In 2022, most businesses transitioned to a hybrid work model, an evolved version of the pandemic-prompted new normal in terms of work arrangements. With 68% of global employees preferring this work setup, organizations were quick to adapt to attract and retain top talent: 74% of employers offered hybrid work arrangements in 2022, including major companies such as HubSpot and Reddit.
The distributed nature of the workforce has pushed employees to collaborate and communicate online now more than ever. And despite the rise of various instant messaging and communication tools over the past decade, email remains popular as a communication medium. Unfortunately, it's also being increasingly used as an attack vector for malware distribution. In fact, in our 2022 annual security roundup, we reported that we have intercepted a total of 79,945,411,146 email threats.
This report delves into the notable email threats of 2022, including the 39,903,938 high-risk email threats we detected and blocked using the Trend Micro™ Cloud App Security.
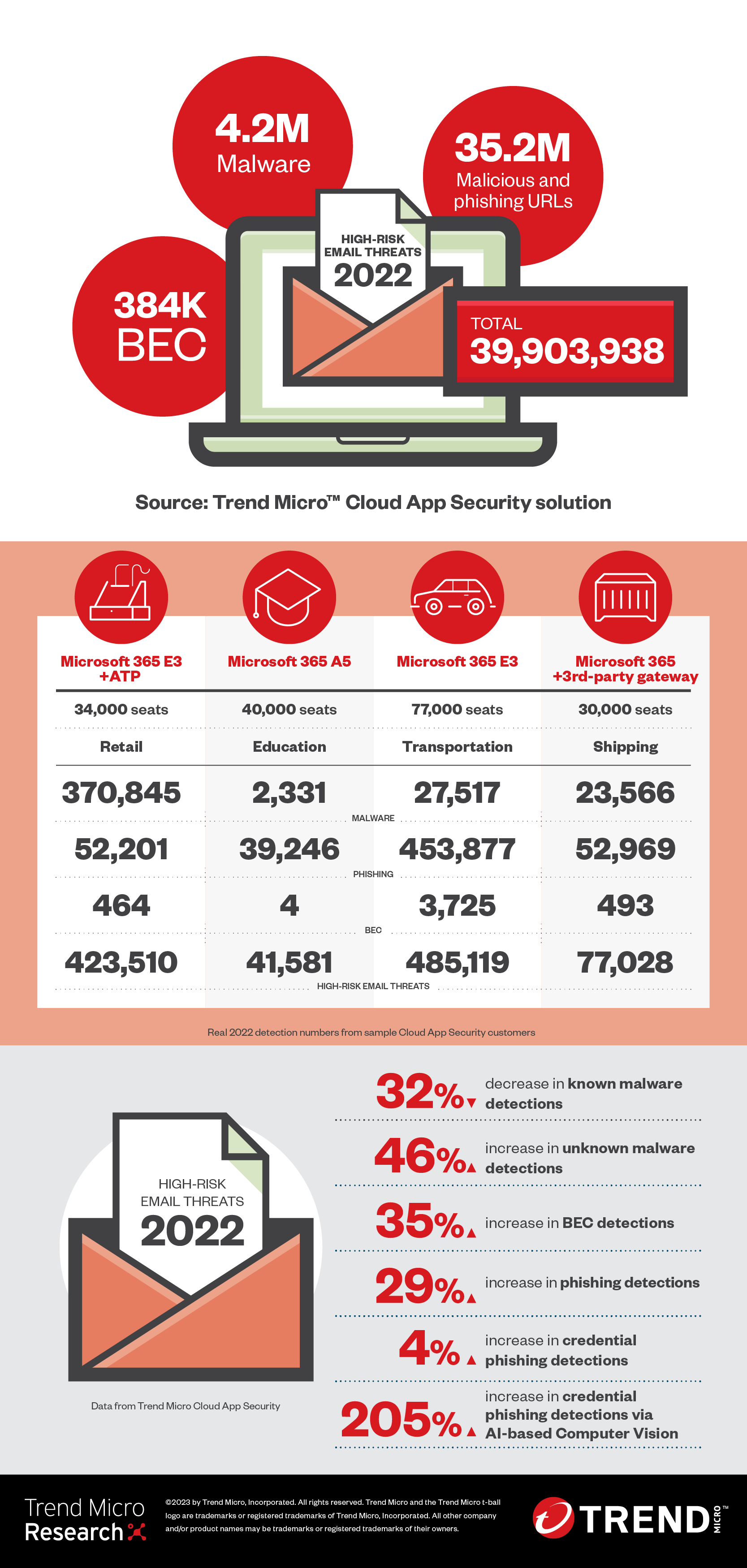
Overall malware detections, unknown malware detections spike
We detected and blocked 4,263,650 malware files in 2022, for a 29% increase from 2021’s numbers. The number of unknown malware files also surged to 3,757,812, for a 46% increase. However, it should be noted that the number of known malware files dropped to 505,838, a 32% decrease in detections.
Our security solution can catch, analyze, and block new and unknown malicious content (such as zero hour malware or URLs) used by threat actors. Unknown or newly created malware could be used by actors to evade detection or in customized attacks tailored to each victim. In fact, threat actors have been increasingly using custom malware in their attacks to target specific industries and sectors, such as government and military groups. We detected more than 3.7 million such threats in 2022, a leap from the 2.5 million detected in 2021.
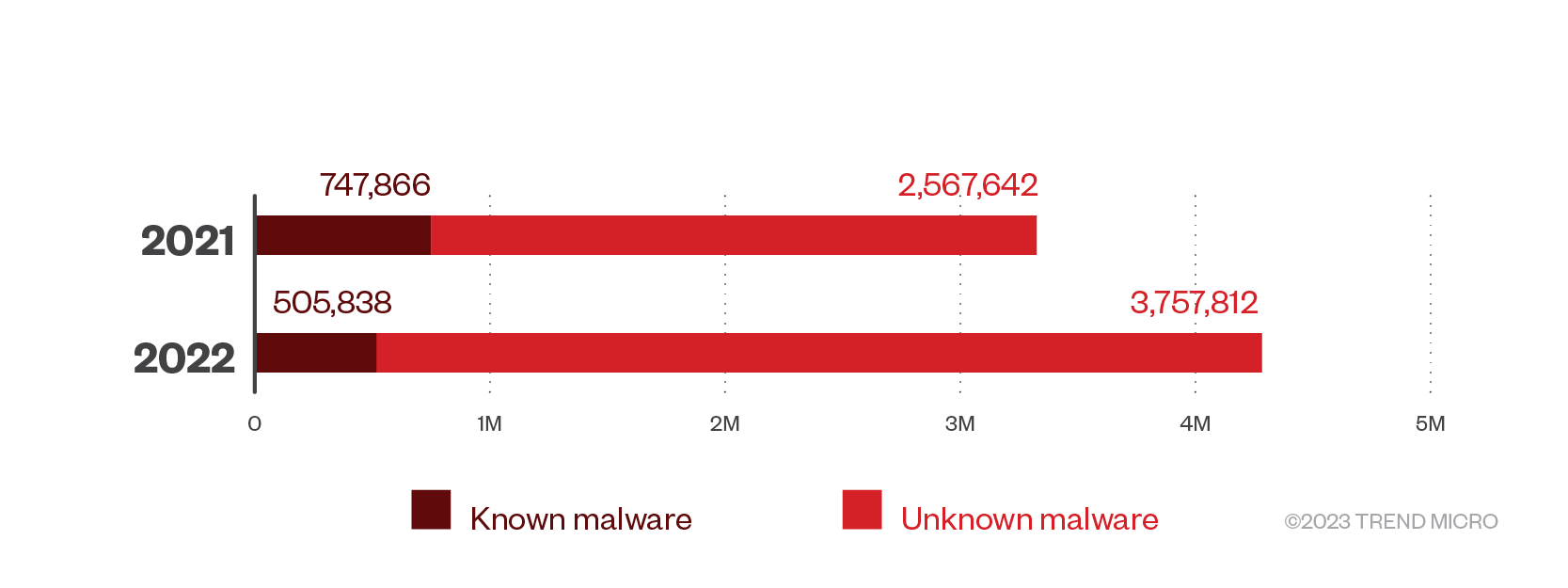
Figure 1. Known and unknown malware detections in 2021 and 2022
This decline can be attributed to a move made by Microsoft in mid-2022, where they blocked the execution of macro programs in Office documents, ones that have been downloaded from the internet, and those that are sent as email attachments. For the past seven years, the most popular initial access vector has been Microsoft Office documents laced with malicious macros, which are typically distributed to victims via email.
Malicious actors use HTML smuggling, fake Google accounts as macro alternatives
Because of this defensive move, cybercriminals resorted to finding malicious alternatives, such as HTML smuggling, an attack that is usually sent through email and uses a malicious HTML file to slip in a Zip file that contains an ISO file. The ISO file contains an LNK file that loads the malware.
Malicious actors had to evolve their social engineering tactics to successfully steal victims’ personal information. In December, we published a report on a social engineering scheme that made use of Trend Micro’s name in a legitimate PayPal payment request invoice (wherein the requestor was a random person’s name) and a prompt for victims to call a phone number to dispute the charges, only to be directed to scammers who will attempt to steal personal information.
Last year, we also reported on a large-scale cyberespionage campaign by an advanced persistent threat (APT) group called Earth Preta, which targeted different countries, including Japan and Australia. This campaign used spear-phishing emails with fake Google accounts and Google Drive links to distribute TONEINS, TONESHELL, and PUBLOAD.
Meanwhile, ransomware detections continued to plummet for the third consecutive year. In 2022, we detected 58,416 ransomware files, a decrease of 42% compared to the previous year’s numbers.
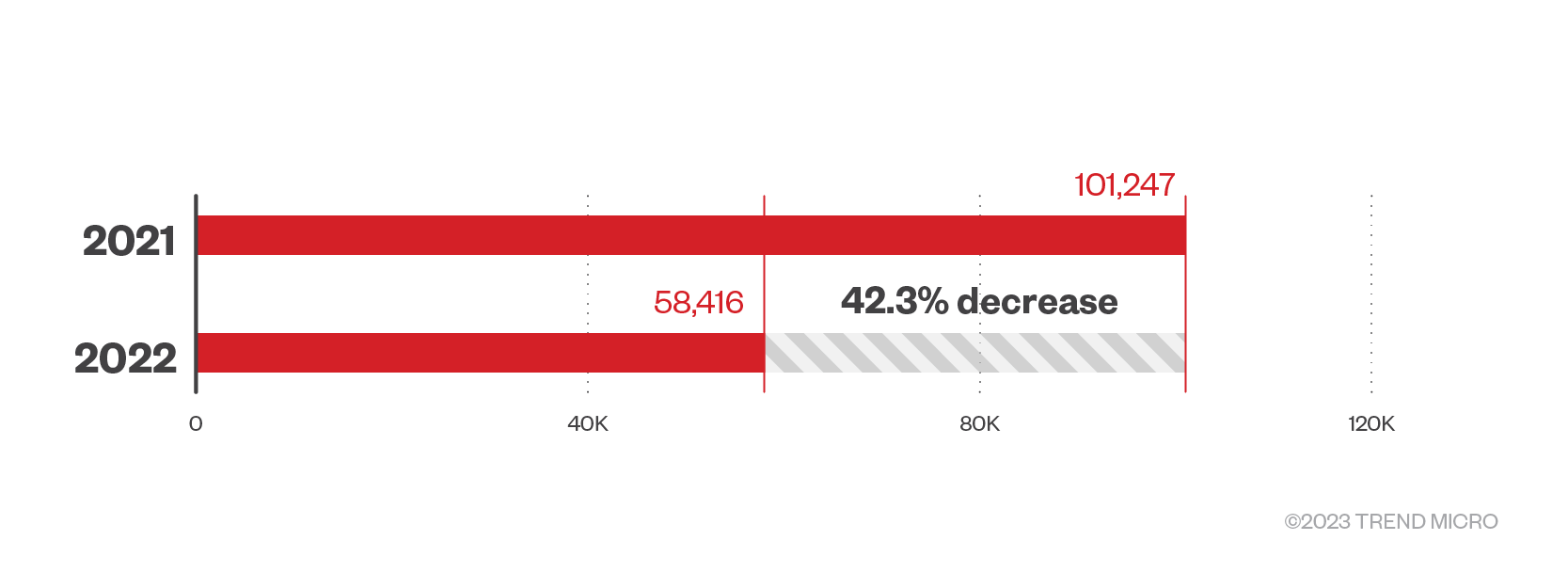
Figure 2. Ransomware detections in 2021 and 2022
There was a notable decrease in victim payouts last year. Ransomware actors countered this by adopting sophisticated business practices, including offering technical support to victims who opt to negotiate ransom amounts, to keep their businesses thriving.
Last year, we saw ransomware actors updating their payloads to have multiple capabilities. In June 2022, we reported on CMD-based ransomware variants, such as YourCyanide ransomware, that use heavily obfuscated scripts for detection evasion. These ransomware variants steal user information, bypass remote desktop connections, and propagate via email, Discord, Pastebin, Microsoft document links, and physical drives.
Toward the latter part of 2022, a new ransomware family dubbed Royal rose to infamy. Though relatively new to the ransomware scene, its operators are former members of Conti Team One, which are established ransomware actors. We found that it used intermittent encryption tactics and callback phishing techniques to lure victim corporations into installing remote desktop malware.
Known, unknown credential phishing attacks show slight growth, Computer Vision detections surge
We saw a 4% growth in overall credential phishing attacks in 2022, with 6,533,778 detections. This year, we also saw minimal growth for both known and unknown credential phishing detections at 1% and 2%, respectively.
Figure 3. Known and unknown credential phishing detections in 2021 and 2022
Meanwhile, we detected 239,777 credential phishing links via Computer Vision, which represent a 205% increase compared to the 78,556 detections found in 2021. Computer Vision is a technology that combines image analysis and machine learning (ML) to check branded elements, login forms, and other site content to detect credential phishing emails.
We can attribute this staggering increase in detections to the prevalence of fake login forms and landing pages in credential phishing attacks. In the fourth quarter of 2022, cybercriminals launched fake Twitter Services landing pages for credential phishing attacks. Malicious actors took advantage of the “blue check” status change at Twitter to trick unsuspecting victims into selecting a malware-laden link that promises to verify their accounts for free.
Last year, Armorblox also reported on another social media-related credential phishing campaign, one that targeted 22,000 students via a fake Instagram support email and a couple of fake landing pages designed to steal user credentials. This malicious campaign was able to bypass Microsoft’s preexisting security features and has passed Sender Policy Framework (SPF) and Domain-based Message Authentication, Reporting & Conformance (DMARC) email authentication checks.
BEC detections rise with improved tactics
Our telemetry shows that business email compromise (BEC) detections rose to 383,928 in 2022, a growth of 35%. The number of BEC attacks that were detected via Writing Style DNA reached 134,894, representing a 1% growth, while those detected via the anti-spam engine totaled 249,034, representing a massive 66% increase.
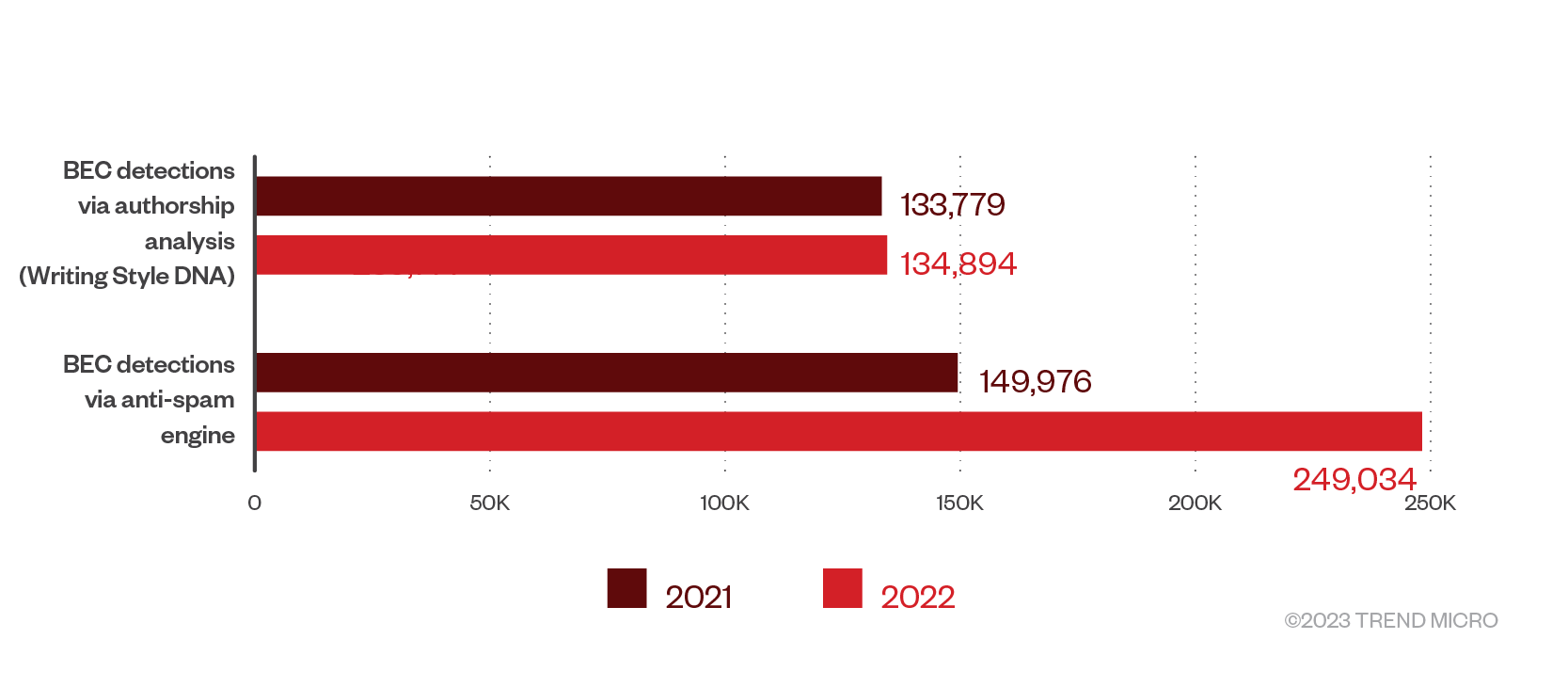
Figure 4. BEC detections via Writing Style DNA and anti-spam engine in 2021 and 2022
BEC, which heavily relies on social engineering or intrusion tactics, continues to be a very lucrative attack option for malicious actors. According to the 2022 Internet Crime Report of the FBI’s Internet Crime Complaint Center (IC3), the bureau received 21,832 BEC-related complaints with adjusted losses of over US$2.7 billion.
Cybercriminals have also started abusing new technologies such as deepfakes to increase their chances of fooling organizations and financial institutions for financial gain. An example of which happened in August 2022, when malicious actors created a deepfake hologram of a Binance executive to trick victims into attending meetings with the scammers.
BEC is also evolving because of new AI-powered technologies. Late last year, security analysts have also expressed concern about how OpenAI’s ChatGPT can help democratize cybercrime, allowing even the most inexperienced of malicious actors to get hold of compelling BEC and phishing email copies or even create malicious code.
Phishing detections increase with current events, political lures
Phishing remains a common attack method. In fact, 92% of organizations have succumbed to phishing attacks in 2022, according to a report by security company Egress.
We detected and blocked a total of 21,267,356 phishing attacks last year — a 29% increase compared to 2021’s detections. We also saw a 45% growth in phishing attacks detected via spam count in 2022, with 14,733,578 total detections.
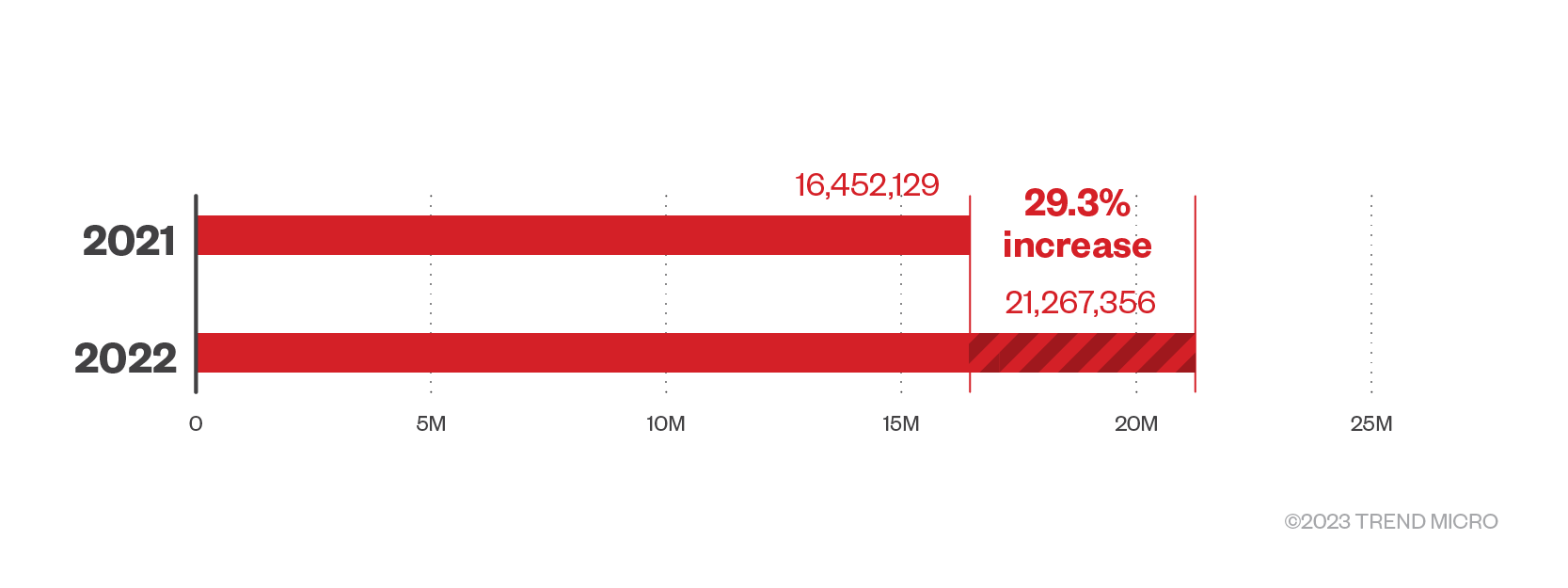
Figure 5. Phishing detections in 2021 and 2022
As Covid-19 restrictions eased in 2022, so did cybercriminals’ preference for Covid-19-related lures. In contrast to the slew of Covid-19 email and website scams we saw in 2021, last year, we saw malicious actors use a variety of decoys, including ones that involve cryptocurrency, charity, and even political instability.
Malicious actors took advantage of political tensions to impersonate charitable and humanitarian organizations to steal cryptocurrency. In one instance, cybercriminals pretended to be part of the Australian Council for International Affairs and requested for cryptocurrency donations. There were other scams that also banked on the international crisis: ones that attempted to cause panic, such as an unusual sign-in activity phishing scam emanating from Russia, and ones that tugged at the heartstrings of victims, including a fraudulent campaign that asks victims to donate to children fleeing political conflict.
Cybercriminals also launched attacks that targeted those who have non-fungible tokens (NFTs) and cryptocurrencies. Aside from fake NFT email offer scams, we also saw a MetaMask Ethereum update scam that attempted to trick users into clicking on a malicious link to “manually update their crypto wallets.”
Secure emails, endpoints, and cloud-based services and apps from threats and mitigate risks with Trend Micro Cloud App Security
Organizations should consider a comprehensive multilayered security solution such as Trend Micro Cloud App Security. It supplements the preexisting security features in email and collaboration platforms like Microsoft 365 and Google Workspace (formerly known as G Suite) by using ML to analyze and detect any suspicious content in the message body and attachments of an email. This security platform supplements Microsoft 365 or Gmail’s built-in security (such as Office 365 E5’s voice, analytics, security, and compliance services) and acts as a second layer of defense that can catch highly evasive and complex threats.
Trend Micro Cloud App Security uses technologies such as sandbox malware analysis, document exploit detection, and file, email, and web reputation technologies to detect malware hidden in Microsoft 365 or PDF documents. It provides data loss prevention (DLP) and advanced malware protection for Box, Dropbox, Google Drive, SharePoint Online, and OneDrive for Business while also enabling consistent DLP policies across multiple cloud-based applications. It also offers seamless integration with an organization’s existing cloud setup, preserving full user and administrator functionality, providing direct cloud-to-cloud integration through vendor APIs, and minimizing the need for additional resources by assessing threat risks before sandbox malware analysis.
Trend Micro Cloud App Security stands on the cutting edge of email and software-as-a-service (SaaS) security, offering ML-powered features that combat two of the primary email-based threats: BEC and credential phishing. Writing Style DNA can help determine if an email is legitimate by using ML to check a user’s writing style based on past emails and then comparing suspicious emails against it. Computer vision, on the other hand, combines image analysis and ML to check branded elements, login forms, and other site content. It then pools this information with site reputation elements and optical character recognition (OCR) to check for fake and malicious sites — all while reducing instances of false positives to detect credential phishing emails.
This security solution also comes with an option to rescan historical URLs in users' email metadata and perform continued remediation (automatically taking configured actions or restoring quarantined messages) using newer patterns updated by Web Reputation Services.
This is a significant option since users' email metadata might include undetected suspicious or dangerous URLs that have only recently been discovered. Thus, the examination of such metadata is an important part of forensic investigations that help determine if your email service has been affected by attacks. This solution also officially supports the Time-of-Click Protection feature to protect Exchange Online users against potential risks when they access URLs in incoming email messages.
Trend Micro Cloud App Security also comes with the advanced and extended security capabilities of Trend Micro XDR, providing investigation, detection, and response across your endpoints, email, and servers. Trend Micro Cloud App Security is part of Trend Micro’s Vision One, a security platform that enhances and consolidates detection, investigation, and response capabilities across email, endpoints, servers, cloud workloads, and networks.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One