- Overview
- Credential Phishing
- BEC
- Malware
- Phishing
- Cloud App Security
The Covid-19 pandemic has caused massive disruptions in how individuals and enterprises operate on a day-to-day basis. At a time when remote work has become essential, the cloud has also become a reliable platform in keeping business operations functioning despite lockdowns and travel restrictions. Indeed, reliance on cloud computing has skyrocketed in 2020 — and the dependency on this technology is bound to continue. In fact, a recent Forrester report predicts that the use of cloud-native technology will increase, stating that in 2021 alone, the global public cloud infrastructure will grow 35%.
Because the cloud has successfully positioned itself at the center of digital transformation, malicious actors are quick to take note and target it with threats. Though cybercriminals are starting to use complex attack methods, they are still employing tried-and-tested ways to wreak havoc on the simplest, most reliable, and most straightforward of vectors that use cloud-based technologies — email — with phishing, malspam, and social engineering attacks.
In this report, we discuss the notable email threats of 2020, including business email compromise (BEC) and credential phishing, that we found using the Trend Micro™ Cloud App Security solution.
The email threat landscape of 2020: an overview
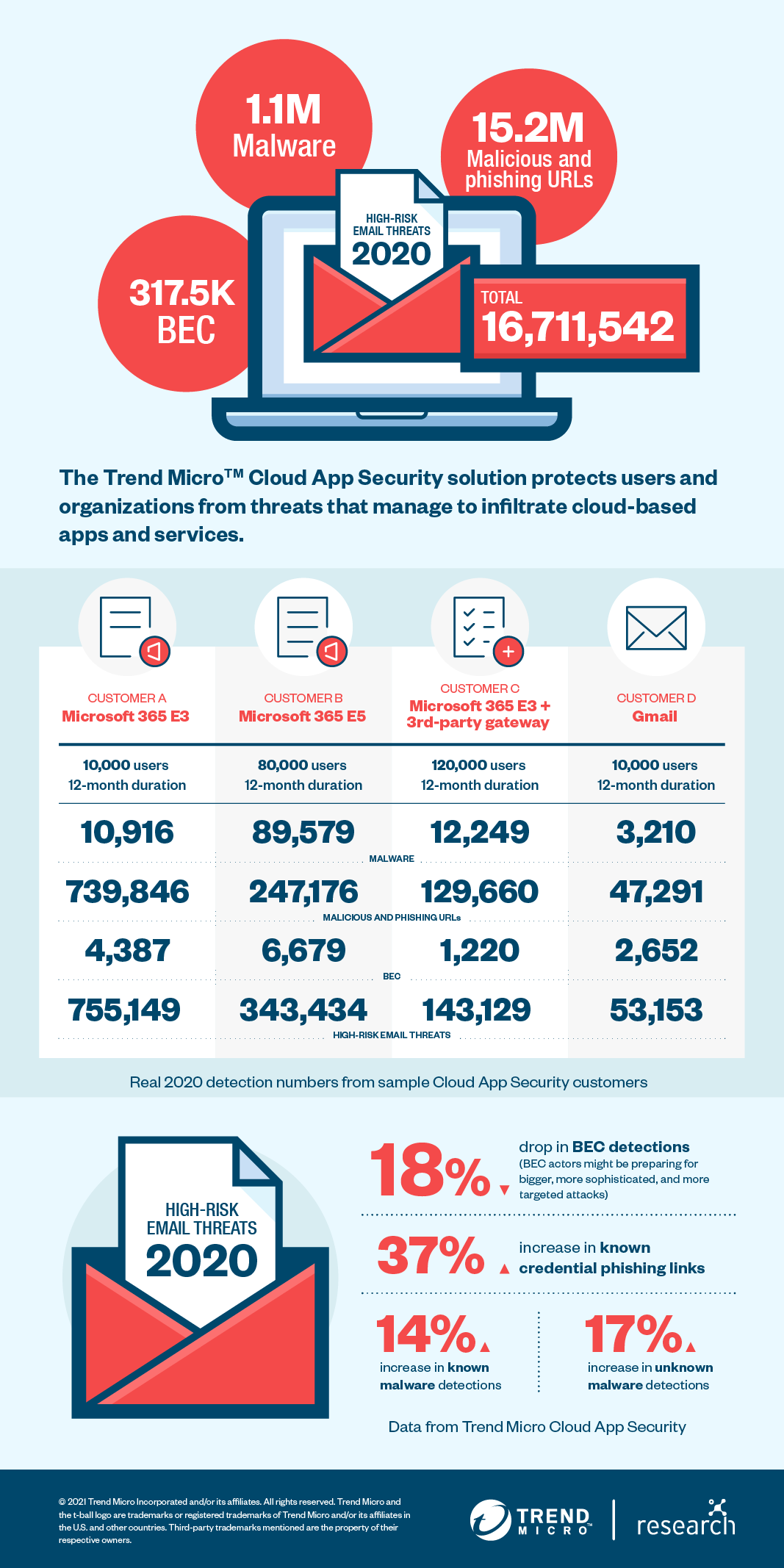
In 2020, over 16.7 million high-risk email threats were detected and blocked by Trend Micro Cloud App Security, an API-based solution that provides a second layer of protection for Microsoft Exchange Online and Gmail. It also protects various cloud-based applications and services, including OneDrive for Business, SharePoint Online, Teams, Google Drive, Box, Dropbox, and Salesforce. This is a 32% increase from the previous year.
Our data also shows that malware, phishing, and credential phishing attacks leaped in 2020, while BEC saw a slight drop in numbers.
When remote work became the norm, more people went online to make use of email and cloud-based services. Last year, internet usage skyrocketed by 50 to 70% and 40 million people in Southeast Asia went online for the first time. With millions of people working from home around the globe, the use of emails to communicate with peers and clients has become more imperative. A report shows that more people sent and opened emails during the pandemic and that a whopping 306.4 billion emails were sent and received per day in 2020.
Unfortunately, a large chunk of these emails is malicious. Malicious actors have been quick to take advantage of the uncertainty and fear that were brought about by the global pandemic, sending out Covid-19-related email threats to steal money, personally identifiable information (PII), and credentials. The FBI has also seen an uptick in pandemic-related scams and warned the public to be cautious of both fake Centers of Disease Control and Prevention (CDC) emails and phishing emails.
Despite cloud-based systems and services having built-in threat detection and security, detections from Trend Micro Cloud App Security show that millions of threats manage to evade these integrated security filters.
Trend Micro Cloud App Security detected over 755,000 high-risk email threats for one organization with approximately 10,000 Microsoft 365 users in 2020 — a staggering 75 high-risk emails per user — after scanning by the native Microsoft 365 security. Though most of the threats that were detected and blocked for this organization involved malicious URLs and phishing links sent via email, Trend Micro Cloud App Security also thwarted 10,000 malware files and over 4,300 BEC attempts for this organization.
This proves that users, enterprises, and organizations will benefit from a multilayered approach to security in order to keep different types of threats at bay.
Credential phishing attacks grow in number and level of sophistication
As remote work has become universal, credential phishing attacks have also become more rampant. For example, credential phishing, an attack where malicious actors steal email account credentials of employees through fake login pages, has grown in 2020.
Our Trend Micro Cloud App Security data shows that in 2020, 5,465,969 credential phishing attacks were detected and blocked — a 14% jump from the previous year. In contrast to last year’s credential phishing detections, the number of known credential phishing links outnumbers the unknown ones by 34%.
4,780,139
5,465,969
Unfortunately, a large number of threats still manage to infiltrate the built-in filters of cloud-based email services. One of these services is Microsoft 365, which has always been on the crosshairs of credential phishing actors. The Trend Micro Cloud App Security service effectively detected and blocked 314,302 credential phishing attacks from one organization with 10,000 Microsoft 365 users and 2,585 for another organization with 550 Microsoft 365 users in 2020. It’s important to note that for both organizations, the bulk of the phishing threats that were detected and blocked are credential phishing attacks.
USERS
USERS
Aside from the greater number of credential phishing attacks, we also saw how credential phishing actors made use of sophisticated techniques. The SideWinder group delivered a malicious LNK file on a malicious server that was also used to host credential phishing pages that targeted government and military units in Nepal and Afghanistan. Based on our investigation, the credential phishing pages had been copied from their victims’ webmail login pages and modified to make phishing attacks more effective.
Cybercriminals are also launching voice phishing or vishing campaigns, calling and duping employees via VoIP systems. The malicious actors trick the victims to log into fake phishing sites to harvest their usernames and passwords in order to look for administrator accounts within the network and cause substantial financial problems for the organization. The FBI released a warning to the public to be wary of such attacks, as the shift to remote work might have made organizations more vulnerable to vishing attacks.
In May 2020, we saw how attackers targeted C-suite company executives with emails containing fake Microsoft 365 password expiration reports to dupe victims into revealing their usernames and passwords. Our investigation shows that the credential phishing campaign’s high-ranking victims come from manufacturing, real estate, finance, government, and technological industries in Japan, the United States, UK, Canada, Australia, and Europe.
Dip in 2020 BEC numbers might be due to more targeted, sophisticated techniques
Although we saw a slight decline in BEC attempts in 2020, BEC continues to cost businesses millions in losses. In a report from non-profit, international consortium Anti-Phishing Working Group (APWG), it has been noted that despite a decline in the number of phishing sites, the losses associated with BEC continue to rise: From US$54,000 (the average cost of a fraudulent wire transfer in the first quarter of 2020), the amount has jumped to US$80,183 in the second quarter of the year.
The Trend Micro Cloud App Security blocked 317,574 BEC attacks in 2020, which is 18% lower than the previous year’s numbers.
The number of BEC attacks detected might be lower in 2020, but this does not mean that enterprises and organizations should let their guards down. After all, the lower number might just be because BEC operators are now working smarter and employing more targeted and sophisticated attacks.
In 2020, the Trend Micro Cloud App Security service effectively protected an organization with 80,000 Microsoft 365 E5 users from 6,679 BEC attempts (an average of 12 attacks per user). It also shielded an organization with 10,000 Microsoft 365 E3 users from 4,387 BEC attempts.
Last year, IBM X-Force discovered a BEC campaign that used a fake invoice containing an IMG or disk image file attachment. When a victim clicks on the IMG file, a NetWire remote access trojan (RAT) is downloaded on the victim’s machine. Another BEC scam cost Puerto Rico’s government a total of 4.2 million dollars in a span of two months. This attack was carried out through the hacked email account of a government finance worker.
The dip in numbers might also be because cybercriminals are preparing for bigger and more targeted attacks. Some researchers believe that malicious actors are actively gathering information from targeted companies and enterprises using Google Forms to survey for a possible BEC trap in the future. Several of the companies that the researchers observed as possibly being targeted in potential BEC attacks belong in different sectors, including retail, telecommunications, healthcare, energy, and manufacturing.
Malware attacks grow in numbers, advance in complexity
There is a 16% growth in the number of malware files that were found and blocked in emails in 2020. At over 1.1 million malware detections, we saw that both known and unknown malware variants that were detected and blocked by Trend Micro Cloud App Security increased by 14% and 17% respectively.
Early in 2020, malware actors disguised the Emotet malware variant as coronavirus notifications in a spam campaign. As a lure to download the malware, malicious actors asked the victims to download an attachment that purportedly has a list of Covid-19 preventive measures. Fortunately, as of January 2021, a global alliance of law enforcement agencies has managed to take down Emotet’s operations and take over its command-and-control (C&C) infrastructure.
Threat actors behind malware variants that are sent via spam emails are not only taking advantage of the global pandemic to fool their victims but are also continuously developing their techniques.
A good example is the banking trojan Trickbot, which we found to have updated its arsenal to include detection evasion, screen-locking, and remote application credential-grabbing. Another Trickbot campaign spreads a fileless backdoor called the “BazarBackdoor” via spam emails and social engineering techniques.
Interestingly, despite the fact that the total number of malware found and blocked in 2020 is higher than that of the previous year, the number of ransomware files blocked for 2020 is still significantly lower compared with that in 2019. The Trend Micro Cloud App Security service detected and blocked 178,893 ransomware threats in 2020.
This paradoxical trend is something that we started seeing in 2017. While there is a lower number of major ransomware families that are at large upon successful infection, these players yield a large payoff. As opposed to sending ransomware via spam to as many potential victims as possible, modern ransomware actors are now more careful and intentional with regard to targeting victims, ensuring that they infect enterprises or organizations who will pay large sums of money for their data. They also use multi-stage attacks where phishing emails are used as entry vectors to spread ransomware across victim organizations.
This might explain the number of ransomware threats that Trend Micro Cloud App Security blocked in several organizations in 2020.
Phishing scams take advantage of Covid-19 and remote work setups
Trend Micro Cloud App Security intercepted 6,924,324 phishing scams in 2020, a 19% increase from the previous year. It should be noted that the number of phishing threats sent via spam has increased a considerable 41%.
With millions of people working from home because of Covid-19, attackers are taking advantage of the lack of security and visibility to lure people into falling for phishing attacks that are sent via email. On top of this, cybercriminals are also exploiting the pandemic and the increased reliance on online shopping to spread malicious campaigns on individuals and enterprises alike.
For example, with the goal of stealing credit card information, malicious actors sent phishing emails that led victims to phishing websites in an international post office phishing campaign that affected 26 countries.
In 2020, malicious actors also attempted to steal credit card information from a French retail company’s customers by employing a unique social engineering tactic: It included each victim’s home address and phone number in its phishing scheme. Based on our investigation, cybercriminals sent phishing emails that contained details of a fake online order that amounted to nearly a thousand euros (over US$1,200 as of writing), prodding the victim to select the “Cancel my order” button. When selected, this leads to a phishing page that attempts to replicate the Darty website.
Additionally, we also analyzed a phishing scam that used a fake Netflix page to steal PII and credit card information by asking victims to update their account information on a fake page. It is evident in this case that cybercriminals are taking advantage of people’s need for quarantine-related entertainment. In fact, in the first three months of 2020, 16 million users signed up for the online streaming service.
Protect your email and cloud-based collaboration tools during the pandemic and beyond with Trend Micro Cloud App Security
The global health crisis has not impeded cybercriminals from wreaking havoc using email-based threats. Rather, they have simply exploited it for ill gain. In 2020, Covid-19-related malware were sent via spam email to millions of people. In fact, for the first five months of 2020, 92% of all cyberthreats that took advantage of Covid-19 were spam or phishing emails. Data shows that Trend Micro™ Smart Protection Network™ blocked 16,393,564 pandemic-related threats and that Trend Micro Cloud App Security thwarted a total of 1,119,504 malware threats.
Despite the dip in BEC attacks in 2020, malicious actors are looking for bigger payouts from BEC — in Q1 of 2020, the average cost of a fraudulent wire transfer jumped to US$80,183.
Meanwhile, credential phishing attacks increased 14% from the previous year, totaling at 5,465,969. Notably, majority of the credential phishing attacks came from known links as opposed to unknown ones. In 2020, we also saw how malicious actors used unique techniques such as vishing and fake Microsoft 365 password expiration reports.
Security, during a pandemic and even beyond, should be a priority for all businesses, regardless of size. Now more than ever, enterprises and organizations rely heavily on cloud-based email services and tools to keep up with the high productivity demands of remote business operations. On top of having a company-wide security training and a checklist for all employees to keep their networks, devices, and connections secure, businesses need to have a multilayered approach to keep a wide variety of ever-evolving threats at bay.
Organizations should consider a comprehensive multilayered security solution such as Trend Micro Cloud App Security. It supplements the pre-existing security features in email and collaboration platforms like Microsoft 365 and Google Workspace (formerly known as G Suite) by using machine learning (ML) to analyze and detect any suspicious content in the message body and attachments of an email. It also acts as a second layer of protection after emails and files have passed through Microsoft 365 or Gmail’s built-in security.
Trend Micro Cloud App Security uses technologies such as sandbox malware analysis, document exploit detection, and file, email, and web reputation technologies to detect malware hidden in Microsoft 365 or PDF documents. It provides data loss prevention (DLP) and advanced malware protection for Box, Dropbox, Google Drive, SharePoint Online, OneDrive for Business, and Salesforce while also enabling consistent DLP policies across multiple cloud-based applications. It also offers seamless integration with an organization’s existing cloud setup, preserving full user and administrator functionality, providing direct cloud-to-cloud integration through vendor APIs, and minimizing the need for additional resources by assessing threat risks before sandbox malware analysis.
Trend Micro Cloud App Security stands on the cutting edge of email and software-as-a-service (SaaS) security, offering ML-powered features that combat two of the primary email-based threats: BEC and credential phishing. Writing Style DNA can help determine if an email is legitimate by using ML to check a user’s writing style based on past emails and then comparing suspicious emails against it. Computer vision, on the other hand, combines image analysis and ML to check branded elements, login forms, and other site content. It then pools this information with site reputation elements and optical character recognition (OCR) to check for fake and malicious sites — all while reducing instances of false positives to detect credential phishing email.
Trend Micro Cloud App Security also comes with the advanced and extended security capabilities of Trend Micro XDR, providing investigation, detection, and response across your endpoints, email, and servers.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering


 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One