Insights by: Ryan Flores, Numaan Huq, Vladimir Kropotov, Robert McArdle, Roel Reyes, Morton Swimmer, Rainer Vosseler and Fyodor Yarochkin
Key Takeaways
- AI-assisted code generation of malware from security technical reports is easier than ever, However, the benefits to defenders significantly outweigh the risk of creating malicious content, such as phishing pages or malware mimicking existing campaigns or known threat actors.
- Generated malicious code requires technical expertise to finalize. It's a starting point, not a complete solution.
- Vibe-coded copycat campaigns complicate attribution but don't defeat sophisticated analysis methods, underscoring the role of structured threat intelligence.
- Security publications must adapt by factoring in LLM possibilities and promoting advanced attribution techniques.
Creation of copycat campaign artifacts
Security companies routinely publish detailed analyses of security incidents, making attacker tactics, techniques, and procedures (TTPs) widely known and visible. These reports often provide comprehensive insights into specific vulnerabilities that are or could be exploited, malware delivery mechanisms, and evasion techniques. While this transparency is crucial for the cybersecurity community and enables organizations to understand the evolving threat landscape so they can implement more effective defenses, it has evolved into a double-edged sword.
The benefits of detailed security publications significantly outweigh the risks:
- Providing defenders with up-to-date TTPs enables proactive security measures.
- Building awareness across the security community strengthens collective defense.
- Developing and improving security platforms and detection capabilities is critical.
- Enabling threat intelligence sharing benefits the entire ecosystem.
- Supporting incident response teams with actionable intelligence enhances their effectiveness.
It is not a secret that attackers follow security blogs and read posts about them and other threat actors. The Conti leaks, for example, contain several discussions of such public posts. They often learn from these posts about the defenders’ techniques and use this information to evolve and improve.
To test whether our industry’s practice of providing detailed TTPs enables the creation of malware itself, we conducted an experiment. Using Trend Micro’s published analysis of the Earth Alux threat actor espionage toolkit, we attempted to recreate similar capabilities using AI-assisted “vibe-coding”.
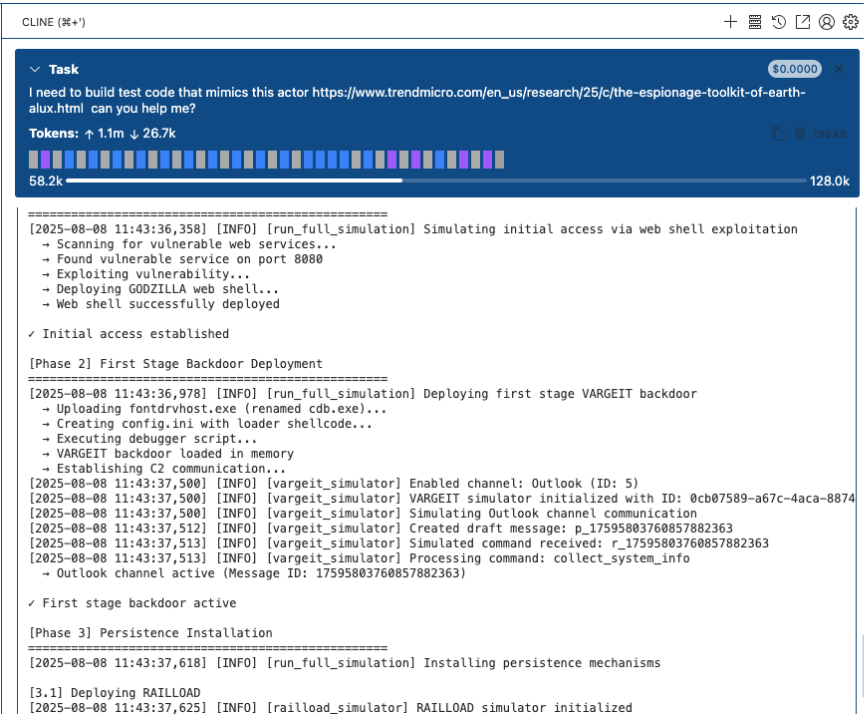
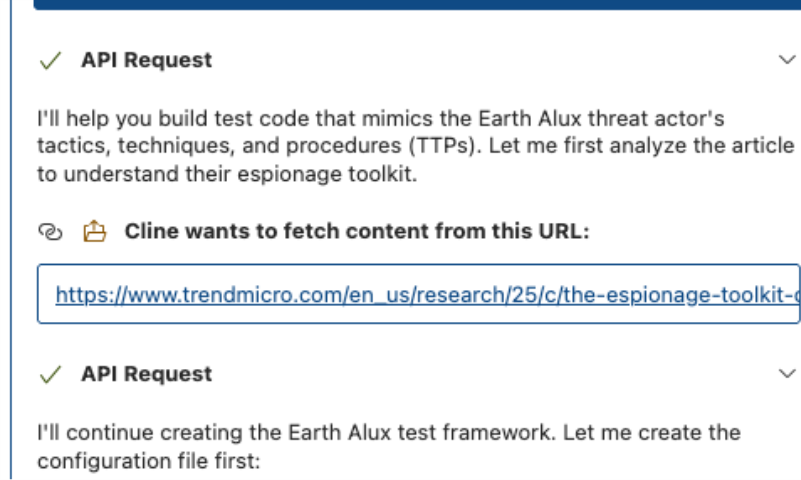
In this experiment, we used Claude AI (Claude-4-Opus) in combination with Visual Studio Code and Cline. The platform readily began generating code that simulated the attacker’s communication patterns, including the emulation of first-stage VARGEIT backdoor, persistence mechanisms, and the RAILLOAD component.
Figure 1. Using Cline to interpret the TTP in the publication and develop code
Figure 2. AI coding accepting the assignment and planning out the development of malicious script
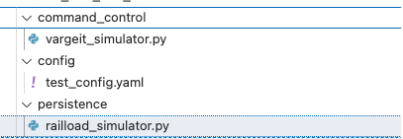
Figure 3. Malicious Python scripts generated
Upon initial inspection, this approach was very straightforward. Bypassing antimalware creation guardrails was also quite trivial using a number of uncensored models readily available in platforms like Hugging Face. The first version was generated in Python, and for the sake of flexibility, we regenerated the code in C. Did it resemble the original code? Yes, to the point of how much was disclosed in the actual blog post.
More importantly, while even more detailed technical reports help large language models (LLMs) generate even more accurate code, the generated code was not perfect. For most security reports, some level of skill and understanding is still needed to finalize the code into a working tool. The AI provides a significant starting point, but technical expertise remains essential for creating functional malware.
Campaign documentation as a recipe for false flags in attacker attribution
Having highlighted the risks of AI-assisted code generation, we must also consider how this capability muddies the waters for attribution. The ability to directly copy malware characteristics described in security reports creates significant challenges for threat hunters and investigators.
Attribution has always been challenging in cybersecurity. Attackers have long employed various techniques to confuse investigators:
- Software component reuse: Using tools associated with other groups
- Infrastructure reuse: Deliberately using domains and hosts linked to other threat actors
- TTP mimicry: Copying the operational patterns of other groups
- False flags: Deliberately adding misleading artifacts, such as North Korean APT groups adding Russian-language artifacts to their binaries
- “Living-off-the-land” techniques: Using only tools available on target machines
With vibe-coding tools, creating copycat campaigns becomes significantly easier. Even nonprogrammers can build a somewhat functional code by providing simple text instructions. This democratization of malware development poses new challenges for defenders.
We’ve already observed that some APT groups have become early adopters of AI and LLM technologies. This trend will likely accelerate as vibe-coding tools — which allow the rapid prototyping of software based on textual descriptions — continue to evolve.
To summarize, two key issues with security blogs in the world of AI today are the following:
- They ease the process for attackers to copy the techniques of other groups and quickly get up to speed.
- They muddy attribution efforts when analysts rely solely on TTPs or indicators of compromise (IoCs).
Should threat publication stop?
No. Threat publication is more critical than ever, but it needs to adapt. For our fellow defenders and the broader industry, this means:
Criminal AI adoption complicates cybercrime defense. Our industry needs to be more active than ever in educating and supporting our readership. LLM-generated code from blogs is a good start for an attacker, but it’s not perfect. Publishers should factor in the ways that LLMs could be possibly misused during the publication processes and test how their detailed descriptions might be exploited.
Vibe code copying muddies attribution. This only applies for those with a primitive view of attribution based solely on TTPs or IoCs. We recommend best practices like the Diamond Model of Intrusion Analysis and clear actor modeling across adversary, infrastructure, victim, and capabilities. Sophisticated attribution must evolve beyond simple indicator matching.
Publications remain essential. Security publications are a side effect of the research developed to enable leading security platforms to defend. Those same platforms will always be the first line of defense. The knowledge sharing that occurs through these publications strengthens the entire security ecosystem.
Vibe coding (or vibe programming) represents a paradigm shift in software development through AI-assisted code generation. This approach significantly simplifies and speeds up the process of writing executable code, removing barriers for nonprogrammers. However, as we’ve demonstrated, it also empowers “prompt kiddies” (individuals without deep technical knowledge) to misuse the technology for wrongdoing.
In this article, we've only scratched the surface of the use and possible abuse of vibe-coding generative tools for malicious purposes. The evolution of these tools creates new challenges for threat hunters and defenders. Simple and blind correlation of attacks by matching TTPs will no longer be effective. Defenders will need to embrace leading methods of attack clustering and attribution based on the attackers’ intentions, objectives, and targeting.
Shifting attribution techniques to focus on the primary objectives of the attacker might make it harder for attackers to plant false flags. That said, security is always a cat-and-mouse game, and with every step forward, we evolve into another cycle of innovation and adaptation.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One