Ransomware Spotlight: DragonForce
What organizations need to know about DragonForce
(Water Tambanakua)
DragonForce (tracked by Trend Micro as Water Tambanakua) has shown consistent activity and a clear drive to expand its influence among affiliates. Its tactics also point toward an aggressive and highly opportunistic approach. One example of this is its use of multivariant payloads, in which it reuses leaked builders from LockBit and Conti codebases. By not relying on a single family, the group can switch their payload quickly, making it difficult for defenses to predict and defend.
In addition to its flexible codebase, DragonForce employs a more advanced evasion technique, specifically bring your own vulnerable driver (BYOVD). This technique allows DragonForce to disable endpoint security defenses by exploiting legitimate but vulnerable drivers—a relatively uncommon tactic among ransomware operators.
Overall, these tactics show an agile and ambitious ransomware group. By providing tools for affiliates and encouraging more autonomous operations, the group could be at the root of more attacks in the future. Being aware of DragonForce’s trajectory would be helpful to defending against attacks that may indirectly surface from this group’s ecosystem.
Here is an outline of what organizations should know about the group:
- The group claimed responsibility for several attacks in the UK, including those against well-known retailers in June 2025, signifying the group’s goal of targeting high-profile entities.
- Aside from targeting retailers, it has also been known to target supply-chain/service providers, often using ransomware and data-exfiltration tactics to disrupt operations and leak sensitive information.
- Since its emergence it has rapidly evolved through the years. It began with Lockbit3.0 builders in 2023, then released its own ransomware and leak site in 2024, before rebranding into a ransomware “cartel,” in 2025.
- The group offers affiliates up to 80% of ransom proceeds, in addition to tools for attack management, automation, and customized ransomware campaigns.
- In August 2025, they launched a “data analysis service,” for creating tailored extortion materials — offered to affiliates targeting organizations with an annual revenue of no less than US$15 million.
- The group allows their affiliates to build multiple variants of their ransomware, tailored for platforms including Windows, Linux, EXSi, and NAS.
- Aside from the uncertainty of its connection to a hacktivist group, DragonForce has been linked to Scattered Spider, The Com, BlackLock (Mamona), and RansomHub.
- Organizations should anticipate more diverse and aggressive campaigns linked to this group, including those that don’t carry the DragonForce brand but instead those of their affiliates.
DragonForce timeline
In August 2023, at the start of its ransomware operations, DragonForce targeted companies in critical sectors using a variant of a leaked LockBit 3.0 builder. By June 26, 2024, the group launched an affiliate program that offered 80% of the ransom to affiliates, along with tools for attack management and automation. These tools allowed affiliates to create customized ransomware samples, including disabling security features, setting encryption parameters, and personalizing ransom notes. A month later, in July 2024, DragonForce released their own variant of ransomware, which was reportedly based on Conti V3. The use of leaked LockBit and Conti builders could hint that affiliates have ties to Lockbit and Conti ecosystems.
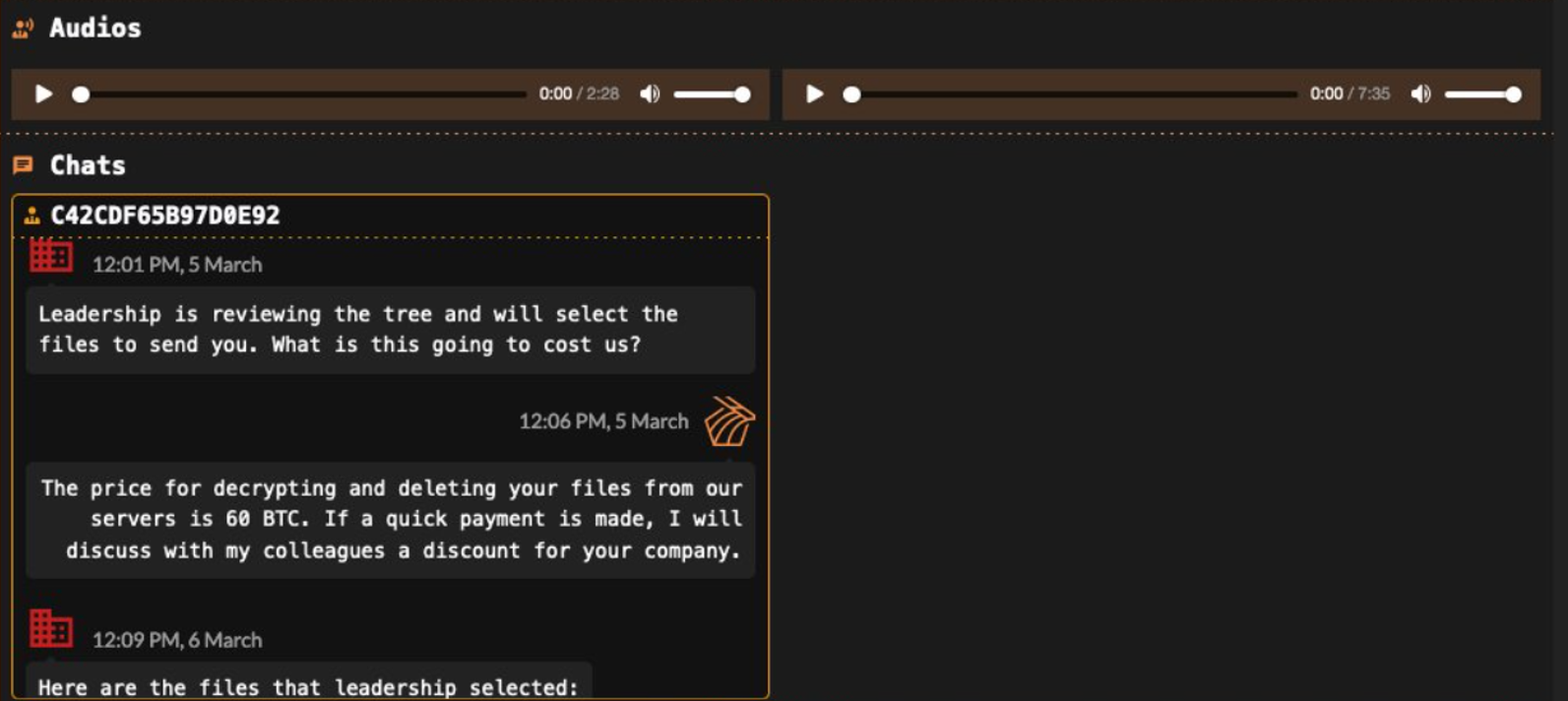
Figure 1. A sample of activity in 2024, where DragonForce published an audio recording of a victim.
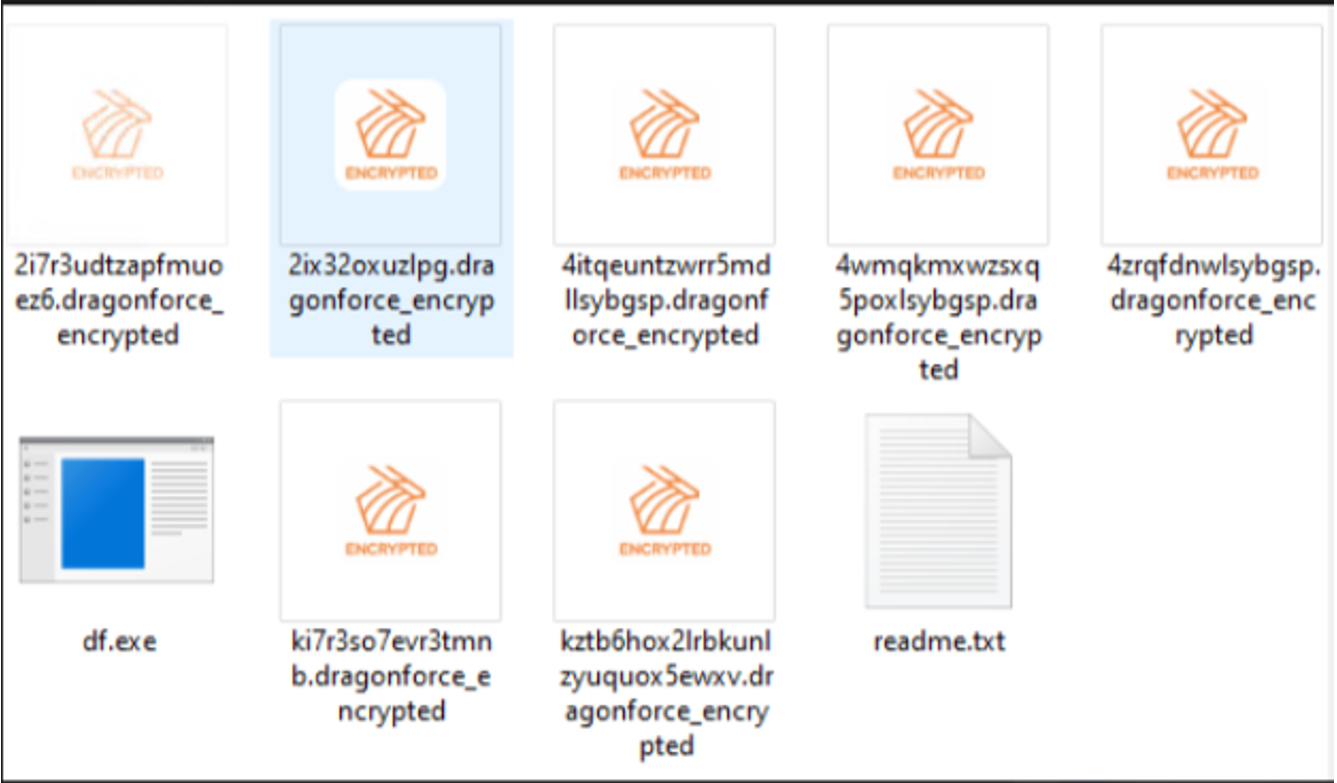
Figure 2. Encrypted files are renamed to random characters + ".dragonforce_encrypted"
DragonForce allows affiliates to build multiple variants of their ransomware, with Windows, Linux, EXSi, and NAS-specific encryptors. In November 2024, we discovered a Linux variant of the ransomware, with findings detailed in the technical section of this report.
Shift to a cartel
On March 19, 2025, they announced their shift to becoming the DragonForce Ransomware cartel. As a cartel, affiliates were encouraged to branch out from the DragonForce brand to build their own, while still using the group’s tools and resources. This change marks a notable shift that was quickly followed by further developments in the months ahead.
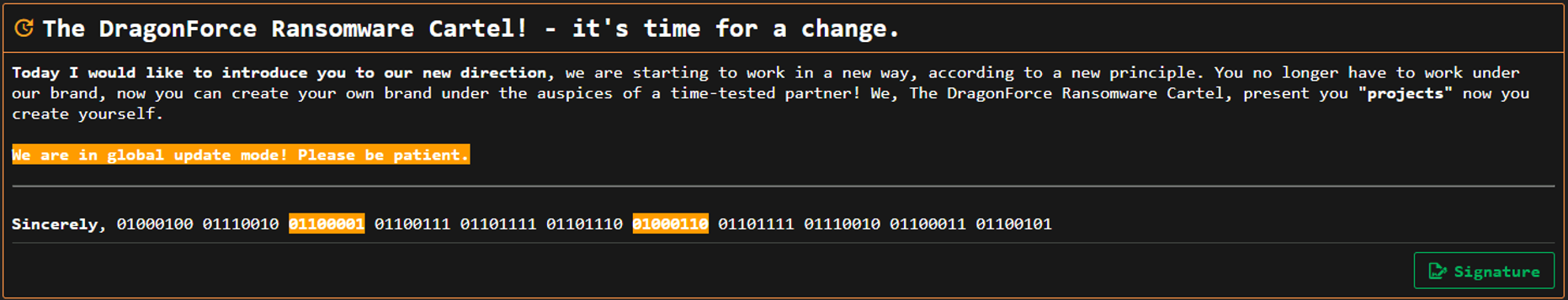
Figure 3. Post on DragonForce’s blog advertising their shift into a ransomware cartel.
Links to other ransomware groups
Around the time it shifted into a cartel, DragonForce was also linked to activity involving other RaaS groups. It was tied to attacks from BlackLock, and consequently, Mamona. It also appeared to be in conflict with RansomHub, which had gone offline during this same period.
The nature of these collaborations and takeovers remains uncertain, with security experts speculating that they could stem from hostile rivalry or a simple consolidation of resources.
Whatever the case may be, DragonForce-linked attacks began to grow in prominence in the following months. The group was linked to the UK retail attack back in April, alongside Scattered Spider (Octo Tempest) and loose threat actor collective the “Com.” Reports suggest that Scattered Spider served as the Initial Access Broker while DragonForce handled deployment and extortion.
In June 2025, we identified a new DevMan ransomware variant that seems to further highlight the link between DragonForce and Mamona (BlackLock).
New services
On August 23, 2025, DragonForce introduced a “data analysis service” designed to assist affiliates, and pressure victims of ransomware/data leak attacks into paying. The "service" functions as a risk audit of both the targeted organization and the stolen data, generating materials such as extortion call scripts, drafts of letters to management, and pseudo legal analysis and advice reports. Fees for this service range from 0% to 23% of ransom payments and is specifically marketed to affiliates who target organizations with an annual revenue of at least US$15 million.
Infection chain and techniques
The following section details the initial infection chain observed from DragonForce activity as illustrated in Figure 4.
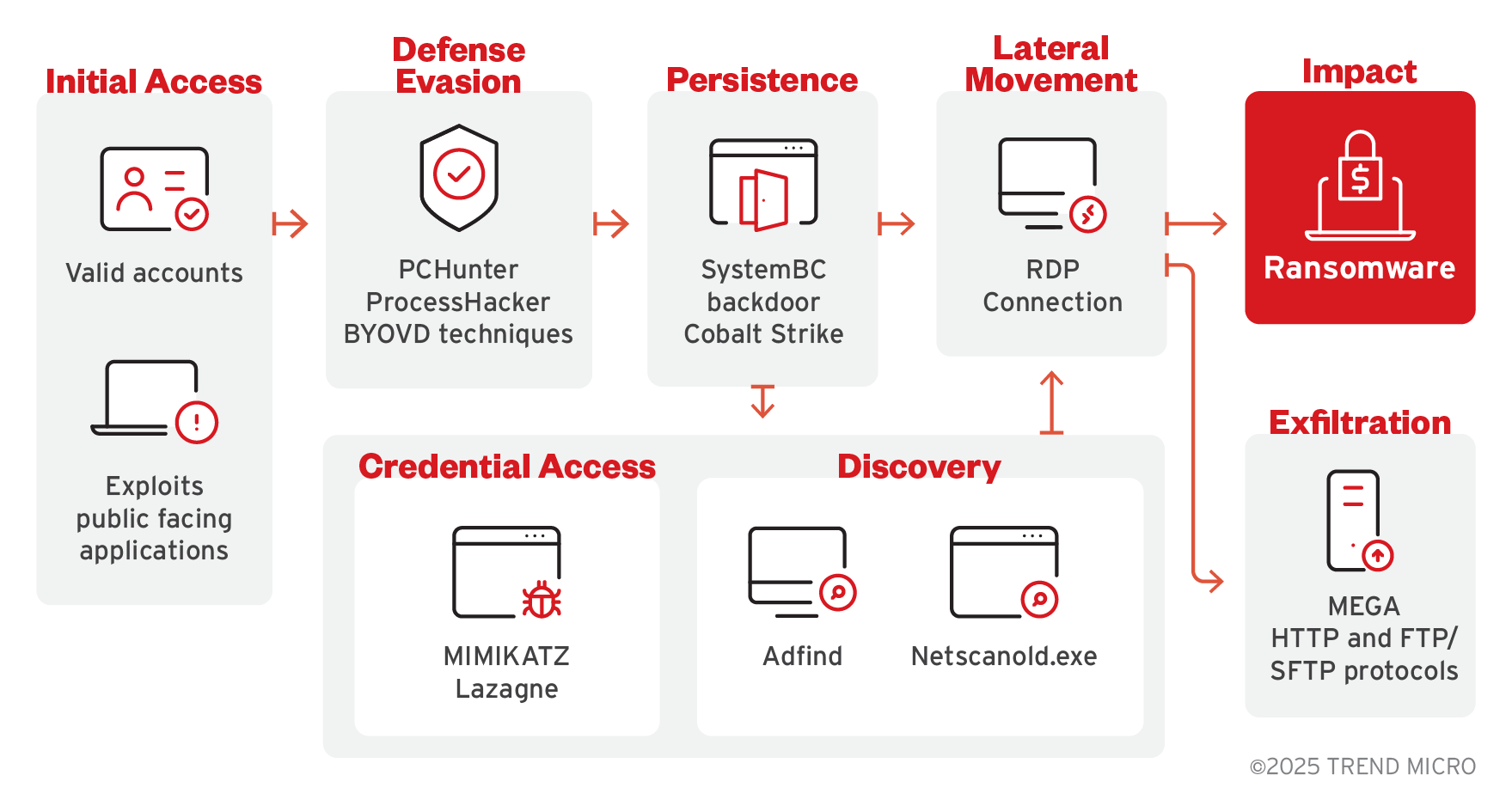
Figure 4. DragonForce observed infection chain
Technical Details
The ransomware accepts the following arguments:
| Argument | Details |
|---|---|
| -safe | Reboots in safeboot, then encrypts the user's machine |
| -wall | Changes system Wallpaper and Print ransom note on printers then deletes itself after renaming for 26 times. |
| -path | Specifically encrypt the target, can be file or folder |
| -gspd | Perform Group Policy Modification for Lateral Movement |
| -psex | Lateral Movement via Admin Shares |
| -gdel | Delete group policy updates |
| -del | Deletes itself after renaming for 26 times. |
It encrypts fixed, removable, and network drives.
This ransomware adds the following processes:
- exe shadowcopy delete
- exe /set {default} bootstatuspolicy ignoreallfailures
- exe delete systemstatebackup -keepVersions:3
- exe delete systemstatebackup
- exe /set {default} recoveryenabled No
- exe delete shadows /all /quiet
- exe delete catalog-quiet
- exe {Drive}:\Contact Us.txt
It appends the following extension to the file name of the encrypted files:
- {original filename}.{original extension}.locked
It contains a list of strings where it chooses files to avoid. For the variant analyzed, it avoids the encrypting files with the following strings in their file path:
- inf
- ini
- bin
- bak
- dat
- ini
- DAT
- db
- ntldr
- dat
- dat.log
- ini
- db
- README.txt
- $recycle.bin
- $windows.~bt
- $windows.~ws
- all users
- boot
- msi
- default
- intel
- Microsoft
- Msocache
- Perflogs
- program files
- program files (x86)
- programdata
- public
- system volume information
- tor browser
- windows
- old
- x64dbg
It contains a list of extensions where it chooses files to avoid. For the variant analyzed, it avoids encrypting the following files with the following extensions:
- 386
- adv
- ani
- bat
- bin
- cab
- cmd
- com
- cpl
- cur
- deskthemepack
- diagcab
- diagcfg
- diagpkg
- dll
- drv
- exe
- hlp
- hta
- icl
- icns
- ico
- ics
- idx
- key
- ldf
- lnk
- lock
- mod
- mpa
- msc
- msi
- msp
- msstyles
- msu
- nls
- nomedia
- ocx
- pdb
- prf
- ps1
- rom
- rtp
- scr
- search-ms
- shs
- spl
- sys
- theme
- themepack
- wpx
The Linux variant meanwhile accepts the following arguments:
| Argument | Description |
|---|---|
| -paths | sets a variable either 1 or 0 but no purpose |
| -vmsvc | also sets a variable, possible for future upgrade or update, so far no purpose |
| -e | ignore other configuration |
| -n | number of dry runs |
| -d | detach |
| -h | number of hours delay |
| -m | number of minutes delay |
| -s | number of seconds delay |
| -j | number of thread |
| -l | log file path |
| -p | Specify a path to encrypt |
| -q | quiet |
| -v | verbose or logger trace enabled |
| -wvi | Whitelist a VM using VM ID |
| -wvn | Whitelist a VM using VM Name |
The Linux variant adds the following processes:
- Enumerates VM using the command vim-cmd vmsvc/getallvms
- Turns off all VM’s using the command vim-cmd vmsvc/power.off
The extracted configuration outlines how DragonForce performs its encryption process. Here we specify the logging details, encryption keys, file renaming rules, and operational parameters, such as delay, threading, and extension naming. The configuration is tailored for VMware ESXi environments (notably /vmfs/volumes) while retaining extensive whitelists of system directories, file extensions, and filenames to avoid encrypting critical components required for the host bootability.
Config:
- Log file: encryption.log
- Log params: out=1 trc=0 stat=1 file=1 enc=0
- Keys: 2DB77648B9962A2B FB1B666974A88AA5
- Dry-run: 0
- Encryption params: 16 52428800 0
- Rename: 1 Extension: .dragonforce_encrypted
- Delay: 20 Threads: 4 Detached: 0
Paths:
- /vmfs/volumes
Whitelist paths:
- BOOTBANK1
- BOOTBANK2
- .sdd.sf
- log
- devices
Whitelist extensions:
- .b00
- .v00
- .v01
- .v02
- .v02
- .v03
- .v04
- .v05
- .v06
- .v07
- .t00
- .sf
Whitelisted filenames:
- .fbb.sf
- .fdc.sf
- .pbc.sf
- .sbc.sf
- .vh.sf
- .pb2.sf
- .jbc.sf
- boot.cfg
- state.tgz
- onetime.tgz
- imgdb.tgz
- jumpstrt.gz
- useropts.gz
- features.gz
- basemisc.tgz
Initial Access
- Exploit public-facing Ivanti Connect Secure application using known vulnerabilities (CVE-2023-46805, CVE-2024-21887, CVE-2024-21893)
- Other exploits that the group used are, CVE-2021-44228 (Apache Log4j2 Remote Code Execution (“Log4Shell”) and CVE-2024-21412 (Microsoft Windows SmartScreen Security Feature Bypass)
- The group has ties with Scattered Spider that had served as the initial access broker of the group.
Execution
- Remote command execution on the compromised server
- Download and execution of crack software and keygens on multiple endpoints
Persistence
- Use of a compromised admin account for maintaining access to the victim’s environment.
- Disabling security services by modifying the registry key to impair their security services which allows the adversaries to ensure the malware’s survivability across the system.
- The group has also been observed to be leveraging living off the land (LOLbas) for its evasion and persistence.
Privilege
- Credential dumping via registry hives to access sensitive OS credentials
- DragonForce ransomware has been observed using access token manipulation, specifically token impersonation, to escalate privileges and execute processes under the NT AUTHORITY\SYSTEM context. This technique allows the ransomware to perform high-impact actions such as disabling security tools, modifying system configurations, and encrypting files with elevated privileges.
Lateral Movement
- Use of RDP and SMB for accessing other systems within the network
- The group was also seen leveraging a remote monitoring and management (RMM) tool called SimpleHelp. The group has leveraged the following vulnerabilities of the tool for lateral movement.
- CVE-2024-57727 - critical path traversal vulnerability
- Cve-2024-57728 - Arbitrary File Upload Leading to Remote Code Execution
- CVE-202457726 - API Key Privilege EscalationThe group was also seen leveraging a remote monitoring and management (RMM) tool called SimpleHelp. The group has leveraged the following vulnerabilities of the tool for lateral movement.
- The group employs multiple native Windows utilities and remote execution methods to move laterally across the compromised network.
- PsExec – legitimate tool used to execute commands on remote systems.
- Windows Management Instrumentation (WMI) – used for remote command execution and system management.
Discovery
- Network and account discovery using tools like "AdFind"
- Credential discovery via PassView or Registry Hive Dumping
- The DragonForce group has been observed exploiting vulnerabilities in the SimpleHelp RMM tool to gain access to its instance and collect information from victim environments. This includes gathering device names, system configurations, user account details, and network connection data. The following vulnerabilities were leveraged:
- CVE-2024-57727 – Critical path traversal vulnerability allowing unauthorized file access.
- CVE-2024-57728 – Arbitrary file upload vulnerability leading to remote code execution.
- CVE-2024-57726 – API key privilege escalation vulnerability enabling low-privileged users to gain administrative access.
Exfiltration
- The group conducts data exfiltration to support its double extortion strategy, where victims are threatened with public data leaks in addition to system lockdown. The group has been using the following tools to steal and exfiltrate stolen sensitive data.
- MEGA.nz – a cloud storage platform frequently abused by threat actors for uploading stolen archives.
- FTP/SFTP Servers – servers used to transfer data to attacker-controlled infrastructure
- HTTP servers – custom or compromised web servers that are used to receive exfiltrated data via HTTP POST request or file uploads.
Defense Evasion
- Disabling of security tools and services
- PCHunter, ProcessHacker, Disable via valid account RDP/RAT
- The ransomware employs the BYOVD technique to terminate security processes, enhancing its ability to evade detection.
Credential Dumping
- Hacktool PassView or Registry Hive Dumping
- The DragonForce ransomware group employs a combination of post-compromise tools and techniques to harvest credentials and map victim environments, enabling lateral movement and privilege escalation.
- After gaining initial access, DragonForce deploys tools such as Mimikatz and LaZagne to extract sensitive credentials from compromised systems:
- Mimikatz is used to dump credentials directly from Local Security Authority Subsystem Service (LSASS) memory, including plaintext passwords, NTLM hashes, Kerberos tickets, and domain admin credentials.
- LaZagne targets local applications, extracting stored credentials from browsers, email clients, databases, and other software.
- These tools are executed post-compromise to maximize access across the environment and facilitate further exploitation.
Collection
- Transfer and use of malicious tools and scripts to compromise systems to collect victim information.
Command and Control
- Communication with C&C servers using web protocols
- Use of RAT: Cobalt Strike and SystemBC
Impact
- Execution of ransomware to encrypt data
- Dropping of ransom notes and encryption of files
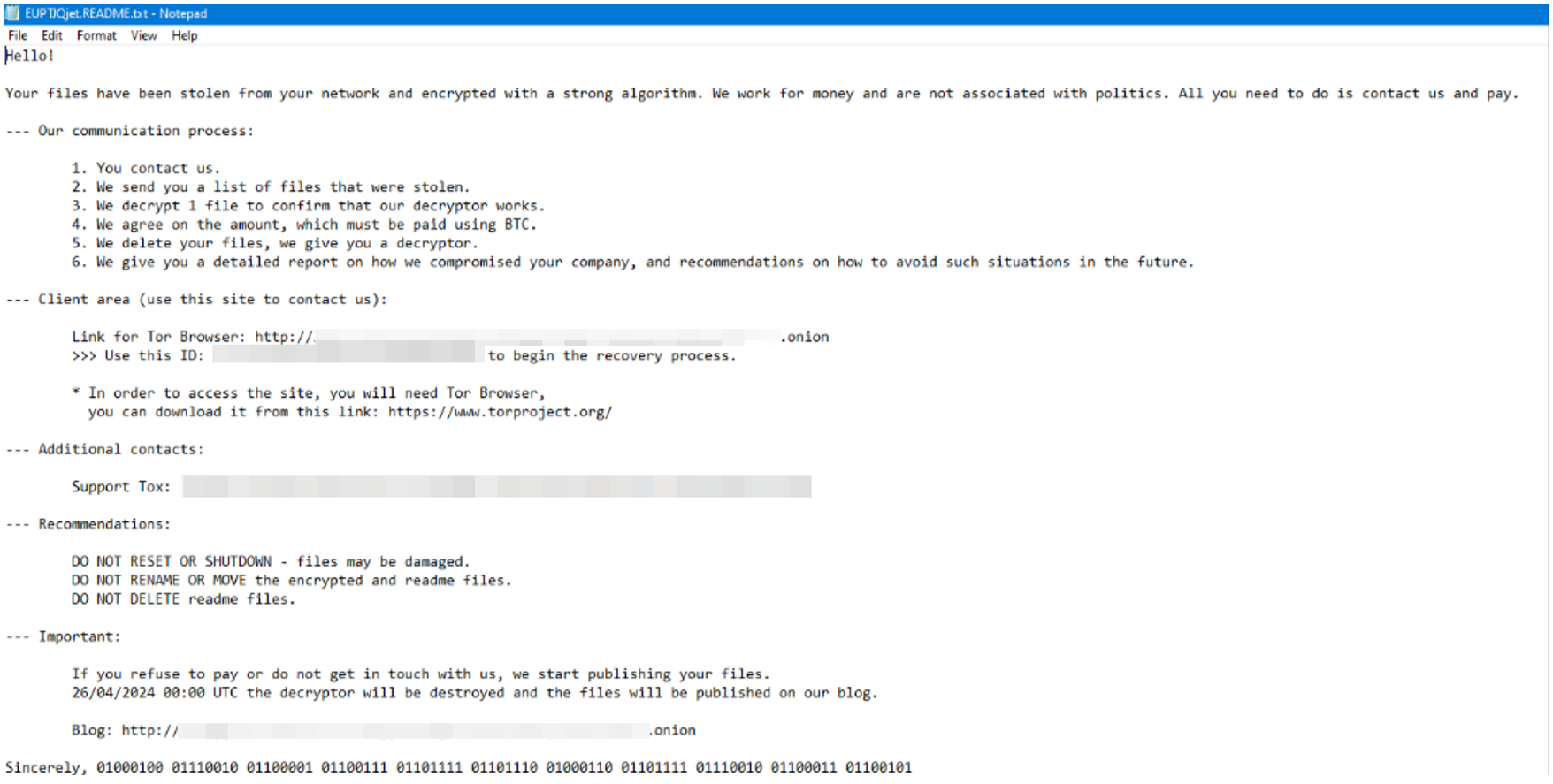
Figure 5. DragonForce ransom note
- Changing of victim’s desktop background image.
Figure 6. Desktop background image altered by DragonForce.
- Inhibition of system recovery by deleting volume shadow copies and disabling recovery measures
MITRE tactics and techniques
| Initial Access | Execution | Privilege Escalation | Defense Evasion | Credential Access | Discovery | Lateral Movement | Exfiltration | Command and Control | Impact |
|---|---|---|---|---|---|---|---|---|---|
T1190 - Exploit Public-Facing Application T1189 - Drive-by Compromise T1078 - Valid Accounts | T1059.003 - Command and Scripting Interpreter: Windows Command Shell | T1078.002 - Valid Accounts: Domain Accounts | T1562.001 - Impair Defenses: Disable or Modify Tools | T1003.002 - OS Credential Dumping: Security Account Manager (SAM) T1003.001 - OS Credential Dumping: LSASS Memory | T1595.002 - Active Scanning: Vulnerability Scanning T1087 - Account Discovery T1018 - Remote System Discovery T1069.002 - Permission Groups Discovery: Domain Trusts T1016 - System Network Configuration Discovery | T1021.001 - Remote Services: Remote Desktop Protocol | T1567.002 - Exfiltration to Cloud Storage | T1105 - Ingress Tool Transfer T1071.001 - Application Layer Protocol: Web Protocols | T1486 - Data Encrypted for Impact T1490 - Inhibit System Recovery T1489 - Service Stop |
Summary of malware, tools, and exploits used
Security teams can look for the presence of the following tools and exploits that are typically used in Water Tambanakua attacks:
| MITRE TTP | ATTACK TOOL |
|---|---|
| Credential Access | MIMIKATZ and Lazagne |
| Discovery | Adfind, Netscanold.exe, PassView, and Registry Hive Dumping |
| Persistence | Using valid accounts obtained from exploit via public-facing application SimpleHelp RMM vulnerability |
| Defense Evasion | PCHunter, ProcessHacker, and BYOVD |
| Data Exfiltration | MEGA and HTTP/FTP/SFTP services |
| Lateral Movement | PSExec and RDP connections |
| Command and Control | Cobalt Strike and SystemBC |
Top affected countries, industries, and business sizes
The US was the most affected by DragonForce, far outstripping other countries in victim count. The UK followed, aligning with the group’s more recent spate of high-profile attacks. Other affected countries include Germany, Australia, and Italy.
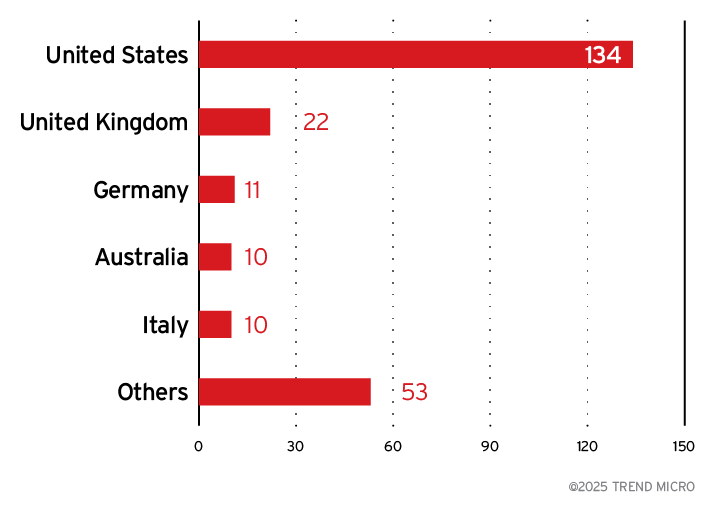
Figure 7. The distribution of countries (top 5) targeted by DragonForce
Sources: DragonForce leak site data and Trend open-source intelligence (OSINT) research (Dec. 2023- Aug. 2025)
DragonForce has mostly targeted companies in the manufacturing, construction, IT, and professional services, but overall, it casts a wide net. This demonstrates the group’s more opportunistic behavior, rather than a sector-specific targeting. Their broad approach is typical of RaaS operations with strong affiliate programs. As most of their victims are tied to infrastructure and digital services, it indicates a strategy for maximizing disruption.
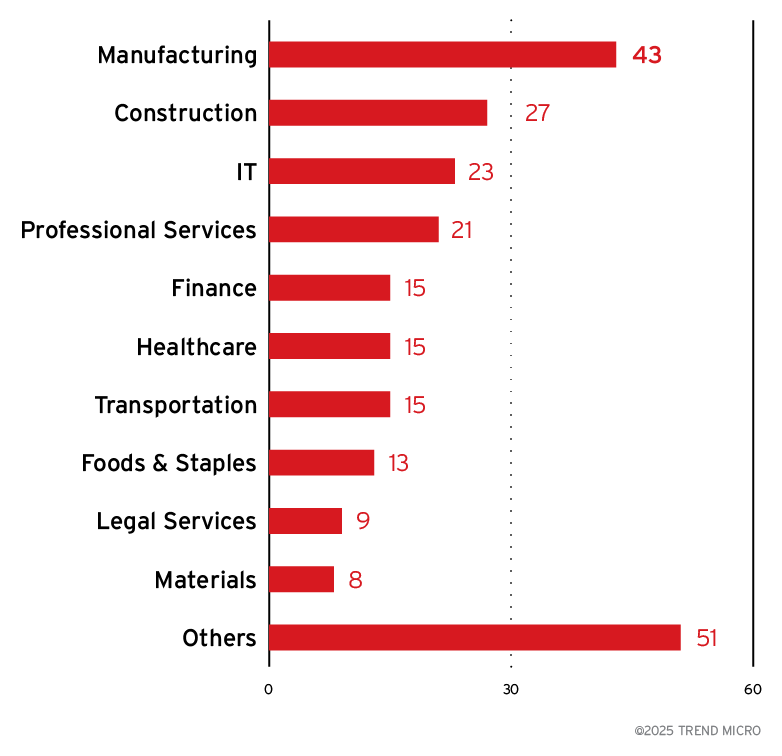
Figure 8. A breakdown of the top 10 industries targeted by DragonForce ransomware attacks
Sources: DragonForce leak site data and OSINT research (Dec. 2023- Aug. 2025)
Across all publicly revealed victims, North America remains the primary target, followed by Europe. This trend aligns with DragonForce’s focus on lucrative markets.
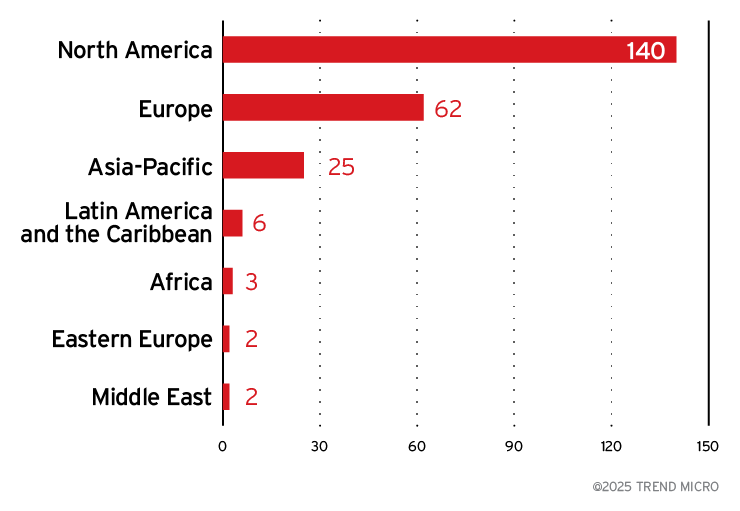
Figure 9. The distribution by region of the DragonForce ransomware’s victim organizations, excluding victims with unknown locations.
Sources: DragonForce leak site data and Trend open-source intelligence (OSINT) research (Dec. 2023- Aug. 2025)
While the majority of the DragonForce’s victim organizations were small businesses, the group has not shied away from larger targets.
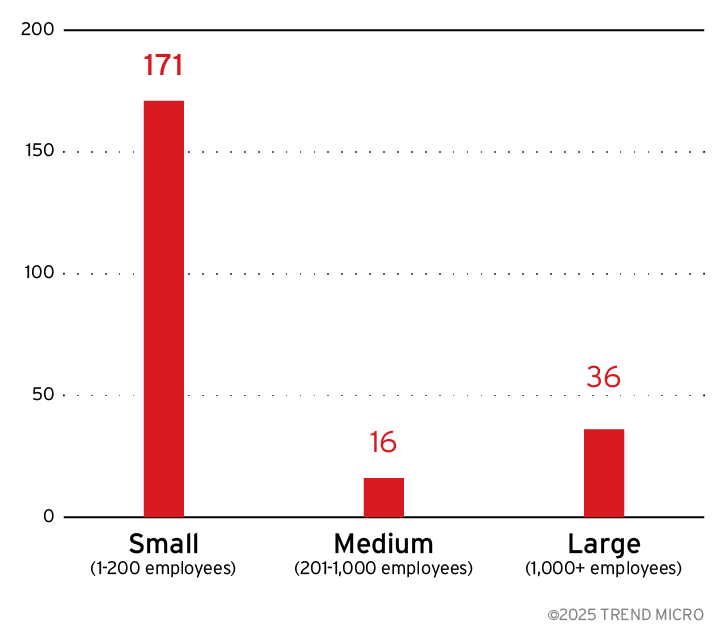
Figure 10. The distribution by organization size of DragonForce’s victim organizations
Sources: DragonForce’s leak site and Trend Micro’s OSINT research (Dec. 2023- Aug. 2025)
Proactive security with Trend Vision One™
Trend Vision One™ is the only AI-powered enterprise cybersecurity platform that centralizes cyber risk exposure management and security operations, delivering robust layered protection across on-premises, hybrid, and multi-cloud environments.
Trend Vision One™ Threat Intelligence
To stay ahead of evolving threats, Trend Micro customers can access Trend Vision One™ Threat Insights, which provides the latest insights from Trend™ Research on emerging threats and threat actors.
Trend Vision One Threat Insights
Trend Vision One Intelligence Reports (IOC Sweeping)
Recommendations
DragonForce stands out for its aggressive affiliate program and ties with other ransomware operations, both defunct and active. Its trajectory suggests that it will continue to be a presence behind future attacks, showing how ransomware groups find ways to evolve and persist through new forms and services. Organizations should monitor its tactics and review standard measures to prevent attacks or minimize their impact.
The following are some best practices can help protect against ransomware attacks:
Audit and
inventory
- Take an inventory of assets and data
- Identify authorized and unauthorized devices and software
- Make an audit of event and incident logs
Configure and
monitor
- Manage hardware and software configurations
- Grant admin privileges and access only when necessary to an employee’s role
- Monitor network ports, protocols, and services
- Activate security configurations on network infrastructure devices such as firewalls and routers
- Establish a software allow list that only executes legitimate applications
Patch and
update
- Conduct regular vulnerability assessments
- Perform patching or virtual patching for operating systems and applications
- Update software and applications to their latest versions
Protect and
recover
- Implement data protection, backup, and recovery measures
- Enable multifactor authentication (MFA)
Secure and
defend
- Employ sandbox analysis to block malicious emails
- Deploy the latest versions of security solutions to all layers of the system, including email, endpoint, web, and network
- Detect early signs of an attack such as the presence of suspicious tools in the system
- Use advanced detection technologies such as those powered by AI and machine learning
Train and
test
- Regularly train and assess employees on security skills
- Conduct red-team exercises and penetration tests
Indicators of Compromise (IOCs)
The IOCs for this article can be found here. Actual indicators might vary per attack.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering



 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One