Spam Campaign Delivers Malware via .WIZ, Targets Banks
By Marshall Chen, Loseway Lu, Rubio Wu
Trend Micro researchers recently discovered a new spam campaign being distributed with a downloader under the guise of
Trend Micro has observed this spam campaign sending email to several email addresses associated with banks. WIZ is short for Wizard files used to guide users through steps on how to perform intricate or repetitive document types or tasks in Microsoft programs. Threat actors may have chosen the banking industry as its target because of its use of Wizards for processing documents such as bank and billing statements, and guiding their customers on filing income tax returns. Threat actors may have abused this to easily trick bank customers into accessing
This
Trend Micro also observed and closely monitored
[READ: Spam Campaign Abusing SettingContent-ms Found Dropping Same FlawedAmmyy RAT Distributed by Necurs]
Infection Chain, Behaviors
This malware campaign has two file attachments with the following infection chains:
Attachments
Threat actors send victims a spam email with 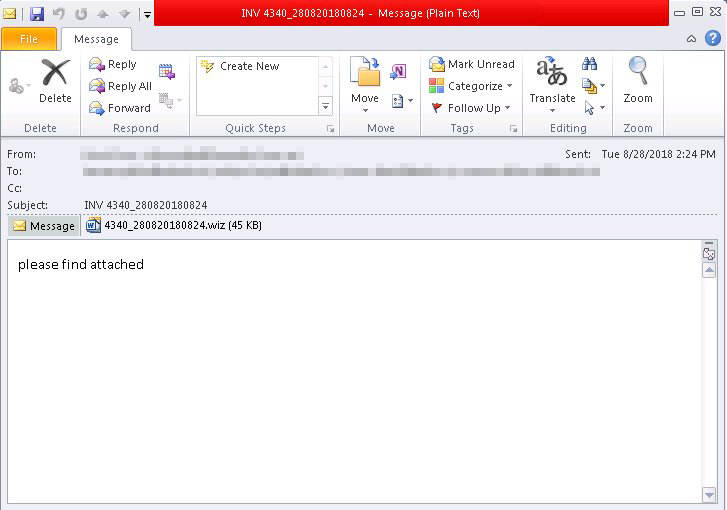
Figure 1. A screen capture of a
Once recipients open
Attachments
A 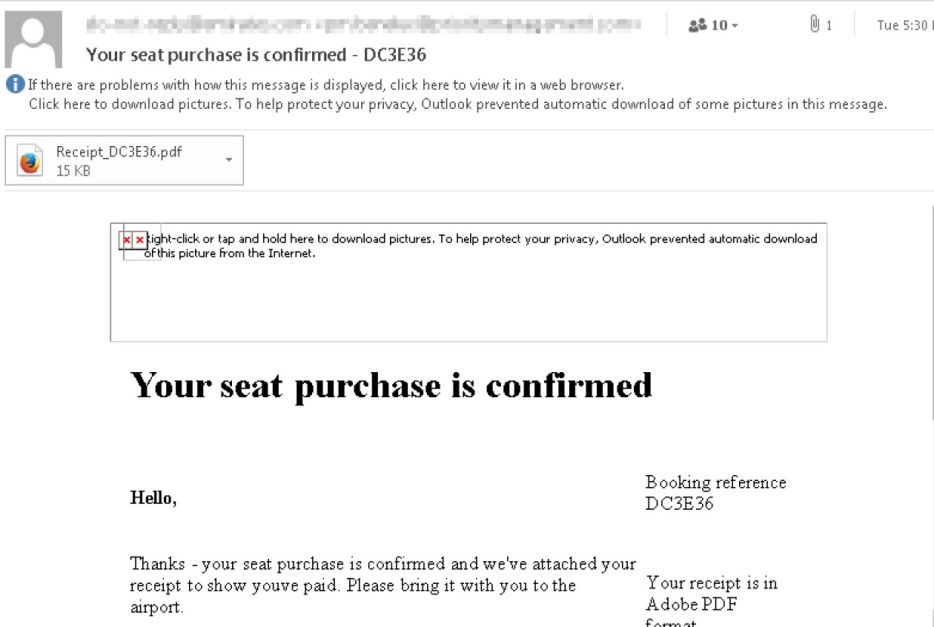
Figure 2. A screen capture of a fake booking confirmation email with
Once the recipient opens
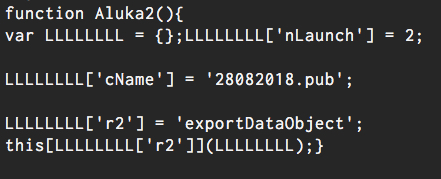
Figure 3. JavaScript inside the
The .PUB file hosts malicious macros that will then download a portable executable file from a malicious website.
After analyzing both infection chains, Trend Micro researchers discovered that both
The backdoor can execute several commands such as executing PowerShell and file system commands, code injection, uploading and downloading files, and using and purging Kerberos tickets, among others.
The results of the commands below are sent via DNS back to the C&C server:
- cmd.exe /C net view /all – finds all the computers that are visible on the network.
- cmd /
C arp – displays current ARP entries by interrogating the protocol data. - cmd /C tasklist /V – displays currently running processes on the computer.
The backdoor can also steal a user’s machine information such as computer name, IP address, OS system, and username, and malware process ID, to name a few.
Trend Micro Solutions
For protection against spam and threats, enterprises can take advantage of Trend Micro™ endpoint solutions such as Trend Micro Smart Protection Suites and Worry-Free™ Business Security. Both solutions protect users and businesses from threats by detecting malicious files and spammed
Trend Micro™ Hosted Email Security is a no-maintenance cloud solution that delivers continuously updated protection to stop spam, malware, spear phishing, ransomware, and advanced targeted attacks before they reach the network. It protects Microsoft Exchange, Microsoft Office 365, Google Apps, and other hosted and on-premises email solutions. Trend Micro™ Email Reputation Services™ detects the spam mail used by this threat upon arrival.
Trend Micro™ OfficeScan™ with XGen™ endpoint security infuses high-fidelity machine learning with other detection technologies and global threat intelligence, offering comprehensive protection against advanced malware.
Indicators of Compromise
| SHA256 | PAYLOAD |
| f3ce17bba51df5f14fa5ac09b9861856bfe6a3bc2646953185ca8edf43dd430e | W2KM_DLOADER.WIZ |
| 1eb0769c885d9a5583c603b0c2605978ec6da80a649df82663d7f30234492bdf | PDF_MDROP.E |
| bd358762e051bce7fbfc5b7cc6850e6ec34010b019ec86dc4c976cdfa3b9f55e | P2KM_DLOADR.YSU |
| 4c6e89bfb50d63f623bb71e3e1a449ef3b2fa7901776db8270a448be6589caba | BKDR_COBEACON |
With additional analysis by Noel Llimos, Kawabata Kohei and Anita Hsieh.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One