Malicious Ads Redirect to Flash Zero-Day Exploit, Affects Top Video-Sharing Site
 A double whammy for video buffs has been found in the wild. Trend Micro researchers found that the recently discovered Adobe Flash player zero-day vulnerability (CVE-2015-0313) is being abused by malicious advertisements used by a top video-sharing site, among other sites.
A double whammy for video buffs has been found in the wild. Trend Micro researchers found that the recently discovered Adobe Flash player zero-day vulnerability (CVE-2015-0313) is being abused by malicious advertisements used by a top video-sharing site, among other sites.
[Read: Trend Micro Discovers New Adobe Flash Zero-Day Exploit Used in Malvertisements]
Visitors of popular video-sharing site Daily Motion found themselves automatically redirected to a malicious website. Researchers noticed the uptick on traffic going to a malicious flash web page on January 27 and identified that malware is served through ads from Daily Motion's ad platform—not from Daily Motion itself—which are causing the redirection.
It’s not just Daily Motion site visitors who are at risk here. Given that the malicious ads were served by an advertising platform, users from other sites using the same platform could also be affected.
Zero-Day Exploit for Malvertising, an Agile Move
Cybercriminals have been known to use advertising networks to distribute malware, a technique known to the information industry as “malvertising.” Attacks like these usually lead to the download of malware or other threats.
[Read: Malvertising: Be Wary of Online Ads That Lead to Malicious Sites]
In this case, the flash web page that users are led to is not just another malicious page: it hosts the latest Adobe Flash zero-day exploit. A zero-day vulnerability is a previously unknown flaw in the software. It becomes a zero-day exploit when cybercriminals launch threats to abuse the flaw before the vendor (Adobe) releases a patch for it. Abusing these kinds of flaws can be more effective for cybercriminals as most users are still exposed.
The use of the Adobe Flash zero-day vulnerability together with auto-loading malicious ads is a particularly agile move for cybercriminals. This allows them to target exposed systems through a generally successful and anonymous technique. Note that, unlike other browser threats, this one does not need you to click or download anything to infect your system.
The graphic below shows how this recent Flash zero-day attack via malvertisement works:
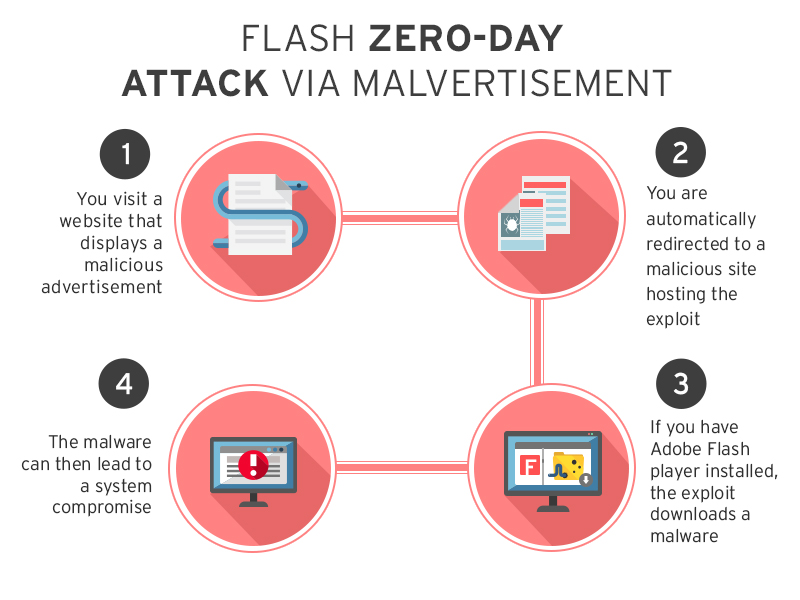
The latest Adobe Flash zero-day vulnerability affects users of the most recent version of Adobe Flash Player (16.0.0.296). Investigations are still being done to see which other versions of the player are affected.
What the cybercriminals do after they redirect malvertising victims and exploit the Flash zero-day vulnerability on their systems is still under close inspection.
Update: Adobe has released an update that addresses this critical vulnerability.
[More: Analysis of the latest Flash player zero-day vulnerability]
Update from the Security Intelligence Blog:
Analysis of the Adobe zero-day exploit has revealed that the exploit downloads and executes malware belonging to the BEDEP family. The malware's primary function is to turn infected systems into botnets that can be used for other malicious intentions, and is also known to carry out advertising fraud routines and downloading additional malware.
What Can You Do?
As Internet users, you can’t always be sure about the security of the sites you visit. At any given time, your favorite site can be used in a way that greatly affects you. This new zero-day exploit and the fact that it’s likely to be used in malvertising on other sites should be enough to consider disabling your Flash Player until a fixed version is released.
For enterprises to protect systems against malvertising ads that may be knowingly or unknowingly served on popular sites, one thing you can do is to choose security solutions that can proactively block browser exploits even while waiting for patches from vendors.Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One