Best Practices: Securing Your Mobile Device
October 10, 2017
 The number of mobile phone users around the world is projected to exceed the five billion mark by 2019. This rapid increase, unfortunately, sees cybercriminals adapting and changing their methods to profit from this growing number of potential victims.
The number of mobile phone users around the world is projected to exceed the five billion mark by 2019. This rapid increase, unfortunately, sees cybercriminals adapting and changing their methods to profit from this growing number of potential victims. Cybercriminals continue to look for ways to exploit vulnerabilities in apps, operating systems, and software, trying to capitalize on security flaws before manufacturers find and patch them. ZNIU (detected by Trend Micro as AndroidOS_ZNIU), which has more than 300,000 detections on the Android platform, can plant a backdoor and perform information theft. iXintpwn/YJSNPI (detected as TROJ_YJSNPI.A), on the other hand, proves that iOS is not entirely unbreachable with its ability to crash iOS devices.
User data is a major target of cybercriminals—from credit card credentials to email passwords and contact lists. Victims have also been baited into downloading adware or subscribing to paid services.
The mobile threat landscape isn’t just filled with rooting malware and information thieves. Trend Micro already had over 235,000 detections for Android mobile ransomware in the first half of 2017 alone, which almost doubled the number of detections in 2016. They may not be as mature as their desktop counterparts such as WannaCry and Petya, but the increasing usage of mobile devices, particularly by businesses, continues to draw attention to this type of threat.
Since cybercriminals usually cast wide nets to reach more potential victims, mobile users should protect their devices early on to defend against threats. The following are some of the easy steps that can be done to protect your mobile device:
- Regularly update the operating system and apps. New vulnerabilities are always discovered, and vendors work to patch their applications and software as soon as they're available. For iOS, users can check for system updates under Settings > General > Software Update. Android users can look for it under Settings > About > System update.
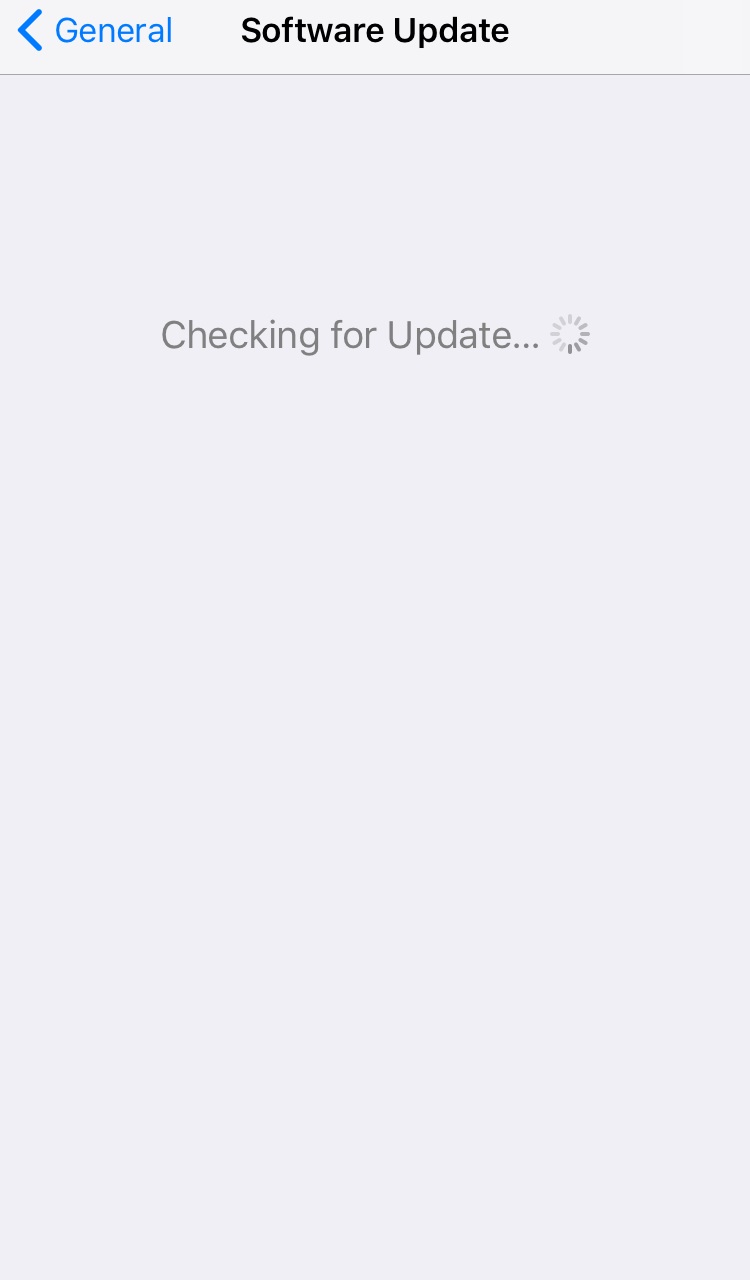
Figure 1. Screenshot of iOs checking for update
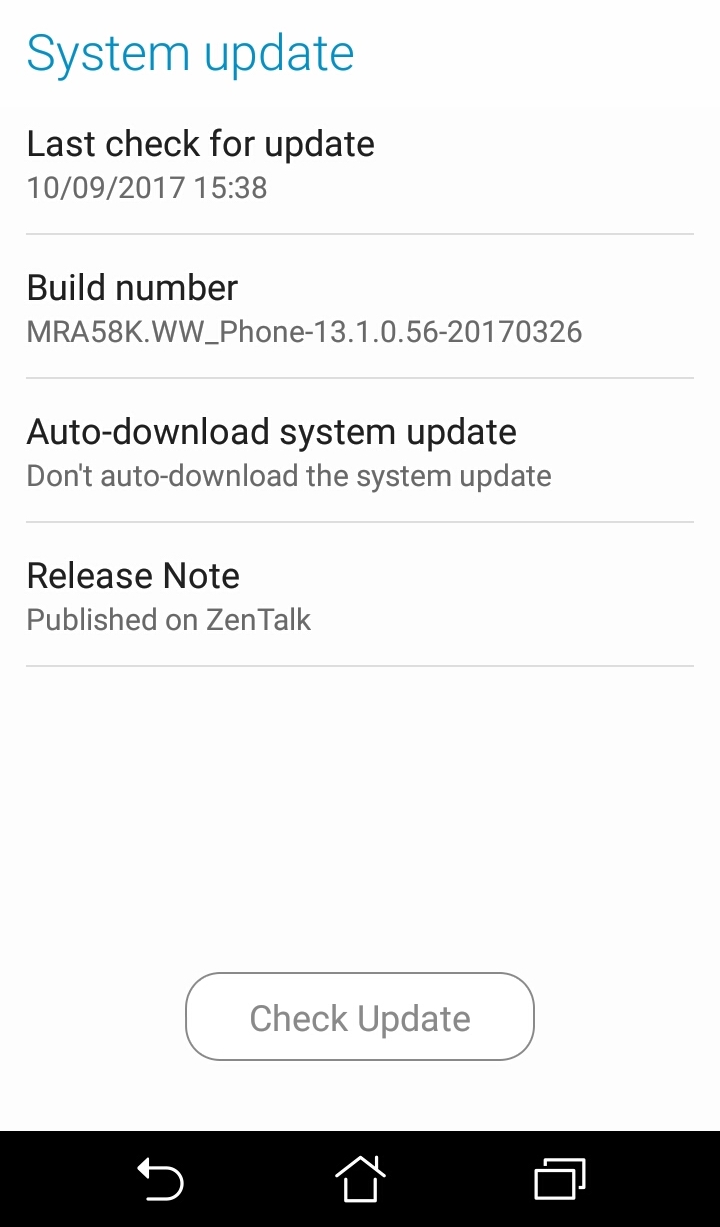

Figure 2. Screenshot of the System update UI of an Android-based ASUS phone
To make sure all apps are up-to-date, iOS users can go to the App Store to check for available updates. Android users can do the same by going to the Play Store.
- Use relevant built-in security features. You can improve your mobile device’s security by using built-in anti-theft apps like Find My iPhone. This app can help you locate your phone, track where it is or where it’s been, and remotely erase data in case you can't recover the device. Users can activate the feature under Settings > Accounts & Passwords > iCloud > Find My iPhone.
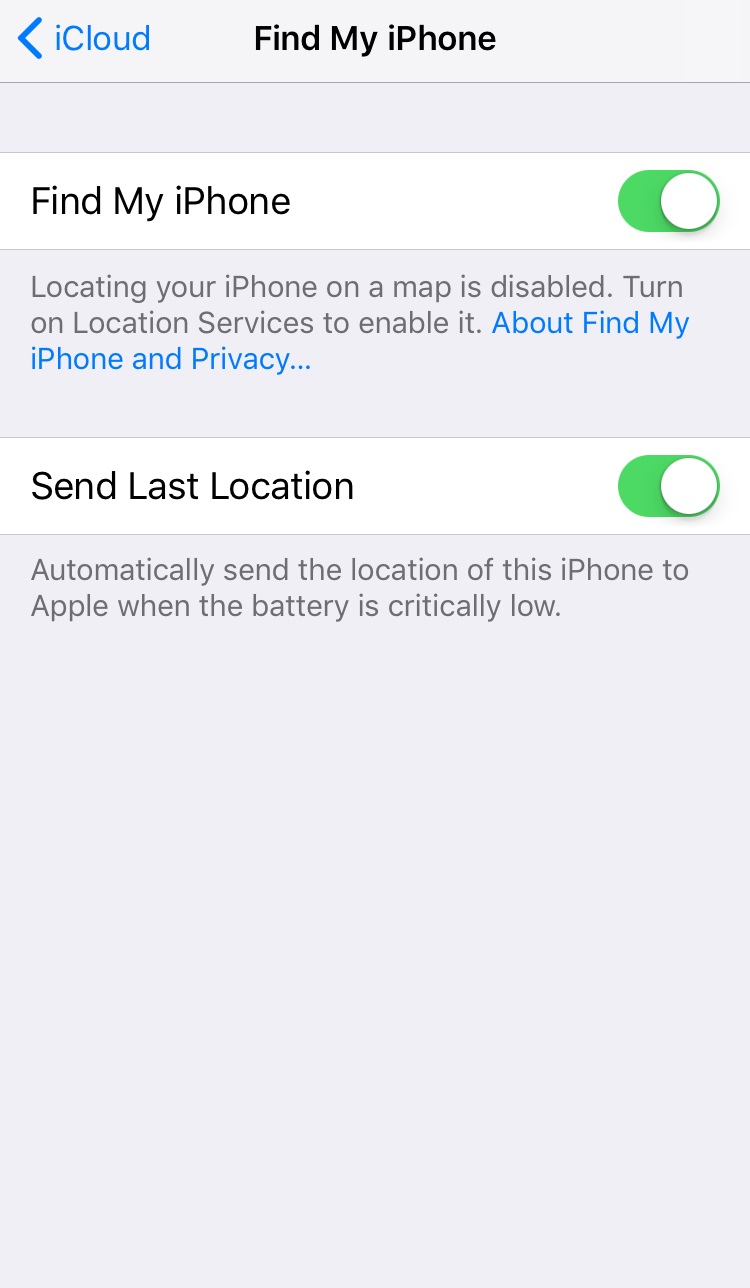
Figure 3. Screenshot of Find My iPhone turned on
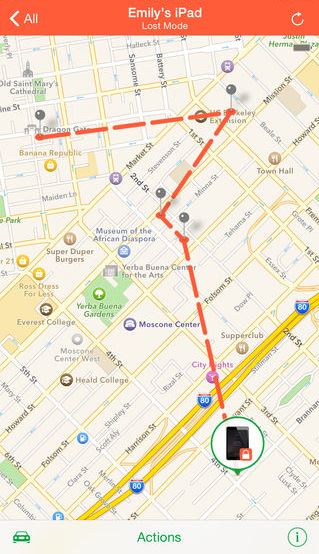

Figure 4. Screenshot of Find My iPhone locating a phone (via itunes.apple.com)
Android users have the same feature which they can access at google.co.uk/android/devicemanager. If they want to erase the device’s data and keep it locked in the event the device goes missing, they can go to Settings > Security > Device administrators and leave the Android Device Manager checked.
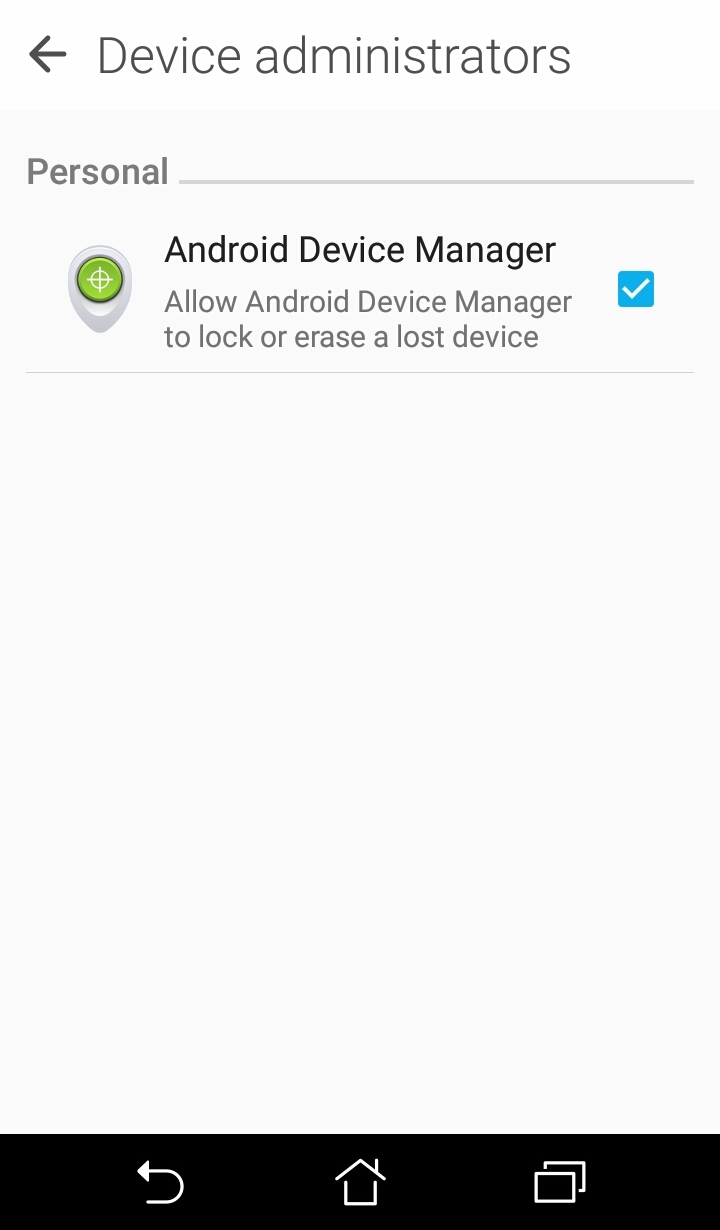
Figure 5. Screenshot of an Android’s Device administrators UI
Meanwhile, users can dodge further security and privacy issues via reviewing the scope of their app permissions. Apps sometimes require more than the basic default permissions. Make sure the installed apps only have access to features they need. Review which permissions they’re allowed to use as subsequent updates and bugs might have caused them to leak user data. iOS users can configure that under Settings > Privacy.
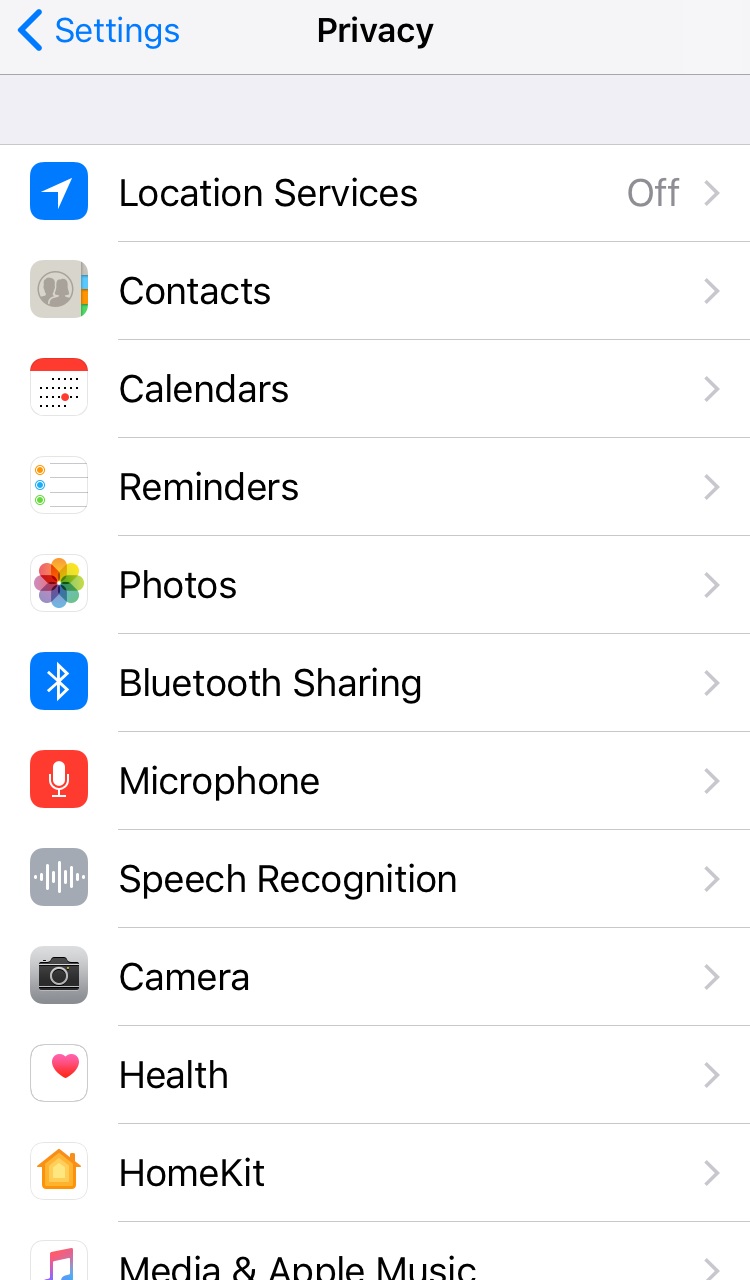
Figure 6. Screenshot of iOS 11.0.2’s privacy settings
iOS users can go to Settings > Touch ID & Passcode > Passcode Lock to turn off features that can be accessed even when the home screen is locked. For Android users, they can limit the information that appears in notifications by configuring the device’s notification settings.
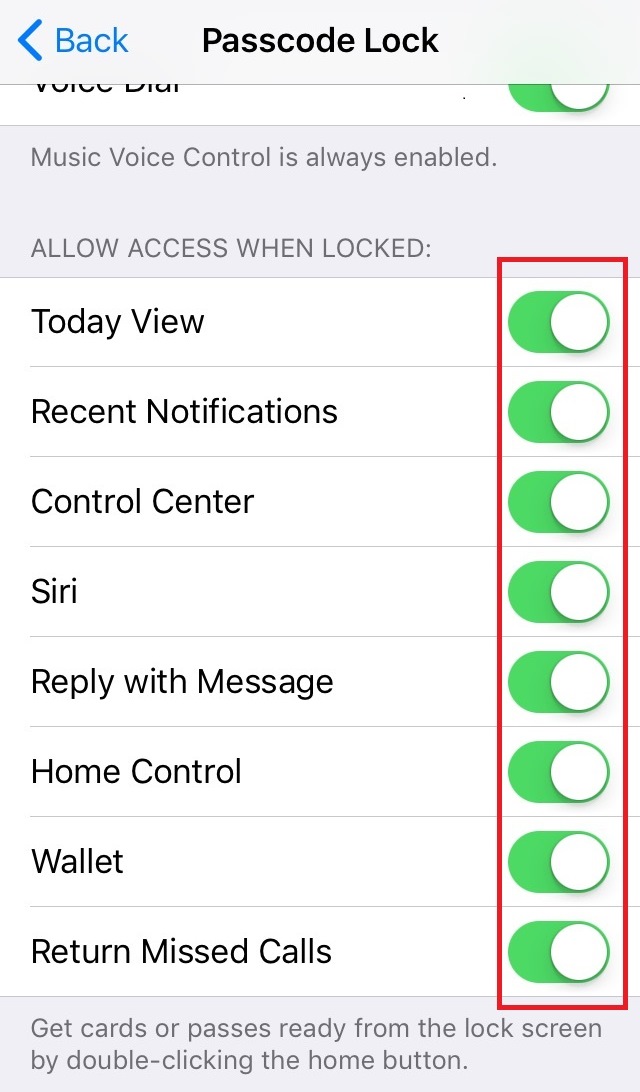
Figure 7. Screenshot of the Passcode Lock UI
Android 8.0 users can check which apps have which permissions by going to Settings > Apps & notifications > App permissions. Users can also grant permissions to apps while the app is running, which gives more control over the app’s functionality. If an app displays a message saying it needs a certain permission, users can decide at that time if it’s necessary.
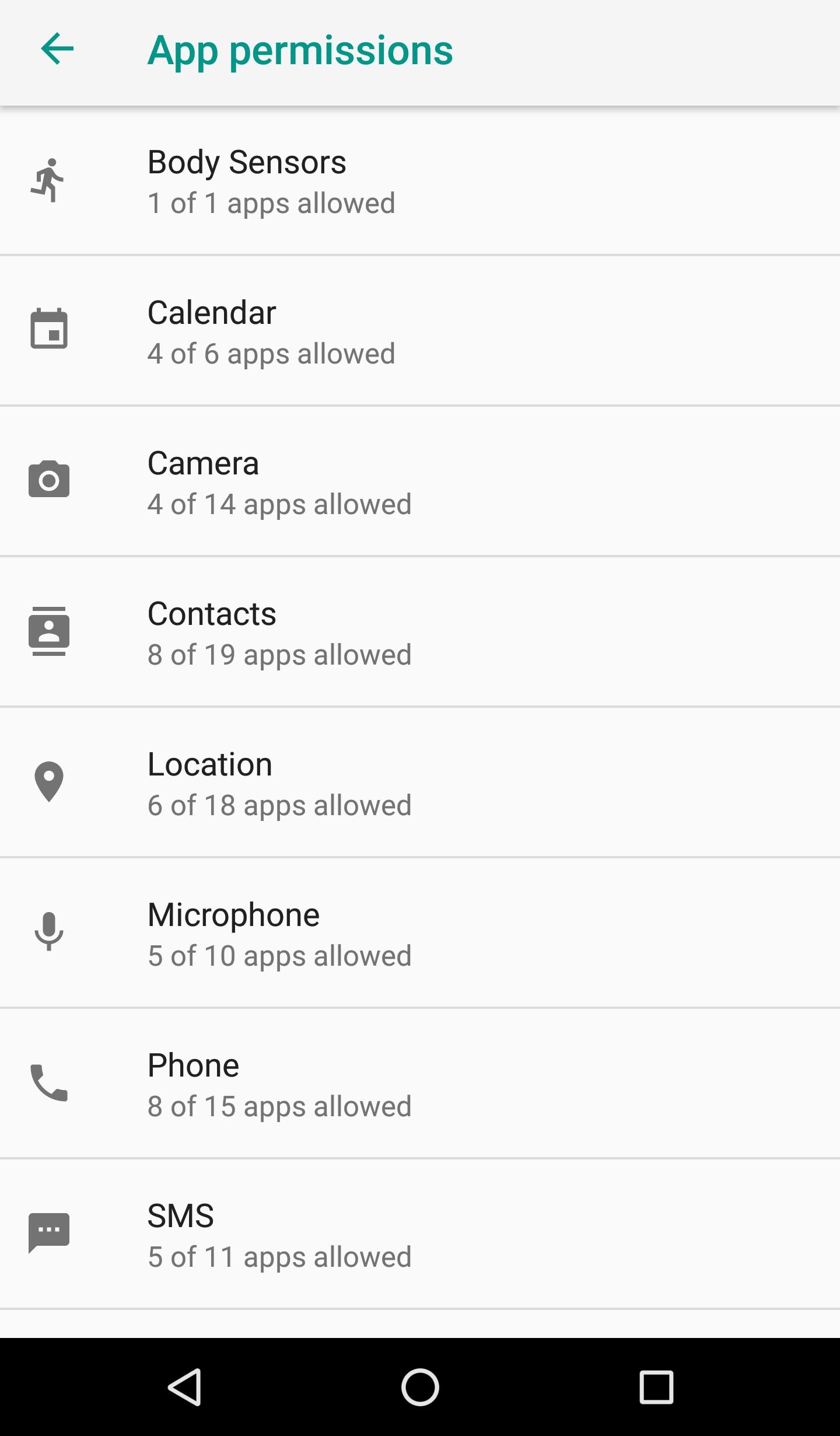
Figure 8. Screenshot of Android 8.0’s App permissions UI
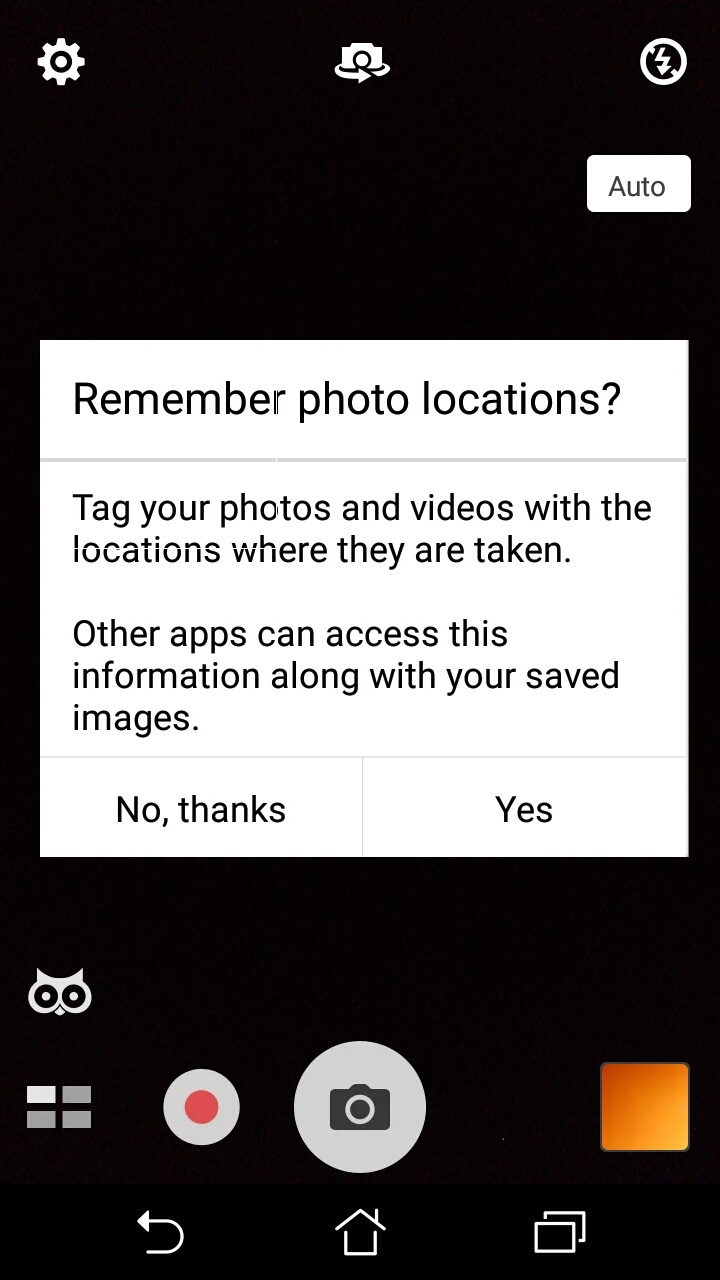
Figure 9. Screenshot of Android asking user permission at run time
- Minimize location access. Location services or settings, which is usually part of the quick settings feature of iOS and Android, allows apps and websites to use information from cellular, Wi-Fi, GPS networks, and Bluetooth to determine a user’s approximate location, which could be a cause for concern. When allowing permission for location access for iOS devices, it is recommended to only select While Using the App instead of Always, as it prevents a malware-ridden app running in the background from stealing a device’s location information.
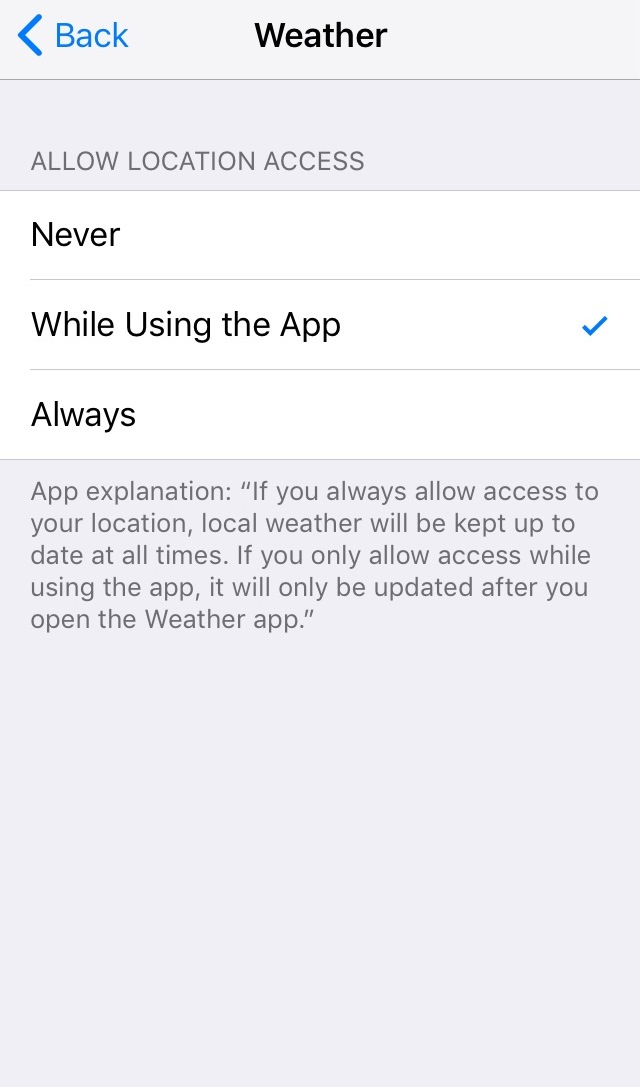
Figure 10. Screenshot of an app choosing ‘While Using the App’ for iOS location access
Android users can simply avoid the risk by turning off their device’s Location, under Settings.
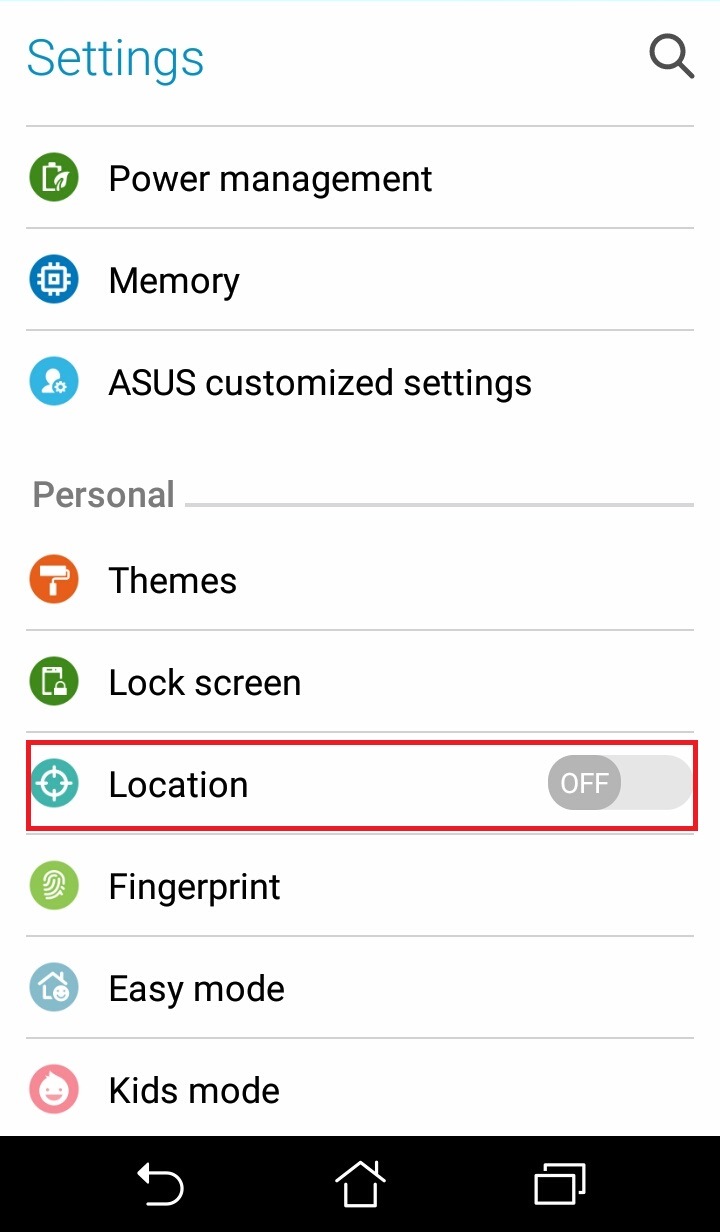
Figure 11. Screenshot of an Android Settings UI
Here are other best practices that must be applied to secure your mobile device:
- Avoid connecting to unsecured Wi-Fi networks. Turn off the automatic Wi-Fi connection feature on your smartphones or tablets. Users should refrain from connecting to public hotspots as they are not secure, and connecting to them can expose the device to a multitude of risks. If connecting is necessary, avoid logging into key accounts or financial services. Setting up a VPN is also a good way to secure data sent and received online.
- Download apps from trusted sources. According to a 2016 Android Security Review by Google, Potentially Harmful Apps (PHA) are still the biggest threat to Android users. Certain third-party app stores have proven to be more likely carriers of malicious apps, so always download from trusted sources. Users should also do their due diligence and check reviews or comments on the app page to make sure it is legitimate. Users who use mobile payment and popular gaming apps should also be cautious as they have become hot cybercriminal targets in the past.
- Know the risks of jailbreaking/rooting. Manufacturers place security restrictions and safeguards on their devices to protect users' devices and data. Jailbreaking or rooting removes these limitations, leaving the system more vulnerable to malware and other threats.
- Be wary of unsolicited calls or messages. Attackers use a variety of methods to get users to download malware or reveal personal information. Scan or verify any messages, calls, or emails from unknown senders before opening.
- Set automatic locks on mobile devices. Ensure that the mobile device locks automatically, and has a strong passcode—a simple pattern or swipe password isn’t much of a deterrent. If a device is lost or stolen, a strong password prevents anyone from quickly peeking at personal information. The use of biometric authentication features such as fingerprint scanner and facial recognition makes unlocking the device much more convenient and the security harder to crack.
- Limit the personal information given to apps and websites. Signing up for a new service or downloading a new app sometimes requires personal information. Be wary of revealing too much, and research on how secure the application or site is before logging on.
- Manage what is shared online. Make sure to use privacy settings on social media apps and sites. Some sites can broadcast location, email, phone numbers, or more to the public by default.
HIDE
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Posted in Mobile Safety, Cybersecurity
Recent Posts
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One