Cyber Threats
The Illicit Business of Selling Stolen Apple Devices
Online scams and physical crimes are known to intersect. Last May we uncovered a modus operandi and tools used to break open iCloud accounts and unlock stolen iPhones. Further research into this crossover revealed how deep it runs.
Online scams and physical crimes are known to intersect. In an incident last May, we uncovered a modus operandi and the tools they can use to break open iCloud accounts to unlock stolen iPhones. Further research into their crossover revealed how deep it runs. There’s actually a sizeable global market for stolen mobile phones—and by extension, iCloud fraud. From Ireland and the U.K. to India, Argentina, and the U.S., the demand for unlocking services for stolen phones is staggering: last year, stolen iPhones were sold in Eastern European countries for as much as US$2,100. In the U.S. 23,000 iPhones from the Miami International Airport, valued at $6.7 million, were stolen last year.
The fraudsters’ attack chain is relatively straightforward. They spoof an email or SMS from Apple notifying victims that their device has been found. The eager victim, wanting their phone back, clicks on the link that will compromise their iCloud credentials, which is then reused to unlock the stolen device. The thieves will then subcontract third-party iCloud phishing services to unlock the devices. These Apple iCloud phishers run their business using a set of cybercriminal tools that include MagicApp, Applekit, and Find My iPhone (FMI.php) framework to automate iCloud unlocks in order to resell the device in underground and gray markets.
Their developers run an iCloud-unlocking business through their social media and personal websites. They also offer additional resale services and rent out servers for sending phishing messages. Their customer base has a global reach that includes Italy, France, Spain, U.S., India, Saudi Arabia, Brazil, and the Philippines. While our research only looked into three iCloud-unlocking apps and services, others can be found online, from social media to online ad and e-commerce sites.
The schemes we uncovered involve several fraudsters from Kosovo, the Philippines, India, and North Africa. AppleKit’s developer is known to be active on dev-point, an Arabic hacker forum. Customers using MagicApp or AppleKit aren’t obligated to use the phishing scripts, but because the developers know each other’s products well (and have a high success rate), many tend to use all three.
Phishing for Credentials
Below is a visualization of the modus operandi. Once attackers have hijacked the victim’s iCloud, their tools also enable them to download the iCloud account (to perform other malicious activities) and then delete it.
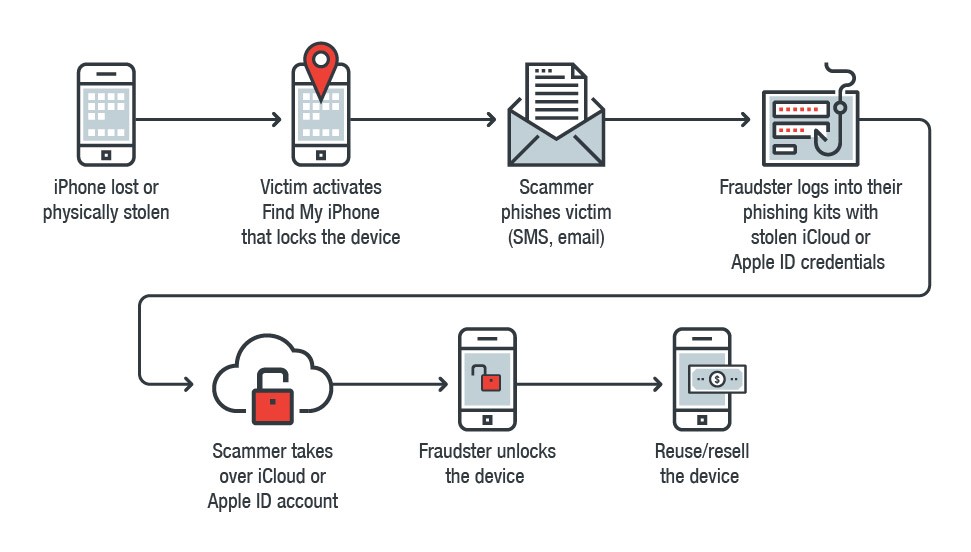 Figure 1: Attack chain of the fraudsters’ modus
Figure 1: Attack chain of the fraudsters’ modus
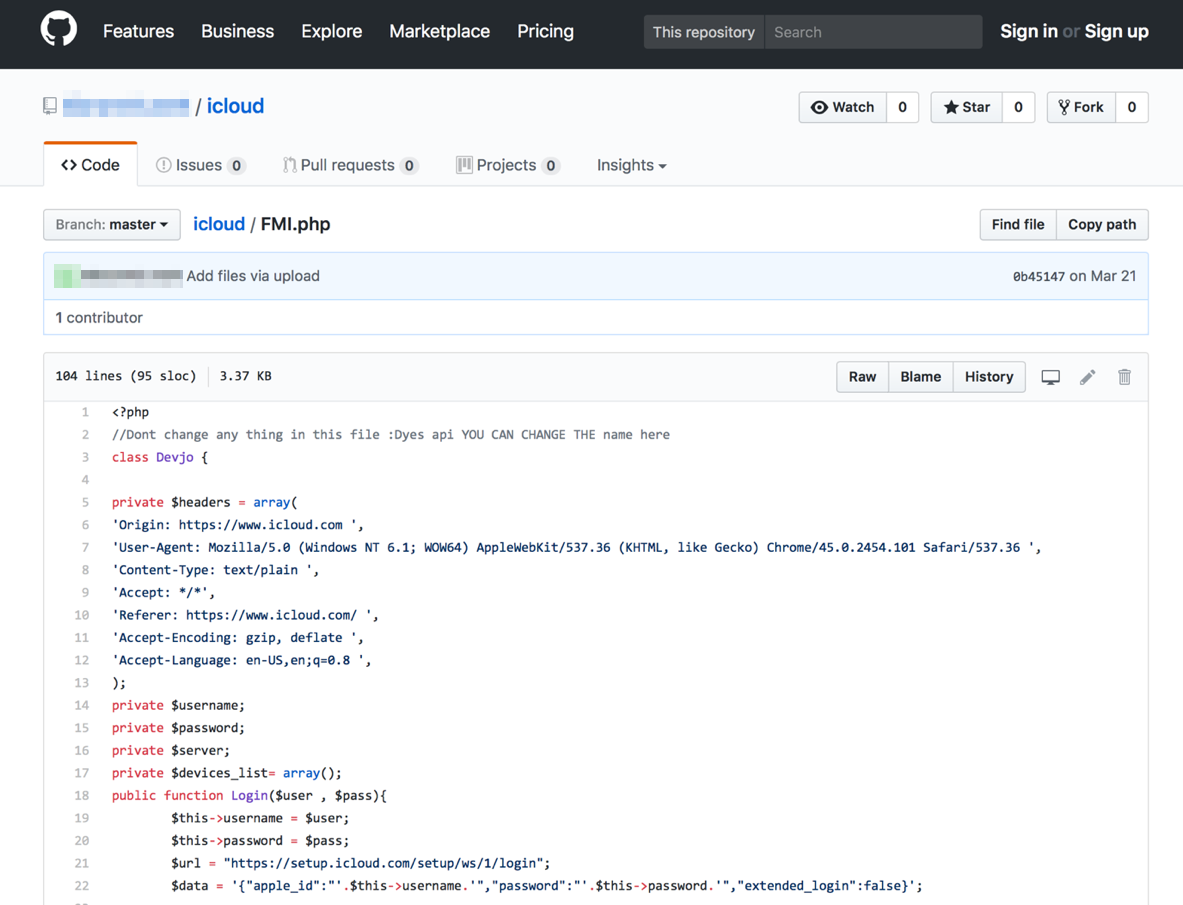 Figure 2: A fake Apple verifier phishing script project on Github (March 21, 2017)
Figure 2: A fake Apple verifier phishing script project on Github (March 21, 2017)
We found parts of the source code of one of the phishing pages in an open Github repository that also kept different tools for building iCloud phishing pages. The phishing page is based on what cybercriminals call FMI.php (Find My iPhone framework) / Devjo class, a component present in many other phishing kits. It’s the closest tool cybercriminals have that resembles Apple’s Find My iPhone Application Program Interface (API).
Once users enter their credentials on the phishing page, the FMI.php framework is used to retrieve the user’s iCloud information such as the cell phone number, passcode length, ID, GPS location, whether the device is locked or not, and if there’s a wipe command in progress. FMI.php framework can also delete the device from the victim’s Apple account after it’s unlocked. Attackers also get notified by email once the victim has been successfully phished.
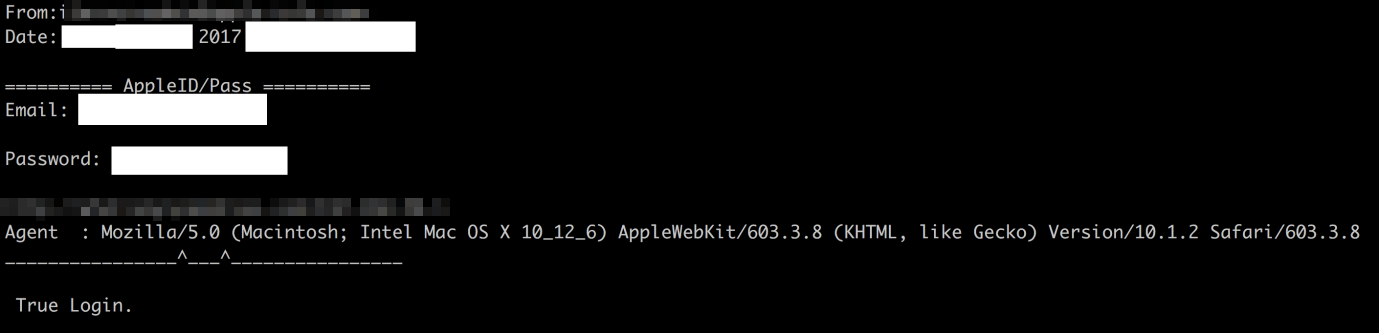 Figure 3: Sample email received by the fraudster with the victim’s Apple ID and password
Figure 3: Sample email received by the fraudster with the victim’s Apple ID and password
These phishing kits are actively advertised on social media, which include full tutorials on how to use them. They offer features such as:
- Email notifications to the attacker, which include the victim’s IP, HTTP referral, browser User-Agent, etc.
- Access to the victim’s iCloud, enabling them to get device information, unlock it, or delete the device from the account
- Anti-crawler and AV scanner capabilities, which are blocked by IP ranges
AppleKit: iCloud Fraud as a Service
Apart from the phishing kits, additional services are offered to help fellow fraudsters set up their own business. One of them is AppleKit, which includes a web panel of hijacked devices. AppleKit, which supports Apple iPhone, iPad, Mac, and Apple Watch, is purportedly updated regularly with additional features.
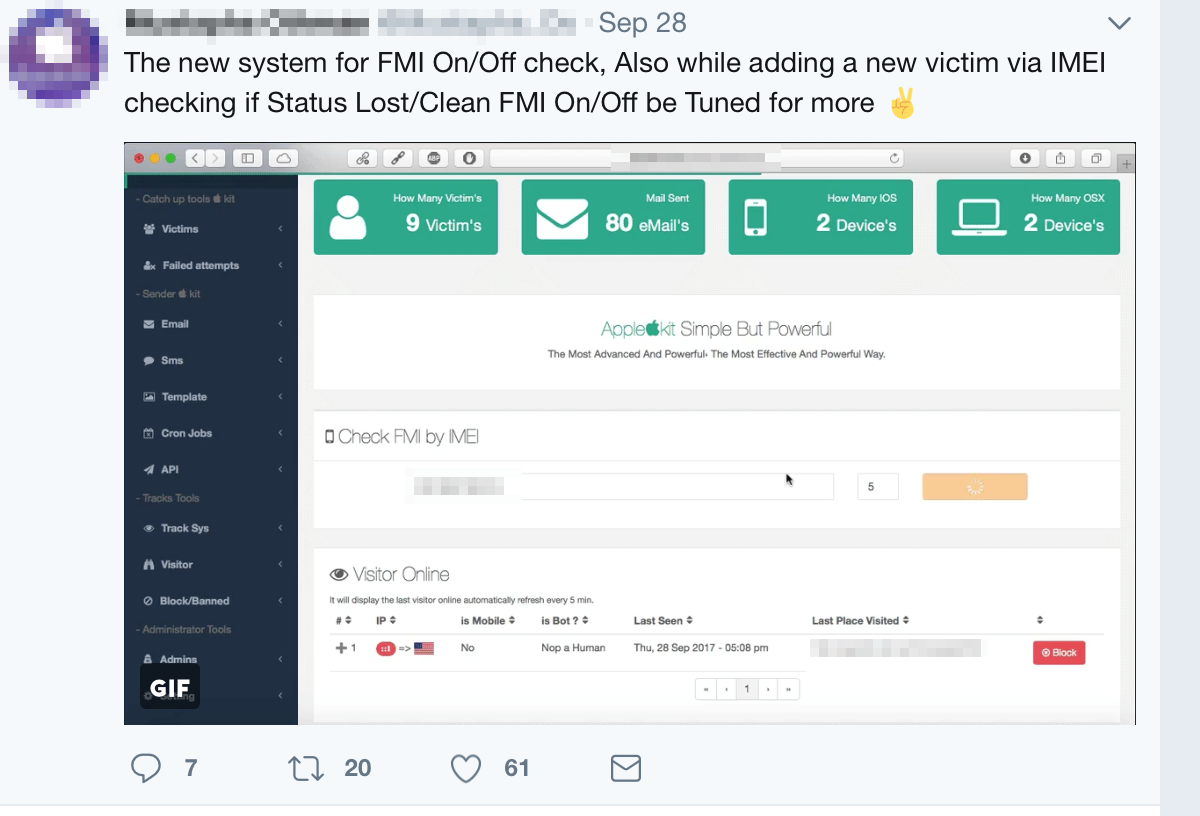 Figure 4: AppleKit’s control panel
Figure 4: AppleKit’s control panel
MagicApp: Automating iCloud Fraud
MagicApp automates the unlocking of iPhones and is used in conjunction with other attack vectors. MagicApp can also run on jailbroken Apple devices, as it is not approved on Apple’s official App Store. MagicApp, offered for free, is also available on Github, as seen below:
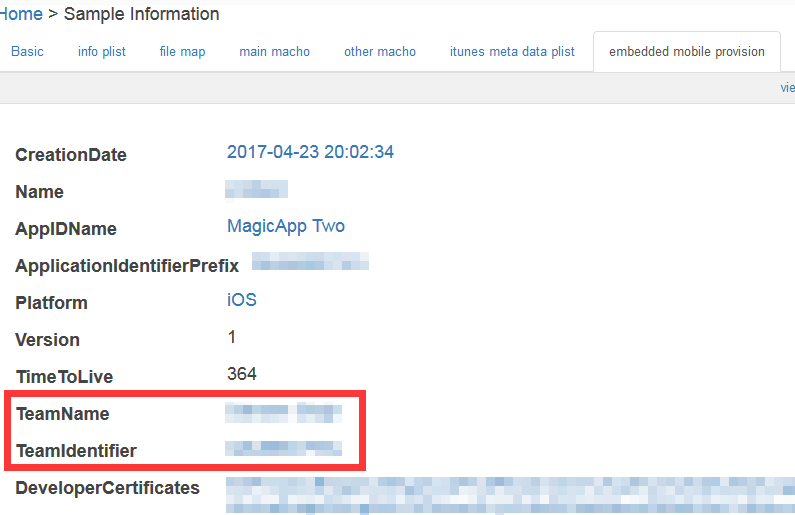 Figure 5: Snapshot of MagicApp’s properties on Github
Figure 5: Snapshot of MagicApp’s properties on Github
MagicApp offers a full range of features for unlocking stolen devices, including the capability to send phishing emails or texts. Every field is customizable, enabling bad guys to send text messages in their own local language. It can also send a fake GPS location to deceive the victim into believing their lost phone has been found. MagicApp even offers 50 customizable phishing templates for each Apple device.
MagicApp’s developer partners with another purveyor, iUnlocker[.]net, whose services are used to check the device status on iCloud and its telecommunications carrier. iUnlocker also offers a service that unlocks devices whose IMEIs were blocked by the carrier.
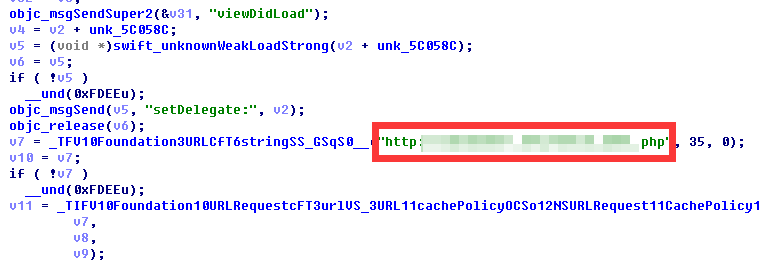 Figure 6: Code snippet using iUnlocker to check the device’s IMEI (analysis by Ju Zhu)
Figure 6: Code snippet using iUnlocker to check the device’s IMEI (analysis by Ju Zhu)
Physical and cyber security go hand in hand
Just as the internet has evolved the way information is accessed and how businesses are conducted, it has also blurred the face of crime. It’s no longer confined to the brick-and-mortar theft. The online tools we’ve seen show how traditional felony and cybercrime can work concertedly—or even strengthen each other—towards bigger payouts for the bad guys. Last September, for instance, cybercriminals got hold of iCloud credentials and abused Apple’s Find My service to lock Mac users out of their devices then extort them. The potential impact: resetting the device and losing all its data. Ultimately, physically securing devices shouldn’t take a back seat. Apart from keeping an eye on your devices, awareness also plays a crucial role:
- Apply best practices for securing mobile devices: enable two-factor authentication on your iCloud account, and set up or enable the device’s security features, i.e., Find My iPhone, Auto-lock
- Regularly back up your data to mitigate the impact of its loss
- Report the device’s loss or theft to your carrier to deter fraudsters from reusing it
- Be more aware of the signs of phishing; in this case, be wary of unsolicited emails or texts requesting for your iCloud and Apple ID credentials
- Enforce robust security policies in the workplace, especially if the device is used to store and manage sensitive data
More importantly, do your research: if purchasing a secondhand device, verify with the vendor or carrier that they’re not blacklisted. The Cellular Telecommunications Industry Association (CTIA) created a website that verifies the IMEI to help customers and law enforcement check if an iPhone has been blacklisted or stolen. Resellers and consumers alike should also note that historical data from the device’s Find My iPhone is saved on Apple’s databases. Smartly enough, Apple devices have preventive measures in place to make stealing and reselling devices tricky, including one that can brick a stolen device.
Trend Micro Solutions
Users can also benefit from multilayered mobile security solutions such as Trend Micro™ Mobile Security for Apple devices (available on the App Store) that can monitor and block phishing attacks and other malicious URLs. For organizations, especially those that use BYOD devices, Trend Micro™ Mobile Security for Enterprise provides device, compliance and application management, data protection, and configuration provisioning, as well as protect devices from attacks that leverage vulnerabilities, preventing unauthorized access to apps, as well as detecting and blocking malware and fraudulent websites. Trend Micro’s Mobile App Reputation Service (MARS) covers iOS threats using leading sandbox and machine learning technologies. It can protect users against malware, zero-day and known exploits, privacy leaks, and application vulnerability. We have disclosed our findings related to these fraudulent schemes to Apple. Details of our research, which includes a closer look at the tools as well as the indicators of compromise (IoCs), are in this technical brief. Updated as of November 14, 2017, 5:10PM PDT, which updated the technical brief.

