Why Ransomware Works: The Psychology and Methods Used to Distribute, Infect, and Extort
 In May 2016, researchers uncovered a dark web site called The Hall of Ransom. Accessible through the Tor network, the underground site boasts a line-up of ransomware-related goods and services sold for hefty prices.
In May 2016, researchers uncovered a dark web site called The Hall of Ransom. Accessible through the Tor network, the underground site boasts a line-up of ransomware-related goods and services sold for hefty prices.
For US$3,000, the site offered the notorious Locky—a variant estimated to have recorded 90,000 machine infections per day in February. Apart from the sale of ransomware variants, The Hall also advertised the availability of a ransomware solution that is described as a USB key reportedly sold for 1,200 USD—a unique, uncopiable "antidote" that promises to unlock files encrypted by Locky on infected Linux and Windows-run machines. The site also introduces what is called a “new generation ransomware” called Goliath for US$2,100. Goliath has been found to have a source code derived from Locky, offered for “newbies” who are looking to enter the cybercrime business.
Locky adds to the growing list of ransomware variants that have become viable products in underground marketplaces. In the past, other families like Petya, Mischa, Cerber, and ORX-Locker have been offered as ransom-as-a-service (RaaS) products. In this distribution model, malware developers pass on the ransomware to affiliates that distribute the malware, and the developers get paid in commissions for every paid ransom. The fact that ransomware has grown into a lucrative business model only means one thing: it works.
While the discovery of the site dedicated to ransomware led researchers and analysts to believe that it was a scam designed to trick the scammers—the site's unreasonable claims and bold statements were a giveaway—unearthing this specific platform in the underground both confirms the level of cybercriminal interest in ransomware and explains its ongoing surge.
[Infographic: The Evolution of Ransomware]
The Psychology Behind Ransomware
Broken down into stages, the ransomware operation is simple: find a way to infiltrate a victim's machine, lock the system or the critical files found in it, and coerce the victim to pay the ransom. Through the years, ransomware has tremendously developed into a very effective cyber threat that no longer just “scares” its would-be victims with a locked screen, but a notorious malware that knows the weak points of its targets. Likea con artist that carefully studies its target, ransomware has consistently banked on exploiting its victim’s fears to make for an effective extortion scheme.
By the end of 2015, the Trend Micro Security Predictions for the year ahead bravely called 2016 the year of online extortion, saying, “In 2016, online threats will evolve to rely more on mastering the psychology behind each scheme than mastering the technical aspects of the operation. Attackers will continue to use fear as a major component of the scheme, as it has proven to be effective in the past.”
[Read: Trend Micro 2016 Security Predictions]
When it was first sighted and categorized as scareware that locks users’ machines, the earlier ransomware variants took advantage of its victim’s fear of losing access to the infected machine, prodding them to pay the ransom instead of having to find an alternative solution. Police Trojans (such as Reveton) incited fear among its targets by feigning legitimate federal law violation warnings to trick users into clicking on a poisoned link. This paved the way for the more evolved, sophisticated data-kidnapping malware, crypto-ransomware, which went for the victim's data.
With ransomware constantly progressing and evolving when it comes to its features, distribution tactics, and ransom demands, fear has remained the biggest factor for its success. The understanding of the victim’s psyche has largely contributed to the spread and effectivity of ransomware.
Cybercriminals who use ransomware are doubling up on their efforts to effectively expand their reach. Social engineering lures continue to work to the advantage of the data kidnappers, but now on a grander scope. In May 2016, Perezhilton.com was once again challenged by a cybersecurity issue after the site went from hosting Hollywood gossip to carrying infected ads that led its hundreds of thousands of its readership-base to a gateway that served CryptXXX ransomware. In his report, security researcher Nick Bilogorskiy noted, “After browser exploitation, Angler typically drops Bedep malware which will further download and infect the victim’s machine with CryptXXX ransomware.” The distribution method used in this case was more traditional, as it relied on an exploit kit that went after vulnerabilities. But its use of a compromised popular site had the potential to affect thousands of unknowing users.
In the same month, millions of Amazon users were put at risk by way of a phishing campaign that potentially led to the download of Locky ransomware. The bait came in the form of bogus emails masquerading as legitimate messages from the eCommerce giant, sent by an amazon.com email address with a subject line that read, “Your Amazon.com Order Has Dispatched (#code)” that could easily trick any unknowing user into downloading an attachment containing a malware-laced file.
When May drew to a close, this same customer trust has been used to data kidnappers’ advantage when a new Torrentlocker campaign used the name of a known Nordic telco giant, Telia, to spread the malware. Similar to the tactic used on Amazon users, cybercriminals crafted a social engineering lure that tricked users with a make-believe invoice from the telecommunications company. Once clicked, the poisoned link redirects potential victims to a fake webpage with a displayed Captcha code. An entered code triggers the download of the ransomware.
Forcing Payments
Creating clever tactics to penetrate a victim’s system isn’t the only thing that has led to the success of ransomware of late. For a cybercriminal, a ransomware infection can only be considered successful if the victim pays. To that end, ransomware developers have developed a variety of ways to convince users that paying the ransom is the best option.
In April, a new ransomware strain emerged called Jigsaw, named after the horror movie franchise, Saw. Interestingly, the extortion method was greatly inspired by the actual movie, involving a timer showed how much time the victim had left to pay the ransom—initially pegged at US$150—to regain access to the encrypted files. To further heighten the sense of urgency, each hour of failure to pay the ransom leads to the deletion of a portion of the victim’s files—much like a scene lifted from the movie. As such, after 72 hours of non-payment, the entire batch of encrypted files are deleted.
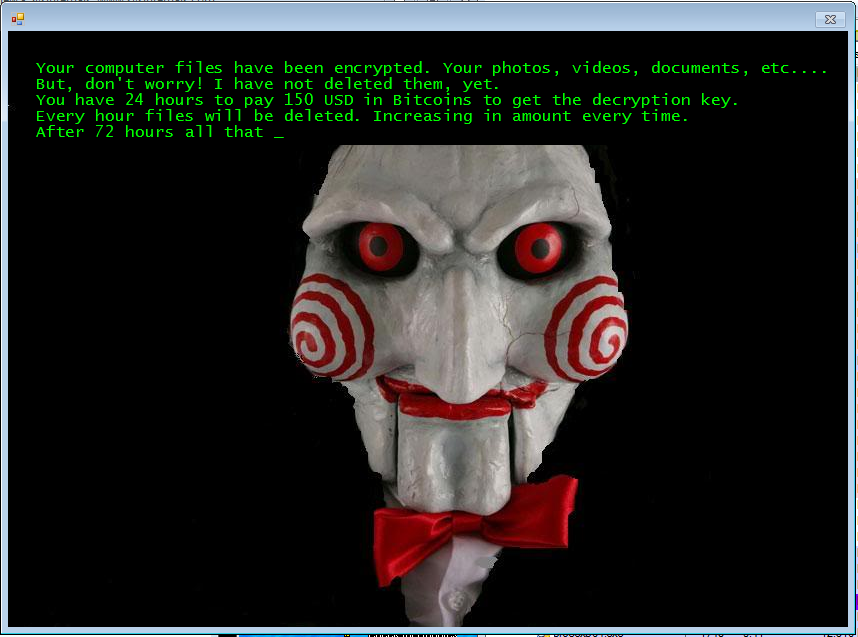
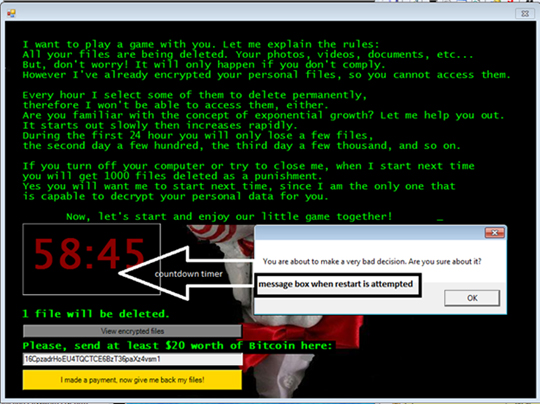
Apart from this, Jigsaw has shown the direction cyber-extortionists are taking these days—a clear, blatant attack on the victim’s psyche. One particular sample unearthed by researchers used a locked ransom note that says, “YOU ARE A PORN ADDICT.” This method shows how shame can also be used to coerce users into paying the ransom.
Casting a Wider Net
In the past few months, various cases of ransomware infections have shown how the malware has gone after bigger fish, from individual users to entire networks of organizations. A number of recent high-profile attacks demonstrated how it can be used to disrupt operations of critical systems across various sectors and industries.
When news of a declared “internal state of emergency” brought down the systems of the Hollywood Presbyterian Medical Center (HPMC), ransomware jumped from being an individual problem into one that could endanger not just an organization, but human lives as well. Network and computer systems of HPMC, including those that involved CT scans, lab work, pharmaceuticals, and documentation remained offline for over a week, causing the hospital staff to revert to pen-and-paper. This incident has also impacted emergency room systems, forcing HPMC to transfer patients to other hospitals.
As reported, the ransom was paid in full in hopes of regaining access to essential operations of the medical center. However, in a statement, Steve Giles, HPMC CIO, said that adhering to the demands of the cybercriminals did not simplify things for them. He said, “We received the decryption codes—900 decryption codes. One decryption code, unique, per device. There was no magic wand of a single decryption code to alleviate the problem. We had to deal with 900 codes to go server by server by server, device by device.”
It did not stop with the HPMC though. The list of institutions with disrupted operations exponentially grew, eventually affecting utility providers, healthcare providers, police departments, and even academic institutions. A recent attack on an educational institution showed how victims are left with no better choice but to pay the ransom. After getting hit by a ransomware attack that affected critical data, the University of Calgary paid a ransom that approximately costs CA$20,000 in bitcoins to regain access to encrypted research data. In a statement, University Vice President of Finance and Services Linda Dalgetty said, “We are a research institution, we are conducting world class research daily, and we don’t know what we don’t know in terms of who’s been impacted and the last thing we want to do is lose someone’s life’s work.” This growing line of high-profile ransomware victims shows that cybercriminals are aware of how they can make its victims—even large institutions—cave in to its demands. Disrupt a victim in a certain way and they're more likely to pay up.
The War Ensues
Looking at today’s ransomware landscape shows that the threat is not going away anytime soon. In a recent attempt to fight the digital extortion method, California State lawyer Bob Hertzberg spearheaded legislation that calls for specific penalties for anyone involved with the spread of ransomware. This involves prison time of up to four years and a fine that totals to US$10,000.
Hertzberg, in his statement, quoted FBI statistics to prove why legislation is needed. The FBI report showed that ransomware has already amassed damages amounting to US$209 million within the first three months of 2016 in the United States alone—a huge leap from the recorded 25 million extorted from victims in all of 2015.
As such, ransomware continues to be a notable security nightmare for end users and organizations not only because of the surge of infections but with the surfacing of newer, more evolved families and ensuing variants almost on a daily basis. This illustrates, in great lengths, an ongoing pattern of development, anchored on the fact that the attack method has been proven to be widely successful.
In fact, ransomware development and infections have been so rampant that it has turned into a common occurrence. To date, 50 new ransomware families have already been seen within the first five months of 2016 alone, a big leap from the figures seen in 2014 and 2015 combined. The most alarming fact is that the threat is still continuously growing—in number and level of effectivity.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One