Assess What You Know About Targeted Attacks
12 lutego 2013
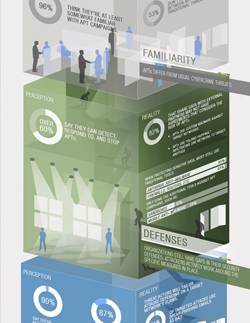 Download the infographic: Grounded in APT Facts
Download the infographic: Grounded in APT Facts
Comparing perceptions versus reality reveals the gaps in enterprise security strategies. For instance, many believe that social networking sites, BYOD, rooting, and jailbreaking spell trouble for IT professionals. However, research shows that most attackers actually choose spear phishing to try and get into a network.
If everyone with access to a company’s network takes the time to assess what they know and what they think they know, then it’s easier to develop a mindset prepared for any threat attackers may pose.
If an IT professional, for instance, is familiar with how to exactly catch all the tell-tale APT signs, he won’t only protect the network using traditional defense solutions like firewalls and free anti-malware. He will, instead, combine the traditional with the new—sandboxing, mobile anti-malware, and custom defense.
Review your targeted attack beliefs and perceptions with the enterprise preparedness infographic here.
HIDE

Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One