Awards Season, A Frenzy for Online Schemes
Most of the buzz around the awards season centers itself around the winners, and the audience’s and critics’ biggest bets. While contenders are not quite set aside as a settled affair, it’s always still sufficiently delightful to await the disclosure of what remains a mystery to all: the Academy Award winners. As we know it, the Grammy’s, Golden Globes, SAG awards, and Critic’s Choice awards serve as the precursor that suggests the competitive slate of nominees for the biggest prize-giving night happening on February 22. This culmination has brought many enthusiastic fans and pundits to search, discuss, and even write on their blogs about movie releases, awards schedules, premieres, and other events related to it.
As the stakes run high for this month’s huge awards night, cybercriminals are coming up with their own list of surprises to victimize unwitting users. Unfortunately, the quickest way to an eager fan’s heart is through cleverly-strewn gossip, stories, and offers, which the bad guys have efficiently mastered. In the past, we’ve seen poisoned search results, suspicious links, and other fake offers that lead to malware download. Just like an actor’s captivating tour de force, most cybercriminals are experts in using these social engineering techniques especially during high-profile events like the awards season.
[Read more on The Most Popular Social Engineering Lures Used in 2014]
Before you revel in the final vestiges of suspense, know first how you can protect yourself from various online threats by learning what they’ve been using as lures to fool you. Here’s a breakdown of a few of the schemes used. The nominees are…
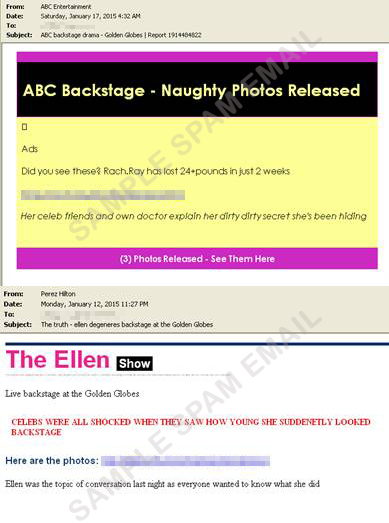
1. Golden Globes
Technique used: Invisible ink and microfont
Even if the Golden Globes are over, people continue to search for the latest news on celebrities, after parties, and other succeeding events tied to the occasion. You can see in the first photo an email wherein a message appears to be normal. However, in reality, spammers are using the invisible ink technique which you can see in the second image.
This technique is used to conceal gibberish words or phrases while using the same font color and background color (i.e. font color: white; background color: white). The unknowing user will not be able to tell that the email is actually malicious. In the third image, attackers used micro fonts to hide the suspicious looking links.
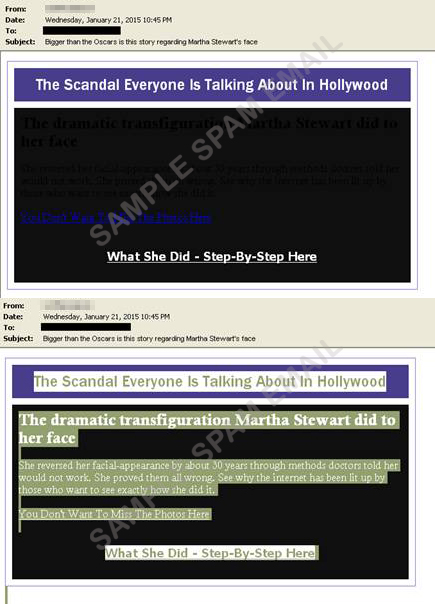
2. Grammys

The Grammy’s had its own share of abuse as well. In this case, attackers used the salad bottom technique. In both images you can see an ordinary-looking email and one with garbled messages at the bottom. The salad bottom technique is an indicator that the content is malicious (i.e. an image is placed at the top of the mail followed by a series of new lines and nonsensical words and phrases).
The widely anticipated Academy Awards is already steering fans towards the wrong direction. Based on our findings, cybercriminals are using this popular event to lure users to open spammed emails. These emails, just like the ones we found in Grammy-related threats, use the invisible ink technique as well. Hence, users won’t be able to tell if the email is malicious or not.
Buzz-worthy events are among the most popular baits cybercriminals use. If you’re not careful, you may end up hacked, robbed, and distressed, as they are ultimately after your money, your identity, and your network as well. While there can be many ways for an attacker to get to you, you can take these simple steps to avoid social engineering attacks:
- Avoid clicking on links that point to unverified targets. They are usually accompanied by promises or offers that are too good to be true.
- Bookmark your favorite sites to prevent from typing in the wrong keywords or address.
- Be sure to confirm with your contacts before opening email attachments. If you receive unknown emails, it’s better to delete and block the sender as they are most likely linked to social engineering threats.
- Even if it’s tempting to click on news that has your favorite movie title in it, avoid them altogether if they don’t come from trusted sources.
- Invest in a security solution as it can protect your system and data from varying threats.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization


 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One