The Cybercriminal Roots of Selling Online Gaming Currency
 View: The Cybercriminal Roots of Selling Online Gaming Currency
View: The Cybercriminal Roots of Selling Online Gaming Currency
Buying online game currency from third parties may sound relatively harmless—after all, it’s not illegal, the practice only involves virtual money used in an online game, and when all is said and done, it's hard to imagine it having any impact on the real world outside the game. Unfortunately, we found that the trade of online game currency could lead to serious real-world implications. Not only did we discover that
First, the
Many of these new online game currency websites are offering an experience similar to popular online shopping sites. Their proliferation and continued operation
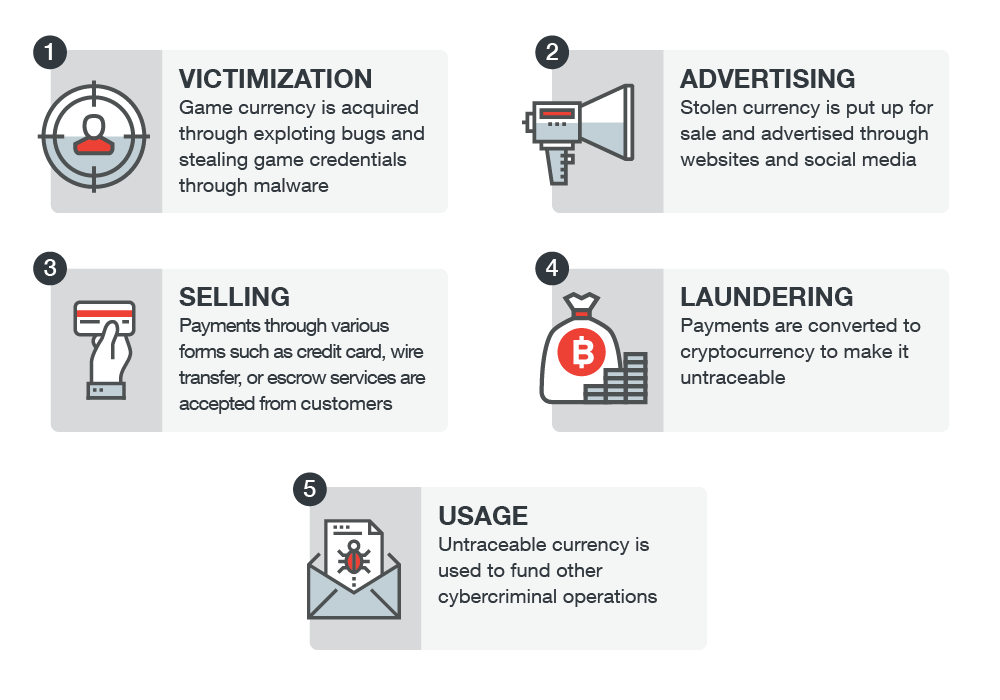
The impact of this cybercriminal activity goes beyond the gaming industry. Apart from negatively impacting the affected games’ economies, enterprises in other industries also get affected as they are the ones victimized by attacks funded by online gaming currency sales.
Online gamers should realize the real-world consequences of what they do, and consider that their decision to take shortcuts through obstacles (as opposed to working through them legitimately) may have a bigger impact. Cybercriminals will always continue to seek new revenue streams—legal and illegal—and turning a blind eye towards them in exchange for short-lived benefits could hurt us all in the long run, not just in-game but in real life.
Enterprises also must recognize this new revenue stream and take it as a sign that more attacks from malicious actors are inevitable, especially those fueled by this kind of service. Companies that are also involved with the games abused in such a manner should also move to address these websites and contribute to the effort of taking them down, or if not, simply to monitor them further for cybercriminal activity. Pushing local authorities to try and pass legislation to outlaw such practices can also help as well.
Read more in the research paper “The Cybercriminal Roots of Selling Online Gaming Currency.”
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One