Cyber Threats
Dilemma of smart factory 4: Security by design
This series of blog posts explains the design security risks involved in legacy languages and risk mitigation measures that all users of industrial robots should take. This part cosider what measures each industrial robot stakeholders should take.
Industrial robots are the core of the automation of manufacturing processes in smart factories, and are the most important components as they support the manufacture of all kinds of products such as automobiles, aircraft, processed foods, and pharmaceuticals. In addition, as equipment that realizes unmanned manufacturing in the post-COVID-19 world where minimal or no contact is a necessity, the importance of industrial robots that can repeatedly execute specified movements with high accuracy is regaining attention. However, it is not commonly known that industrial robots are programmed using languages designed decades ago. Trend Micro has been conducting cybersecurity research on smart factories since 2017, and discovered vulnerabilities in "task programs" that define the behavior of industrial robots and also design flaws in "programming languages." These languages are legacy languages that were designed decades ago, but they continue to be used for purposes such as maintaining compatibility with successor models and reducing the burden of re-learning, and are a technology that is still being used in modern smart factories. In this series, based on the results of our third joint research project with the Polytechnic University of Milan, from a short to long-term perspective, we analyze the design security risks involved in legacy languages and risk mitigation measures that all users of industrial robots should take. In this final installment, we will consider what measures each industrial robot manufacturer, integrator, and user should take, and present, from a short-term to long-term perspective, how to overcome factory-specific issues and implement security.
A modern smart factory environment where the assumptions of 20 years ago do not apply
Factory environments have traditionally been "closed" network spaces. In other words, it was an environment in which network communication with the outside and its effects were not considered (or did not need to be) on the premise that only the people who work there would touch the factory equipment. The industrial robots that were the subjects of this empirical study were designed on the same premise.
However, in today's world where network connectivity is advancing even in factory environments, that premise is a thing of the past. In order to improve productivity and reduce the ratio of defects, which are critical issues for factories, and to maintain employee safety and business continuity even during the COVID-19 pandemic, smart manufacturing processes using digital technology will become the industry standard. When that happens, factories are also exposed to the risk of cyberattacks. Software runs everywhere in smart factories and is connected to the network. In addition, not only user companies but also system integrators, consultants, manufacturers of industrial robots, etc., who are the subjects of this study, are involved in the development and supply of such software in a complicated manner. Therefore, the efforts of the entire ecosystem are required to realize safe smart factories. In other words, it is important for each user, integrator, and manufacturer to "make safe software" and thus "keep software safe".
Implementing risk mitigation measures from a short- to long-term perspective
The security concerns presented in this series are deeply rooted in the basic technology of industrial robots, making it difficult for manufacturers to immediately replace it with another technology or make corrections. Therefore, in addition to protecting the existing environment as a short-term measure, it is recommended that the stakeholders involved in industrial robots should gradually and systematically implement risk mitigation measures in anticipation of future smartness as a medium- to long-term measure. Figure 1 shows Trend Micro's recommended stakeholder-specific step-by-step risk mitigation measures. In order to make smart factories more secure, it is important for field engineers, system integrators, and industrial robot manufacturers to implement their respective security measures. Below, let's take a closer look at short- to long-term countermeasures.
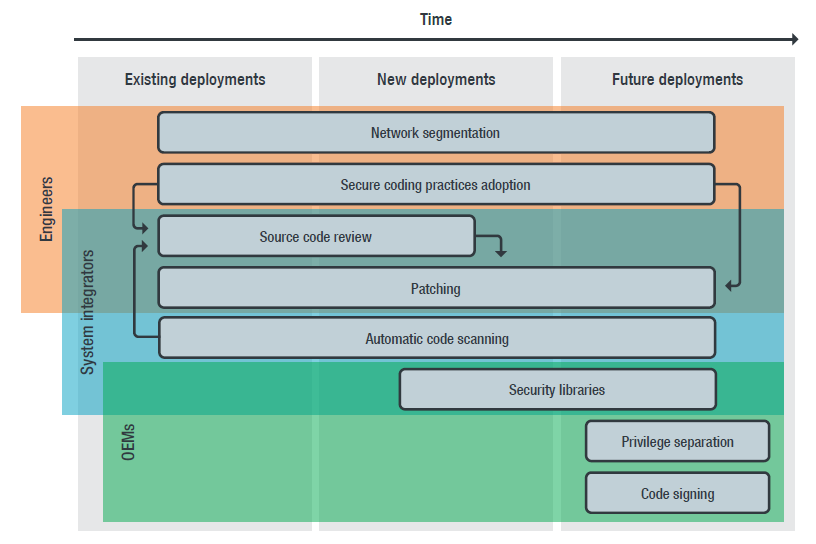
<Fig. 1> Stakeholder-specific step-by-step risk mitigation measures
Short-term measures
As explained in the previous article, it would be extremely difficult to solve the security risks of industrial robots from the ground up in a short period of time. Therefore, in the short term, it is a realistic solution to minimize the risk at the field level on the premise of retaining the security flaws that are explained in this series.
The key players in implementing short-term measures are the control process engineers in the field and the system integrators who actually write, implement, and operate task programs. Field engineers on the user side must ensure that network segmentation is performed to minimize the damage if a task program of an industrial robot is abused. This action significantly reduces network-related security risks. In addition to these essential security measures, protection of networks and endpoints is recommended to minimize the risk of being vulnerable to or being infected with malicious code. In addition, although details will be described later, secure coding practices are also indispensable for users. If you perform development with a system integrator, try to share a similar security policy with them. Source code reviews, bug fixes, and creation of appropriate source code control processes are both basic and effective measures.
Medium-term measures (Security measures in new environments)
In addition to the above short-term measures, a security library for industrial robot programming languages can be given as a medium-term measure with a view to protecting new environments. Security libraries include, for example, encryption libraries. At this stage, the key players are system integrators and industrial robot manufacturers. By implementing such security measures in higher development, on-site developers can easily implement input value verification and authentication functions without spending time adding new processes.
In addition, system integrators and industrial robot manufacturers should implement motion server references. By implementing such references, developers do not have to check each piece of motion data processing code for defects one by one. Typical examples of such reference implementations are Mitsubishi Electric's native motion server and Kuka's EKI. In addition, as a countermeasure against defects found in source code reviews, system integrators should consider providing proactive patches for task programs that may contain vulnerabilities.
Long-term measures (Security measures for the entire future market)
In the future, the efforts of manufacturers will be essential to ensure that the designs of programmable industrial robots are safe. For example, in an industrial robot platform (controller), it will be essential that security functions (such as authentication, access control, encryption, etc.) are incorporated into programming languages. The runtime in an industrial robot controller must implement fine-grained privilege separation that leverages an authorization system. An effective way to reduce the effects of vulnerabilities and malicious code is to limit the execution of functions to privileged directives only. On top of that, developers also need to make others aware of these usage limits in advance, similar to the process we saw in the Android app development example.
Last, but not least, code signing is the only way to ensure that code for industrial machines has not been tampered with. Code signing is not easy to do, but using this measure makes it possible to ensure that the code is exactly what the original developer wrote. Implementing code signing in factory equipment has a long way to go, but if market needs continue to drive innovation that favors integration and flexibility, it should be possible to achieve more dynamic automation code implementation in shorter cycles. This should speed up development and reduce the amount of time spent manually checking programs. Task programs that are written securely also reduce the chances of vulnerabilities being created. This, in turn, reduces the risk of programmable industrial machines being exposed to external attacks. In fact, there are already a number of safety-conscious coding guidelines for general-purpose programming languages. As the integration of IT and OT progresses, over the coming decade, the industrial engineering industry may face the same challenges that the IT software industry faces today. Now is the time to start implementing and establishing secure coding processes at the same level.
Responsibility as a security specialist
Factory security is a medium- to long-term strategy that cannot be handled completely by one company. It can be said that users, integrators, manufacturers, and security vendors should work together to implement solutions with the aim of improving the security level of the entire ecosystem. And Trend Micro is one of the security vendors aiming for the same goal.
Trend Micro has been focusing on research and development for the integration of IT and OT (Operation Technology) for many years. Security solutions for factory environments, which have been expanded since 2020 and are being deployed around the world, have been devised to realize network segmentation, which is the core short-term measure, without changing the settings of existing environments. In addition to this, we provide a group of solutions that protect entire factory environments, such as IPS that prevents intrusion from IT/OT connection points, detection tools that enable internal monitoring in factory networks, and industrial endpoint protection products. In addition, the effectiveness of these security solutions is supported by the accumulation of advanced threat research such as that introduced here.
In addition, Trend Micro was able to participate in the "ROS-Industrial (ROS-I) Consortium" as a result of this study, and will be involved in the promotion of safe development of industrial robot applications in Industry 4.0 over the medium to long term. In this study, Trend Micro discovered a security problem affecting the ROS-I driver that controls industrial robots, and in response, proceeded to investigate it in collaboration with the ROS-I Consortium. This joint investigation found that an attacker could compromise the communication interface of a motion server program running on the ROS-I driver and the controller of an industrial robot. In this case, the recommended remedy is to configure the network appropriately. In this regard, the ROS-I Consortium has published a report to help users improve their security. In addition, the Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) of the US Cybersecurity and Infrastructure Security Agency (CISA) emphasized the significance of the results of this investigation and issued a report approving recommended mitigation measures. Trend Micro not only provides security solutions, but also contributes to improving the security level of the entire ecosystem by sharing the results of research that utilizes its expertise.
Aiming for "security by design" for the entire ecosystem
Through the four parts of this series, we have analyzed the task programs and programming languages of industrial robots from the perspective of cybersecurity, and clarified the issues facing modern industrial robots. At this point, although it may be difficult to take all possible measures needed to address the security issues identified in this survey, it is possible for manufacturers, integrators, and users to work together to reduce these risks to an acceptable level.
Cybersecurity measures in factory environments are in the process of being transformed. Within 10 years at the latest, smart factories that assume network connectivity with the outside world will become commonplace. At that time, the industrial automation industry is likely to face the same challenges that the modern IT software industry faces. But there is still time. There are many things each player can do from this point on in preparation for that time.
We hope that this study will serve as a reference for everyone who will be creating the future of smart factories.
Appendix: Checklist for secure programming
Adhering to a safe development process based on a programming guide is one basic measure, but it has not yet become established as a common measure in the industrial robot market. Industrial robots are computers that execute programs, and control process engineers are programmers. And as long as the programmer is human, the chances that the written code will be insecure cannot be eliminated. Therefore, task programs, like any computer systems, should be checked to ensure that they are secure. This section provides security checklists to help control process engineers and system integrators develop and evaluate task programs.
The following is a list of check items for control process engineers and system integrators to use when they are writing task programs. Please use it when developing a task program.
----- Checklist for when writing a task program -----
- Recognize that industrial machines are computers and task programs are exploitable code.
- All communication is subject to authentication.
- Access control policies are implemented.
- Input is validated as needed.
- Output information is always scrutinized.
- Appropriate error handling is performed without disclosing unnecessary details.
- Appropriate configuration and placement procedures are implemented.
- There is a change control process in place for industrial task programs.
In addition, the factory security officer of the user company must clarify the items to be evaluated regarding the expected control level of the task program to be outsourced before actually outsourcing the creation of a task program to an integrator. To encourage the implementation of appropriate security functions, users should clearly inform the integrator of the following:
----- Checklist for when outsourcing task program development -----
- If the task program will receive data from outside the controller of the industrial robot.
- If the task program will generate data that is processed outside the controller of the industrial robot.
- If the task program is static over time. If there an upgrade procedure to change whether the task program is static. If the module will be loaded while the main program is running.
- Who implemented the task program.
- Who has access to the task program before it is transferred to the controller of the industrial robot.
- Who is the system user authorized to run, load, and modify task programs during normal operation.

