Cybercriminals are Using Paid Ads to Get to Top Cloud Provider’s Customers
Here's a new twist on malvertising: Trend Micro threat analysts Dark Luo and Kenney Lu found that cybercriminals are using paid ads to victimize the customers of a top cloud provider.
[Read: Malicious ads redirect to flash zero-day exploit, affects top video-sharing site]
The top advertisement link triggered by the keywords ”Amazon Web Services,” “Amazon web console,” and “Amazon AWS” at the time of research redirected from the display link “aws.amazon.com” to an AWS phishing site when clicked, showing that they are targeting the login details of existing AWS customers.
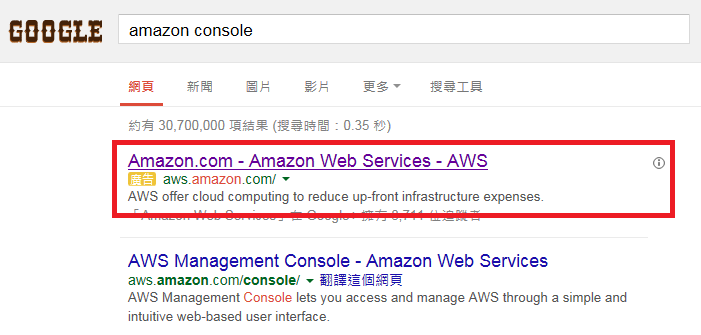
Paid Google ad that leads to phishing page
The infected ads lead to a phishing page with a URL that starts with “aws.amazon.com” to mimic the original Amazon Web services (AWS) Web page. Apart from the URL, the only difference is the Baidu icon found at the bottom of the page that was added to provide the attacker with reports about the site’s visitors.
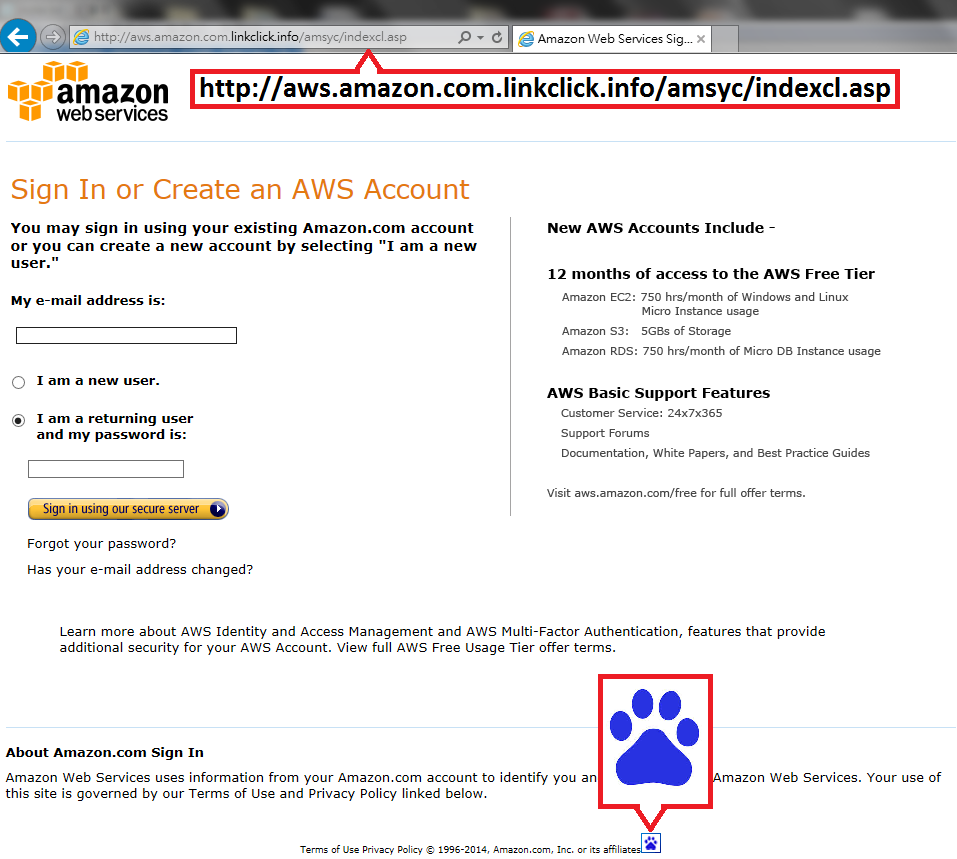
AWS phishing page
Luo and Lu notes that the page’s login form was modified so that any data provided by the site's visitors will be sent to the cybercriminals instead of Amazon.
The phishing page is registered under the name “Shang Xian” from Shanghai, China. Experts note that this is the same name used in phishing attacks against Amazon AWS and PayPal in February and March.
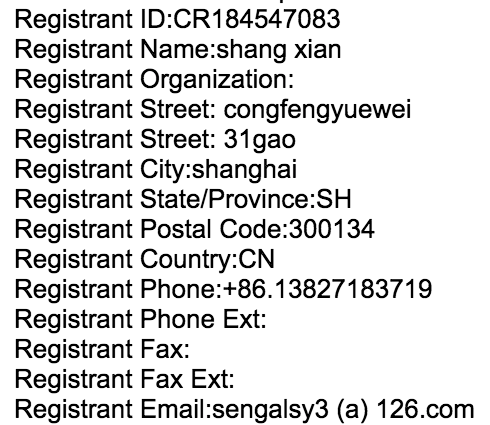
AWS phishing page WHOIS Information
Ads Will Rank, Even Malicious Ones
This threat is an outright abuse of the automated bidding and ad display process of Google’s ad network. It shows that cybercriminals who planned this are both knowledgeable on how exactly Google AdWords work and are willing to pay for the keyword bid. They are aware that advertisers only need to set up a Google AdWords account, set a clear budget for their chosen keywords, write the ads, and select where they would like them to appear to run ads.
[Read: Google AdWords phishing scam sent via email]
To own the top-ranking positions in legitimate keyword searches such as those mentioned, the scheme's operators have also shown that they know how to keep their “ad rank” competitive. For cybercriminals to nab the tap spot, they ensure that their ad and website are relevant to the keyword to get a high quality score (QS) or keep their bids high. Having a high QS virtually protects them from overbidding for their chosen keywords, so much so that they don’t even need to pay that much. Keeping their bids high compensates for a mediocre QS, while still allowing them to rank high on chosen keyword searches.
This abuse puts both Google searchers and advertisers in trouble. Customers of Amazon web products are at risk of data theft, should they mistakenly log into their AWS accounts in the phishing page. Given that AWS products are mostly for the enterprise, this can also be used to farm network login details. The broad range of sites that Google ads appear in also lets cybercriminals use the same method to get prime display spots from other legitimate advertisers.
Here are some best practices for Web users to be safe from this threat:
- Bookmark sites that house sensitive information or directly type the URL on the address bar to prevent being victimized by fake ads that lead to phishing sites.
- Before clicking on an ad, hover over it to check if the link is legitimate.
- When in doubt, double check links’ safety rating using the Trend Micro Site Safety Center.
[Read: How to spot bad links]
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization
- Agentic Edge AI: Development Tools and Workflows
- Ransomware Spotlight: DragonForce

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One