 View: Understanding Targeted Attacks: What has Changed?
View: Understanding Targeted Attacks: What has Changed?
Targeted attacks are (or should be) an important concern to large organizations anywhere. Well-designed attacks proceed in six stages that show how attackers progress within their targets.
It has been several years since targeted attacks first emerged onto the threat landscape, and both the threats and our understanding of them have evolved and matured. What have we learned and what has changed since then?
Before we jump into the discussion about the different components of a targeted attack, it is also important to consider the factors that make a campaign successful. One of the reasons a company gets breached is because their frontline—the employees and their awareness—is weak. Meaning, the human barrier is critical as a first line of defense against targeted attacks.
The components are not particularly distinct.
The six components or "stages" of a targeted attack represent distinct steps in a logical, structured attack. Reality, however, is far messier. Once a stage is “finished”, it doesn't mean that no other activities related to that stage will take place. It may be possible for multiple stages of an attack to be going on at the same time: for example, C&C communication takes place throughout any targeted attack. The attacker needs to keep control of any activities going on within the targeted network, so naturally C&C traffic will continue to go back and forth between attacker and any compromised systems.
It's better to think of each component as different facets of the same attack. Different portions of a network may be facing different facets of an attack at the same time.
This can have a significant effect on how an organization has to respond to an attack. It cannot simply be assumed that because an attack was detected at an “earlier” stage that “later” stages of an attack are not in progress. A proper threat response plan should consider this and plan accordingly.
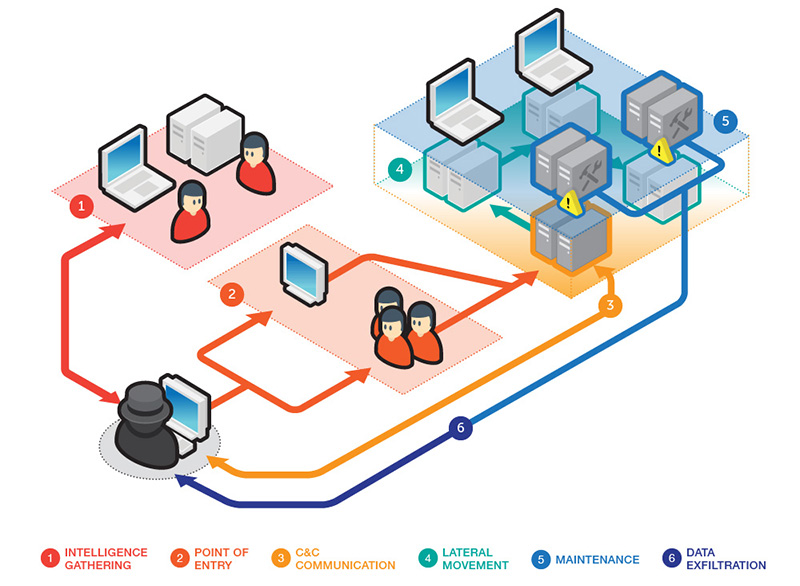 The six stages of a targeted attack
The six stages of a targeted attack
Intelligence gathering
The first stage of any targeted attack involves gathering information about the intended target. However, large amounts of information that can be useful in carrying out attacks lie exclusively within company networks. As such, this stage does not stop even if the attack is already well under way. Data acquired from within the network can help improve the efficacy of any ongoing attacks.
Beyond information, discovering the connections that exist between various teams, as well as those that extend outside of the target organization, can help an attacker determine good targets for more attacks.
Points of entry
Traditionally targeted attacks have used spear phishing emails to infiltrate the networks of targeted organizations. While this is still an effective tactic, attackers have added other methods to do this.
These alternatives include watering hole attacks (i.e., attacks that target websites frequently visited by the target industry or organization). However, beyond the initial point of entry, an attacker can add additional points of entry into the target network. Different employees and/or network segments may be targeted to ensure a more complete attack.
In addition, an attacker can constantly add backdoors to various systems during lateral movement that can serve as additional entry points into an already compromised organization. For an attacker, these could be incredibly valuable in case older points of entry are detected and removed.
Command and control communication
To effectively mount a targeted attack, an attacker needs to be able to effectively control any compromised machine within a targeted network. We’ve
previously discussed some of the methods used to hide backdoor C&C traffic, but another trend we’ve seen of late is how
internal machines are acting as intermediate C&C servers. The attacker would connect to this internal C&C server, which would then pass it on to other compromised machines within the organization.
Lateral movement
Lateral movement of a targeted attack is constantly repeated by the attacker. During this process, some activities take place that are classified with other stages (such as intelligence gathering) also take place. In addition, other systems may be backdoored to serve as additional compromised machines.
Lateral movement uses legitimate system administration tools to help hide its activities, and has three goals in mind: escalate the available privileges within the target network, perform reconnaissance within the target network, and the lateral movement to other machines within the network itself.
This facet is perhaps the most repeated of a targeted attack; in addition it is also the most comprehensive as this step can encompass other stages of a targeted attack as well. Internal reconnaissance and information gathering is performed, and any “intelligence” gathered can be used to identify potential targets for lateral movement, as well as any assets that can be found.
Maintenance
A successful targeted attack is one that can stay in progress for as long as the parties behind it require. Like anything else, the attacker needs to perform maintenance on an attack in progress to keep it operational. This can include using different backdoors and C&C servers, or the use of patches to ensure that other attackers can't exploit the same vulnerabilities used in the attack.
Data exfiltration
Data exfiltration is the ultimate goal of any targeted attack. However, compromised machines won't always contain valuable information, and some systems may not contain any information worth stealing.
The process of exfiltration can be “noisy” as viewed by network security solutions, as it could involve a high amount of network traffic that would not be found in the course of normal operations. One attempt by attackers to try and “hide” exfiltration traffic is to transfer much of the stolen data to machines within the organization before the data is extracted in a controlled manner. This has been known to happen in incidents involving PoS malware.
Targeted attacks are a significant problem for any organization today, and will continue to be so for the foreseeable future. It is important for those playing defense to understand that the threat landscape is constantly changing in order to create the appropriate defenses necessary.
For more details on targeted attacks, including how it works, the attacker's motivations, and its effects on its victims, download the primer Understanding Targeted Attacks: What has Changed?
HIDE
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 View: Understanding Targeted Attacks: What has Changed?
View: Understanding Targeted Attacks: What has Changed? The six stages of a targeted attack
The six stages of a targeted attack
 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One