Security Technology Evolves With Endpoints
June 27, 2014
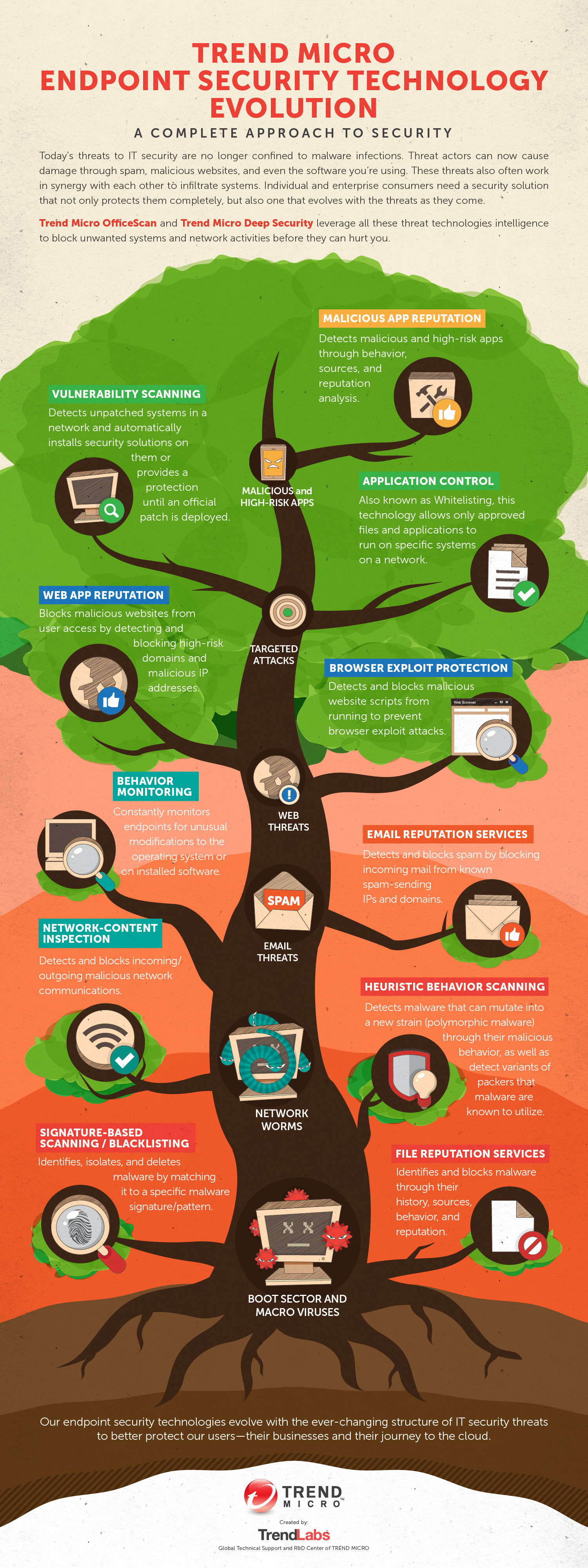
 View infographic: Trend Micro Endpoint Security Technology Evolution
View infographic: Trend Micro Endpoint Security Technology Evolution
The boom of office and home networks gave cybercriminals a larger attack surface brimming with data. Email and instant messaging opened up doors for them to get their foot into systems. And the Internet’s growing popularity gave them a whole new playground to explore. With it, they could reach just about anybody with a connection. They could, for example, use online domains to host malware or use webpages for phishing attacks. For a time, cybersecurity became a matter of blocking malicious files, webpages, and emails. That is, until mobility came into the picture.
Today’s mobile technology further expanded the reach of cybercriminals whose motivations have evolved over time. From being script kiddies who create viruses for fun, cybercriminals became sophisticated attackers targeting high-level organizations for big data and even bigger profits. This continuous progress of technology and threats is the reason why we owe it to ourselves to rethink our understanding of security.
Large enterprises need to be aware of the growing arsenal of threats at cybercriminals’ disposal. Unlike before—when network worms and other malware were already considered the biggest threat to businesses—an attacker can now use a wide array of threat combinations to get what they want in an organization’s network. They can use social engineering via email or social media to trick employees into divulging information. They can take advantage of the BYOD trend by infiltrating employee-owned devices through mobile malware. An employee’s honest mistake could turn the company’s security upside down. So you see, the need to protect against cybercrime requires much more than a one-off security solution.
Targeted attacks don’t just happen in a day; they occur throughout extended time periods. To prevent such attacks, organizations have to develop and establish control and preventive systems. They need to educate employees about threats and the underlying consequences these high-level attacks bring. They need to have security solutions in place. But ultimately, to meet the challenges of our ever-changing threat landscape, organizations need to take on a proactive and versatile security approach that is custom-fit and works across all the areas of their workspace.
HIDE
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Threat Attribution Framework: How TrendAI™ Applies Structure Over Speculation
- AI Skills as an Emerging Attack Surface in Critical Sectors: Enhanced Capabilities, New Risks
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One