Ransomware Recap: The Week of WannaCry
 After a few of weeks of relatively low ransomware activity, the week of May 13-19 was an explosive one, as the widely publicized ransomware known as WannaCry (Detected by Trend Micro as RANSOM_WANA.A and RANSOM_WCRY.I) managed to infect thousands of systems across multiple industries around the world.
After a few of weeks of relatively low ransomware activity, the week of May 13-19 was an explosive one, as the widely publicized ransomware known as WannaCry (Detected by Trend Micro as RANSOM_WANA.A and RANSOM_WCRY.I) managed to infect thousands of systems across multiple industries around the world.
WannaCry was first detected back in April, where it was discovered using file hosting service Dropbox as part of its propagation method. The new variant leverages MS17-010, a vulnerability in the Windows Server Message Block (SMB) with an exploit—code-named EternalBlue—to deliver its payload, which includes the ransomware file. Affected files in the target system would then be encrypted with a .WNCRY affix.
The ransomware’s infection flow is shown in this diagram: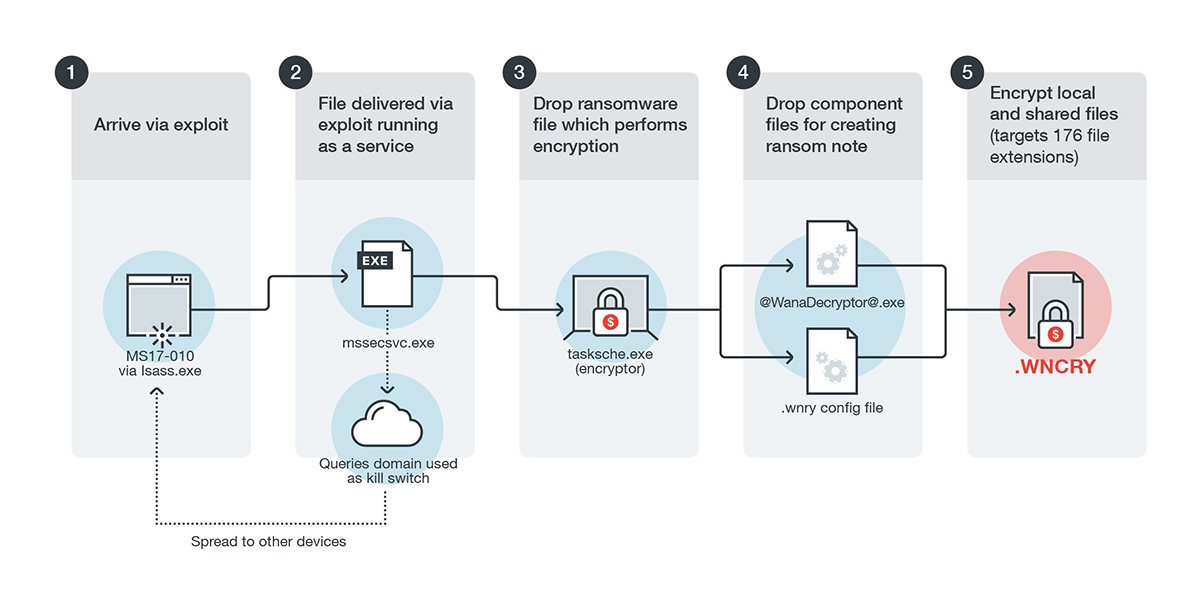
The ransom note will also be dropped into the system, asking for $300 for file decryption. This amount increases gradually after certain time limits are hit: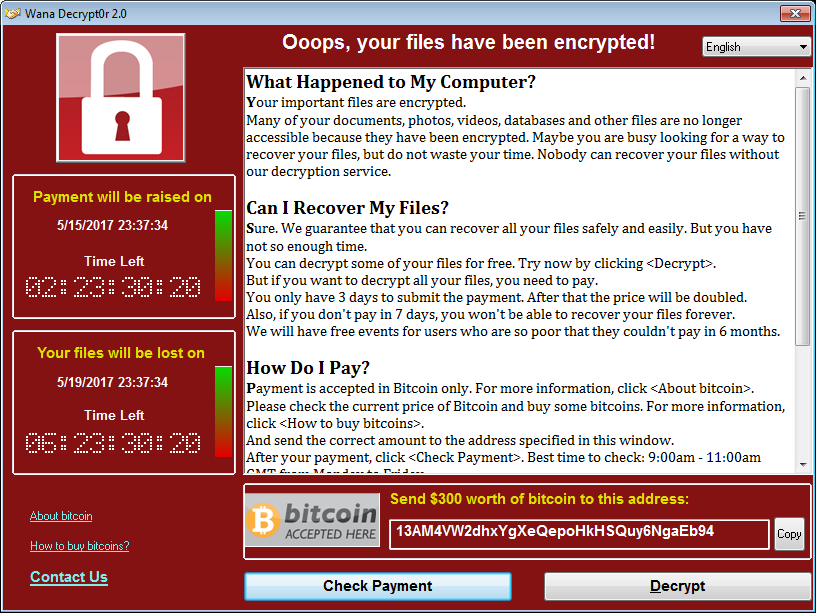
What makes WannaCry particularly dangerous is that it also has a worm component, which scans and attempts to infect machines with an open port 445 on both the Local Area Network (LAN) and on the internet itself. It scans all enumerated addresses within the network and look specifically for machines with an open 445 port. For the internet portion, it will again scan for random IP addresses to check for an open port 445. When it finds an IP address with an open port, it will begin scanning all devices in the same /24 IP range as additional targets. This worm routine allowed the ransomware to spread quickly within a short period of time.
While Microsoft had already patched MS17-010 in an earlier security update, WannaCry cleverly affects older Windows-based systems—notably those that are no longer included in Microsoft’s supported operating systems. Unpatched systems are also vulnerable to being infected by WannaCry.
While WannaCry’s impact was certainly devastating, it was lessened somewhat by a built-in “killswitch” that activated whenever a certain URL was detected to be “live”. Once activated, WannaCry will no longer perform its routines on the affected system.
UIWIX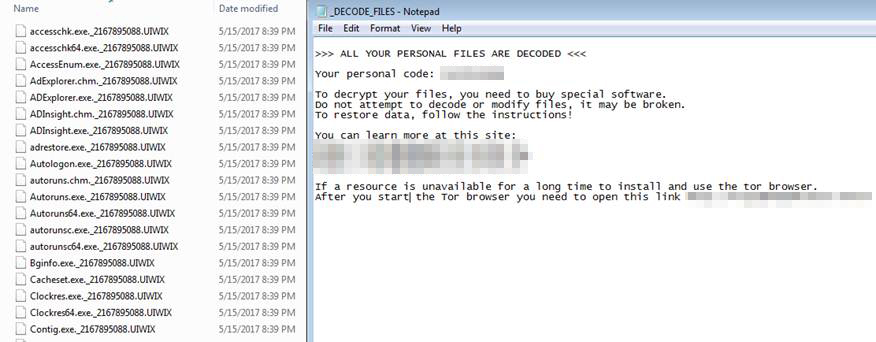
In the wake of WannaCry, other ransomware variants were detected trying to exploit EternalBlue. The most notable of these is the ransomware known as UIWIX (detected by Trend Micro as RANSOM_UIWIX.A).
Unlike WannaCry, UIWIX appears to be executed only in memory after exploiting the vulnerabilityn, a fileless feature that makes it stealthier than WannaCry. It’s also designed to be evasive, with a feature that allows it to detect the presence of a virtual machine or sandbox. UIWIX also uses a different method of connecting to its Command&Control (C&C) server; instead of scanning IP addresses for an open port 445, it uses the component mini-tor.dll to connect to an .onion site, which serves as the ransomware’s C&C server. The malware also seems to have information stealing capabilities, as its code strings indicate that it can gather personal credentials from the target system.
While UIWIX gained hype as a potentially more dangerous ransomware compared to WannaCry due to its lack of a killswitch, it also lacked the latter’s worm capabilities, severely limiting its potential to spread in a similar manner.
Jaff
Other than the ransomware that leveraged EternalBlue, Jaff ransomware (Detected by Trend Micro as Ransom_CRYPJAFF family) also emerged during the week.
Jaff arrives as a spam email with an attached malicious PDF document that contains an embedded Microsoft Word document. Once opened, the PDF file will then attempt to open the Word document, after which the user will be requested to provide permissions to edit the document. This behavior is similar to the Locky variant discovered earlier in May. The document then executes a macro that will download the actual ransomware payload, after which the victim’s system will be infected. During the encryption routine, the target files will be appended with a .jaff affix.
The payload also includes a text based ransom note, while the home screen will be modified to reflect the ransom note message: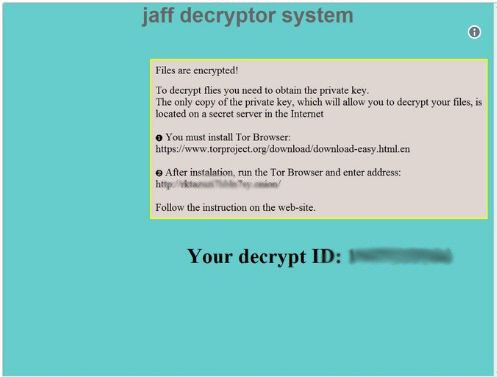
This week’s events show how truly dangerous and disruptive ransomware can be—especially given a wide enough scope and a large enough number of victims.
The uptick from this fiasco is that it also provided awareness to a large number of people who viewed ransomware as just another security incident without really understanding what it does or how damaging it could be. More than ever, people need to focus on security issues they can handle themselves, such as the very basic but often ignored act of updating their machines on a regular basis. Patching must also be done by both organizations and individuals as soon as they are able to avoid any potential problems.
Ransomware Solutions:
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevents ransomware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimizes the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers—whether physical, virtual, or in the cloud.
For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
For home users, Trend Micro Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
Users can likewise take advantage of our free tools such as the Trend Micro Lock Screen Ransomware Tool, which is designed to detect and remove screen-locker ransomware; as well as Trend Micro Crypto-Ransomware File Decryptor Tool, which can decrypt certain variants of crypto-ransomware without paying the ransom or the use of the decryption key.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One