Exploits & Vulnerabilities
Wordpress: Analyzing CVE-2019-8942 and CVE-2019-8943
This blog post expounds the technical details of the vulnerabilities CVE-2019-8942 and CVE-2019-8943, specifically, how a potential attack could look like and the parameters that are added to take advantage of a vulnerable WordPress site."
With its open-source, feature-rich, and user-friendly content management system (CMS), WordPress powers nearly 33 percent of today’s websites. This popularity is also what makes them an obvious cybercriminal target. All it could take is a vulnerability to gain a foothold on a website’s sensitive data. This could be compounded by security issues that can be brought by outdated websites or use of unsecure third-party plugins or components.
On February 19, 2019, Simon Scannell of RIPS Technologies published his findings on core vulnerabilities in WordPress that can lead to remote code execution (RCE). These have been assigned as CVE-2019-8942 and CVE-2019-8943. In a nutshell, these security flaws, when successfully exploited, could enable attackers with at least author privileges to execute hypertext preprocessor (PHP) code and gain full system control. Affected versions of WordPress include versions 5 (prior to 5.0.1) and 4 (prior to 4.9.9). The vulnerabilities have also been disclosed to WordPress’ security team.
This blog post expounds the technical details of the vulnerabilities, specifically, how a potential attack could look like and the parameters that are added to take advantage of a vulnerable WordPress site.
Vulnerability analysis and attack chain
An attacker with author privileges can upload PHP code embedded in an image file to a WordPress site. The uploaded file will get saved in the wp-content/uploads folder; an entry of this file will also be saved in the database’s postmeta table.
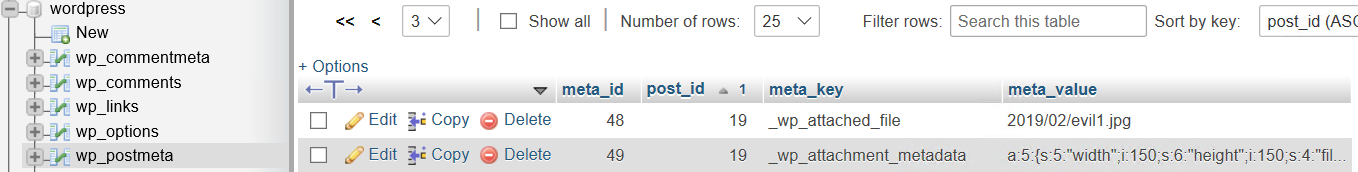 Figure 1. Screenshot showing how CVE-2019-8942 could be exploited
Figure 1. Screenshot showing how CVE-2019-8942 could be exploited
By exploiting CVE-2019-8942, an attacker can modify the _wp_attached_file meta_key (used to retrieve a value saved from the database and display it) to an arbitrary value. Exploiting the vulnerability requires sending the crafted post an edit request. A benign request typically would not have a file parameter in the request. An attacker-crafted request can have a file parameter that allows hackers to update the _wp_attached_file meta_key. As shown in Figure 3, the same can also be observed in the database table.
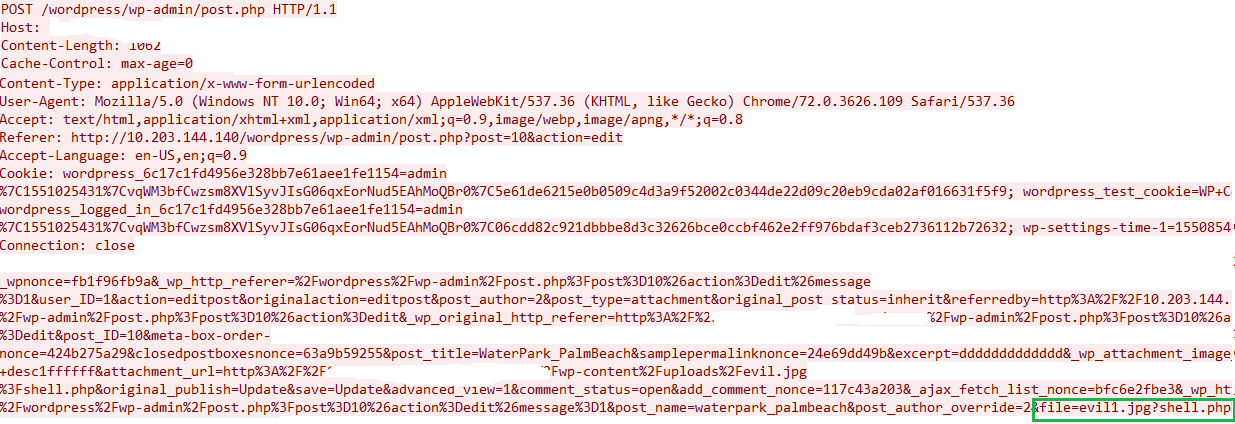 Figure 2. Screenshot showing how an especially crafted PHP file is embedded (highlighted)
Figure 2. Screenshot showing how an especially crafted PHP file is embedded (highlighted)
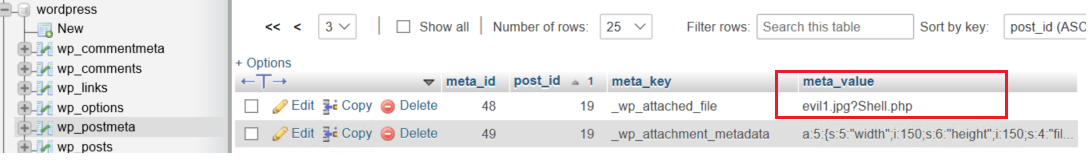 Figure 3. Screenshot showing a modified file name in the database (highlighted)
Figure 3. Screenshot showing a modified file name in the database (highlighted)
Patched versions of WordPress (before 4.9.9 and 5.0.1) do not have checks to validate which MetaData fields are going to get updated through a request. Attackers could take advantage of this to update or alter the _wp_attached_file meta_key value to an arbitrary one.
In the patched versions, the new function _wp_get_allowed_postdata() in admin/includes/post.php was added to check if “file”, “meta_input” or “guid” are sent in the edit request and removed before updating the POST request. Figure 3 shows that exploiting CVE-2019-8942 can let hackers modify the file name in the database akin to a path traversal (e.g., evil1.jpg?../and ../evil1.jpg).
An attacker can chain the exploit of CVE-2019-8942 with another, this time exploiting CVE-2019-8943. The latter can let attackers move the uploaded file to an arbitrary directory where the embedded PHP code can get executed successfully.
Figure 4 shows what CVE-2019-8943 entails. In the wp_crop_image function (which lets WordPress users crop images to a given size or resolution) in wp-admin/includes/image.php doesn’t validate the .dst (a drawing sheet file) file path before the saving the file.
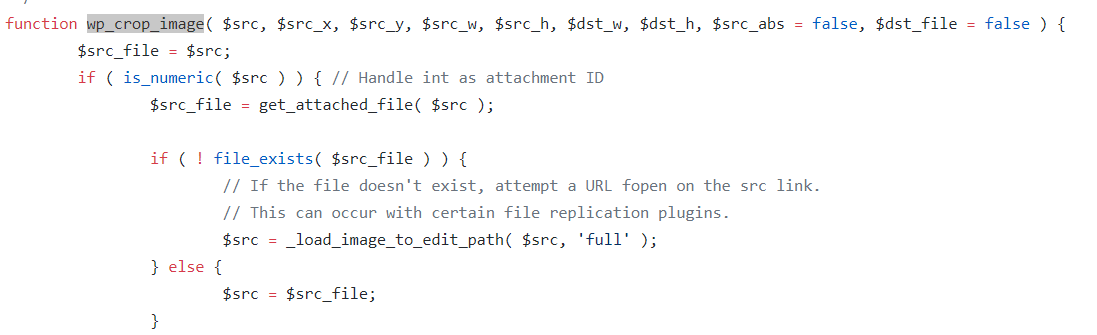 Figure 4. Screenshot showing the wp_crop_image function not validating .dst file path
Figure 4. Screenshot showing the wp_crop_image function not validating .dst file path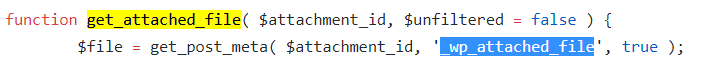
Figure 5. How the wp_crop_image function tries to access the file locally
In a possible attack scenario, once the file name in meta_key is modified, the file (e.g., evil1.jpg?../../evil1.jpg in Figure 3) will not be found in the upload directory. Hence, it will fall back to the next If condition in the wp_crop_image function where it will try to access the file by URL. It requires file replication plugins to be installed in the WordPress site. The request will look something like this:
hxxps[:]//vulenrablewesbite/wp-content/uploads/evil1.jpg?../../evil1.jpg
While loading the image, it will ignore the path after “?” and the image will be loaded successfully. An attacker will crop the image, and while saving, it will follow the path traversal and save it in an arbitrary directory.
Caveats and best practices
Patching CVE-2019-8942 makes CVE-2019-8943 non-exploitable, as the former plays an essential part in successfully exploiting the latter. That’s because the meta_key in _wp_attached_file first needs to be updated or modified to a path traversal file name before it can execute an embedded PHP code.
More importantly, these vulnerabilities highlight the importance for developers to practice security by design, and for administrators to adopt security hygiene to reduce their website’s attack surface. Regularly update the CMS or employ virtual patching to address vulnerabilities for which patches are not yet available and on systems that need to be constantly up and running. Consistently vet the website and its infrastructure or components against exploitable vulnerabilities. Enforce the principle of least privilege, and disable or delete outdated or vulnerable plugins.
The Trend Micro Deep Security™ solution protects user systems from threats that might exploit CVE-2019-8942 and CVE-2019-8943 via the following deep packet inspection (DPI) rules:
- 1005933 - Identified Directory Traversal Sequence In Uri Query
- 1009544 - WordPress Image Remote Code Execution Vulnerability (CVE-2019-8942)
Trend Micro™ TippingPoint™ customers are protected from these vulnerabilities via this MainlineDV filter:
- 34573 - HTTP: WordPress Image Remote Code Execution Vulnerability
- 34578 - HTTP: WordPress Image Remote Code Execution Vulnerability
Updated as of February 27, 2018, 5:20 PM PDT to update the description of TippinPoint MainlineDV filter 34573.

