badWPAD - The Lasting Menace of a Bad Protocol
 View badWPAD: The Lasting Legacy of a Bad Protocol
View badWPAD: The Lasting Legacy of a Bad Protocol
WPAD is a protocol that allows computers to automatically discover web proxy configurations and is primarily used in networks where clients are only allowed to communicate to the outside world through a proxy—which is the case in most enterprises. It was designed to provide automatic configuration to save time and resources. The WPAD protocol has been around for almost 20 years, but bears inherent risks. These risks have been recognized in the security community for some time, but were unfortunately left largely ignored.
In fact, it is relatively easy to exploit WPAD, which can lead to some serious security concerns for home and enterprise users alike. This sparked our interest and prompted us to carry out a few experiments of our own to test the potential promise WPAD holds for an attacker. The results of our experiments were quite surprising, making us firmly believe that WPAD is, in fact, badWPAD. BadWPAD is not a vulnerability—it is the consequence of an inherent design flaw that wasn't sufficiently addressed.
badWPAD: The Lasting Legacy of a Bad Protocol highlights the flaws inherent to WPAD to create the awareness it deserves. The research paper also describes how WPAD works and why it is a serious security concern, especially under the altered conditions in today’s connected world.
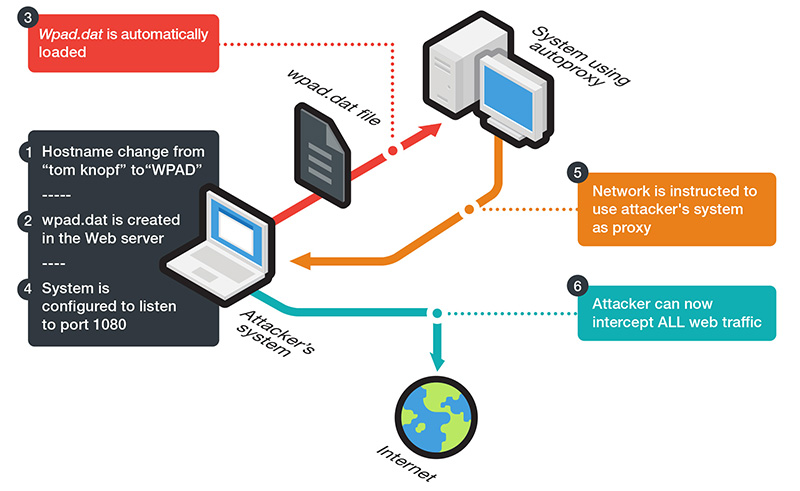
Figure1: Simple attack setup at the local level
Today's end users are more mobile, constantly moving or traveling, thereby connecting to different networks without being aware of the security implications. Even a typical employee may have multiple portable devices that indiscriminately connect to any available Wi-Fi network—from the airport lounge to the hotel wireless network, and then to the coffee shop around the corner. This paper also explores the implications of these new realities and looks at the ways in which WPAD can be exploited in local and public networks.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One