17-Year Old MS Office Flaw (CVE-2017-11882) Actively Exploited in the Wild
 Trend Micro uncovered a malicious Rich Text Format (RTF) file exploiting CVE-2017-11882 to deliver the spyware Loki (TSPY_LOKI). The payload is dropped via an HTML Application (HTA) that invokes PowerShell, which then retrieves the information stealer.
Trend Micro uncovered a malicious Rich Text Format (RTF) file exploiting CVE-2017-11882 to deliver the spyware Loki (TSPY_LOKI). The payload is dropped via an HTML Application (HTA) that invokes PowerShell, which then retrieves the information stealer.
What does CVE-2017-11882 entail?
CVE-2017-11882 is a 17-year old memory corruption issue in Microsoft Office (including Office 360). When exploited successfully, it can let attackers execute remote code on a vulnerable machine—even without user interaction—after a malicious document is opened. The flaw resides within Equation Editor (EQNEDT32.EXE), a component in Microsoft Office that inserts or edits Object Linking and Embedding (OLE) objects in documents. A proof-of-concept exploit was released publicly, but this has been fixed by Microsoft’s November Patch Tuesday.
The Loki family can steal account information from File Transfer Protocol (FTP) clients, as well as credentials stored on various web browsers and cryptocurrency wallets. Loki can also harvest data from “Sticky”-related (i.e., Sticky Notes) and online Poker game applications.
[RELATED: Cobalt Hacking Group Sets Sights on Russian-speaking Businesses Anew]
How are attackers exploiting CVE-2017-11882?
Trend Micro’s initial and ongoing analysis also found that a spammer group is also actively exploiting CVE-2017-11882 to infect systems with information stealers Pony/FAREIT and FormBook. The attack chain involves the use of a command that retrieves the payloads from a remote Server Message Block (SMB) open directory.
The Cobalt hacking group also weaponized this security flaw in one of their campaigns in late November, sending out a similarly constructed RTF file. The final payload is a dynamic-link library (DLL) file. In their previous spear-phishing campaigns, the DLL is a component of the penetration testing tool Cobalt Strike, which they abuse to hijack the infected system.
Trend Micro also saw other threat actors using CVE-2017-11882 to infect systems with a keylogger and a lockscreen with a ransom note that resembles that of Bad Rabbit. Spam runs were also seen in Australia and Japan on November 21, which dropped ZLoader—a downloader Trojan for ZBOT—and Ursnif, respectively.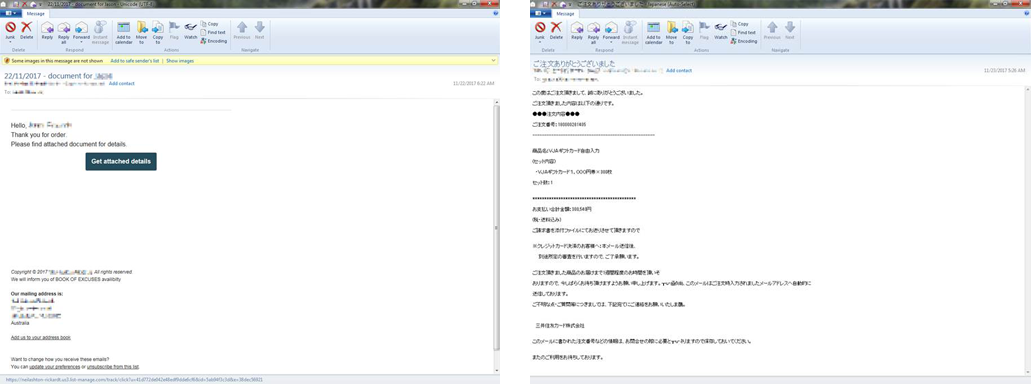
Screenshots of the sample emails in the spam runs in Australia (left) and Japan (right)
What can users and businesses do?
Here are some of the countermeasures that can be used against threats that use CVE-2017-11882:
- Blacklist, restrict, and secure the use of command-line applications and system administration tools such as PowerShell
- Make sure the system and its applications are patched and updated; consider virtual patching for legacy or end-of-life systems
- Secure the email gateway—the aforementioned threats use email as their main entry point
- Implement security mechanisms that can mitigate further exposure of sensitive data, such as network segmentation and data categorization
- Reduce the attack surface by monitoring and blocking anomalous activities in the system or network—firewalls, sandboxes, as well as intrusion detection and prevention systems, help in this regard
Trend Micro™ Deep Security™, Vulnerability Protection, and TippingPoint provide virtual patching that protects endpoints from threats that abuse unpatched vulnerabilities.
Trend Micro™ Hosted Email Security is a no-maintenance cloud solution that delivers continuously updated protection to stop spam, malware, spear phishing, ransomware, and advanced targeted attacks before they reach the network. Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevent malware from ever reaching end users. At the endpoint level, Trend Micro™ Smart Protection Suites, deliver several capabilities that minimize the threat’s impact.
These solutions are powered by the Trend Micro XGen™ security, which provides a cross-generational blend of threat defense techniques against a full range of threats for data centers, cloud environments, networks, and endpoints. It features high-fidelity machine learning to secure the gateway and endpoint data and applications, and protects physical, virtual, and cloud workloads.
Trend Micro™ Deep Security and Vulnerability Protection protect user systems from any threats that may use CVE-2017-11882 via the following DPI rule:
- 1008746 - Microsoft Office Memory Corruption Vulnerability (CVE-2017-11882)
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One