Next-Gen Payment Processing Technologies: What They Are, and How They Work
 Thanks to advances in technology, we no longer have to bring that much cash around on hand with us to buy the things we need and want. The most we need to make room in our wallets and purses for are some plastic cards, or better yet, none at all, if we already have our smartphones with us. And with it just a few more months until the holiday season—where there will obviously be a lot of money changing hands—we’re running a series of articles that tackle each modern payment system currently in use right now. What they are, how they work, and what their pros and cons are.
Thanks to advances in technology, we no longer have to bring that much cash around on hand with us to buy the things we need and want. The most we need to make room in our wallets and purses for are some plastic cards, or better yet, none at all, if we already have our smartphones with us. And with it just a few more months until the holiday season—where there will obviously be a lot of money changing hands—we’re running a series of articles that tackle each modern payment system currently in use right now. What they are, how they work, and what their pros and cons are.
But before we can get to those newer payment systems, let’s look at one of the oldest electronic payment systems—traditional credit cards. This’ll not only help us understand more of the processes involved in such a system, but also the advantages and the disadvantages that come with them.
The Credit Card Payment System
First issued in 1966 by Mastercard in the US, the common credit card payment system is a type of electronic payment system that involves the use of a plastic card with a magnetic stripe (or more recently, a chip) that retains information of the cardholder’s credit account made with a bank or other financial institution. The cardholder uses the card to pay for products and services in lieu of cash, and the transactions are logged by the bank as debt to be paid off at a predetermined time.
Who is involved in the credit card payment system?
To fully explain how credit card systems work, we need to explain the relationships between the parties involved in this payment system:
- Consumer: The cardholder who purchases goods and services using the credit card.
- Merchant: Goods and services provider who accepts credit card payments.
- Issuer: Bank or financial institution that issues credit card to consumers.
- Acquirer: Bank that processes and settles merchant’s credit card transactions with an issuer.
- Card brand: Visa, Mastercard, American Express (AMEX). These are brands whose networks are used to facilitate interactions between acquirers and issuers when authorizing and settling transactions.
- Payment Service Provider (PSP): A third party service provider who handles payment transactions between merchants and multiple acquirers.
- Payment Switch: In-house or third party service providers who provide routing services between merchants and multiple PSPs.
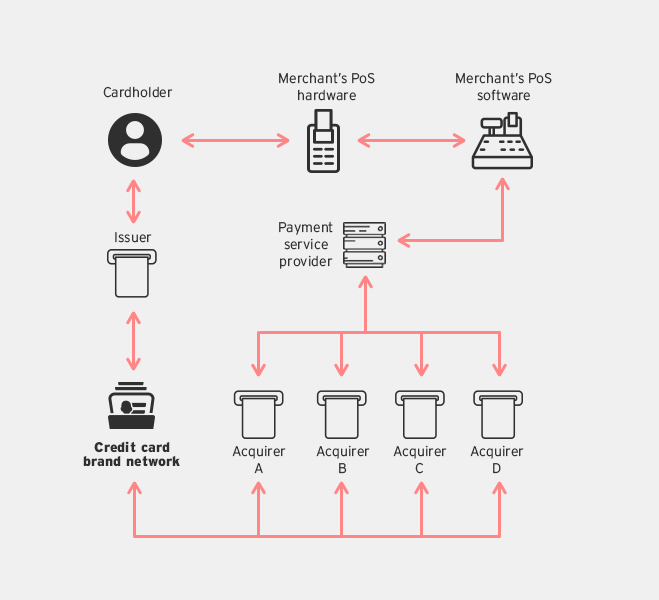
Transaction flow model for regular merchants
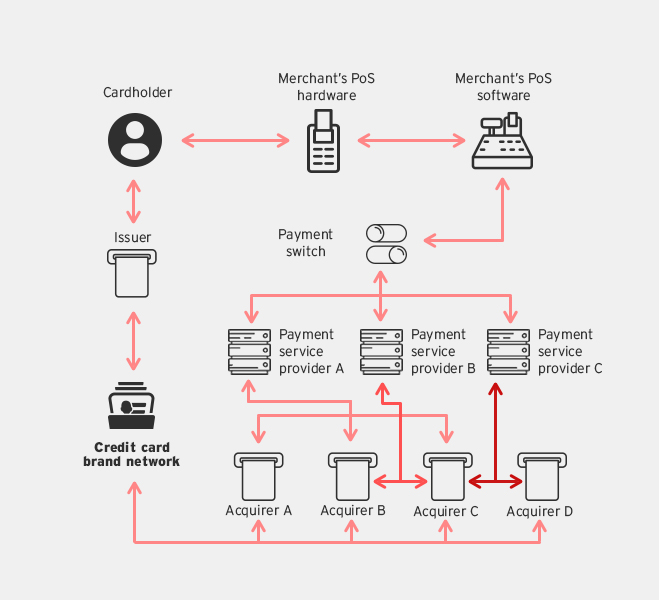
How do credit cards work?
Here's the typical process that takes place after a credit card is swiped:
- The consumer swipes their credit card on the merchant’s Point-of-Sale (PoS) terminal to purchase goods and services.
- The PoS terminal reads the magnetic stripe on the card, and then sends the credit card information to the merchant’s PoS system.
- The PoS system then contacts the PSP, who, depending on the card brand used will contact a designated acquirer for transaction authorization.
- The acquirer uses the card brand’s network to contact the issuer of the credit card.
- The issuer returns an authorization status to the acquirer using the card brand’s network.
- Finally, the acquirer passes the authorization to the PSP who forwards it to the PoS system, which then completes the transaction.
All of this happens in a matter of seconds, and thanks to breakthroughs in online technology it is a very reliable payment process that is easily available nearly everywhere in the world.
What are its advantages?
One of the key advantages of using a credit card is that consumers can defer paying for their purchases at a later time. This is especially convenient when a consumer finds themselves without cash at the moment of purchasing. There’s also the fact that many banks allow cardholders to pay their incurred credit card debt in installments or increments.
It's also widely accepted globally, so a consumer isn’t completely out of luck if for some reason they are left with only their credit card in a foreign country, provided they do accept their brand of card.
What are its disadvantages?
Since the boom of e-commerce, credit cards have been the target of many cybercriminals who have designed many malware and phishing schemes to steal banking credentials. But credit cards also has its share of offline threats with the proliferation of card cloners—retail PoS devices that have been tampered or altered to retain the information of cards that have been used on them. The simplicity of the traditional magnetic stripe card has made it easy for criminals to use these methods and devices to collect that information for their own gain—such as the use of the stolen credit card information to pay for their own purchases, i.e. credit card fraud.
PoS RAM scrapers are malware designed to do the same exact thing as card cloners, but without the need for a device or physical access to the machine. The malware infects retail PoS devices and sends the information remotely to cybercriminals.
Finally, a cardholder’s credit card being stolen or lost can also lead to unauthorized charges, but thankfully credit card companies have developed policies to protect their customers from such unfortunate incidents. At worst, a consumer will only need to fill out forms to declare that their cards have been used without their permission.
Next-Gen Payment Processing Technologies
The numerous threats that have preyed on the traditional credit card payment system, coupled with new technology, has led to the development of different payment processing technologies that not only allow for more convenient transactions, but also ones that are more secured. Click on the links below to read about the new technologies, how they work, and their advantages and disadvantages.
- EMV Credit Cards – Also called Chip-and-PIN cards, these cards feature a chip that stores a cryptogram that detects modified transactions. It also requires a PIN for extra authentication.
- Contactless RFID Credit Cards – This payment technology uses passive Radio Frequency Identification that allows cardholders to wave the cards in front of RF terminals to complete transactions.
- Mobile Wallets – First launched in Japan in 2004, this technology works on NFC enabled smartphones, and has since been implemented by Google and Apple through their mobile platforms.
- New Payment Processing Architectures - three next-gen architectures designed to improve secure mobile payments.
- Encryption and tokenization
- Cloud-based PoS systems
- Secure Element systems.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- AI Skills as an Emerging Attack Surface in Critical Sectors: Enhanced Capabilities, New Risks
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One