APT & Targeted Attacks
Threat Intelligence Sweeping now supports container security telemetry data
Threat Intelligence Sweeping starts to support sweep container security telemetry data. Users can now use the TI tool to identify possible malicious activity in their container-based environments. The trigger events are visible in workbench alert.
In a threat landscape that changes daily, security teams need more than alerts — they need intelligence that drives fast, confident action. With increasingly sophisticated attacks targeting endpoints, servers, cloud workloads, and containers, it's essential to move from reactive defense to real-time, intelligence-led proactive security.
Trend Vision One™ – Threat Intelligence empowers organizations to identify potential past attacks proactively. This process helps organizations detect threats that may have been missed by real-time detection systems and provides actionable insights for incident response which based on overall trend threat knowledge.
Retrospective scan to identify possible attacks
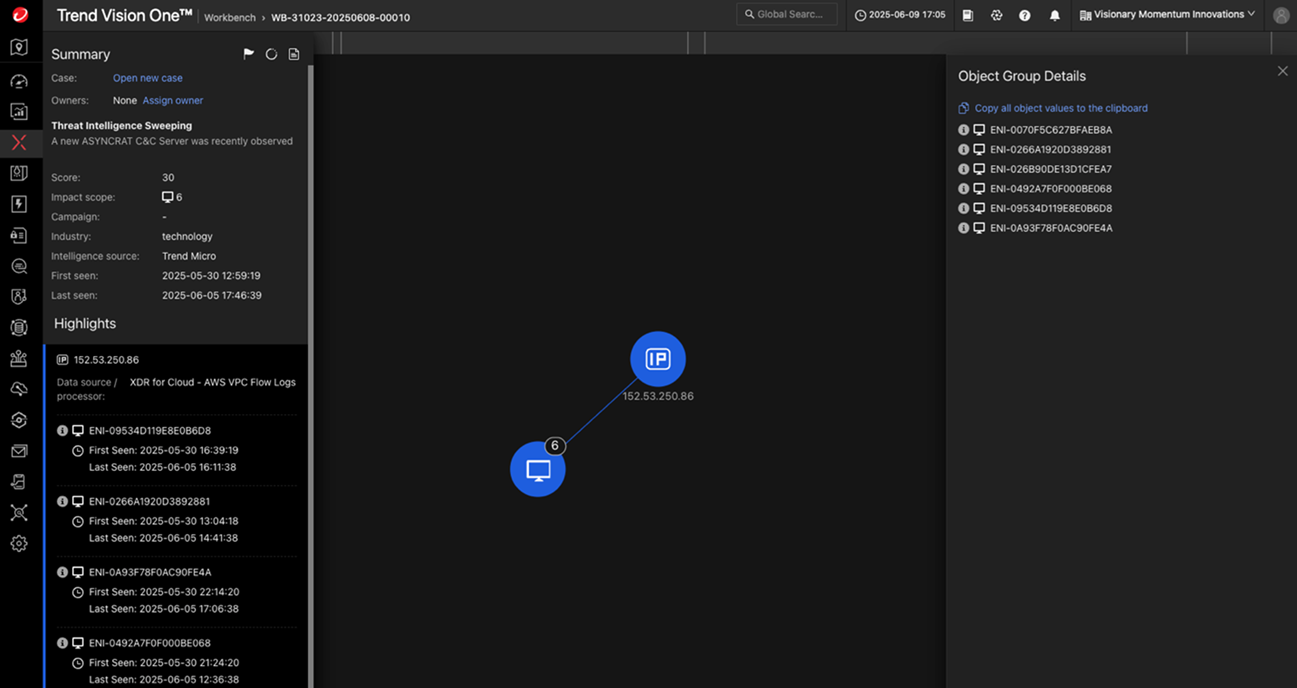
By combining real-time detection with retrospective analysis, security teams gain a broader view of threat activity, leveraging Trend’s global threat research, MITRE ATT&CK mapping, and built-in retrospective scanning to uncover hidden or dormant threats that could indicate prior compromise. One standout feature of Threat Intelligence is its ability to trace the network's activities to containers. This real-time visibility allows teams to:
- Identify unusual or unauthorized communications
- Trace connections to known malicious IPs or domains
- Detect potential command-and-control (C2) traffic or exfiltration attempts
By actively mapping communication flows and comparing them against a threat intelligence database, Trend Vision One reduces the time it takes to detect container-based threats and limits attacker dwell time — a key pillar of modern Zero Trust architectures.
Automated Investigations & Custom Intelligence Sweeping
The Threat Insights application serves as the primary interface for operationalizing Trend Threat Intelligence within the Trend Vision One platform. It provides a centralized, contextualized view of malicious activity across endpoints, servers, cloud workloads, and containers—all in a single dashboard, powered by Trend Micro’s vast global threat expertise.
Threat Insights enables security teams to quickly identify suspicious events, correlate indicators of compromise (IOCs) with known threat campaigns, and understand the potential impact of ongoing or retroactive attacks. It also integrates tactical and strategic intelligence, enabling proactive hunting and faster decisions in incident response.
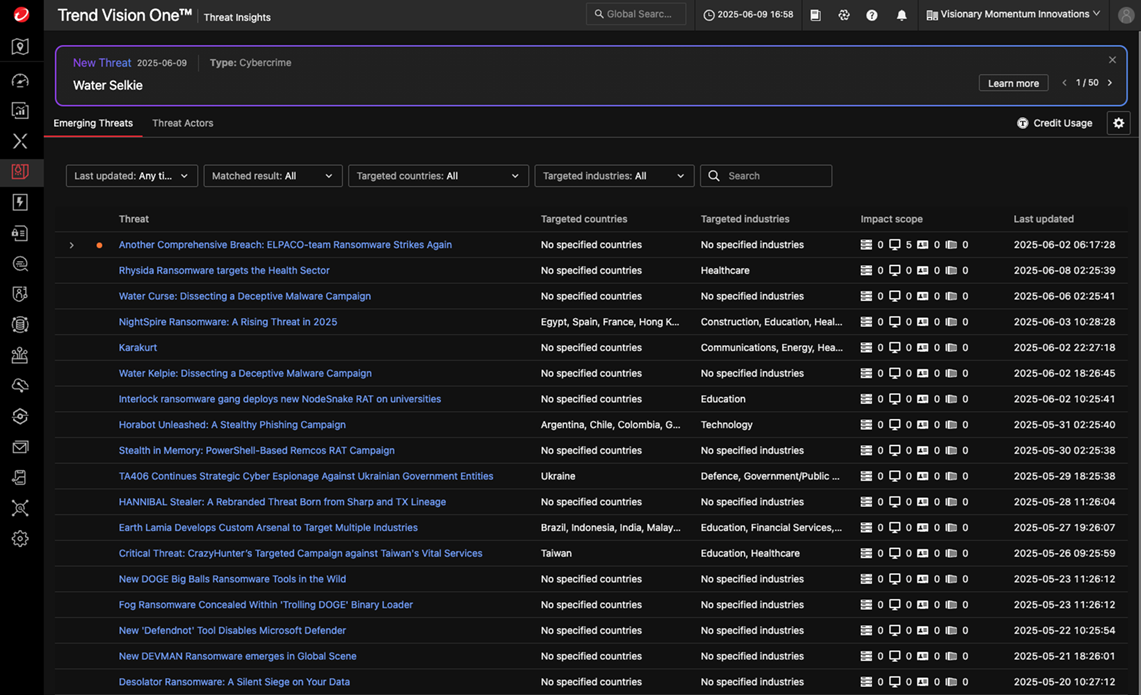
With this application, the value of Trend Micro’s Threat Intelligence becomes tangible: instead of dealing with siloed alerts, organizations gain a deeper understanding of the “why” and “how” of each threat, empowering their teams to act more accurately and effectively. With Threat Insights, manual investigations have become a thing of the past. The platform automates threat triage by combining:
- Real-time malware analysis
- IoC-based threat lookups
- Custom and third-party threat feeds
This allows teams to automatically sweep the environment for relevant indicators, prioritize what matters, and kick off guided investigations with far less time and effort. It also enhances threat hunting, giving analysts deeper control with less guesswork.
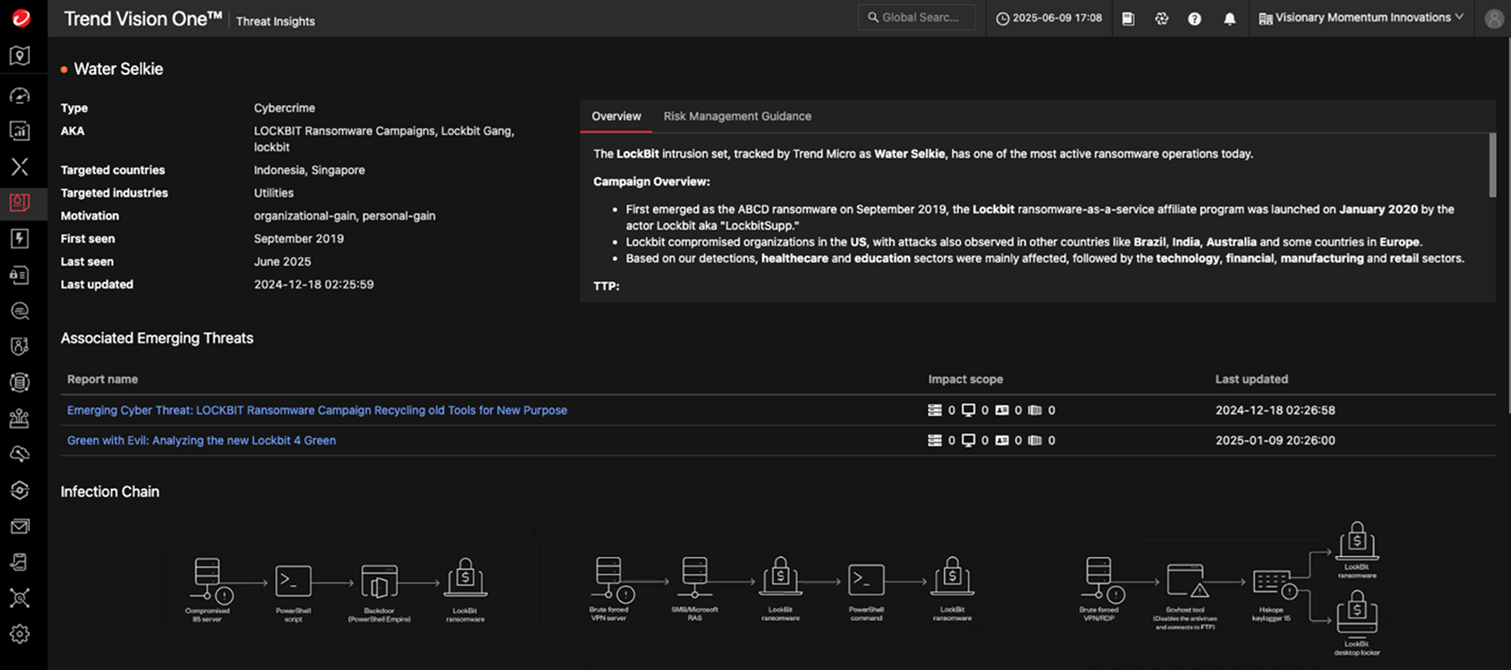
Operational Threat Intelligence with Real-World Impact
In today’s dynamic threat landscape, security teams must go beyond isolated alerts and pivot to intelligence-driven action. Threat Insights, a core application within the Trend Vision One™ platform, delivers real-time, operational threat intelligence that enables faster, more confident response across your entire attack surface.
Integrated natively with Trend Vision One’s XDR capabilities, Threat Insights empowers SOC teams to understand, prioritize, and respond to threats based on rich, contextual data — not just signatures or rules.
Before diving into use cases like phishing investigations or zero-day analysis, it’s important to highlight the core benefits Threat Insights brings:
- Up-to-date intelligence on active threats and attackers
- Contextual details (e.g., malware behavior, attack stages, affected sectors)
- Cross-platform correlation across endpoint, identity, network, and cloud layers
- Pre-built MITRE ATT&CK mappings for faster response planning
Conclusion
Modern threats don’t wait — and neither should your security team. With Trend Vision One – Threat Intelligence, you gain the ability to move from static defense to dynamic, real-time protection. One of the most impactful capabilities is its container-aware visibility, which monitors network activity in and out of container environments. By automatically tracing these connections and comparing them against known malicious infrastructure, organizations can detect command-and-control (C2) traffic and other suspicious behavior early — often before attackers can take meaningful action.
This level of proactive monitoring reduces the attacker’s window of opportunity and gives security teams the clarity, speed, and context they need to stay ahead.

