Modern Ransomware's Double Extortion Tactics and How to Protect Enterprises Against Them
 Download Modern Ransomware’s Double Extortion Tactics and How to Protect Enterprises Against Them
Download Modern Ransomware’s Double Extortion Tactics and How to Protect Enterprises Against Them
Ransomware actors have been a persistent threat for years, but they are still evolving. The wide adoption of advanced cybersecurity technologies and improved ransomware response processes has limited the success of traditional ransomware attacks. Upgraded security has forced these cybercriminals to evolve their strategies, and has paved the way for what we now call modern ransomware attacks.
What does a modern ransomware attack look like?
Modern ransomware actors identify and target valuable data, often exfiltrating it from a victim’s network organization rather than simply encrypting it. This gives them another avenue for extortion: if a victim does not pay the ransom, the attacker can threaten to publicize the private data. For enterprises holding intellectual property data, proprietary information, private employee data, and customer data, this is a serious concern. Any data leak will come with regulatory penalties, lawsuits, and reputational damage.
Another significant feature of modern ransomware is that the actors are more precise and involved in the attack. They take over networks in multiple human-supervised stages, veering away from click-on-the-link automatic events. They also spend significant time conquering different parts of the victim’s network (a process that may take weeks or months) before they execute the ransomware payload, making such attacks look more like nation-state advanced persistent threat (APT) attacks instead of traditional ransomware incidents.
This report discusses the differences between modern ransomware and traditional attacks, and also offers a look into the new ransomware business model using the Nefilim ransomware as a case study.
Shifts in criminal business models
The tools, tactics, and procedures (TTPs) that make up the ransomware business model have changed significantly, primarily to take advantage of new technologies that advance the attackers’ capabilities.
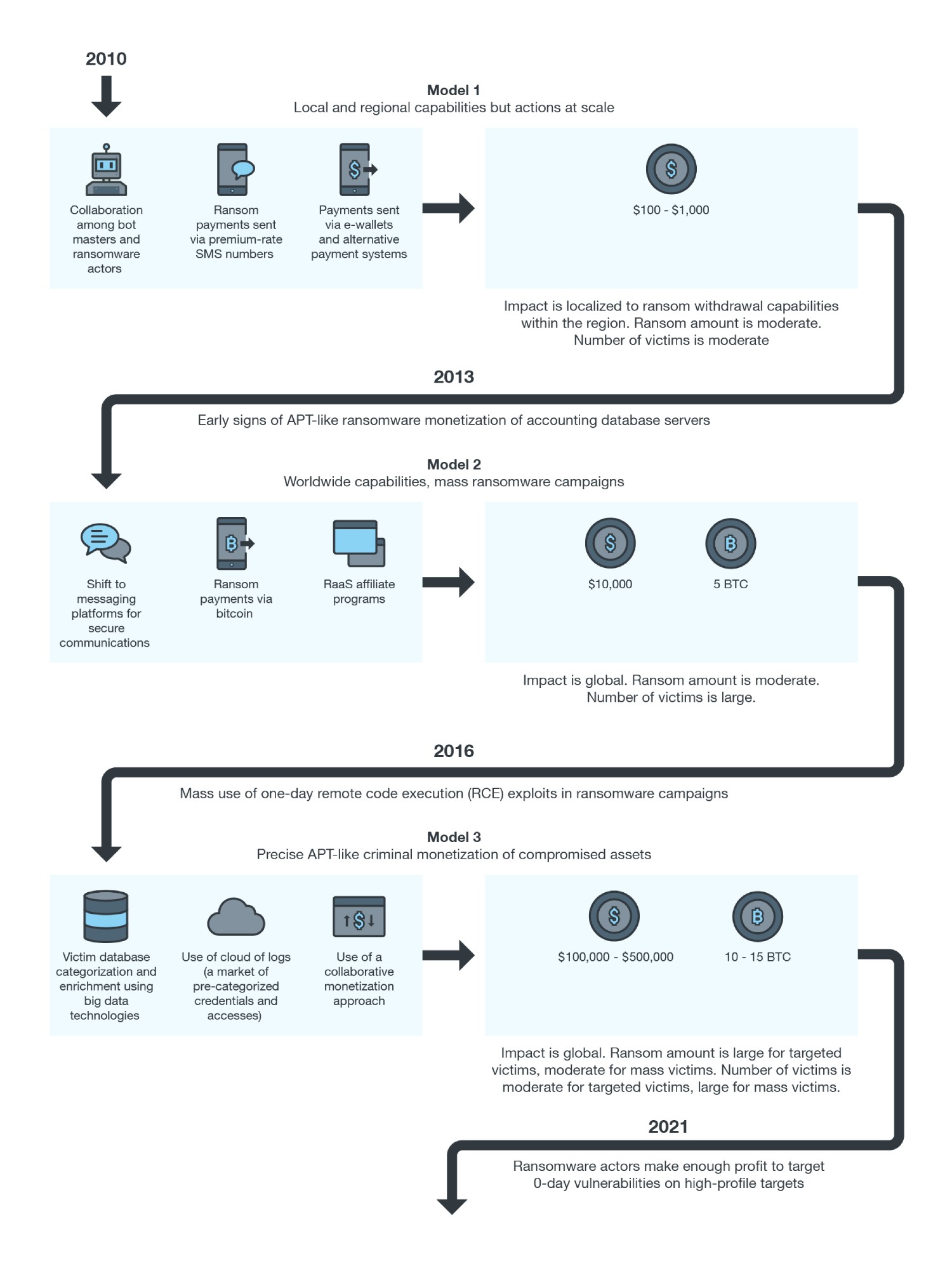
Figure 1. Changes in ransomware business models and monetization methods
Figure 1 shows the evolution and the major shifts in different ransomware business models and their respective monetization methods. Model 1 is related to early monetization strategies, wherein actors were limited by localized payment methods. This model is outdated and is rarely used compared with Models 2 and 3. Some underground actors still prefer Model 2, which provides moderate monetization from a large number of victims. Model 3 is related to more targeted monetization of victim assets and includes the deployment of several additional steps in the cybercriminal business process.
Areas where we have seen significant changes:
Modern ransomware case study
This section will use the Nefilim ransomware family as an example of a modern ransomware attack.
To gain initial access into victim’s networks, Nefilim actors use exposed RDP services and publicly available exploits. They exploited a vulnerability in the Citrix Application Delivery Controller (CVE-2019-19781), and a Windows Component Object Model (COM) elevation of privilege (EoP) vulnerability that Google Project Zero discovered, which was then fixed by Microsoft in May 2017.
After gaining initial access, Nefilim attackers start by downloading additional tools on a web browser. One significant download is a Cobalt Strike beacon that is used to establish a remote connection to the environment and execute commands. (Cobalt Strike is a versatile post-exploitation penetration tool that allows security testers to attack the network, control the compromised system, and exfiltrate interesting data. Unfortunately, its capabilities can be misused by attackers.) Other downloaded files are: the Process Hacker tool, which is used to terminate endpoint security agents; and Mimikatz, which is used to dump credentials.
Attackers move laterally once they gain a foothold into the network, meaning they will use a compromised system to find other areas they can access. To avoid detection, attackers will often weaponize tools that are built-in or are commonly used by administrators, a tactic that called “living off the land.”
Lateral movement
TOOLS
Attackers can use Mimikatz to dump hashes, tickets, or plain text passwords.
Lateral movement
TOOLS
Attackers can deploy tools within systems to aid in lateral movement. This includes tools such as PsExec, Bloodhound, and AdFind.
Lateral movement
TOOLS
Cybercriminals can abuse tools like AdFind to collect Active Directory information and map out the infrastructure to find more targets.
Privilege escalation
TOOLS
Attackers can exploit known vulnerabilities to elevate privileges and perform administrative actions or actions requiring elevated privileges.
Nefilim's initial tactics and tools
Calling home and exfiltration
As discussed in the previous section, the commercially available software Cobalt Strike is run on the victim’s system. The beacon will connect back to a Cobalt Strike C&C server that the attackers control. We have seen Nefilim-related Cobalt Strike C&C servers being hosted in different clusters on the internet. The actors have a preference for hosting companies in various countries including Bulgaria, the UK, the US, and the Netherlands. Other Nefilim-related Cobalt Strike C&C servers are hosted through small bulletproof web hosting services created by various shell companies. Some of the shell companies seem to be set up almost exclusively for hosting Cobalt Strike beacon C&Cs , large scale internet scanning (including the scanning of Citrix servers and in one case, the clear-web back end for a Tor-hidden website where Nefilim actors post stolen data from their victims.
We observed Nefilim actors making use of at least three different kinds of bulletproof hosting services: a Tor-hidden server that is used to leak stolen information, small IP ranges belonging to small shell companies, and fast flux hosting (hosting where the frontend regularly changes its IP address).
Malware payload
Nefilim is a post-compromise ransomware, which means it is launched manually by actors or affiliates after they determine that they have adequate control over the victim’s infrastructure. Once it is running, the execution flow is very straightforward.
First, Nefilim creates a mutual exclusion (mutex) object to prevent more than one thread of the same process. Then, it will decrypt the ransom note using a fixed RC4 key. Figure 2 shows an example of the ransom note, which includes three email addresses that victims can use to contact the Nefilim actors about the ransom payment.
It then generates a random AES key for each file that it queues for encryption. To enable file decryption in case the victim pays the ransom amount, the malware encrypts the AES key with a fixed RSA public key and appends it to the encrypted file.
If launched without any problems, the Nefilim executable prepares to encrypt. Before starting, it checks an exclusion list of files and directory names. This prevents Nefilim from encrypting files that the operating system needs, and it allows common applications such as browsers and e-mail clients to continue working properly. Then, it encrypts the files that are not on the exclusion list — the encryption function is largest function in the Nefilim code.
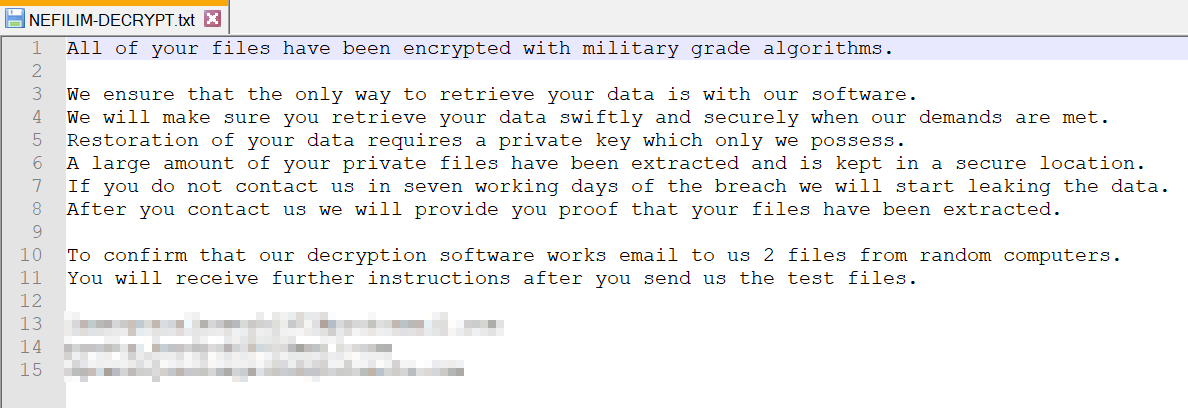
Figure 2. The Nefilim ransom note
Variants and evolution
After its first version was spotted in the wild, we have continued to monitor Nefilim’s activities and its evolution. To date, we have observed 18 different variants among an estimated 65 different samples.
Based on the information we have gathered, Nefilim samples follow a consistent pattern. This suggests that:
- Each victim gets a unique sample, including a ransom note that has the ransomware actors’ contact information in the form of three e-mail addresses.
- When Nefilim authors change the certificate they use to sign the binaries, they also change the extension added to encrypted files.
The following table lists the tactics and techniques used in the Nefilim ransomware samples we observed.
| Tactic | Technique |
| Initial access | T1078 – Valid accounts |
| Execution | T1106 – Native API* |
| T1059 - Command and scripting interpreter | |
| Privilege escalation | T1055 - Process injection |
| Defense evasion | T1140 – Deobfuscate/Decode files or information |
| T1070 – Indicator removal on host* | |
| T1070.004 - File deletion* | |
| Discovery | T1083 - File and directory discovery* |
| T1120 - Peripheral device discovery* | |
| T1135 - Network share discovery* | |
| Lateral movement | T1570 - Lateral tool transfer |
| Impact | T1486 - Data encrypted for impact* |
| T1489 - Service stop |
Victim profile
The profile of a Nefilim victim is relatively broad in terms of location and industry, but the targets tend to be companies with a revenue of over US$1 billion. The majority of the targets are located in North and South America, but we have also seen targets throughout Europe, Asia, and Oceania.
Our data showed a steady and substantial growth in the amount of sensitive information that has been leaked by Nefilim actors. Nefilim has been able to keep websites with victim’s data up-and-running for more than a year. The group has also been known to post their victims’ sensitive data over several weeks and even months, with the goal of scaring future victims into paying ransom.
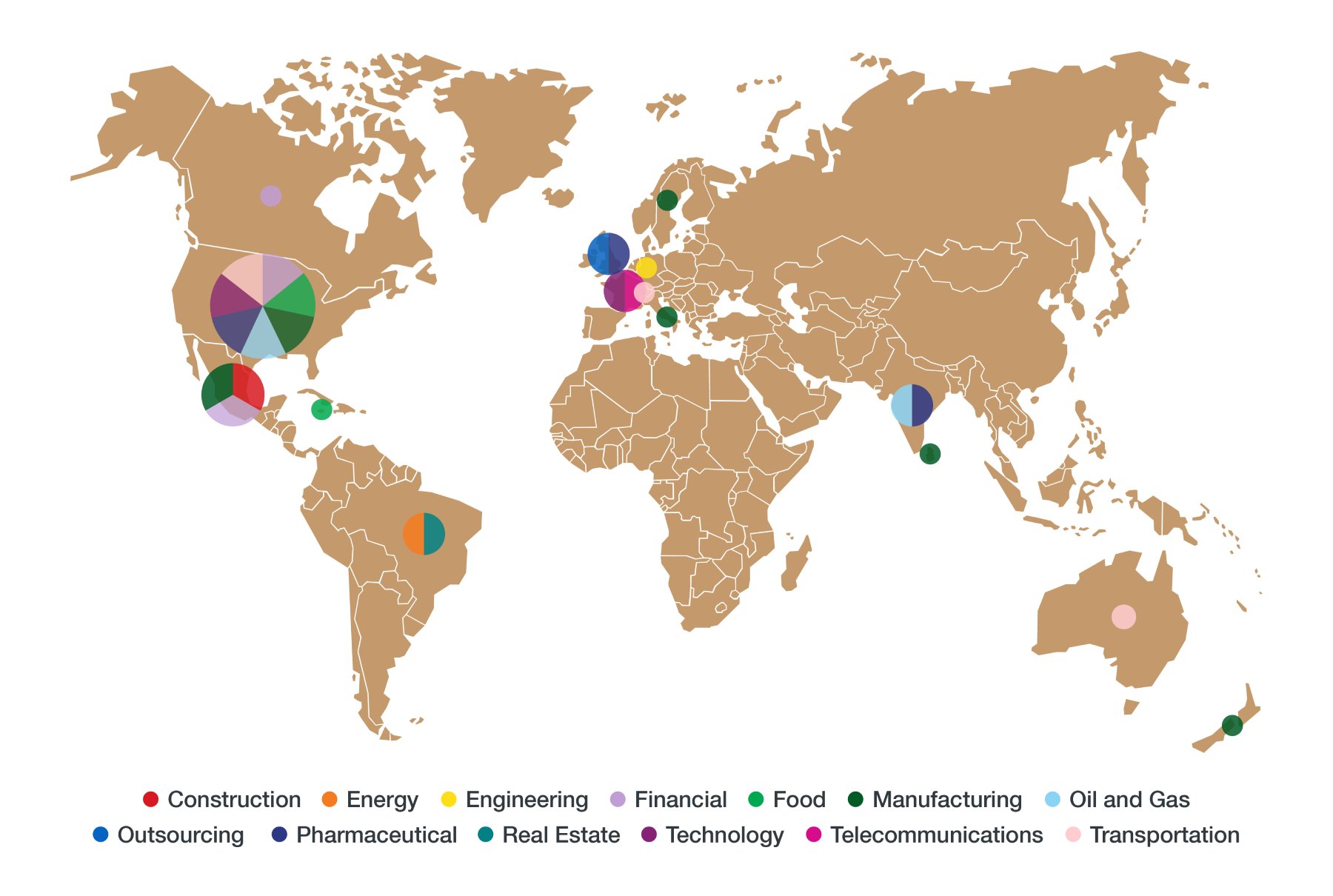
Figure 3. Nefilim victims by number, location, and industry
Figure 4. The median revenue (in millions of US$) of ransomware victims with leaked data per RaaS as of February 21, 2021
Figure 5. The cumulative data (in gigabytes) leaked by Nefilim actors from March 2020 to January 2021
Comparing how Nefilim actors and different RaaS actors leak stolen data
We think that the primary reason ransomware actors leak sensitive data is to issue a clear warning to future victims: ransomware actors will try to cause further harm when the ransom amount is not paid. For example, the infamous REvil actors boldly started an “auction” on their website in the dark web for the stolen data of a victim organization that refused to pay their ransom.
We researched the RaaS sites of 16 ransomware actors and found significant differences in how these actors extort money from their victims. Most actors claim that they will keep stolen data publicly available for several months. Some actors such as Nefilim and Cl0p manage to keep terabytes of stolen data online for over a year and threaten to leak increasing amounts of data over time. As mentioned above, some websites are on Tor-hidden servers while others are hosted using bulletproof hosting. We noted that RaaS actors upload stolen files on commercially available and free file-sharing platforms, or even host files on their websites on the clear web.
Attribution
We believe that the Nefilim ransomware evolved from an older family called Nemty. Based on the code similarities between Nemty and Nefilim, as well as what we believe to be similar business models, we find it likely that the version called Nemty Revenue 3.1. was the first version of Nefilim.
Over the years, we have been monitoring malicious ransomware activities, including the actors behind the Nefilim and Nemty ransomware. Specifically, we tracked the group behind these ransomware families under the intrusion set “Water Roc.” Currently, we associate the underground actors jsworm and Jingo with Water Roc activity, and both actors have actively sold and supported Nemty in the past. Based on their activities online, both are believed to be Russian-speaking. Nemty’s code also contained lyrics from several Russian songs and artists. While we can’t state with full confidence that either of these two actors are still actively involved in Nefilim’s operations, we do believe that they were involved in Nefilim’s early development at the very least.
May 1, 2019
jsworm posts on the Exploit forum for the first time; JSWorm and RazvRAT go on sale
May 8, 2019
jsworm posts that RazvRAT is no longer for sale
Aug. 20, 2019
The Nemty ransomware affiliate program starts with 25 vacancies available
Sep. 6, 2019
Jingo advertised the Nemty ransomware on a verified Tor website
Oct. 9, 2019
Nemty ransomware version 1.6 is released
Dec. 11, 2019
Nemty ransomware version 2.3 is released
Jan. 20, 2020
Corporate links website launches the Nemty ransomware blog
Mar. 10, 2020
The initial Nefilim ransomware variant is compiled
Mar. 14, 2020
jsworm mentions starting a separate project
Mar. 25, 2020
Nephilim ransomware variant is compiled
Mar. 30, 2020
Nemty Revenue 3.1 is released on the Exploit forum
Apr. 14, 2020
jsworm shuts down the Nemty ransomware
Apr. 30, 2020
Nemty ransomware starts using Trickbot
May 31, 2020
Sigareta ransomware variant is compiled
June 11, 2020
Telegram ransomware variant is compiled
Jul. 2020
Nef1lim ransomware variant is compiled
Oct. 4, 2020
Merin ransomware variant is compiled
Dec. 2020
Fusion ransomware variant is compiled
Jan. 28, 2021
Milihpen ransomware variant is compiled
Feb. 27, 2021
Gangbang ransomware variant is compiled
Mar. 16, 2021
Mansory ransomware variant is compiled
*a complete version of this is available in the PDF
Conclusion
The breakdown of Nefilim’s tools, tactics, and processes reveals significant features regarding the modus operandi of modern ransomware:
We see that modern ransomware affiliates can find ways into large enterprises through access brokers, manage to exfiltrate large quantities of valuable data, and then try to extort victims in as many ways as possible. Operations like these are powered by evolved affiliate programs that give ransomware actors a hefty arsenal: customizable software, new and readily available technologies for better victim-targeting, and improved avenues for collaboration.
Corporations and network guardians have to stay ahead of the curve and be prepared for APT-level ransomware attacks, especially given the amount and value of data that many businesses have stored in their systems. Security investigators have a difficult task as well — they have to piece together actions from multiple groups: the intruders who first breach the network and the group that will try to move laterally and monetize the attack. The full kill chain becomes more complex because of the various groups that are involved.
Although there are challenges and complexities in shielding organizations from these threats, recent events show that even the most advanced malware families can be brought down. Cybersecurity is also evolving constantly, and always finds new ways to defend against these persistent threats.
To read more about modern ransomware, read our full report.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One