The Internet of Everything: Layers, Protocols and Possible Attacks
 View infographic: Layers and Protocols: Possible Attacks on Internet of Everything
View infographic: Layers and Protocols: Possible Attacks on Internet of Everything
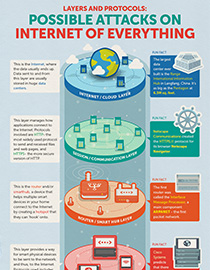
The Internet is an arrangement of connected, yet autonomous networks and devices. Each device, or host, uses protocols or set of rules in order to communicate with other devices within a network. Simply put, the Internet is used to send and receive information quickly between devices and people all around the world. While the Internet of Everything—or the concept that interconnects people, data, things and processes—is projected to play a rather large part in the future of technology, it still lacks development in terms of utility and security.
In 2012, the number of connected devices surpassed the human population. While some tech experts believe that the IoE still has to prove itself and that much credence is needed to baptize the concept into the present landscape, the number of smart devices is still projected to reach 50 billion by 2020. Additionally, as much as our enthusiasm bemuses industry players, we need to be aware that cybercriminals are also preparing to cast their nets toward relevant IoE vulnerabilities. But where do you stand in the web of all things?
Let’s say when you hit your favorite café; first thing’s first: you pull out your trusty device, whether it’s a laptop, tablet or phone, you enable your Internet connection and then go online. Once you’re connected, you’re entitled to a world of information where everything is virtually possible, and potentially dangerous. But it isn’t all just plug-and-play; communication between devices and networks involves a complex system of layers, protocols, and data. Since the language we use is vastly different from the language a computer uses, the messages need to be translated from alphabetic signals to a code that goes through several series of connections such as cloud layers, session, router, and link layers. If unsecured, these layers could be attacked and used as infection vectors by cybercriminals.
For example, a typical exchange between you and the cashier in the café would compose of you ordering a drink while the cashier ticks the specifics: tall double-shot macchiato, skimmed milk and no whipped cream. The cashier then passes your order to the barista but upon receiving your drink, you notice a huge dollop of whipped cream on your coffee. What went wrong? In order to execute a successful transaction, the communication between you, the cashier and the barista should begin and end with the right information. In this example, somewhere in the middle of the order, someone obviously made a mistake, botching the order altogether. The same goes with the Internet. To send and retrieve data, it must to go through certain network protocols, and for the message to rightfully end up on the Internet and for it to route back to your intended recipient, the data must be transmitted within the communication protocols.
Securing an entire IT infrastructure is hard enough but the IoE demands an even bigger security approach to keep endpoints and networks protected against more sophisticated cybercrime techniques and tools such as sniffer attacks, denial of service attacks, compromised-key attacks, password-based attacks, and man-in-the-middle attacks.
The adoption of the IoE is set to go upward and as we get more familiar with the smartification of devices, it’s time to increase our awareness and prepare to protect our privacy and security. View our infographic on IoE layers and protocols, and how they can be compromised.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One