Operation Pawn Storm: Fast Facts and the Latest Developments
 View Operation Pawn Storm Targets and Activities
View Operation Pawn Storm Targets and Activities
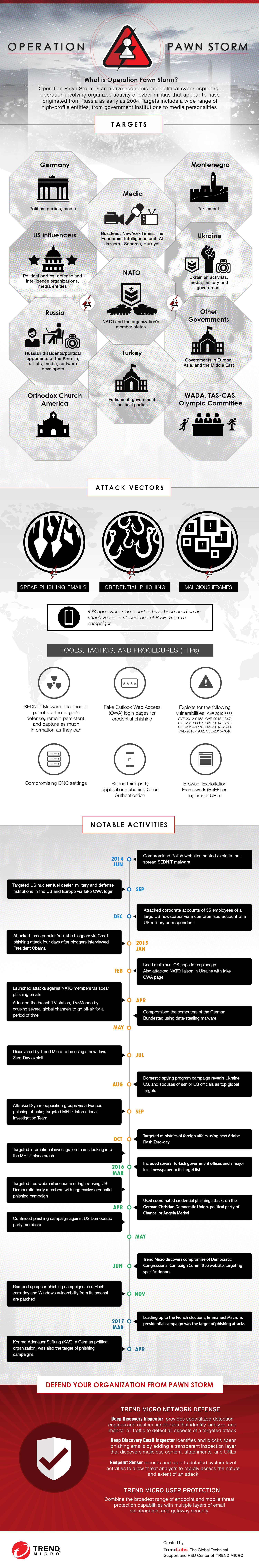
Operation Pawn Storm is an ongoing cyber espionage campaign that’s as far-reaching as it is ambitious. It has been known to primarily target military, embassy, and defense contractor personnel from the United States and its allies, including government institutions such as the North Atlantic Treaty Organization (NATO). Opposing factions, dissidents of the Russian government, international media, and high-profile political personalities in Ukraine are targeted as well.
We published our findings about Operation Pawn Storm in October 2014, in a research paper titled “Operation Pawn Storm: Using Decoys to Evade Detection” and we’ve been tracking its movements and developments since then.
What is Operation Pawn Storm?
Operation Pawn Storm is an active economic and political cyber-espionage operation that targets a wide range of high-profile entities, from government institutions to media personalities. Its activities were first seen as far back as 2004, but recent developments have revealed more concrete details about the operation itself, including its origins and targets.
What makes it different from other cyber espionage groups/operations?
Operation Pawn Storm is distinct from other politically-inclined threat actor groups because of its attack methods, which include the following:
- Utilizing spear-phishing email leading to SEDNIT/Sofacy. The spear phishing email itself may contain geopolitical material/subjects to bait the recipient into opening it. SEDNIT is a malware known for its backdoor and infostealing routines.
- Creating fake Outlook Web Access (OWA) login pages for credential phishing mail payloads. A variant of their spear phishing emails redirected users to a fake Outlook Web Access login page instead, in the hopes of stealing their login credentials. One of the many targets of this particular method include US defense contractor ACADEMI, formerly known Blackwater.
- Exploits for the following vulnerabilities: CVEs: CVE-2010-3333, CVE-2012-0158, CVE-2013-1347, CVE-2013-3897, CVE-2014-1761, CVE-2014-1776, CVE-2015-2590, CVE-2015-4902, CVE-2015-7645
- Creating (and using) iOS malware for espionage. The malicious app, detected by Trend Micro as either IOS_XAGENT.A or IOS_XAGENT.B, steals all sorts of information from the mobile device it infects, such as messages, contact lists, geo-location data, pictures and even voice recordings.
Operation Pawn Storm is known to have targeted the following:
- NATO and the organization's member states
- Government, Military and Media entities in the US
- Government, Military and Media entities of US allies
- Russian dissidents/political opponents of the Kremlin
- Russian citizens across different civilian industries and sectors
- Ukrainian Activists
- Ukrainian Media
- Ukrainian Military and Government
- Governments in Europe, Asia and the Middle East
Some of Operation Pawn Storm’s most notable activities include:
- June 2014 – compromised Polish government websites
- September 2014 – targeted a large US nuclear fuel dealer by setting up fake Outlook Web Access login pages for its employees. Also launched fake OWA login page attacks against military and defense institutions in the US and Europe
- December 2014 – attacked the corporate accounts of 55 employees of a large US newspaper, using the compromised account of a US military correspondent they’d attacked earlier in the same month
- January 2015 – targeted three popular YouTube bloggers with a Gmail phishing attack. The attack happened four days after the bloggers interviewed US President Barack Obama at the White House
- February 2015 – discovered to be using malicious iOS apps for espionage. Also attacked NATO liaison in Ukraine with fake OWA page
- April 2015 – launched attacks against NATO members. Also attacked the French TV station TV5Monde by causing several global channels to go off-air
- July 2015 – discovered by Trend Micro to be using a new Java zero-day exploit
- July 2015 – redirected one of their C&C servers to a Trend Micro IP
- August 2015 –domestic spying campaign revealed, targeted Russian dissidents, media, artists, military, including the spouses of senior US officials
- September 2015 – set up fake server that mimicked the SFTP (Secure File Transfer Protocol) server of the Dutch Safety Board and created a fake Outlook Web Access (OWA) server to target a Dutch Safety Board partner in the MH17 investigation
- October 2015 – discovered by Trend Micro to be using Adobe Flash zero-day exploit code and targeted several ministries of foreign affairs via spear phishing emails
Zero-day exploits are used in targeted attacks because they are effective, given that software vendors have not created patches for them. In July 2015, we detected suspicious URLs that hosted a newly discovered zero-day exploit in Java, identified as CVE-2015-2590. According to our research, email messages targeting a certain armed forces of a NATO country and a US defense organization contained these malicious URLs where the Java exploit is hosted. Once successfully exploited, it executes arbitrary code on the default Java settings, compromising the security of the system.
In October 13, the attackers behind Pawn Storm have been using Adobe Flash zero-day exploit identified as CVE-2015-7645 for their campaign. Based on our analysis, the Flash zero-day affects at least Adobe Flash Players versions 19.0.0.185 and 19.0.0.207. In this campaign, Pawn Storm targeted several ministries of foreign affairs around the globe, except in Russia. The targets received spear phishing emails that contained links leading to the exploit. The emails and URLs were crafted to appear like they lead to information about current topics.
Operation Pawn Storm is an ongoing campaign. Get a quick look at the notable developments and how your organization can protect against Pawn Storm in the attached infographic.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One