Olympic Vision: Business Email Compromise Campaign Targets Companies in US, Middle East and Asia
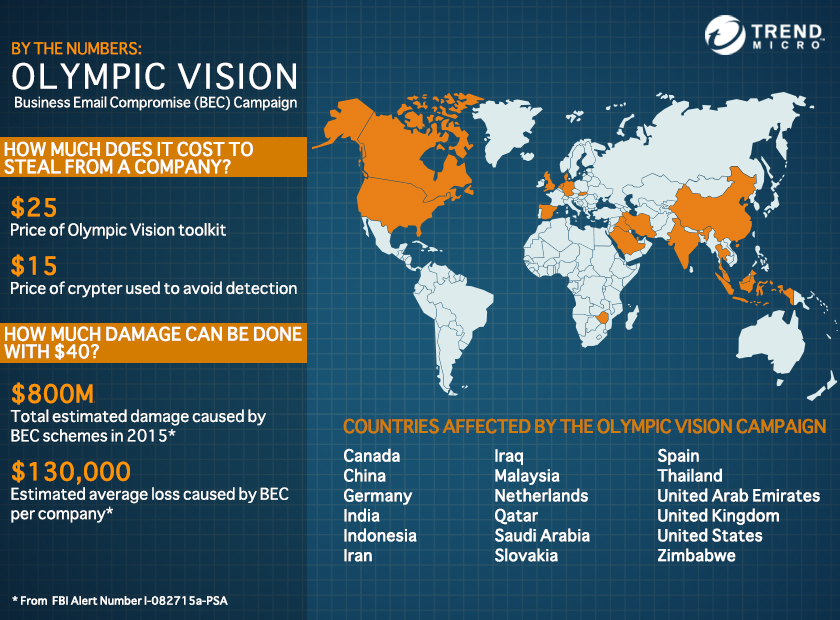
In 2015, Business Email Compromise (BEC) schemes have caused a significant amount of damage to enterprises, amassing at least $800 million in total losses. The damage potential and the surprising rate of effectivity brought by these campaigns have pushed the Federal Bureau of Investigation (FBI) to issue a warning to companies regarding this burgeoning threat—banking on simple yet effective social engineering lures to steal valuable company information or intercept money transactions. The FBI believes that, to this date, employees remain unfamiliar with how this type of threat works, and how it affects those who have been targeted.
[More: What you need to know about BEC Schemes]
Apart from using tried-and-tested tricks to turn employees into accomplices, the success of a BEC attack also relies greatly on an information-stealing malware normally sent to targets as email attachments, much like in an ongoing campaign that uses a simple keylogger malware to cause substantial damage to its targets.
Following the surfacing of its predecessors Predator Pain, Limitless, and Hawkeye, Olympic Vision is the fourth malware used in a BEC campaign, and has been found to have targeted 18 companies in the United States, Middle East and Asia.
In the case of this newly-discovered campaign, cybercriminals made use of Olympic Vision, a keylogger purchased online for $25. The attack method is far from complicated, but the damage is staggering. Feigning legitimacy and urgency, the malware is sent to an employee through an email attachment. Once opened, a backdoor is installed and infects the victim’s system and steals vital information.
[More: A technical review of Olympic Vision]
Business Email Compromise schemes are known for using social engineering techniques to gain unauthorized access to email accounts of target company employees, or simply to get information needed offhand. Recent reports illustrate how employees were duped by emails masquerading as legitimate messages coming from company heads in order to get information.
At the onset of March, Snapchat employees fell for an email disguised to have come from the company’s CEO. This turned out to be a phishing scam that led to the exposure of information of its employees. Similarly, a Seagate employee was also duped by an email message that appeared to be sent by the company’s CEO, requesting for data of present and past employees. More than the theft of information that can potentially be used to stage further attacks, BEC schemes put companies at risk of losing money by using similar ploys to coerce employees to wire funds to an account controlled by the scammers. According to the FBI, the average loss caused by a BEC scheme on a company is estimated to reach $130,000.
[Read: How to avoid falling for BEC schemes]
A closer look at Olympic Vision has led Trend Micro researchers to confirm that the identities behind the keyloggers can be traced to two Nigerian cybercriminals, operating separately in Lagos and in Kuala Lumpur in Malaysia. This is similar to the Nigerian cybercriminals linked to the HawkEye BEC campaign studied in 2015. As of this writing, our security experts are working hand in hand with law enforcement to pin down the operators involved in this campaign.
Social engineering techniques are the most vital component to a BEC scheme’s success. That said, employee education on the nature of the scheme is still the most effective ways of thwarting attacks that use social engineering.
Apart from a more sturdy security mindset, the InterScan Messaging Security Virtual Appliance with enhanced social engineering attack protection defends against socially-engineered emails used in BEC attacks. Medium and large enterprises using Trend Micro products are protected from this threat. The Olympic Vision variants and BEC-related emails are blocked by the endpoint and email security capabilities of the Trend Micro Smart Protection Suites and Network Defense solutions.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One