By Stephen Hilt, Vladimir Kropotov, Fyodor Yarochkin, Benjamin Zigh
Microsoft Power Automate has transformed the way businesses handle repetitive tasks by simplifying workflows and connecting apps more efficiently. It allows users to automate workflows and integrate various services, streamlining tasks across apps like Outlook, SharePoint, and Teams. While this automation reduces manual effort, it introduces new complexities in managing and securing these automated processes at scale.
However, like any powerful tool, especially one with growing complexity, it comes with its own set of risks. What used to be discussed mostly among penetration testers and security professionals is now gaining attention in cybercriminal communities. Attackers are starting to use Power Automate to avoid detection, carry out malicious actions, and leverage legitimate workflows to maintain access or extract sensitive data. There are already cases of this being used to stay embedded in Office 365 environments and quietly pull business information without raising alarms.
Many organizations are still unaware of this threat, even though the very features and complexity that make automation so useful can also turn it into a subtle and effective attack method. While we have not yet observed current attacks using Power Automate in the wild (also owing to the complexity to observe them), there is significant interest in these techniques on underground markets. This article will explore how these threats are emerging, how cybercriminals are taking advantage of Power Automate, and what steps security teams should take now to protect their environment.
The ever-changing landscape of Microsoft environments
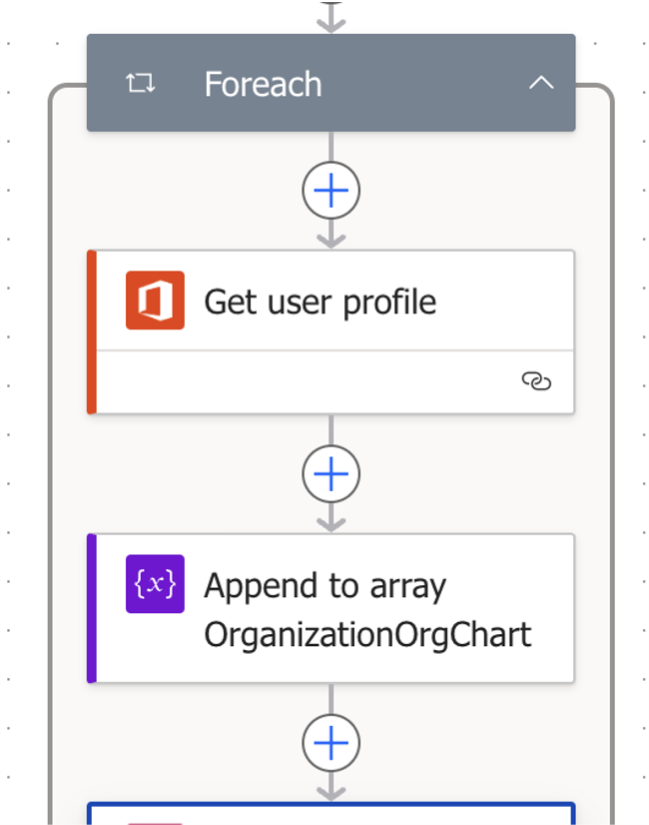
Configuring proper security and visibility in Microsoft environments is a complex and dynamic challenge. The landscape is constantly evolving, much like the flow of water in a river. The Power Automate ecosystem has been evolving as well, changing significantly, even if compared to research from just two years ago. This complexity is exacerbated by the integration of advanced technologies such as AI, which adds layers of intricacy to the already multifaceted ecosystem. Power Automate is a tool within the Office 365 ecosystem that exemplifies this complexity. The addition of AI-powered features, such as document processing and text recognition, further complicates the environment. Abundant availability of connectors (Figure 1) allows multiple scenarios for automated data interception, analysis and exfiltration.
Figure 1. Use of Office 365 connector to get userProfile information on users
Despite its benefits, Power Automate’s complexity can lead to significant visibility gaps and security blind spots. The tool’s ability to automate actions across various platforms means that any misconfiguration or unauthorized access can result in unmonitored automations performing critical tasks within the environment. This creates a false sense of security, as users may assume that low-code tools are inherently safe, overlooking the potential risks.
The complexity of Power Automate
Key capabilities and scenarios
Power Automate enables users to create workflows that connect applications like Outlook, SharePoint, and Teams, automating tasks such as sending notifications, syncing files, and processing approvals. While these capabilities enhance productivity, they also introduce complexities in managing automation at scale. Misconfigured flows can lead to unintended email loops or excessive notifications, and the integration with third-party services can create security gaps if not properly managed.
For example, one of the more widely used features is its integration with Outlook, where it can automate email notifications, categorize messages, or trigger workflows based on incoming mail. While useful, misconfigured flows can also cause issues like waste of computational resources or even excessive use of costly APIs.
Malicious users – for example, insiders or compromised accounts – can create clearly malicious flows focused on tasks like persistent information exfiltration, communication monitoring, or covert channels to control other parts of an attacker’s infrastructure. For example, an attacker attempting business email compromise (BEC) might use Power-Automate to exfiltrate and interact with email correspondence of its victims.
For cases where APIs aren’t available, Power Automate includes robotic process automation (RPA) capabilities, allowing it to interact with desktop applications through UI automation. This is useful for legacy software, but comes with challenges like reliability issues when UI elements change.
It also supports Office Scripts in Excel Online, allowing users to automate spreadsheet operations, like data entry or report generation. This makes repetitive data manipulation easier, but fully taking advantage of it requires some scripting knowledge.
Another aspect is AI Builder, which allows workflows to include AI-powered features like document processing or text recognition. While this adds more automation capabilities, it also introduces dependencies on Microsoft’s AI models.
Power Automate also connects with third-party services using prebuilt connectors, making it possible to automate processes across different platforms. However, organizations need to manage access properly, since poorly configured connectors can lead to security gaps.
Overall, Power Automate provides a lot of positive automation options inside Office 365, but it’s not a silver bullet. It requires careful setup, monitoring, security and regulatory considerations to avoid unintended consequences.
Risks of automation
If an attacker compromises a user account, they can create persistent flows that exfiltrate data, be used as covert channels or even be used as means of persistence and trigger lateral movement automation, all while remaining potentially undetected.
The ease of creating flows in Power Automate means that anyone with access can potentially create workflows that interact with sensitive systems or move data to external services. These flows can be built without IT or security input, leading to unmonitored automation performing critical tasks. This creates a false sense of security, as Power Automate supports connectors for email, file systems, HTTP endpoints, and databases, potentially giving it access to critical business data.
Visibility gaps in Power Automate
Audit trail transparency
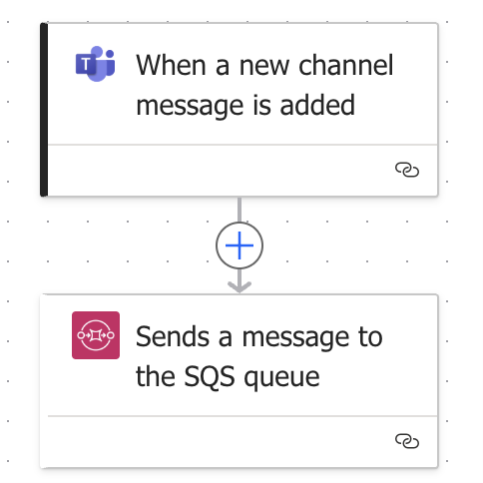
One of the difficult tasks we encountered – and we consider this to be one of the weakest areas in Power Automate – is the visibility of automation actions. While the Power Platform admin center provides a high-level view of flow activity, it lacks granularity. For example, administrators of Microsoft Teams Channels have no way to observe if the conversations in the channel are being monitored and/or exfiltrated by a power-automate script (Figure 2). The tenant administrators can probably see that a flow ran and which user triggered it, but they can’t delegate access to visibility to the users who manage Microsoft Teams channels, for example.
Figure 2. Example of exfiltration of Microsoft Teams Channel messages via AWS SQS queue
This lack of detailed visibility creates a dangerous blind spot, as users build automation logic that behaves like code but without the versioning, peer review, or change management expected from traditional development.
Ability to audit and trace events
To mitigate these risks, organizations must log and audit Power Automate activities. Microsoft logs several core events tied to user and system activity, including flow creation, edits, deletions, permission changes, and hosted RPA bot join actions. These logs are available on the Microsoft Purview compliance portal and can be exported or ingested into a security information and event management (SIEM) for monitoring. However, many security teams do not have full coverage out of the box, and unless flow telemetry is collected and analyzed, there is only partial visibility.
Attacker’s view
Insights from the cybercriminal underground
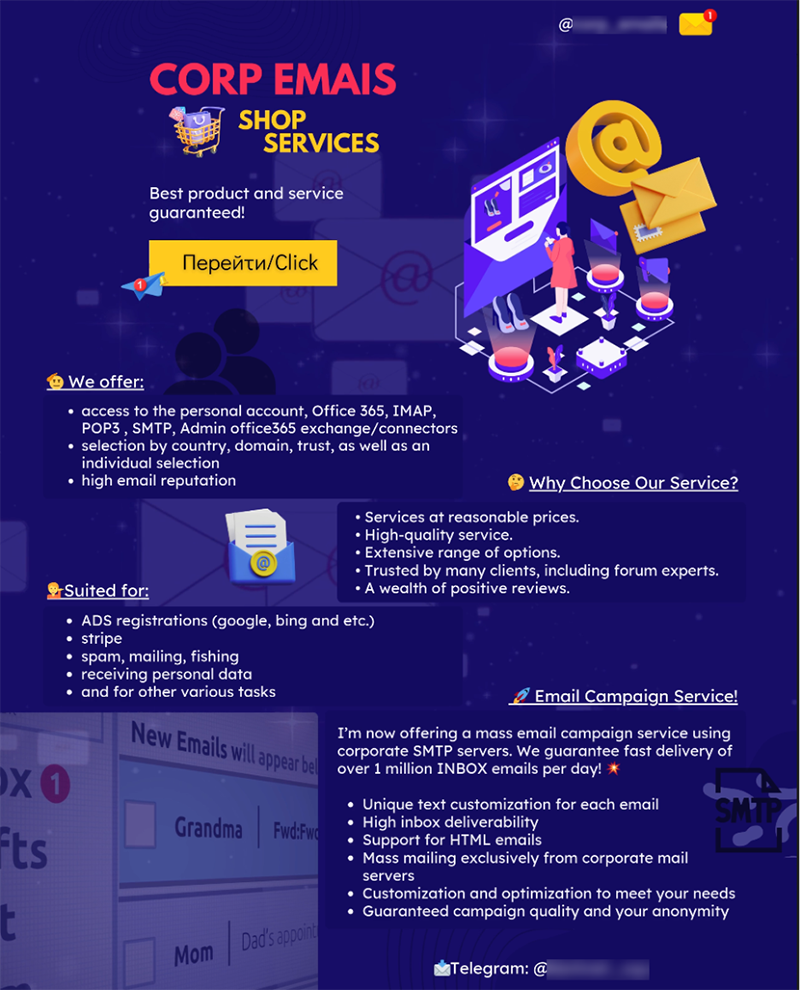
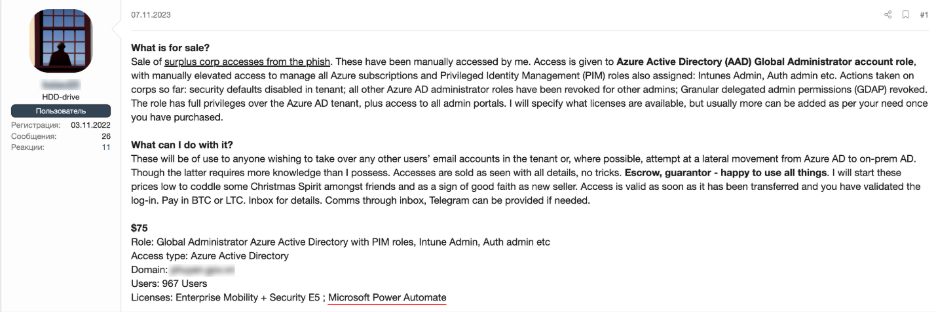
It is impossible to consider Power Automate outside the whole Office 365 ecosystem for which it gives opportunities to scale existing, and develop new, easy monetizable criminal business processes. The criminal markets already have tools to collect, sell and categorize corporate accounts and assets related to the Office 365 infrastructure and indicate the presence of the Power Automate capabilities (Figure 3).
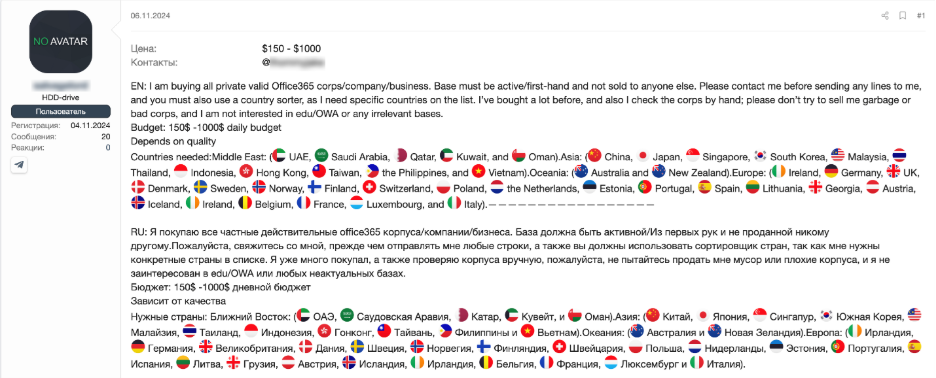
In the request to purchase such accounts, we often see the expected parameters related to the target organization, like industry sectors, revenue levels, and the geographic location of their assets (Figure 4). The presence of Power Automate adds not just scalability but also enables the ability to bypass a variety of traditional cybersecurity and business process integrity controls for the attackers. It may fuel existing criminal business processes by providing new options of doing similar or even more advanced tasks. The context of Power Automate discussions in the criminal underground indicates early adoption of the technology en mass, with more mature actors having a good understanding of its value and potential.
The range of posts in the cybercriminal underground suggests that the demand in this market is often higher than the capabilities to provide the assets. As an example, the post below mentions the queue of customers for accounts (Figure 5).
Automated account triage tools (called “checkers”) already have capabilities to recognize the presence of Microsoft Power Automate, which means that anyone with the demand to use Power Automate features can filter the accounts provided by initial access brokers according to these criteria (Figure 6).
Ransomware actors are also discussing Power Automate and its capabilities, for example, we have seen posts on the Russian Anonymous Marketplace (RAMP) forum, which is heavily associated with ransomware groups, quoting software-as-a-service (SaaS) attack techniques that can use Power Automate. In another post on the Cracked forum, we have seen discussions on how to perform downloads of attachments from Outlook that can be done with means of power-automate automation.
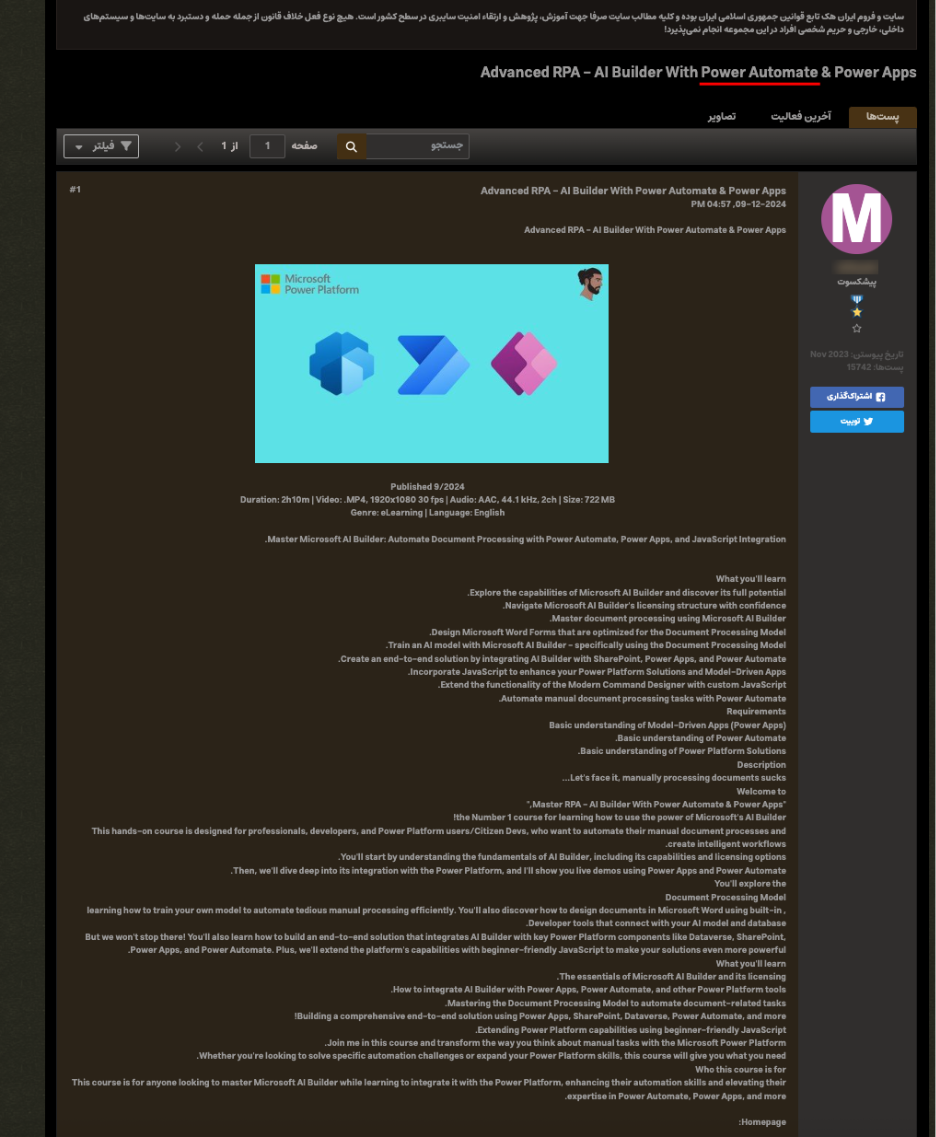
A variety of educational resources related to Power Automate are also being discussed on the underground forums. For example, the iranhack forum has several threads where Power Automate functionality is discussed and related education materials are shared for download (Figure 7). It is important for enterprises to better understand this threat now, ahead of criminal groups continuing to ramp up usage of this technology.
Figure 3. Advertisement offering corporate email accounts
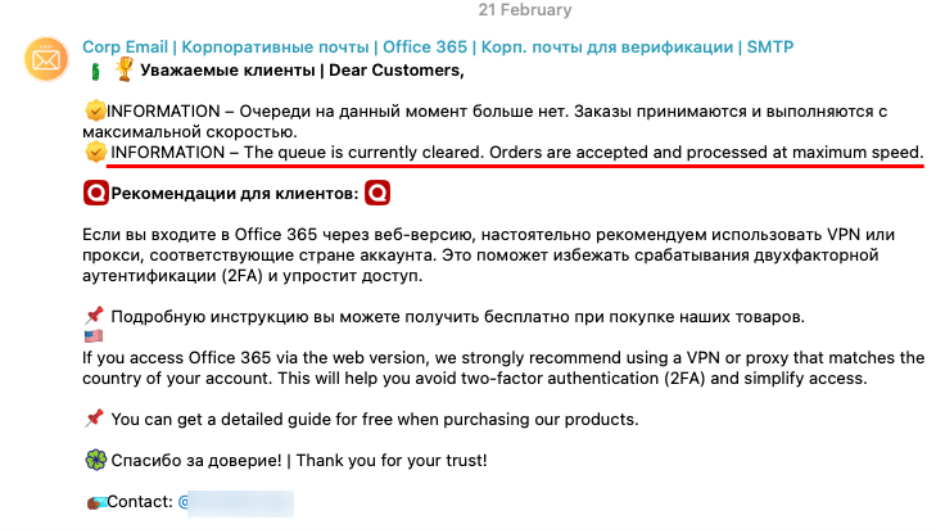
Figure 4. Example of a request to buy corporate Office 365 accounts written by non-native speaker on Russian-speaking forum
Figure 5. indication of the high demand for accounts and recommendations on how to minimize the effectiveness of Zero Trust security controls for the accounts
Figure 6. Example compromised accounts categorized by a checker tool as accounts that have Power Automate capabilities
Figure 7. Examples of Power Automate related post on the iranhack forum
Value for financially motivated cybercriminals
Financially-driven cybercrime tends to operate like investments in the sense that the monetary profit is expected to be higher than investment for the criminals. In recent years, attackers were regularly capable of obtaining millions of dollars from single victims, and that means they are ready to invest proportional resources to get this monetary gain.
Because Power Automate can enable, empower and scale many attack scenarios, it is not surprising that criminals are discussing such attacks and highlighting the presence of Power Automate in the assets and services they trade and provide - leveraging automation for their own profit.
A variety of scenarios may be easily executed:
Collecting sensitive data
Power Automate is able to create actions triggered by keywords that appear in Microsoft Teams chat flows. It is possible to automate sensitive information collection and exfiltration (even without users’ knowledge), such as monitoring for any credentials that are being shared over the corporate chat system (which is not uncommon).
Similarly, triggers that act on the upload of new documents to SharePoint can be configured to automatically access, analyze, and even exfiltrate potentially sensitive documents or extracted information.
Hidden data exfiltration
Power Automate has the ability to communicate with third-party components and cross-tenant Microsoft resources, which can be used for automation of hidden data exfiltration. A variety of triggers can be created to monitor Office 365 environments and automate exfiltration of documents, messages, emails, email analytics and more. AI integration allows for the creation of sophisticated processes that can perform preliminary data analysis before the data is sent to an external organization. The technique resembles living-off-the-land (LOTL) approaches, in which most of the communication would be happening to known and trusted resources, thus advanced monitoring capabilities are needed to be able to identify and respond to this kind of behavior.
Denial of Service of Executive orders (DoSEO)
Attackers could also use Power Automate to automate posts via instant messaging (IM) and email from important compromised individuals, issuing confusing orders to their staff. For example, at the same time attackers are carrying out a wider attack like deployment of ransomware, messages could be sent on behalf of a compromised IT department ordering everyone to quickly install a new “update” they are sending (which, in reality, spreads the attack). A similar scenario is applicable during a major exfiltration, in which a high-ranking compromised official orders all management to prepare slide decks for a meeting at short notice – having them pull in all their departments to work on it forms a good distraction for the attackers. Such activities can consume resources of subordinates, who normally tend to process requests from executives with high priority. In addition, the real orders originating from executives are ignored or processed with delays due to a high number of malicious orders which were sent through automation on their behalf.
Many of these attacks can be designed to trigger a delay at the most critical time to maximize impact: This could be during a major event, like a product launch, or at the end of the fiscal year.
Value for nation-state-aligned groups
The typical goals of a targeted attack, also known as an advanced persistent threat (APT) are to be able to create points that maintain persistence at the compromised organization, perform lateral movement, elevate privileges, and to secretly (and possibly continuously) exfiltrate information such as office documents, emails, and messaging communication to an external location. The Power Automate framework has features that can allow all this to happen.
A few simple scenarios could be easily executed:
Automated sensitive data exfiltration
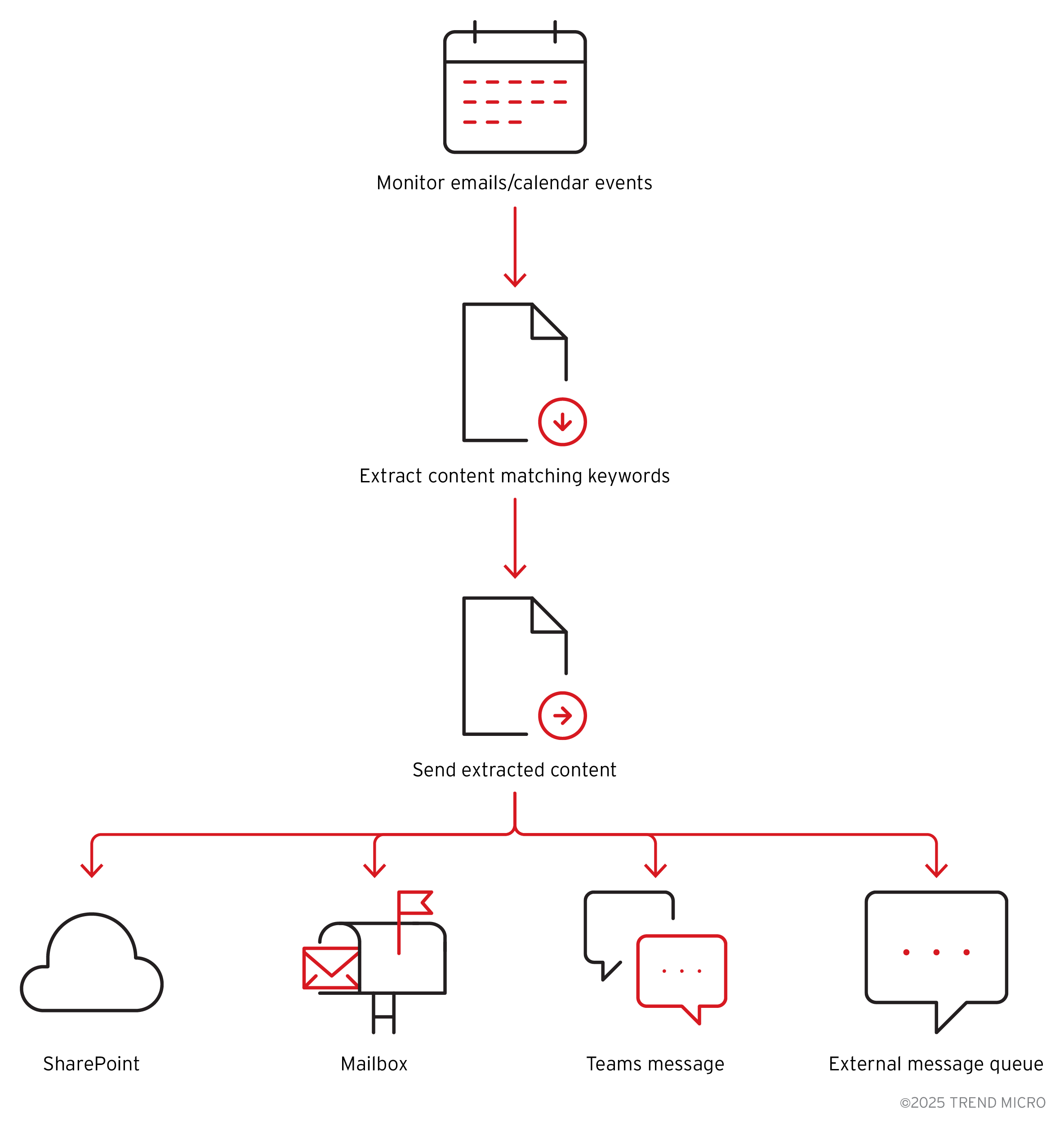
Using the Power Automate framework, malicious actors could monitor emails or calendar events, extract content matching certain keywords, and deliver the content to a SharePoint location, another mailbox, a Teams message or even an external message queue (Figure 8). Depending on the configuration of the environment it might be even possible to exfiltrate data to other environments such as Amazon Web Services (AWS) or to another Microsoft account.
Figure 8. How the Power Automate framework may be used for automated data exfiltration
Automation of impersonation of company staff members
Power Automate allows interactions with email, Microsoft teams messaging and other platforms. These tools allow scenarios for automation of monitoring and/or mimicking interactions in online Microsoft Teams messenger and Outlook. Given the wealth of processing capabilities, it is also possible to automate social engineering of company employees (thanks to powerful AI capabilities), mass-automate phishing and the collection of sensitive details across compromised companies, and more.
Excessive permission exploitation
While the Active Directory users themselves may be limited with their permissions, certain Power Apps can have permissions that allow types of access that are different from the permissions granted to the user. Logic in Power Apps can be exploited to access resources that are not accessible by the user, normally brought on by the complexity of managing the permissions models. That means that the same legitimate user would be unable to access particular assets using normal interfaces, while those restricted resources can be accessible through Power Automate. In the case of account compromise, an attacker can leverage excessive permissions to improve attack speed, scale, and impact.
There are variety of other scenarios, and we highly recommend reading the more comprehensive set of examples in the appendix.
How to deal with this
Power Automate’s flexibility and integration capabilities make it useful for streamlining operations. But these capabilities, without the proper guardrails, may make it a potential attack vector as much as a business enabler. Security teams will need to enforce strict access controls, robust monitoring, and continuous auditing of automated workflows to help their organizations respond effectively to emerging threats that target the intricate Office 365 ecosystem. Applying the following best practices can also help defenders reduce their organization's attack surface and close visibility gaps:
Configuration Hardening to Prevent Abuse
Organizations aiming to reduce the risk of misuse in Power Automate, particularly Power Automate Desktop (PAD), should begin by evaluating whether the tool is necessary across their environment. If PAD is not required, it should be disabled using Group Policy. Microsoft provides detailed guidance on this in its governance documentation.
Where PAD is needed, access should be tightly controlled. Role-based access control (RBAC) should be implemented to ensure that only authorized users can create, modify, or share flows. This limits the potential for insider misuse and reduces the likelihood of accidental exposure of sensitive data.
Data Loss Prevention (DLP) policies should be defined and maintained across the Power Platform. These policies help prevent sensitive data from being transferred between business-critical systems and non-business connectors, such as personal email or cloud storage services. Microsoft’s DLP capabilities for Power Automate are described in this guide.
Monitoring flow execution is another critical layer of defense. Administrators should use built-in analytics and custom security roles to track who is running flows, what those flows are doing, and whether they align with expected behavior. Microsoft has published a guide for admins that outlines how to implement these controls effectively.
Detection mechanisms should be established to identify signs of abuse. These include flows executing from non-standard paths, launching command-line tools such as cmd.exe or powershell.exe, or modifying registry keys to establish persistence. While native telemetry from Power Automate is limited, these behaviors can often be detected through endpoint monitoring and behavioral analysis.
Mitigation Strategies for Trend Micro Customers
The Trend Vision One™ platform enables a comprehensive approach to detecting and mitigating Power Automate abuse. The platform provides broad visibility which can be used to correlate signals across endpoints, identity, and network layers. This multi-layered approach is essential for identifying automation abuse that may otherwise go unnoticed.
On the endpoint, Trend offers behavioral analysis that can detect script-based activity commonly associated with flow abuse, such as PowerShell or CMD execution. In-memory analysis helps identify fileless malware and suspicious automation that may be triggered by PAD flows. Application control can restrict unauthorized use of PAD components, and device control combined with DLP policies can prevent data exfiltration via USB or network shares. Ransomware rollback and intrusion prevention features help mitigate persistence mechanisms such as scheduled tasks or registry autoruns.
Trend’s XDR capabilities further enhance detection and response. Automated playbooks can isolate compromised endpoints, terminate malicious processes, and alert SOC teams. These playbooks can be customized to monitor for PAD launching from non-standard paths, using command-line tools, or modifying registry keys. YARA and osquery integration allows for deep inspection of PAD-related artifacts, including scheduled tasks and suspicious DLLs.
Although Power Automate telemetry is not currently available through Trend’s connectors, the platform supports integration with Microsoft 365, Purview, Dataverse, and Azure. This enables broader visibility into user behavior and data movement, which is essential for detecting abuse that spans multiple layers of the environment. Customers are encouraged to coordinate with product teams to explore roadmap options for deeper Power Platform telemetry integration.
Trend also provides robust identity and access control features. Zero Trust Secure Access (ZTSA) helps limit lateral movement, while identity posture analytics can detect risky user behavior, such as flow creation outside of normal patterns or automation initiated from unmanaged devices.
In the email layer, Trend Vision One™ – Email and Collaboration Security integrates with Microsoft 365 to intercept outbound messages sent via Power Automate flows. While the platform does not automatically block these emails, administrators can manually configure mail flow rules to inspect headers inserted by Power Automate, such as x-ms-mail-application: Microsoft Power Automate. By filtering on these headers and validating flow identifiers, organizations can block or quarantine messages that originate from unapproved flows. This configuration allows customers to prevent automated flows from exfiltrating data via email, provided that appropriate rules are in place.
Together, these capabilities form a holistic defense strategy that addresses the limitations of any single solution. By combining endpoint telemetry, behavioral analytics, identity insights, and email controls, Trend Micro enables organizations to detect and respond to Power Automate abuse even when direct visibility into flow execution is limited.
Conclusion
Power Automate is a great tool for any business looking to save time and reduce manual work, offering a simple interface and seamless integration with other Microsoft services like Outlook, SharePoint, and Teams. It supports everything from approvals and reminders to pulling data from forms; and with a wide range of templates and custom flow options, it suits users of all skill levels. But with that power comes complexity – and that complexity can create blind spots. As automation expands, so does the potential for misconfiguration, misuse, or even malicious activity if proper oversight is not in place. Fortunately, Microsoft’s admin tools offer visibility and control, and solutions like Vision One can help organizations proactively identify and manage risks. In the end, Power Automate enables teams to focus on meaningful work instead of repetitive tasks – but only when its complexity is understood and managed responsibly.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One