Ransomware: Behind the Scenes
There is no denying that the ransomware threat has surged dramatically into an epidemic that has plagued not just endpoint users but also public and private organizations. The malware type is made very effective because it exploits and cashes in on the fear of its would-be victims.
From the simple loss of access to files found in a user’s system to a smeared reputation due to empty threats, ransomware infections heavily rely on an array of scare tactics to coerce its victims to pay up. But much of what makes ransomware so effective is the fact that victims usually don't know they've been infected until they see the ransom note popping up on screen—and it's too late by then, as the malware has already done its damage.
[Related: What makes ransomware so effective?]
Much of the coverage on ransomware either focuses on how it arrives in a system and the damaging repercussions that comes after. But what happens in between? Here's what happens in the background, before victims see the ransom note.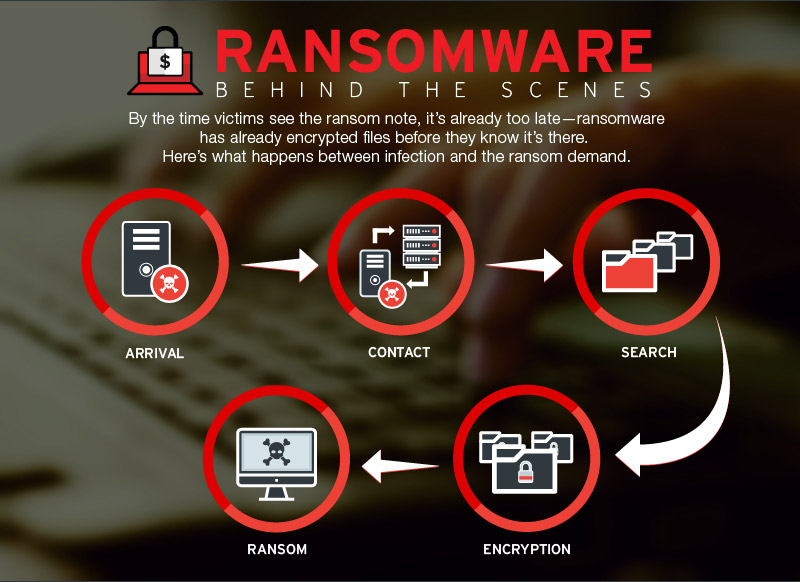
The moment an unknowing victim clicks on a harmful link or downloads an infected file opens the gates for the malware’s arrival onto a system. It drops a copy of itself, usually in the form of an executable file, into a user directory. In Windows, the malware usually drops the files either in the %appdata% or the %temp% folder. These folders are usually used because operating systems allow normal users to write to these directories without administrator privileges. The ransomware then starts to run stealthily in the background.
As soon as the malware has established itself onto the system, it connects to the network and begins to communicate to its server. At this stage, the ransomware sends and receives configurations to and from its command and control (C&C) server. In the case of the recently-discovered Pogotear ransomware (detected by Trend Micro as RANSOM_POGOTEAR.A) based on the Pokemon GO app, the malware connects to a particular website to send and receive information.
Search
It then goes through the infected system's directories, searching for specific file types to encrypt. The file types to be encrypted depend on the ransomware family—from identifying folders to target and exempt, down to the file types and extensions.
For ransomware families that delete mirror files and backups, this is also done during this stage, prior to the encryption process.
Encryption
Before it starts encrypting files, the cryptographic keys that the ransomware uses for encryption are generated.
Encrypting the files of the infected system varies on the type of encryption method a particular ransomware family uses—either AES, RSA, or the combination of the two, among others. The length of time it takes to encrypt files may differ depending on the number of files, the affected system's processing power, and encryption method used.
Several ransomware variants are capable of creating auto-start entries that continue the encryption routine in cases the when encryption process is halted by a system shutdown.
Ransom
The display of the ransom note will signify the success of the file-encrypting process of most ransomware variants. This could either happen instantaneously after the encryption process is complete, or after a system reboot, for ransomware types that modify the boot sector. Interestingly, some ransomware types do not even show a ransom note at all—at least not automatically. Some would drop its ransom notes into the affected folders, or resort display an HTML page with its ransom demand and payment instructions. Lockscreen ransomware would render the machines inaccessible, displaying a ransom note that can't be closed.
The Signs:
In an incident at the Colorado allergy clinic reported in July, employees reported difficulty accessing computer files and documents. This led the organization’s IT department to shut down servers in fear of a virus attack on its network. Later on, evidence of an interrupted ransomware infection—including a ransom note draft left in the system—were uncovered by the health clinic’s IT team and the third party cybersecurity partner commissioned to analyze the incident. Unfortunately, not all cases of ransomware infections have been thwarted as easily.
Ransomware behavior varies per family or variant, but there are telltale signs that could alert a vigilant user or an IT admin to a ransomware infection. For instance, during the encryption process, a would-be victim could experience system slowdown due to the extra processes running in the background. A hard drive light that's constantly flickering—without any legitimate process running—means that the hard drive is being accessed. Unfortunately, this could mean that the search and encryption process has begun.
Defending against ransomware
The entire process could be done within minutes after a victim clicks on a bad link or downloads an email attachment. This short window of time could spell trouble for a user or a business, but it could also provide ample opportunities for IT administrators to establish control of the situation.
True, ransomware is a serious threat that can cause a lot of damage, but it is not unstoppable, and is certainly preventable. Vigilance, when embodied by users and employees of an organization, greatly helps reduce the risk of downloading ransomware.
There is no all-encompassing antidote when it comes to preventing ransomware. A multi-layered approach that prevents it from reaching networks and systems is the best way to minimize the risk of reaching endpoints.
A majority of ransomware arrives via email. Subscribing to an up-to-date email and web gateway solutions greatly minimizes the risks by preventing malware from entering the network.
Maintaining a regular backup schedule of critical data can also turn cyber-extortionists powerless, as victims won't have to resort to paying the ransom to regain access to locked data.
The key is in arming users with knowledge on infection techniques commonly used by cybercriminals. In organizations, IT admins should be proactive in educating the workforce on possible ransomware entry points and in enacting policies that would prevent the access of potentially harmful sites that could compromise the company’s network.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One