Curbing the BEC Problem Using AI and Machine Learning

Business email compromise (BEC) scams are dangerous threats to businesses across the globe. With BEC present in over a hundred countries now, the Federal Bureau of Investigation (FBI) has reported a total of US$5.3 billion in global losses from over 40,000 incidents between 2013 and 2016. While BEC attempts continued to proliferate in 2017 with a 106 percent increase from the first half of the year to the second, cybercriminals are not just relying on its prevalence to produce lucrative payouts. Cybercriminals have become crafty that BEC scams no longer have to rely entirely on detectable malicious components. Although malware remains an option to launch attacks, cybercriminals are increasingly using phishing and social engineering to target individuals in the company who may become vulnerable to underhanded tactics.
Characteristics of BEC that make it hard to detect
Due to BEC’s evolving and treacherous nature, run-of-the-mill best practices and security solutions have become weak to withstand attacks. Undetected by traditional AV, socially-engineered BEC scams are quick and require relatively little reconnaissance to proceed with an attack as opposed to schemes that rely on planting keyloggers and remote access tools. Cybercriminals use the following deceptive strategies:
- The sense of urgency, a request for action, or a financial implication used in BEC schemes trick targets into falling
for the trap. For instance,a cybercriminal contacts either the employees and/or executives of the company and pose as either third-party suppliers, representatives of law firms or even chief executive officers (CEOs), manipulating the targeted employee/executive into secretly handling the transfer of funds. - Fake email is made to appear legitimate. Cybercriminals will play into the employee’s desire to be responsive to the executive being impersonated. The most targeted positions in the past few years were chief financial officers (CFO), finance controllers, finance managers, and finance directors, while the most spoofed high-level executives were CEOs, managing directors, and presidents.
- When a user’s account or mailbox is compromised, the attacker can use the compromised account to send internal phishing or BEC emails. Since the email is coming from a legitimate user’s mailbox, there won’t be anything suspicious
on the mail header or sender address.
Using advanced solutions to counter BEC
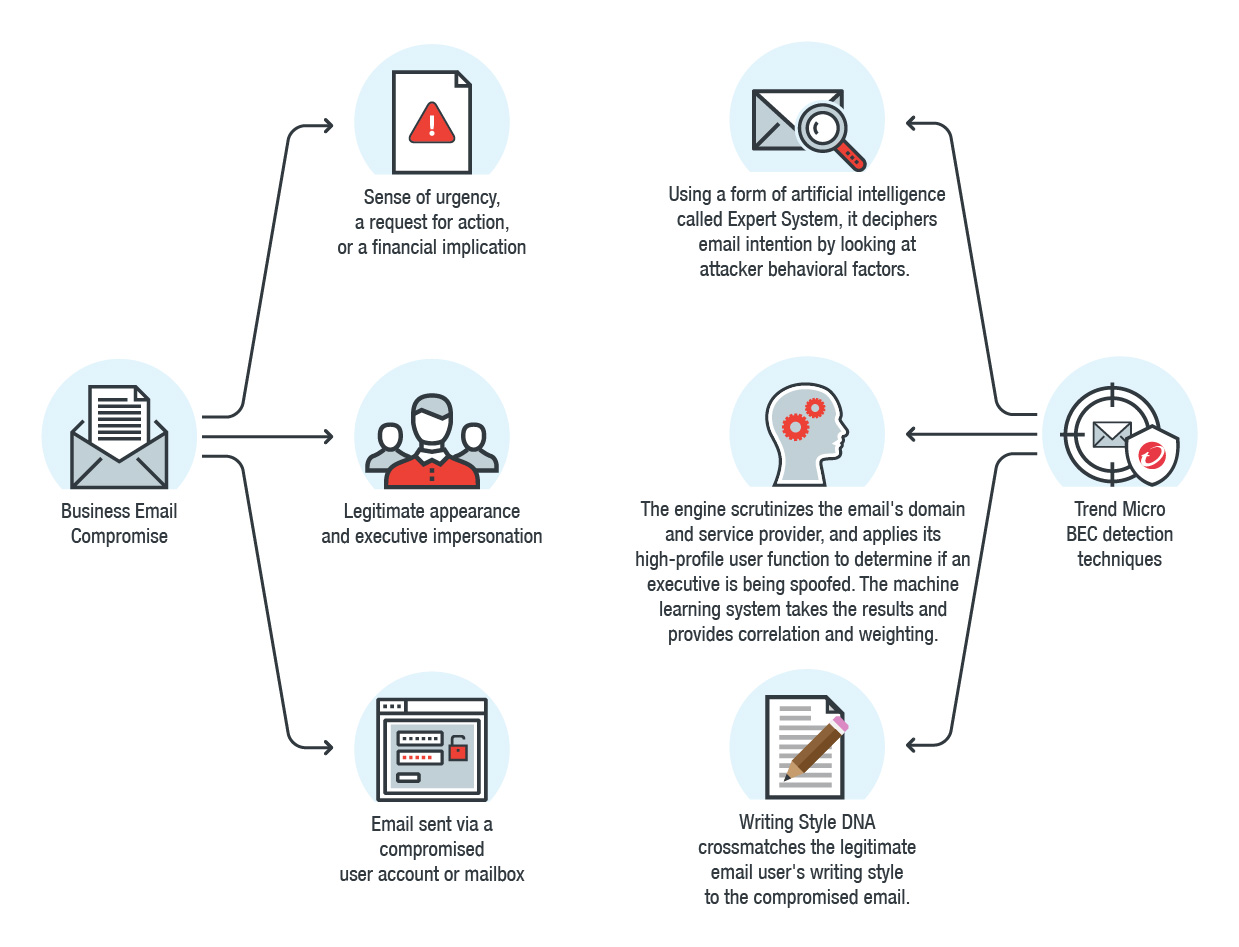
Figure 1. How Trend Micro’s BEC detection techniques expertly defend against BEC
Advanced security solutions are necessary to stop BEC attackers from successfully deploying the abovementioned tactics. BEC detection techniques featured in Trend Micro™ email security products use artificial intelligence (AI) and machine learning to defend against BEC. Trend Micro anti-BEC technology combines the knowledge of a security expert with a self-learning mathematical model to identify fake emails by looking at both behavioral factors and the intention of an email.
Trend Micro BEC detection techniques first mimic the decision-making process of a security researcher through a form of AI called Expert System. The engine will check if an email is coming from a dubious email provider, as well as the similarity of the sender’s domain to that of the target organization. It will also check if the sender is using a name of an executive at the recipient’s organization, among other factors. The engine’s “high-profile user” function applies additional scrutiny and correlation with commonly spoofed senders (such as executives at the target organization) and their real email addresses.
Expert System also has the capability to assess the content of an email to decipher its intention. Suspicious factors would include a sense of urgency, a request for action, or a financial implication. None of these factors are suspicious on their own, but they paint
The engine’s machine learning system takes the results given by the Expert System and uses a machine learning algorithm to provide correlation and weighting. It determines if the email is real, fake, or suspicious more precisely. The machine learning algorithm is based on millions of legitimate and fake emails and is constantly learning and improving.
Writing Style DNA supplements existing BEC protection techniques that use Expert System and machine learning to analyze email behavior (for example, using a free email service provider), email authorship (for example, checking the email sender’s writing style), and email intention (for example, payment or urgency). When an email is suspected of spoofing a high-profile user, the writing style is compared to this trained AI model and a warning is sent to the implied sender, the recipient, and the IT department.
A security mindset to combat BEC
Educating employees on how BEC scams work should also be a top priority for businesses. Workforce awareness is key in keeping enterprise systems and networks safe from cybercriminals. Some tips on how to stay safe from BEC scams:
- Carefully scrutinize all emails. Be wary of irregular emails sent by high-level executives, as they can be used to trick employees into acting with urgency. Review and verify emails requesting funds to determine if the requests are out of the ordinary.
- Raise employee awareness. While employees are a company’s biggest asset, they can also be its weakest link when it comes to security. Commit to training employees, review company policies, and develop good security habits. Trend Micro offers a free phishing simulation and user training service to help employees be aware.
- Verify any change in vendor payment location by establishing a secondary sign-off by company personnel.
- Verify requests. Confirm requests for fund transfers when using phone verification as part of two-factor authentication, and use known familiar numbers, not the details provided in email requests.
- Report any incident immediately to law enforcement or file a complaint with the IC3.
The set of BEC detection techniques used in Trend Micro email security products, when employed alongside workforce cybersecurity awareness, can be an effective defense against BEC scams, as well as other threats such as phishing and ransomware. Our advanced security technology is enhanced by artificial intelligence and machine learning, and it works best when it interoperates with other security layers. A multi-layered threat defense further ensures the privacy, security, and integrity of the gateways, endpoints, networks, servers, and other infrastructures that manage business processes.
Our Simply Security blog post talks more about the power of artificial intelligence in stopping these email-borne threats.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One