Why Do Attackers Target Industrial Control Systems?
Industrial Control Systems (ICS) are found everywhere–from automated machines that manufacture goods to an office building’s cooling system.
Previously, it was standard that ICS were based on specific OS and specific communication protocols. However, in recent years, system development costs have been reduced and productivity has been improved by implementing network connection based on general purpose OS and standard communication protocols.
To compete in today’s market-driven economy, businesses and organizations opt for efficient control systems that can automatically manage processes. ICS can be found in manufacturing, processing facilities, and even power plants–which play a vital role in running a country. On the other hand, the increased efficiency that ICS introduce also presents new problems on security. In reality, threat actors have much to gain when they attack such companies. A successful attack on ICS has serious impact on any organization. Some of these effects include operational shutdowns, damaged equipment, financial loss, intellectual property theft, and substantial health and safety risks.
Motivations for attacking ICS
Threat actors have different motives when choosing an enterprise to target. When carrying out attacks, these threat actors are often motivated by financial gain, political cause, or even a military objective. Attacks may be state-sponsored or they could also come from competitors, insiders with a malicious goal, and even hacktivists.
One of the earliest examples of an ICS attack happened in 2005 when 13 DaimlerChrystler U.S. car manufacturing plants went offline for nearly an hour. The main cause was Zotob PnP worm infections that exploited a Windows Plug and Play service. The total downtime has resulted in a backlog in production costing the company thousands of dollars. While the attack was not linked to an individual or a cybercriminal group, cybercriminals may also be hired by competitors who have much to gain from the damage caused by an attack.
How are ICS attacked?
The first stage of an attack against ICS usually involves reconnaissance that allows the attacker to survey the environment. The next step would be to employ different tactics that will help attackers gain a foothold in the target network. The strategies and tactics at this point are highly similar to a targeted attack. To launch a malware, an attacker will make use of all the possible vulnerabilities and specific configurations of an ICS. Once these vulnerabilities have been identified and exploited, the effects of an attack can cause changes to certain operations and functions or adjustments to the existing controls and/or configurations.1
The complexity of launching an attack on ICS depends on different factors, from the security of the system to the intended impact (e.g., a denial-of-service attack that disrupts the target ICS is easier to achieve than manipulating a service and concealing its immediate effects from the controllers). While there are already a lot of ways for attackers to damage an ICS, new tactics will continue to emerge as more and more devices are introduced to every ICS environment.
What vulnerabilities are exploited in ICS?
Since all ICS deal with both Information Technology (IT) and Operational Technology (OT), grouping vulnerabilities by categories assists in determining and implementing mitigation strategies. The National Institute for Standards and Technology’s (NIST) security guide for ICS divides these categories into issues related to policy and procedure, as well as vulnerabilities found in various platforms (e.g., hardware, operating systems, and ICS applications), and networks.2
|
Policy and Procedure Vulnerabilities |
|
|
Platform Configuration Vulnerabilities |
|
|
Platform Hardware Vulnerabilities |
|
|
Platform Software Vulnerabilities |
|
|
Malware Protection Vulnerabilities |
|
|
Network Configuration Vulnerabilities |
|
|
Network Hardware Vulnerabilities |
|
|
Network Perimeter Vulnerabilities |
|
|
Communication Vulnerabilities |
|
|
Wireless Connection Vulnerabilities |
|
|
Network Monitoring and Logging Vulnerabilities |
|
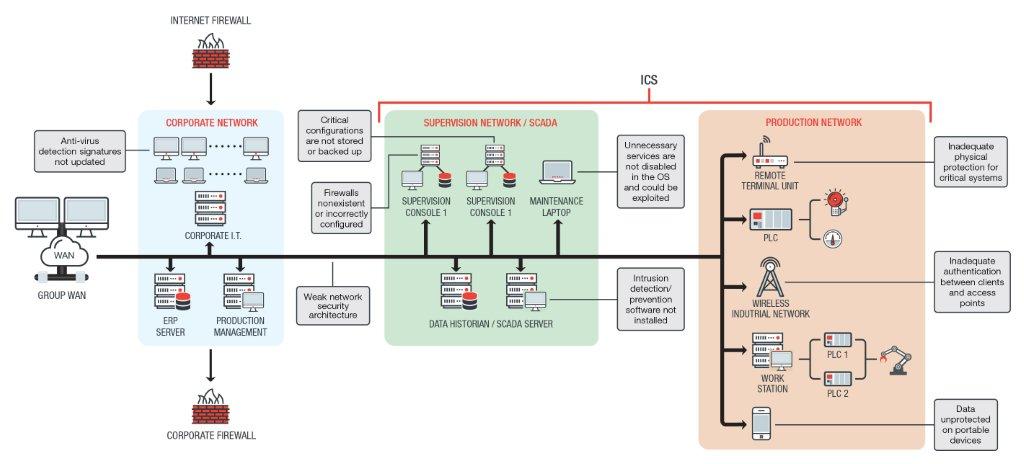 Possible weaknesses in ICS network
Possible weaknesses in ICS network
Every ICS environment may contain weaknesses depending on their configuration and their purpose. The size of an ICS environment can also be a factor–the bigger the environment, the greater the chance for an error to occur. An ICS environment that replaced its legacy system with modern systems and introduced tools like Industrial Internet of Things (IIoT) devices may also have more weaknesses for threat actors to exploit.
Industrial IoT and How It Affects ICS
As ICS continue to modernize, an increasing number of Internet of Things (IoT) devices are introduced to improve productivity and enhance system control. With the use of related IoT devices; process controls, data monitoring, and communication with other systems are made simpler. However, there are risks involved when smart devices are used for such tasks.
IIoT incorporates machine learning and big data analysis. It also harnesses sensor data, machine-to-machine (M2M) communication, and automation technologies that have previously existed in the industrial setting.3 IIoT can perform tasks such as data aggregation, predictive analysis, prescriptive analysis, data value addition, and even the creation of new business models.4
Similar to how the introduction of smart phones was followed by the rise of vulnerabilities and malware related to the platform, integrating Human Internet of Things (HIoT) and IIoT devices may create similar problems. In fact, managing IoT devices in the ICS environment can create major challenges in security, as each device will have to be properly defended and secured. Not applying adequate security leaves the entire ICS ecosystem highly vulnerable to attacks.
With the use of IIoT there are also a few unique challenges to overcome:
- Technology fragmentation complicates network processes. As devices of different and/or independent operating systems are used, the varying patching schedules may be difficult to address. An example of this is when an ICS uses a mix of legacy systems and new software. Not only will the two not communicate properly, the vulnerabilities found in unpatched legacy systems may also be used by threat actors to break into an ICS network.
- Machine to Machine (M2M) and IoT application development is difficult. Unlike manufacturing HIoT, which are mass produced, the development of M2M and IoT applications for ICS requires special skill sets on hardware and software development, IT, and communications.
- Legacy systems and legacy communication protocols are still widely used in industrial environments. An example of legacy systems is Windows 3.1, which still runs the program DECOR (used in Airplane takeoff and landing). Then there are also legacy communications protocols that include PROFIBUS, which is still widely used today. These systems have to be integrated via standards-based protocol gateways to send and receive data and commands easier.
Although hacking IoT devices may be challenging, threat actors behind targeted attacks are both knowledgeable and persistent–which could lead to successful breaches in a target’s network. In addition to this, device loss is also a major cause of data breach. One misplaced device may give cybercriminals the necessary access to penetrate the target’s network.
Potential Impact on ICS Components following Cyber Attacks
The impact of cyber attacks on industries using ICS depends on the target’s nature of operation or the motivation of cybercriminals pursuing the attack. Every effect listed below may be felt by a target’s internal, as well as external, clientele.
- Changes in a system, an operation system, or in application configurations. When systems are tampered with, it may produce unwanted or unpredictable results. This may be done to mask malware behavior or any malicious activity. This may also affect the output of a threat actor’s target.
- Change in Programmable Logic Controllers (PLC), Remote Terminal Units (RTU), and other controllers. Similar to a change in systems, a change in controller modules and other devices can lead to damaged equipment or facilities. This can also cause process malfunction and disabled controls over a process.
- Misinformation reported to operations. This scenario may lead to the implementation of unwanted or unnecessary actions due to wrong information. Such an event can result in a change in the programmable logics. This can also help hide malicious activity, which includes the incident itself or the injected code.
- Tampered safety controls. Preventing the proper operation of fail safes, and other safeguards puts the lives of employees, and possibly even external clients, at risk.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- Forecasting Future Outbreaks: A Behavioral and Predictive Approach to Proactive Cyber Risk Management
- Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report
- The Industrialization of Botnets: Automation and Scale as a New Threat Infrastructure
- From Holiday Snap to Custom Scam in 30 Minutes: How AI Turns Public Photos Into Targeted Attacks
- From LinkedIn to Tailored Attack in 30 Minutes: How AI Accelerates Target Profiling for Cybercrime

 Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report
Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One