Cybercriminal Underground Works In Business Models
May 10, 2014
 Download the infographic: The Cybercriminal Underground: How Cybercriminals Are Getting Better At Stealing Your Money
Download the infographic: The Cybercriminal Underground: How Cybercriminals Are Getting Better At Stealing Your Money
That’s child’s play. Though these scenarios may be possible—if and only if the attackers actually have the skills, technology, and years of planning and reconnaissance to do so—they give a distorted picture of what the cybercriminal underground actually is in real life.
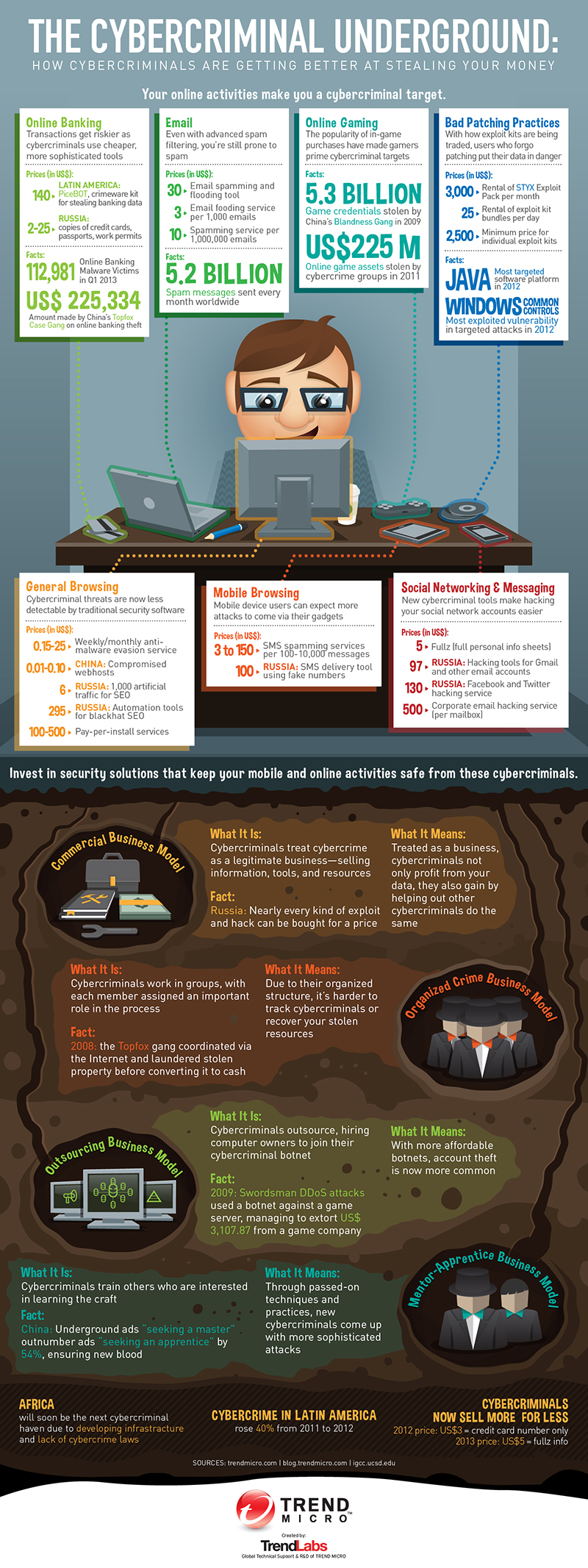
Think of the cybercriminal underground as a global marketplace full of anonymous buyers and sellers. It’s composed of several smaller markets unique to each region. Currently, the most prominent are those in Russia, China, and Latin America. These virtual black markets mostly thrive in forums or chat rooms where numerous cybercriminals act as anonymous businessmen who trade goods and services to make profit. And much like typical businessmen, these cybercriminals adhere to specific business models:
- Commercial model: It’s the most straightforward approach. Cybercriminals hawk goods like stolen user credentials, malware, exploits, and the like, and sell them to anyone who’s interested.
- Organized crime model: This set-up involves several individuals or groups who work together to achieve certain targets. Each person in the chain serves their own unique function integral to the whole team’s operations.
- Outsourcing model: This business model requires cybercriminals to partner with outside computer owners, whose network of machines they can rent as botnets for malicious schemes.
- Mentor-apprentice model: Those interested to advance their know-how in hacking or creating malicious applications can hire more skilled cybercriminals to pass on what they know.
Whatever model cybercriminals choose to follow, one thing’s for sure, if you’re using the Internet, you, including your personal information and money, are prone to their schemes. Whether you’re checking email, playing games, or connecting with friends on social media, cybercriminals are continuing to develop wares designed to piggyback on each of your activities. As long as cybercriminals have something to profit from, the cybercriminal underground is always open for business.
HIDE
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One