Rethinking Tactics: Annual Cybersecurity Roundup 2022
To combat waning ransomware revenues — a staggering 38% decrease from 2021 to 2022 — active ransomware actors have increased their level of professionalism to ensure higher ransomware payouts. In the past year, we’ve seen them take a page out of the corporate handbook to diversify, rebrand, and even offer professional services such as technical support, with the goal of keeping their attacks potent.
BlackCat ransomware actors have used their connections or networks with ransomware-as-a-service (RaaS) groups that have considerable experience in the industry to improve their operations.
In March and April 2022, Cuba ransomware operators offered technical support to victims who chose to negotiate and pay the ransom amount.
Conti, one of the most active and widely known ransomware families in recent years, shut down in mid-2022 and rebranded after being tagged as “toxic” because of its Russian ties. Former Conti members rebranded as new ransomware groups, namely Black Basta, BlackByte, Karakurt, and Royal.
LockBit 3.0 actors introduced the first ransomware bug bounty program in June 2022, which offered remuneration to security researchers who would submit vulnerability reports to help improve their operations.
In the latter part of 2022, we saw Agenda, BlackCat, Hive, and RansomExx actors develop versions of their ransomware in Rust, a cross-platform language that is harder to analyze and detect by antivirus engines, to target the Linux operating system.
Figure 1. Ransomware operating system (OS) comparison counts
Source: Trend Micro™ Smart Protection Network™
The top vulnerabilities of 2022 shifted from Microsoft-focused common vulnerabilities and exposures (CVEs) to Log4J CVEs. This is likely because malicious actors took advantage of several Log4J vulnerabilities that were publicized in 2021.
Table 1. The top three CVEs in 2021 and 2022
Source: Trend Micro ZDI
During the pandemic, businesses began depending more on virtual private networks (VPNs) for their remote and hybrid work needs, and cybercriminals were quick to take note and take advantage. Cybercriminals have set their sights on certain VPN vulnerabilities, a trend that we also covered in our 2022 midyear cybersecurity report.
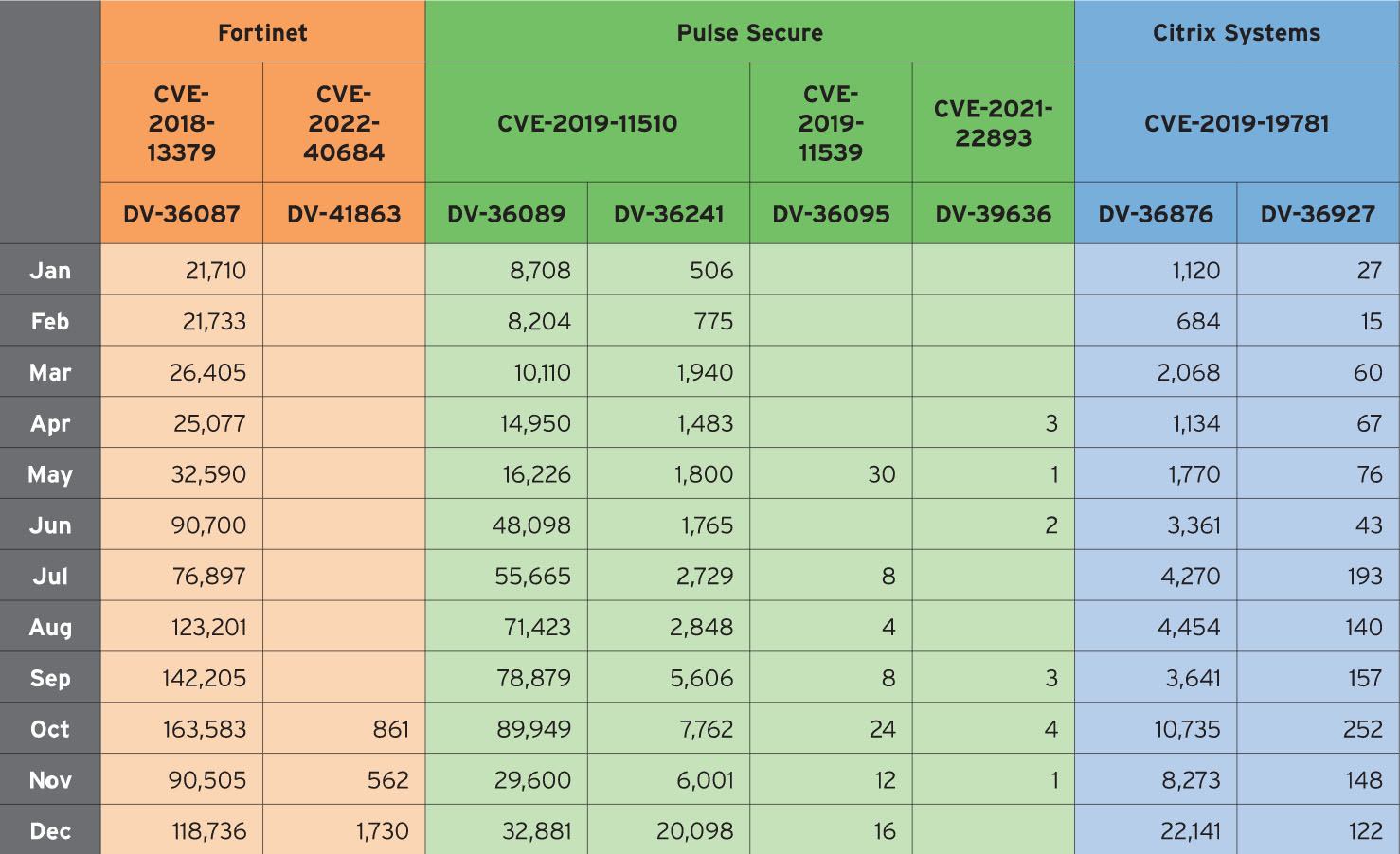
Table 2. A monthly record of detected attempts to exploit known VPN vulnerabilities
Top tracked vulnerability: CVE-2018-13379
A path traversal vulnerability in the FortiOS SSL VPN web portal that can allow unauthenticated attackers to download FortiOS system files via specially crafted HTTP resource requests.
The Trend Micro™ Zero Day Initiative™ (ZDI) also recorded their third record-breaking year in 2022 in terms of the number of published advisories. This can be attributed to two factors: an exponential increase in the attack surface and ZDI’s investment in automating analysis, which helped researchers find more bugs in 2022.
Figure 2. The number of published advisories by the ZDI program from 2020 to 2022
Source: Trend Micro ZDI
In 2022, the number of critical-, high-, and medium-severity CVEs increased compared to 2021. The number of critical bugs doubled in 2022 versus 2021, though it did not exceed the number of critical bugs in 2020.
Figure 3. The severity ratings of published CVEs from 2020 to 2021
Source: Trend Micro ZDI
After studying the vulnerabilities that ran rampant in 2022, we observed that there haven’t been any big shifts in the types of bugs. Instead, we saw a troubling trend — an increase in the number of incomplete or faulty patches.
Failed patches can come from:
146,408,535,569
Overall number of threats blocked in 2022
Blocked email threats
Blocked malicious URLs
Blocked malicious files
Email reputation queries
URL reputation queries
File reputation queries
Download our annual cybersecurity report to learn how to harden your cybersecurity defenses against sophisticated, expansive, and ever-evolving threats.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization
- Agentic Edge AI: Development Tools and Workflows


 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One