Critical Attacks Emphasize the Continuing Menace of Phishing
 Although phishing may seem out-of-date in light of the more sophisticated cybersecurity threats that make headlines today, it is still a credible threat. The newer methods used are still effective as adaptable techniques to mine key information, steal valuable assets, or even cause damage to critical infrastructure.
Although phishing may seem out-of-date in light of the more sophisticated cybersecurity threats that make headlines today, it is still a credible threat. The newer methods used are still effective as adaptable techniques to mine key information, steal valuable assets, or even cause damage to critical infrastructure.
Just a few weeks ago, an employee of cryptocurrency exchange Bithumb, the fourth-largest exchange in the world, was hacked. User information like contact numbers and email addresses were stolen—the phishing attacks that followed abused the stolen information but didn’t follow the usual tactics. Also this month, users of the cryptocurrency Ethereum were the focus of a scheme that targeted small user communities. According to reports, attackers used phishing tactics to collect US$700,000 in just six days.
Apart from the incidents revolving around cryptocurrency, there were persistent phishing campaigns against US energy facilities and critical infrastructures. These attacks were severe enough that the FBI and Homeland Security sent a general warning to the different facilities. Based on the analysis detailed in the reports, phishing emails were using an unusual technique to harvest credentials from targets.
To help users understand and defend against this adaptable threat, we’ve detailed the tactics and techniques involved in these recent attacks:
Voice phishing
Conventional phishing scams start with a spoofed email usually impersonating a trusted source that either asks for account information or leads the target to a malicious website. The previously mentioned Bithumb attacks reused an older tactic: voice phishing, or vishing. The attackers used the information stolen from the Bithumb employee to call the targets posing as Bithumb executives. On the pretense of a compromised account, they asked the targets for passwords and key security information related to the accounts. News accounts say that “billions of won” were lost (the exchange is based in South Korea).
Perhaps less familiar to users than online phishing, vishing is more reliant on social engineering than anything else—the success of the attack depends on how legitimate the caller sounds and how effectively he can manipulate the target. In this case, the effectivity of the tactic may be because of the information stolen from Bithumb—relaying correct account details make the caller sound more legitimate and trustworthy.
Forum phishing
Aside from vishing, another tactic used against cryptocurrency users was a more targeted version of the usual email tactic. This time, attackers sent phishing messages to small communities like the Ethereum subreddit and Slack forum. They impersonated community administrators and told the members to check their accounts because a popular Ethereum wallet was hacked. The attackers were able to phish the credentials of several members who fell for the ruse, allowing them to steal thousands of dollars in Ethereum. While some savvy users may be able to distinguish a phishing email from a legitimate one, phishing messages on forums and message boards may not be as easy to spot. In these small communities, users may feel safer since the content is somewhat curated by involved and informed members. A false sense of security might be at play in these situations, which could lead to members falling for the phishing messages.
Template injection attack
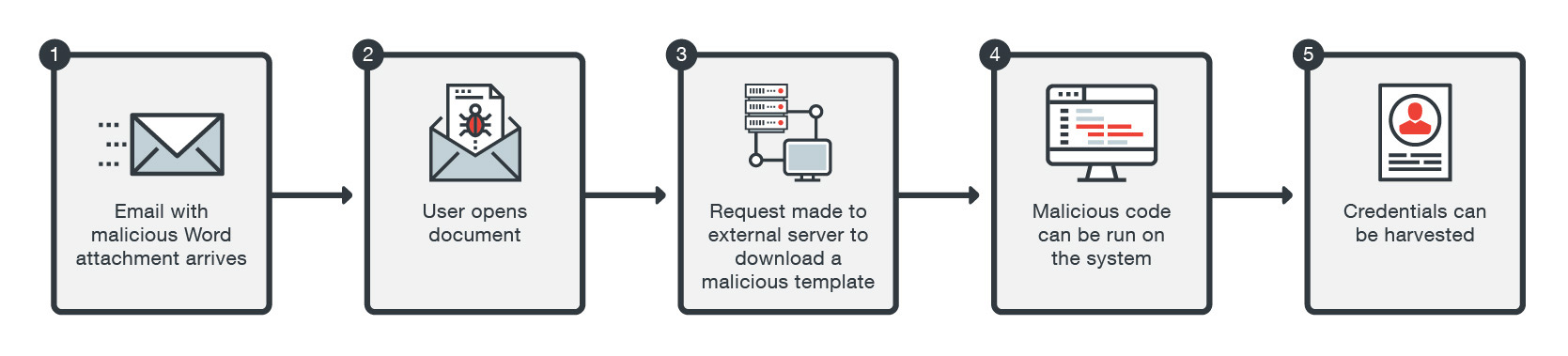
In the attacks against the US energy facilities, the actors revamped a typical phishing tactic—an email delivering a Word document embedded with a malicious macro. Instead of a macro, they used template injection, which is a relatively new tactic used in phishing schemes. Specific energy facilities were sent emails containing fake resumes or environmental reports in Word documents. If a user opens the document, a request is made via the Server Message Block (SMB) protocol to download a template file from an external server. If successful, attackers can silently harvest the user's credentials. The connection is made through TCP 445, a typical Microsoft networking port. Reports also say that there is a similarity to the methods used by Phishery, a known credential harvester that also uses template injection via Word documents. Since this is a newer tactic, users may not be aware that the Word document is downloading a template or connecting to a malicious server that is covertly harvesting their credentials.
Figure 1. Flow of a template injection attack
How to avoid phishing attacks
Phishing is still as effective as ever—the use of older techniques and revamped tactics contribute to the continuing success of these attacks. Some reports also say that users are now overconfident—thinking that they know what to expect and adopting a lax attitude that actually makes them more vulnerable.
The best any user can do is to be informed, alert, and prepared. To help, here are some basic guidelines on how to avoid and mitigate phishing attacks:
- In terms of vishing, always compare calls against the typical behavior of that service or organization, and also against industry standards. If anything seems unusual, don’t hesitate to drop the call and check other channels for more information.
- Network administrators should not allow outbound protocols such as SMB unless specifically required for the environment.
- Users should avoid downloading any attachments unless it's from a known, trusted, and verified source.
- Attachments that require an additional download or credentials to open them should be treated with suspicion.
- Users can use the built-in protection of their email clients to filter messages. One example is setting the email client to block all images unless approved.
- Trend Micro’s Global Site Safety Center helps customers manually check if URLs are malicious.
Trend Micro™ InterScan™ Messaging Security stops email threats in the cloud with global threat intelligence, protects your data with data loss prevention and encryption, and identifies targeted email attacks, ransomware, and APTs as part of the Trend Micro Network Defense Solution. The hybrid SaaS deployment combines the privacy and control of an on-premises virtual appliance with the proactive protection of a cloud-based pre-filter service.
Trend Micro™ Maximum Security provides multi-device protection so that users can freely and smoothly live out their digital lives. The product includes ransomware protection, blocks malicious links in email and IM, and provides anti-spam filters as well as effective anti-phishing features.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- The State of Criminal AI: Market Consolidation and Operational Reality
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One