Ransomware Recap: Expanding Distribution Methods
 In a relatively slow week for new ransomware variants, a new ransomware has popped up using the file hosting service Dropbox—specifically, a variant of the WannaCry/Wcry ransomware (Detected by Trend Micro as RANSOM_WCRY.C). This comes on the heels of a TorrentLocker variant that was using abused Dropbox accounts to spread its payload.
In a relatively slow week for new ransomware variants, a new ransomware has popped up using the file hosting service Dropbox—specifically, a variant of the WannaCry/Wcry ransomware (Detected by Trend Micro as RANSOM_WCRY.C). This comes on the heels of a TorrentLocker variant that was using abused Dropbox accounts to spread its payload.
Wcry initially spreads via an email, a malicious website, or dropped by another malware. Once the malware gains access to a user's system, it drops its prerequisite files and components, after which it prompts the user to download files from Dropbox URLs (Dropbox has already been notified of these links, which have since been removed). These files include the TOR Browser Bundle and the executable file "!WannaDecryptor!.exe". If the user clicks on the executable file, Wcry will display the ransom note shown below: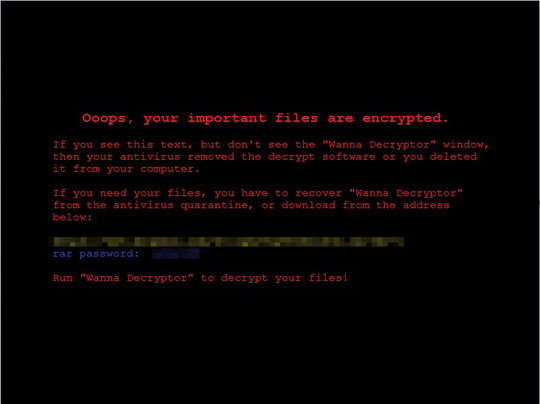
A graphical user interface (GUI) showing the ransom amount of $400 worth of bitcoin will also be displayed. The GUI also comes with a timer that threatens to permanently delete the affected files if the ransom isn't paid within the allotted time.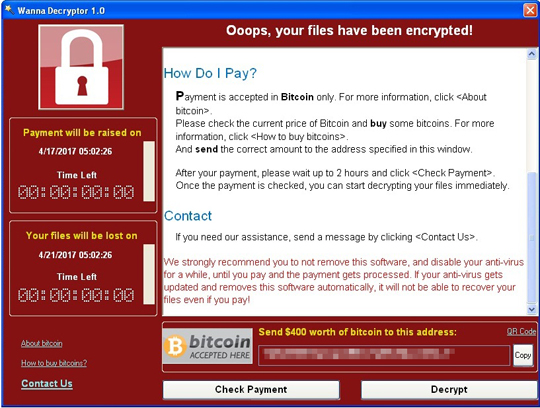
The ransomware will then proceed with its file encryption routine, appending encrypted files with the .CRY extension.
CryptoMix: Mole
A CryptoMix variant calling itself Mole (Detected by Trend Micro as CRYPAURA.MOLE) has been detected abusing Google Doc URLs to infect victims. The ransomware arrives via spam mails from a sender claiming to be affiliated with the US Postal Service. These emails contain a link that redirects users to a fake Microsoft Office Portal that instructs the user to click on a certain button to download a required plug-in. However, this link leads to the actual ransomware, which comes from Google Docs URLs that is specific to each individual sample. When threat actors upload a new sample, a new URL is generated for this sample.
The ransomware’s arrival scheme can be seen in the chart below: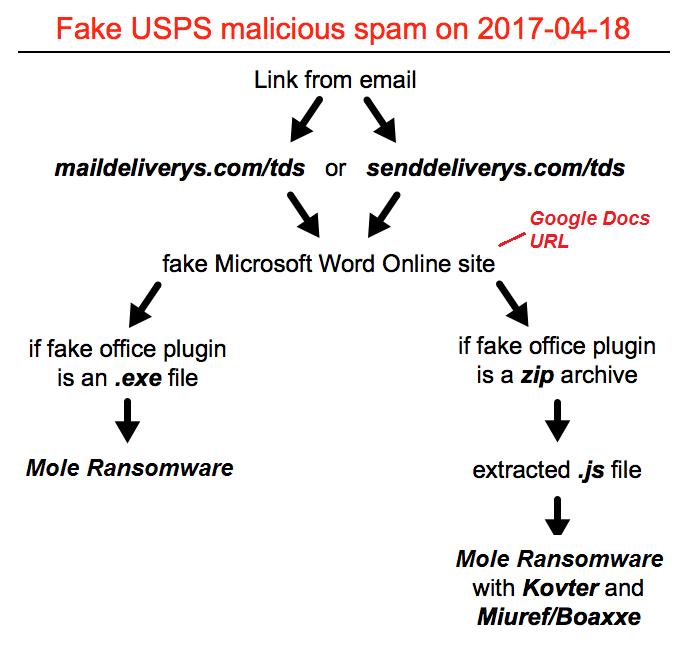
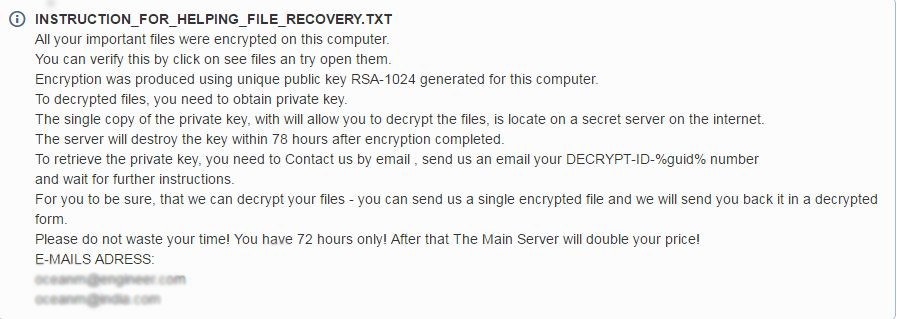
Once Mole encrypts its target files, it will display the ransom note, which does not ask for a specific amount but instead instructs the user to send an email requesting decryption instructions.
Hidden Tear: WinSec
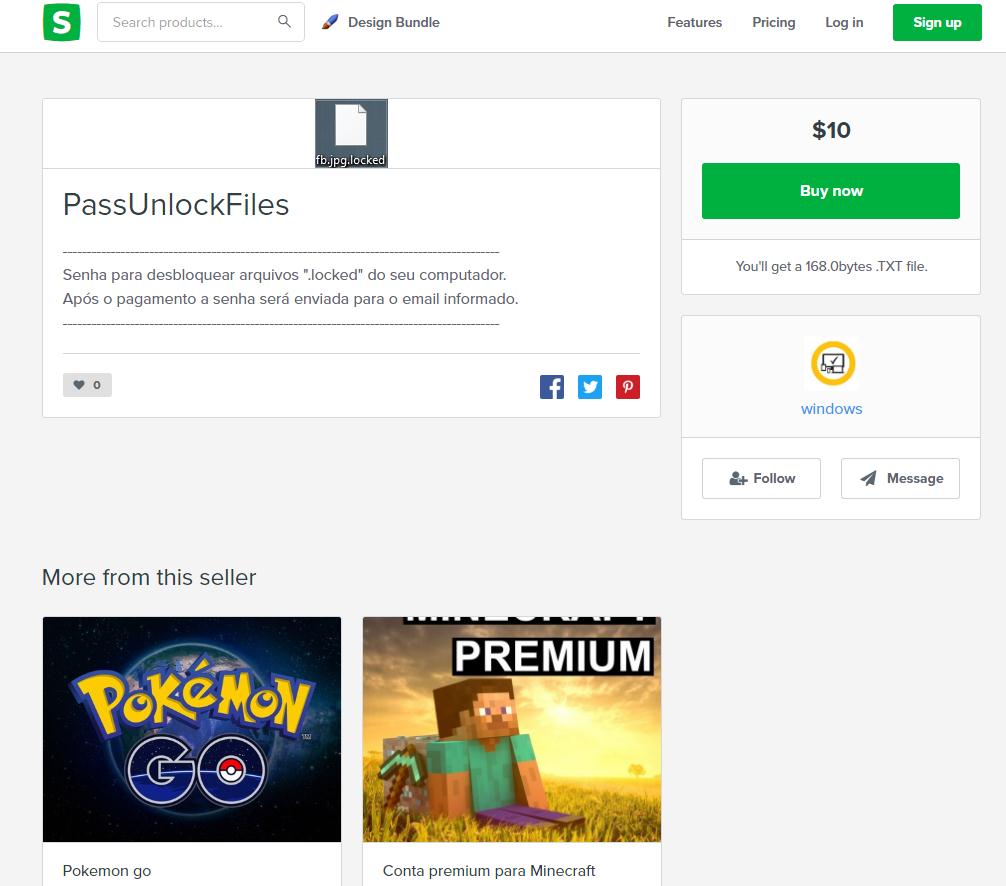
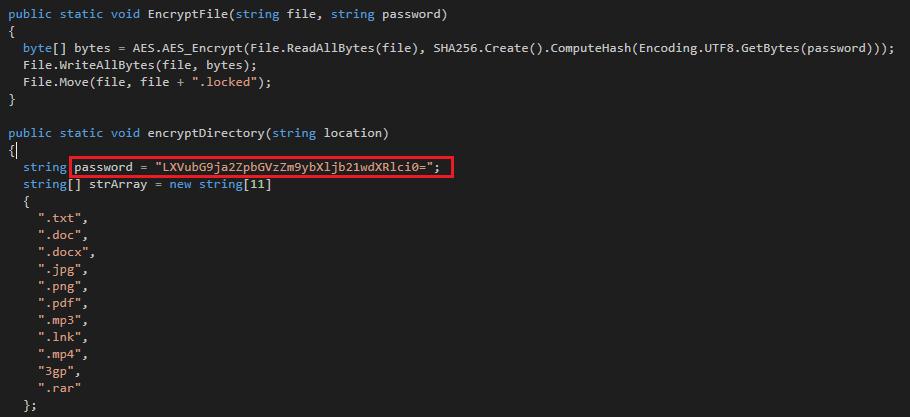
The Hidden Tear variant WinSec (Detected by Trend Micro as RANSOM_HiddenTearDESBLOQ.A and RANSOM_HIddenTearDESBLOQ.B) is a ransomware of Brazilian origin written in .NET that uses online selling platforms such as e-commerce websites for digital products.
The first variant, RANSOM_HiddenTearDESBLOQ.A, drops and executes Desbloquear.exe, which causes the following UI to be displayed: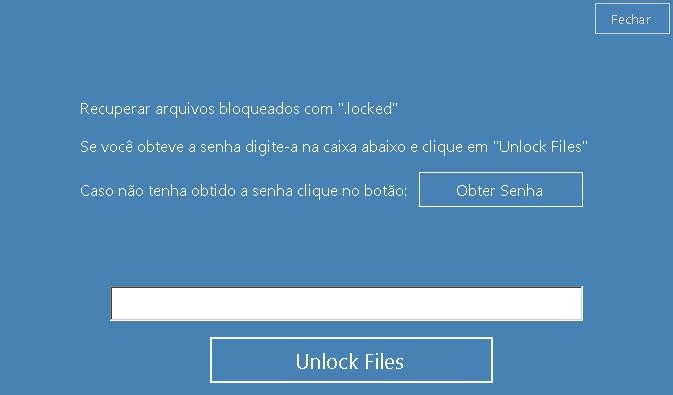
Roughly translated, the ransom note reads as follows:
Recover files locked with ".locked" If you have the password enter it in the box below and click on "Unlock Files" If you did not get the password click the button: [Get Password] (Button)
If a user clicks the "Obter Senha" (Get Password) button, a separate browser window opens the website “Sellfy”, which is an online platform for selling digital products. The ransom amount is a relatively affordable $10, which can be paid via PayPal. A random encrypt key will then be generated.
While the week was relatively light in terms of incidents, we still see ransomware variants popping up using different methods of propagation to infect victims. This kind of evolution in distribution makes ransomware more unpredictable in terms of how they infect their victims. As such, both users and organizations need to be extremely cautious about the files they download and the websites they visit, as cybercriminals might be exploiting them for malicious purposes.
Ransomware Solutions
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevents ransomware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimizes the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers–whether physical, virtual or in the cloud.
For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
For home users, Trend Micro Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
Users can likewise take advantage of our free tools such as the Trend Micro Lock Screen Ransomware Tool, which is designed to detect and remove screen-locker ransomware; as well as Trend Micro Crypto-Ransomware File Decryptor Tool, which can decrypt certain variants of crypto-ransomware without paying the ransom or the use of the decryption key.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One