Ransomware Spotlight: BlackCat
Top affected countries and industries
according to Trend Micro data
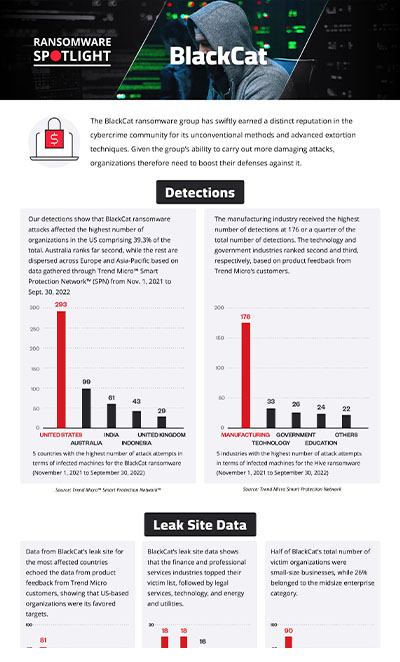
This section cites Trend Micro™ Smart Protection Network™ (SPN) data on BlackCat’s attempts to compromise organizations. Note that these detections pertain only to Trend Micro customers and consist of only a fraction of the victims found in BlackCat’s leak site. Our detections show that organizations in the US received the greatest number of BlackCat ransomware attacks, comprising 39.3% of the total. Australia ranks far second, while the rest are dispersed across Europe and Asia-Pacific.
Figure 1. 10 countries with the highest number of attack attempts in terms of infected machines for the BlackCat ransomware (November 1, 2021 to September 30, 2022)
Source: Trend Micro™ Smart Protection Network™ ™
The highest number of detections came from the manufacturing industry, with 176, or a quarter of the total.
Figure 2. 10 industries with the highest number of attack attempts in terms of infected machines for the BlackCat ransomware (November 1, 2021 to September 30, 2022)
Source: Trend Micro™ Smart Protection Network™
Targeted regions and industries
according to BlackCat’s leak site
This section provides information on the attacks recorded on the BlackCat group’s leak site which represents successfully compromised organizations that have declined to pay ransom as of this writing. Trend Micro’s open-source intelligence (OSINT) research and its investigation of the site show that from December 1, 2021 to September 30, 2022, the group compromised a total of 173 organizations.
Figure 3. The distribution by region of BlackCat’s victim organizations from December 1, 2021 to September 30, 2022
Sources: BlackCat’s leak site and Trend Micro’s OSINT research
Trend Micro’s product feedback on the top affected countries (shown on Figure 1) was consistent with data found in BlackCat’s leak site, which revealed that the group favored enterprises based in the US, with a victim count of 81 or 58.7% of the total. Also, organizations based in Europe and Asia- Pacific were among the most targeted by the group.
Figure 4. The distribution by country of BlackCat’s victim organizations from December 1, 2021 to September 30, 2022
Sources: BlackCat’s leak site and Trend Micro’s OSINT research
BlackCat’s leak site data suggests that in terms of industry, finance and professional services were the most hit, followed by legal services. Technology, energy and utilities, construction, materials, and manufacturing were also largely affected.
Figure 5. The distribution by industry of BlackCat’s victim organizations from December 1, 2021 to September 30, 2022
Source: Sources: BlackCat’s leak site and Trend Micro’s OSINT research
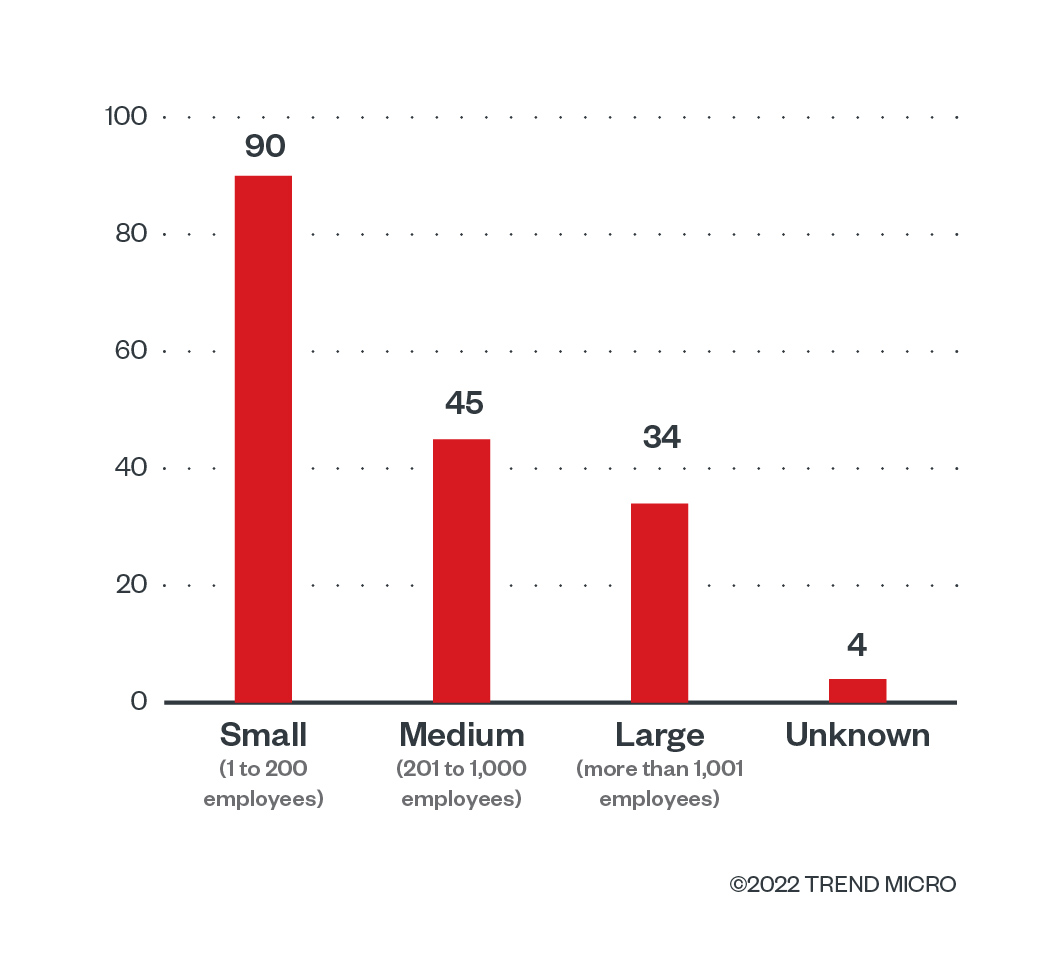
Small-size businesses make up 52% of BlackCat’s victims, followed by midsize businesses at 26%. Combined, they constitute more than three quarters of the gang’s preferred targets. This trend is expected to persist in the months to come.
Figure 6. The distribution by organization size of BlackCat’s victim organizations from December 1, 2021 to September 30, 2022
Source: Sources: BlackCat’s leak site and Trend Micro’s OSINT research
Infection chain and techniques
Initial Access
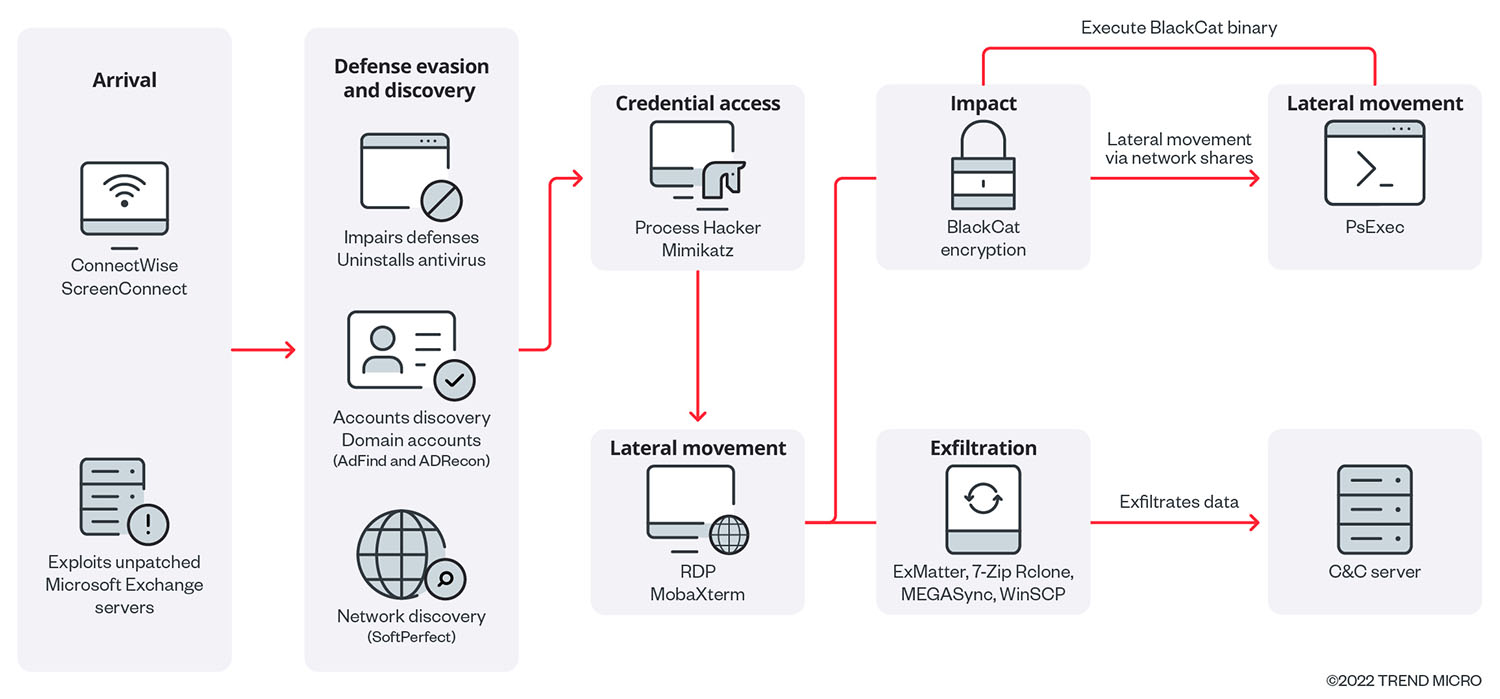
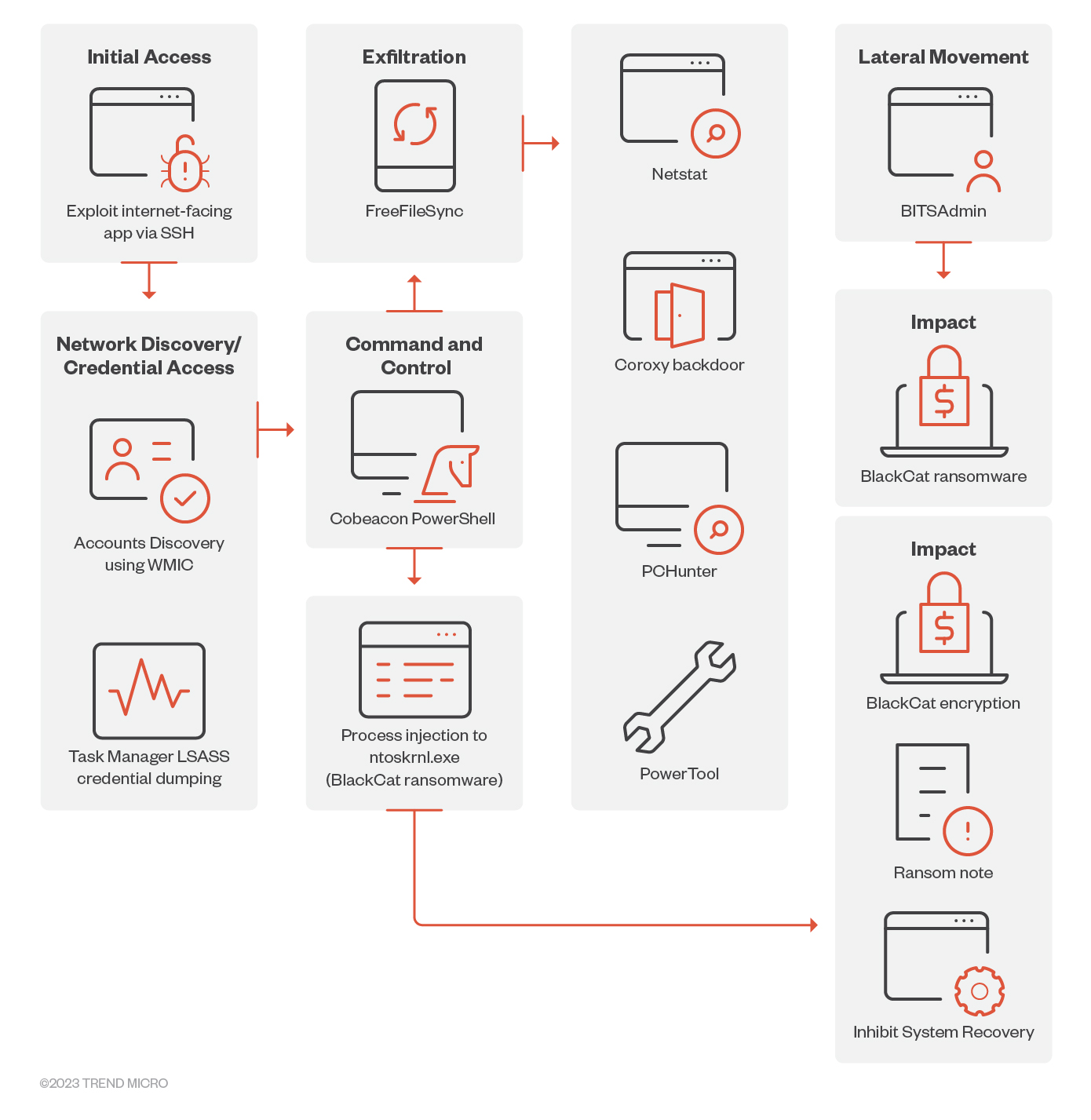
- Trend Micro detected the arrival of BlackCat ransomware through MS Exchange Server vulnerabilities, listed as CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065. The malware authors keep their access using remote code execution (RCE) via ConnectWise, a software solution designed for managed service providers (MSPs). This allows them to query credentials without passwords or other essential account information.
- We also found evidence of a possible initial entry of the threat actor that is related to exploiting SSH keys to establish foothold on the target’s machine.
- It should be noted that we cannot rule out other methods of initial access.
Execution
- Despite finding no evidence of the ransomware binary being executed on the machine, we observed that the encryption of files was carried out with ntoskrnl.exe as the parent process. This led us to believe that Cobeacon served as the conduit for the ransomware's execution by injecting the process into a Windows component (ntoskrnl.exe) to evade detection and ensure successful encryption of the victim's files.
Defense evasion, discovery, and credential access
- Upon gaining access to the network, the malicious actors impair the defenses of the target organization by uninstalling antivirus applications, using AdFind and ADRecon to get hold of the victims’ domain accounts, and SoftPerfect to find information about the victims’ network. BlackCat operators also leverage Process Hacker and Mimikatz to access and dump the victims’ credentials.
- To facilitate reconnaissance, privilege escalation, and lateral movement on the victim's network, threat actors also utilized WMIC and Netstat to extract information on user accounts and their associated Security Identifiers (SIDs). Additionally, the threat actors employed Task Manager to extract LSASS credentials.
Lateral Movement
- The BlackCat ransomware binary can propagate and execute laterally on its own by using an embedded PsExec module. Trend Micro has observed BlackCat operators accessing other endpoints in the victims' network for lateral movement using remote control applications like RDP and MobaXterm.
- Threat actors were also observed using BITSAdmin to copy what we believe is the ransomware binary onto other machines within the victim's network, using the following command: /transfer zzz \\ {redacted}\share$\zzz.exe %AppData%\zzz.exe. Other files with the following filenames are also copied using the same command: xxx.exe, yyy.exe, and sv.exe.
Command and Control
- A Base64-encoded PowerShell script with an embedded Cobalt Strike SMB beacon is used to inject the shellcode into memory and establish connection with the C&C via the following named pipes – \\ .\pipe\npfs_78, \\ .\pipe\fullduplex_9c.
Exfiltration
- Malicious actors also used ExMatter to steal information for double extortion, aside from their use of 7-Zip, Rclone,MEGASync, or WinSCP to archive stolen information, which they send to their C&C server. Trend Micro reports that threat researchers noted BlackCat’s use of an upgraded version of ExMatter published in September 2022.
- We also observed traces of FreeFileSync, a file synchronization and backup tool. We believe threat actors used this tool to exfiltrate valuable information from the victim’s machines weeks before the actual execution of the ransomware binary.
Impact
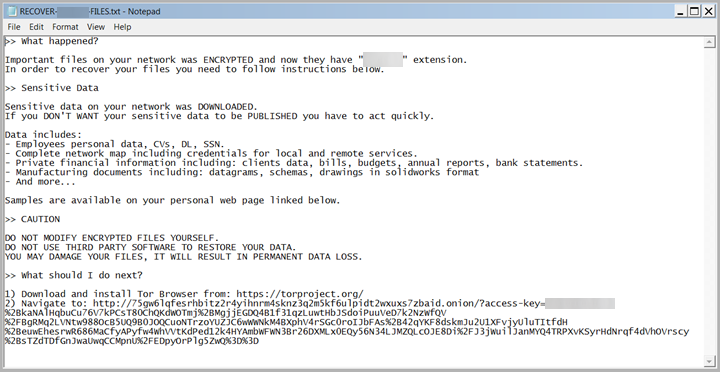
- The malicious actors’ use of Rust to deliver the ransomware payload sets the stage for its encryption routine . The ransomware binary defaces the system’s background image and replaces it with one containing a notification that important files had been downloaded and encrypted, plus information on where additional instructions can be found (see Figure 10).
- The payload also terminates specific services related to backups, antivirus applications, database, Windows internet services, and ESXi virtual machines (VMs).
- Trend Micro researchers also found another variant of BlackCat ransomware binary that restarts the affected system to safe mode before proceeding to its encryption routine. It also disables system recovery and deletes volume shadow copies to inhibit the recovery of the affected systems.
- For the Sphynx variant, the string appended for encrypted files is based on the ransomware binary's configuration so it should vary for each sample. The ransomware drops its ransom note in an archive format with randomized characters.
- Based on additional analysis, the Sphynx variant also inhibits system recovery by deleting volume shadow copies using the commands:
vssadmin.exe Delete Shadows /all /quiet and wmic.exe Shadowcopy Delete
Other technical details
BlackCat avoids the following directories:
- system volume information
- intel
- $windows.~ws
- application data
- $recycle.bin
- mozilla
- $windows.~bt
- public
- msocache
- windows
- default
- all users
- tor browser
- programdata
- boot
- config.msi
- perflogs
- appdata
- windows.old
It avoids encrypting the following files with strings in their file name:
- desktop.ini
- autorun.inf
- ntldr
- bootsect.bak
- thumbs.db
- boot.ini
- ntuser.dat
- iconcache.db
- bootfont.bin
- ntuser.ini
- ntuser.dat.log
It also prevents the encryption of files with the following extensions:
- themepack
- nls
- diagpkg
- msi
- lnk
- exe
- cab
- scr
- bat
- drv
- rtp
- msp
- prf
- msc
- ico
- key
- ocx
- diagcab
- diagcfg
- pdb
- wpx
- hlp
- icns
- rom
- dll
- msstyles
- mod
- ps1
- ics
- hta
- bin
- cmd
- ani
- 386
- lock
- cur
- idx
- sys
- com
- deskthemepack
- shs
- ldf
- theme
- mpa
- nomedia
- spl
- cpl
- adv
- icl
- msu
BlackCat terminates the following processes and services:
Processes:
- agntsvc
- dbeng50
- dbsnmp
- encsvc
- excel
- firefox
- infopath
- isqlplussvc
- msaccess
- mspub
- mydesktopq
- mydesktopservic
- notepad
- ocautoupds
- ocomm
- ocssd
- onenote
- oracle
- outlook
- powerpnt
- sqbcoreservic
- sql
- steam
- synctime
- tbirdconfig
- thebat
- thunderbird
- visio
- winword
- wordpad
- xfssvccon
- *sql*
- bedbh
- vxmon
- benetns
- bengien
- pvlsvr
- beserver
- raw_agent_svc
- vsnapvss
- CagService
- QBIDPService
- QBDBMgrN
- QBCFMonitorSe
- SAP
- TeamViewer_Service
- TeamViewer
- tv_w32
- tv_x64
- CVMountd
- cvd
- cvfwd
- CVODS
- saphostexe
- saposcol
- sapstartsrv
- avagent
- avscc
- DellSystem
- EnterpriseClient
- VeeamNFSSvc
- VeeamTransportSvc
- VeeamDeploymentSvc
Services:
- mepocs
- memtas
- veeam
- svc$
- backup
- sql
- vss
- msexchange
- sql$
- mysql
- mysql$
- sophos
- MSExchange
- MSExchange$
- WSBExchange
- PDVFSService
- BackupExecVSSProvider
- BackupExecAgentAccelerator
- BackupExecAgentBrowser
- BackupExecDiveciMediaService
- BackupExecJobEngine
- BackupExecManagementService
- BackupExecRPCService
- GxBlr
- GxVss
- GxClMgrS
- GxCVD
- GxCIMgr
- GXMMM
- GxVssHWProv
- GxFWD
- SAPService
- SAP
- SAP$
- SAPD$
- SAPHostControl
- SAPHostExec
- QBCFMonitorService
- QBDBMgrN
- QBIDPService
- AcronisAgent
- VeeamNFSSvc
- VeeamDeploymentService
- VeeamTransportSvc
- MVArmor
- MVarmor64
- VSNAPVSS
- AcrSch2Svc
MITRE tactics and techniques
| Initial Access | Execution | Defense Evasion | Credential Access | Discovery | Lateral Movement | Exfiltration | Impact |
|---|---|---|---|---|---|---|---|
T1078 - Valid Accounts T1190 - Exploit Public-Facing Application | T1059 - Command and Scripting Interpreter | T1562.001 - Impair Defenses: Disable or Modify Tools T1562.009 - Impair Defenses: Safe Mode Boot T1070.001 - Indicator Removal on Host: Clear Windows Event Logs | T1003.001 - OS Credential Dumping: LSASS Memory | T1087 - Account Discovery T1083 - File and Directory Discovery T1057 - Process Discovery T1135 - Network Share Discovery T1016 - System Network Configuration Discovery T1069 - Permission Groups Discovery T1018 - Remote System Discovery | T1021.002 - Remote Services: SMB/Windows Admin Shares | T1048 - Exfiltration Over Alternative Protocol T1567 - Exfiltration Over Web Service | T1489 - Service stop T1490 - Inhibit System Recovery T1486 - Data Encrypted for Impact T1491.001 - Defacement: Internal Defacement |
Summary of malware, tools, and exploits used
Security teams should watch out for the presence of the following malware tools and exploits that are typically used in BlackCat attacks:
| Initial Access | Defense Evasion | Discovery | Credential Access | Lateral Movement | Exfiltration | Impact |
|---|---|---|---|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
Recommendations
All indications of BlackCat’s malicious activities suggest that the ransomware group has predisposed itself to more aggressive attacks. Its penchant for unconventional methods, the sophistication of its techniques, and a growing affiliate base show that its operations are robust and will remain so in the future. This should give organizations more reasons to ensure that they are well informed and that they have security measures in place to ward off ransomware threats.
To protect systems against similar threats, organizations can establish security frameworks that allocate resources systematically to establish a strong defense strategy against ransomware.
Here are some best practices that organizations can consider:
Audit and inventory
- Take an inventory of assets and data.
- Identify authorized and unauthorized devices and software.
- Audit event and incident logs.
Configure and monitor
- Manage hardware and software configurations.
- Grant admin privileges and access only when necessary to an employee’s role.
- Monitor network ports, protocols, and services.
- Activate security configurations on network infrastructure devices such as firewalls and routers.
- Establish a software allowlist that only executes legitimate applications.
Patch and update
- Conduct regular vulnerability assessments.
- Perform patching or virtual patching for operating systems and applications.
- Update software and applications to their latest versions.
Protect and recover
- Implement data protection, back up, and recovery measures.
- Enable multifactor authentication (MFA).
Secure and defend
- Employ sandbox analysis to block malicious emails.
- Deploy the latest versions of security solutions to all layers of the system, including email, endpoint, web, and network.
- Discover early signs of an attack such as the presence of suspicious tools in the system.
- Use advanced detection technologies such as those powered by AI and machine learning.
Train and test
- Regularly train and assess employees on security skills.
- Conduct red-team exercises and penetration tests.
A multilayered approach can help organizations guard possible entry points into their system (endpoint, email, web, and network). Security solutions can detect malicious components and suspicious behavior, which can help protect enterprises.
- Trend Micro Vision One™ provides multilayered protection and behavior detection, which helps block questionable behavior and tools early on before the ransomware can do irreversible damage to the system.
- Trend Micro Cloud One™ Workload Security protects systems against both known and unknown threats that exploit vulnerabilities. This protection is made possible through techniques such as virtual patching and machine learning.
- Trend Micro™ Deep Discovery™ Email Inspector employs custom sandboxing and advanced analysis techniques to effectively block malicious emails, including phishing emails that can serve as entry points for ransomware.
- Trend Micro Apex One™ offers next-level automated threat detection and response against advanced concerns such as fileless threats and ransomware, ensuring the protection of endpoints.
Indicators of Compromise (IOCs)
The indicators of compromise (IOCs) for the threat discussed in this article can be found here. Actual indicators might vary per attack.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization


 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One