shift in the way nations and enterprises across the world handle data, digital currency, and vulnerabilities.
<<
>>
-
Aftershocks from Meltdown and Spectre

Vulnerabilities that changed processor design
The Meltdown and Spectre vulnerabilities were described as “catastrophic” by many in the security industry, and it's obvious why, given the scope and severity of the issue. These vulnerabilities affect nearly every microprocessor manufactured in the last 20 years, and could allow for a dangerous level of unauthorized access as well as information theft. The flaw is in the features built into the chips, so solutions and fixes are difficult.
Software patches were a quick mitigating tactic against threats associated with the vulnerabilities, but not a complete fix. The real solution is rooted in the actual chip design. The next generation of microprocessors has to be redesigned to protect users from these vulnerabilities — and manufacturers have already made good progress. While initial improvements have been implemented, it's going to take a lot more to resolve the issues completely.
Meltdown and Spectre triggered a real change in the way chips are designed and continue to impact manufacturing companies. The industry has also become more aware of security issues from hardware, and has its guard up for any future threats.
-
Regulating Data Protection
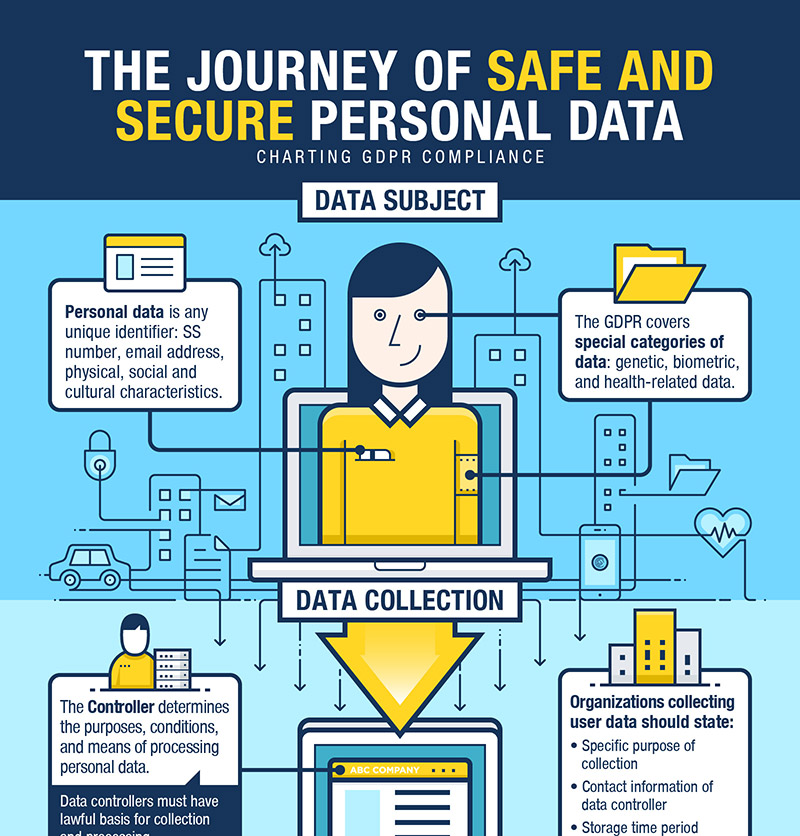
Large-scale privacy incidents changed the way companies collect and store data
This year, data protection and privacy have been topics of interest and debate for governments across the world. Large-scale incidents have prompted inquiries into the data collection and storage practices employed by enterprises, from large tech companies to small businesses. This is largely due to continuous massive data breaches, and data sharing practices that have gone largely unregulated.
2018 also saw the enforcement of the General Data Protection Regulation, a tough piece of legislation from the European Union that affects the data protection policies of enterprises across the world. Preparations for the GDPR have been going on for years, and any non-compliant enterprise could be hit with heavy fines. In Europe, fines are already being doled out, and more are expected in the coming years. The EU has set the standard, and many countries and sectors are following suit, expanding data protection laws and privacy legislation.
As more people are concerned over privacy and what happens to their personal data, we can expect the conversation to continue, and more countries to enact tougher data privacy legislation. Data is a valuable commodity and protecting it should be a priority for the enterprises that collect it and the governments who protect all aspects of their citizen’s lives.
-
Cashing in on Cryptocurrency

Methods of profiting from virtual currencies increased substantially
The volatile nature of cryptocurrencies means their values rise and fall steeply and quickly, but despite that, threat actors still try to take advantage of their virtual nature. The well-publicized peak of Bitcoin in late 2017 attracted get-rich-quick malware authors, causing the number of cryptocurrency mining families to rise. We also saw many threat actors trying new ways to mine cryptocurrencies in 2018 — from using malicious add-ons for media platforms to abusing internet of things devices. There were also multiple attempts to hack cryptocurrency exchanges through many different social engineering schemes — classic ways to manipulate someone into handing over access into their account. It seems that many different threat actors were quite focused on profiting from cryptocurrencies.
The desire to profit from cryptocurrencies isn't just limited to threat actors; normal individuals naturally want to do so as well. Mining in itself is not malicious, and since it went mainstream, it is largely considered a legitimate practice if done by consenting parties. There are even some websites that are experimenting with new ways to make money without ads by asking users for permission use their system resources to mine.
Since cryptocurrency mining has been adopted by both legitimate users and threat actors, it is considered malicious only if done without the user’s knowledge or permission. As regulators increase their oversight on cryptocurrency, mining rights may change as well. But for now, it is largely dependent on user consent.
Looking back at security stories from the past year may help us prepare for the threats we will be facing in 2019. Aside from hardware issues, data protection concerns, and cryptocurrency schemes, the cybersecurity landscape is riddled with other threats. To learn more about the projected security landscape in 2019, read our security predictions report, Mapping the Future: Dealing With Pervasive and Persistent Threats.
HIDE
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.




 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One