Banks in Peru Hit by Phishing Attack Using Bitcoin Advertisements as Lure
We came across an alert in the Peruvian media on August 17 regarding cyberattacks that were targeting banks in Peru. Discussions on social media platforms revolved around the attacks being a Distributed Denial of Service (DDoS) campaign, while others mentioned that it could have been ransomware.
From what we’ve observed, the campaign involves the use of phishing emails intended to lure victims via clickable links. In addition to Peru, phishing attempts were also seen in other countries, including Thailand, Malaysia, Indonesia, the USA, as well as other European and Asian countries.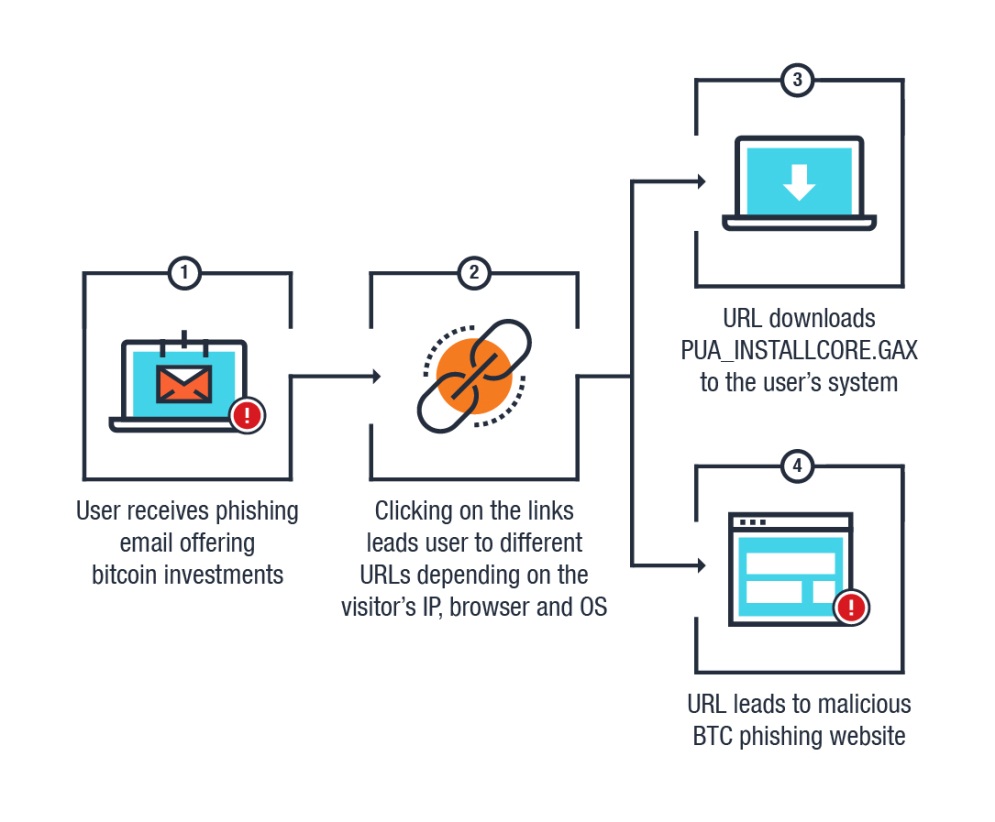
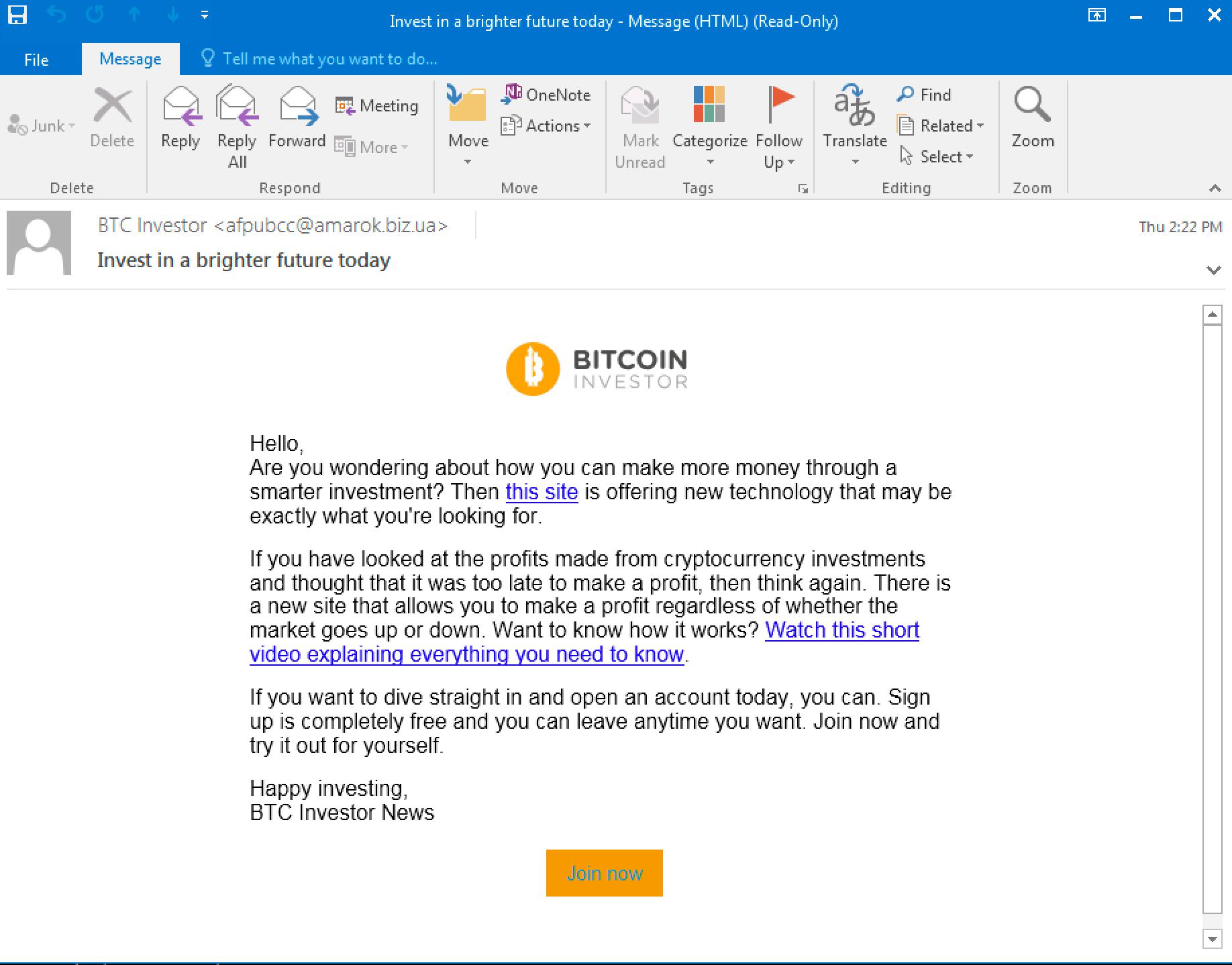
We found an email from a certain “BTC Investor News” inviting a target to invest in Bitcoin (BTC). The email had two links in the message body: one that redirected the user to a website offering “new technology,” while the other goes to a video explaining cryptocurrency investments. The address of the sender, seen in the screenshot below, does not appear to be legitimate.
The links in this phishing campaign point to the malicious domain matchtv[.]biz[.]ua. The URLs have the following pattern:
- http://matchtv[.]biz[.]ua/matchtv{XX/}
In this case, XX is a number, most likely used to track victims. When visited, the link then redirects the victims to different URLs depending on the user's IP location, browser, and operating system.
We accessed this URL multiples times and ended up with different results. The first time we accessed the URL, it led us to a suspicious file download, adobe_flash_setup_2956372845.exe (detected as PUA_INSTALLCORE.GAX)
Our analysis of this malicious file shows that it connects to the following command-and-control (C&C) server:
- http://dev.{ }sad-teh.com/
It then modifies Internet Explorer browsers, most likely to lead users to malicious websites as seen in our second example.
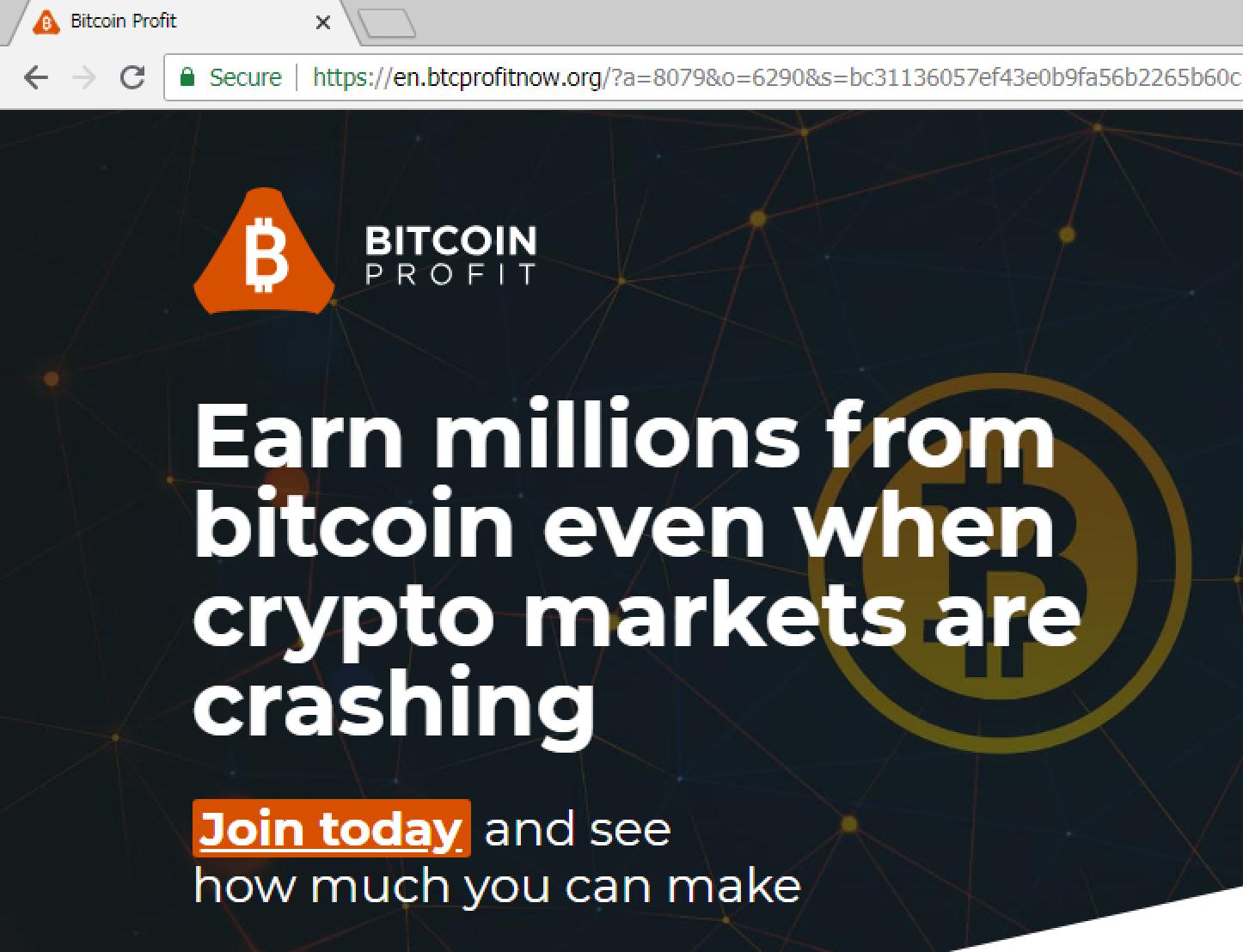
Accessing the URL the second time led us to what appears to be a malicious BTC phishing website.
Given what we know of the targets, it seems that these attacks might have a larger scope than just targeting Peruvian banks. Whether it’s part of a widespread campaign involving groups like Lazarus or related to another large campaign such as the supposed “ATM Cashout” that the FBI warned against earlier in August, remains to be seen.
Trend Micro Recommendations and Solutions
The effectiveness of phishing techniques in malicious attacks is well-documented. Therefore, it’s no surprise that even coordinated campaigns still use this relatively simple strategy, often combining it with “hot” topics such as cryptocurrencies to lure in targets.
Knowledge and awareness of phishing attacks play a large part in mitigating their effects and limiting their effectiveness. Users should always check the email for any red flags such as a suspicious sender address or multiple typographical errors in an “official” document. Furthermore, context should always be taken into account; for example, an invoice letter sent to the marketing team rather than the finance department should be a warning sign that the message might be a malicious one.
We also recommend that users avoid clicking on any links in an email unless they are certain of the source's legitimacy.
Organizations can also consider the use of Trend Micro XGen™ security, which provides a cross-generational blend of threat defense techniques against a full range of threats for data centers, cloud environments, networks, and endpoints.
It features high-fidelity machine learning to secure the gateway and endpoint data and applications, and protects physical, virtual, and cloud workloads. With capabilities like web/URL filtering, behavioral analysis, and custom sandboxing, XGen protects against today’s purpose-built threats that bypass traditional controls, exploit known, unknown, or undisclosed vulnerabilities, and either steal or encrypt personally identifiable data. Smart, optimized, and connected, XGen powers Trend Micro’s suite of security solutions: Hybrid Cloud Security, User Protection, and Network Defense.
Indicators of Compromise (IOCs)
URLs
- https://flare[.]draftsoftwaresets[.]win/?afgasd=MdPY0PcprjvQCaRkZQ2kTycIT47NXxmNcEA1m_B-Dp3b1NX95dGeGr4w06ppke1s4rVXeo_aSduf2KpQZeUnyA..&cid=kUS25GII0009OG1002S11B94H00MKLWF0TPC1VM568YA0G9L00MKL00&sid={channel_id}-{schannel_id}&v_id=4NHGmobEQSeGt-lV70gmxiwEwJgSt44g5Uhk1BD0t6I.
- http://matchtv[.]biz[.]ua/matchtvXX/ (where XX is a two-digit number)
Hashes (SHA-256)
Fake Adobe Flash Installation (Detected as PUA_INSTALLCORE.GAX)
- f6b379a624f67169d4b20d553a5a1aa02170a022f4ae909c0d5c3b27af27c8f4
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One