Compliance & Risks
Guidelines to secure factories 3: NIST CSF
The purpose of this series is to explain typical examples of general-purpose guidelines for ICS and OT security and understand the concepts required for security in smart factories. Part three explains the NIST Cyber Security Framework (CSF).
Posts in this series
- Part 1: IEC62443 overview
- Part 2: IEC62443 system
- Part 4: NIST SP800
- Part 5: CIS Controls
- Part 6: MITRE ATT&CK
The purpose of this series is to explain typical examples of general-purpose guidelines for ICS and OT security and understand the concepts required for security in smart factories. Part 3 explains the NIST Cyber Security Framework (CSF).
What is the NIST CSF?
The NIST CSF is a cyber-security framework issued by US National Institute of Standards and Technology (NIST). Originally, the initial version was released in 2014 to protect the US government and critical infrastructure. It has been developed with general usage in mind, regardless of critical infrastructure. It has been published for free, and widely referenced by other countries and ordinary companies as a guideline. In the IT security world, it has been used in many cases as a standard. It is a widely-recognized framework.
The NIST CSF focuses on considering cyber-security risks as part of the risk management process of an organization. Its document consists of three parts: Core, Tier, and Profile.
- Core: The classification of measures. This consists of five functions, 23 categories, and 108 subcategories.
- Tier: A level where an organization manages risks. The level of a practice is indicated in four tiers.
- Profile: The status of measures in a specific environment. Measure a gap between the current profile and the target profile, and then make a road map.
Core: A classification of measures
Core is classified into five Functions.
- Identify: Which processes and assets should be protected?
- Protect: What kind of protection can be applied?
- Detect: How to identify an incident?
- Respond: How to reduce the influence of an incident?
- Recover: How to recover a function?
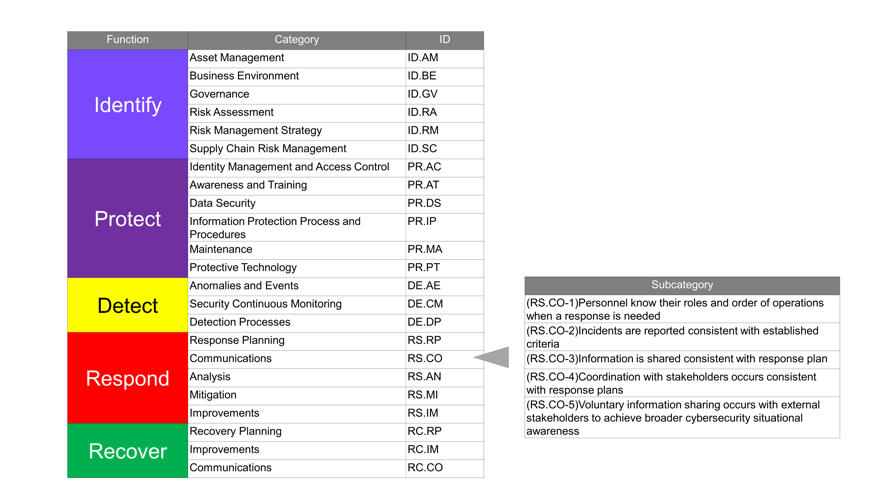
The categorization of measures assumes that incidents will occur, and the characteristics are sufficient post-incident measures as follows: "Detect," "Respond," and "Recover." In addition to measures for preventing the occurrence of incidents, organizational capabilities are also required when finding an incident, minimizing its impact, and recovering from the incident.
Function and Category are expressed with relatively plain words, without using technical jargon. The reason is that these words are intended to be used as common words in communication between different backgrounds or layers. There is an intention that by using the same words, it is possible to facilitate communication between board of directors, middle-management people and technical engineers in the field, and discussions with people in departments that do not specialize in cyber-security and risk management.
In the update to ver. 1.1 in 2018, "Supply Chain Risk Management" was added to "Identify."
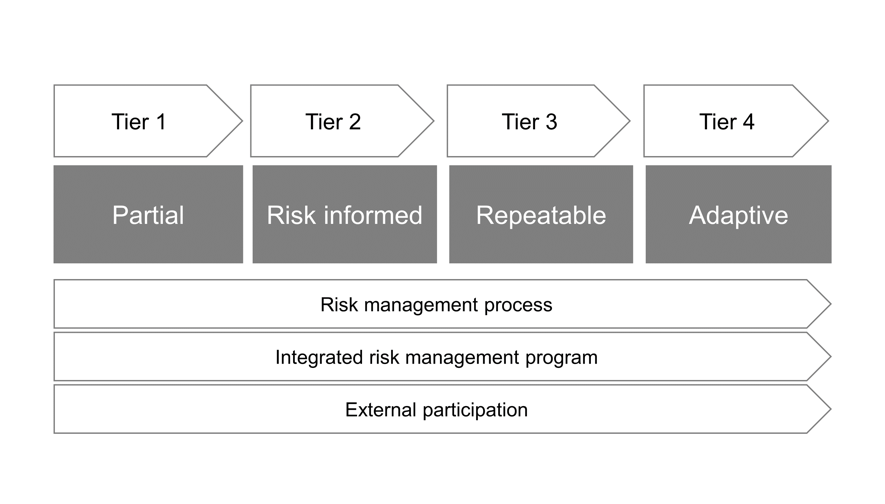
Tier: The level of security
Tier indicates the practice level of a process where an organization manages cyber-security risks, in four levels as shown below:
Tier 1: Partial
Tier 2: Risk informed
Tier 3: Repeatable
Tier 4: Adaptive
Although this is a slightly rough interpretation, the images of these tiers are as follows: Tier 1 is an impromptu action, in Tier 2, risks are recognized and handled in the field, in Tier 3, risks are documented and reviewed periodically, and in Tier 4 potential risks are handled actively and positively.
In documents, Tiers are defined from the following three viewpoints.
- Risk management process: Management functions and reproducibility
- Integrated risk management program: In various risk managements, cyber is considered
- External participation: Sharing to/from the outside of the organization
Tiers are measured, from a viewpoint of the reproducibility of processes and risk management, except cyber-security, or active participation in communities outside the organization.
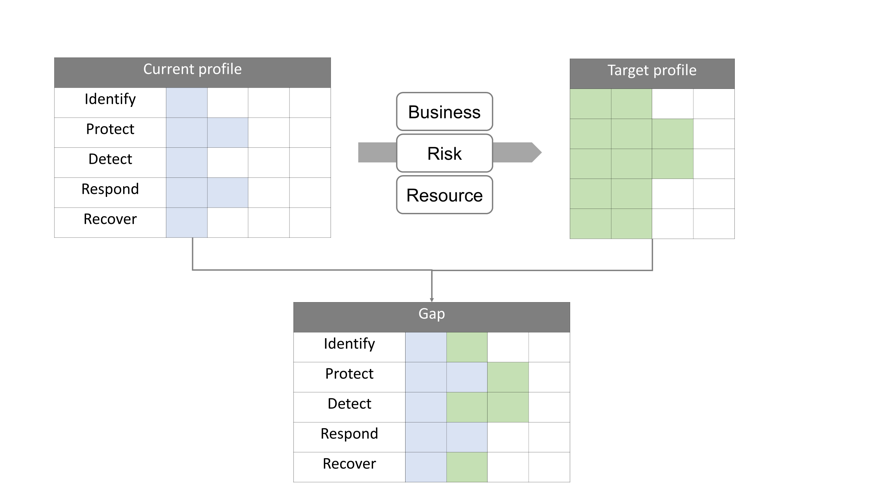
Profile: Status of security
Profile is a concept that indicates a status. The situation of measures for functions, categories, and sub-categories is created according to organization-specific environments. The point is that it is possible to establish a road map for a gap by creating the current profile and a target profile. If content obtained by inspecting the situation of current measures is considered as a current profile, then create a target profile by checking the current profile against business requirements, risk tolerance, and resources as targets. By comparing the current profile with the target profile, it is possible to create the list of priority, magnitude of gap, and cost of enforcement plan, which would be helpful when making a resource plan.
Examples of usages
In the documents of the NIST CSF, some usage examples are also described.
Basic Review of Cybersecurity Practices
Make an inspection by checking against the current status of measures, and consider an improvement plan. Use Core as a shared language that will be the base of communication.
Communicating Cybersecurity Requirements with Stakeholders
Submit the target profile to an external service provider. As SCM, identify, evaluate, and reduce "products and services including a function which may be a malicious function, fake products and services, or products and services that are vulnerable due to insufficient production or development practices in a cyber supply chain."
Buying Decisions
Evaluate requirements with high priority, and products/services supporting items with large gaps. Achieve the target by combining not only products but also operations.
General steps for building/improving risk management processes are also described, and the following procedure is repeated if necessary.
- Prioritize and scope: Determine the business line and process to be targeted.
- Orient: Identify the specific system, assets, and organization that are related to the target.
- Create a Current Profile: Understand the achievement status of the category and subcategory of a Core.
- Conduct a Risk Assessment: Evaluate the possibility of the occurrence of a security event and its impact.
- Create a Target Profile: Make a target profile (with external stakeholders also in mind).
- Determine, Analyze, and Prioritize Gaps: Identify a gap, and make a plan for achieving the target (with costs, benefits, and risks in mind).
- Implement Action Plan: Implement the plan.
Applying to the manufacturing industry
Documents that help you to apply the NIST CSF to the manufacturing industry have also been published. These documents describe target profiles (target status) focusing on the manufacturing industry, and are helpful when you make a security road map in the manufacturing industry by using the NIST CSF.
The documents are described with consideration of five missions in the manufacturing industry, which are based on human safety, environmental safety, product quality, production target, and the protection of confidential information in sales. For each Core and Category, target profiles that are classified into three levels are described. From several viewpoints, guidelines based on influence are also indicated for the level classification (fatal and injury-causing accidents, finance, environment, discontinuation of production, corporate image, manufacturing products, small classification of industry sectors). Therefore, the classification can be used as a guide for setting a target in the manufacturing industry.
*References:
Cybersecurity Framework Manufacturing Profile
https://www.nist.gov/publications/cybersecurity-framework-manufacturing-profile
The NIST CSF is a framework, and the NIST CSF itself is not criteria or regulations. It does not mean that observing descriptions is a correct solution. It is prepared to support the self-assessment of security activities and return on investment depending on circumstances specific to each organization.
The NIST CSF has become widely used in a short time in many regions, industries, and organizations. It can be said that the biggest factor is that it is described in intelligible terms, such as Core and Category, and is easy to use as a shared language.
In the security of a smart factory, communication between stakeholders is a big issue. The NIST CSF has been widely accepted. Viewed from the opposite side, the reason may be that people with various backgrounds and roles have a growing need for the enhancement of their relationships, from various viewpoints such as IT and OT departments, engineers in the field, middle-management and management layers, system integrators, and cloud service providers.
Part 4 will deal with the NIST SP800 series, which is a guideline where specificity is increased according to the NIST CSF.
*References
NIST Cybersecurity Framework
https://www.nist.gov/cyberframework
An Introduction to the Components of the Framework
https://www.nist.gov/cyberframework/online-learning/components-framework

