Ransomware Recap: The Short-Lived Spread of Bad Rabbit Ransomware
Bad Rabbit was mostly spread using watering hole attacks that lead to a fake Flash installer install_flash_player.exe. Compromised sites were injected with a script that contains a URL that resolves to hxxp://1dnscontrol[.]com/flash_install. These compromised sites, which were based in Bulgaria, Estonia, Germany, Hungary, Japan, Slovakia, Ukraine, and Russia, were used to deliver the fake Flash installer to visitors from Japan, Turkey, and Russia, among others.
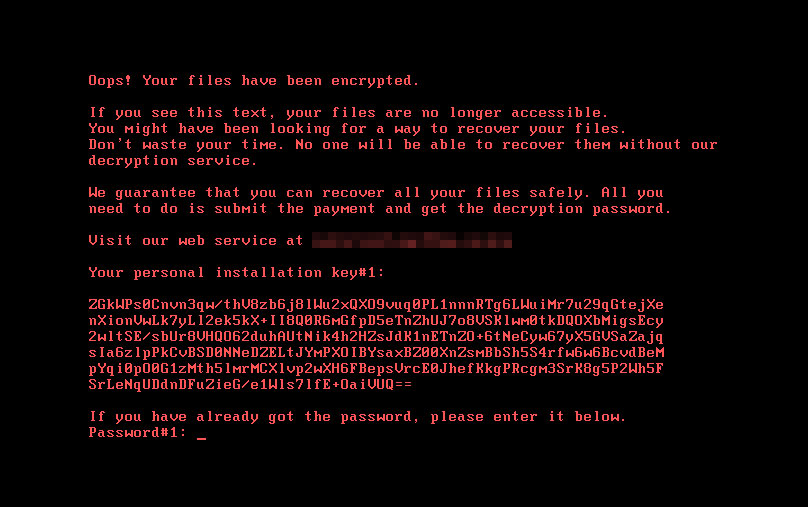
Bad Rabbit uses files referencing characters from the HBO show Game of Thrones, starting with rhaegal.job, which is responsible for executing the encryptor/decryptor file (detected as BKDR.Win32.TRX.XXPE002FF019) upon the reboot of the system, as well as drogon.job, that is also responsible for restarting the victim’s machine. A third file, viserion_23.job, reboots the target system a second time. The ransomware will encrypt files in the system upon execution. It will also encrypt the system’s MBR and display the ransom note shown below:
Further analysis revealed that Bad Rabbit uses SMB vulnerabilities patched in MS17-010 to spread across a network. Bad Rabbit attempts to brute force any administrative shares it finds and drops a copy of itself into these shares if successful. If the brute force attacks fail, it then resorts to using an exploit targeting the said vulnerabilities.
The variant was also discovered to be capable of spreading to other computers in the network by dropping copies of itself in the network using its original name and executing the dropped copies using Windows Management Instrumentation (WMI) and Service Control Manager Remote Protocol. When the Service Control Manager Remote Protocol is used, it uses dictionary attacks for the credentials.
Bad Rabbit’s C&C server has since been inaccessible after the news of its spread in Russia and Ukraine broke out.
Trend Micro XGen™ security products with machine learning enabled can proactively detect this ransomware as TROJ.Win32.TRX.XXPE002FF019 without the need for a pattern update.
Here are the other notable ransomware stories this week:
Matrix Ransomware
A security researcher discovered Matrix ransomware being spread via the RIG exploit kit on malvertisement-ridden websites. The RIG exploit kit targets vulnerabilities in Internet Explorer (CVE-2016-0189) and Flash (CVE-2015-8651). CVE-2016-0189 and CVE-2015-8651 are vulnerabilities that prey on visitors using unpatched and outdated versions of Internet Explorer and Flash Player.
Matrix encrypts files, scrambles their file names, and appends the .pyongyan001@yahoo.com extension name to the file's scrambled name when the variant infects the system.
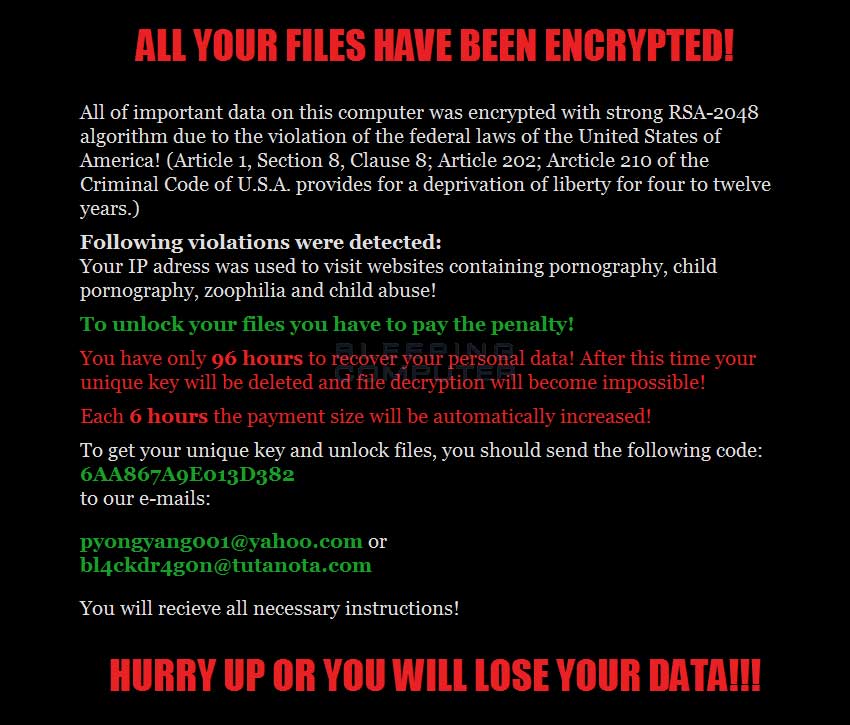
Matrix’s ransom note says it encrypts files using the RSA-2048 algorithm and scares victims by telling them they violated federal laws by visiting pornography, child pornography, zoophilia, and child abuse websites. The note also warns victims they have 96 hours to regain access to the encrypted files, and that the ransom payment will increase every six hours.
AllCry Ransomware
The AllCry ransomware (Ransom_AllCry) demands one bitcoin from victims in exchange for a decrypt key. Appending encrypted files with an .alllcry extension name, the variant arrives in the system as a Win32 EXE file for the Windows GUI subsystem. It encrypts a variety of file types that include Microsoft Office documents, as well as audio and video file formats.
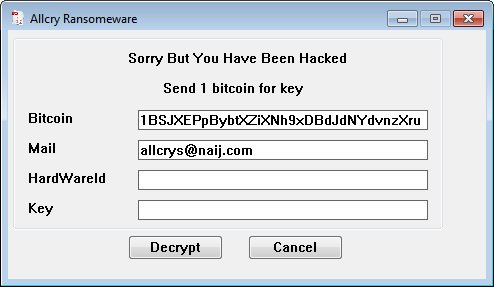 Figure 3. AllCry ransom note (via bleepingcomputer.com)
Figure 3. AllCry ransom note (via bleepingcomputer.com)This ransomware variant can be distributed via hacking through an unprotected RDP configuration, spam email and malicious attachments, fraudulent downloads, exploits, web injections, fake updates, repackaged and infected installers.
Users and enterprises can adopt these best practices to lower or eliminate the risk of ransomware infection.
Trend Micro Ransomware Solutions
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevent ransomware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimize the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers–whether physical, virtual or in the cloud. Trend Micro XGen™ security provides a cross-generational blend of threat defense techniques against a full range of threats for data centers, cloud environments, networks, and endpoints. Smart, optimized, and connected, XGen™ powers Trend Micro’s suite of security solutions: Hybrid Cloud Security, User Protection, and Network Defense.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One