The Case for Making BYOD Safe
 View infographic: Making BYOD Safe
View infographic: Making BYOD Safe
The Bring Your Own Device phenomenon is a godsend for businesses of all sizes looking to save or redirect some resources to other avenues of their organization. After all, it does allow employees to bring their own personal devices to the workplace that they can use for their day-to-day tasks. The organization, on the other hand, enjoys the efficiency and productivity that these devices provide the workforce without having to pay for them.
While it seems like a win-win, there are also a number of potential risks to having these devices connect to the company network. Ultimately, organizations that run a BYOD network should recognize and address these issues, or else find themselves getting more than what they bargained for—and not in a good way.
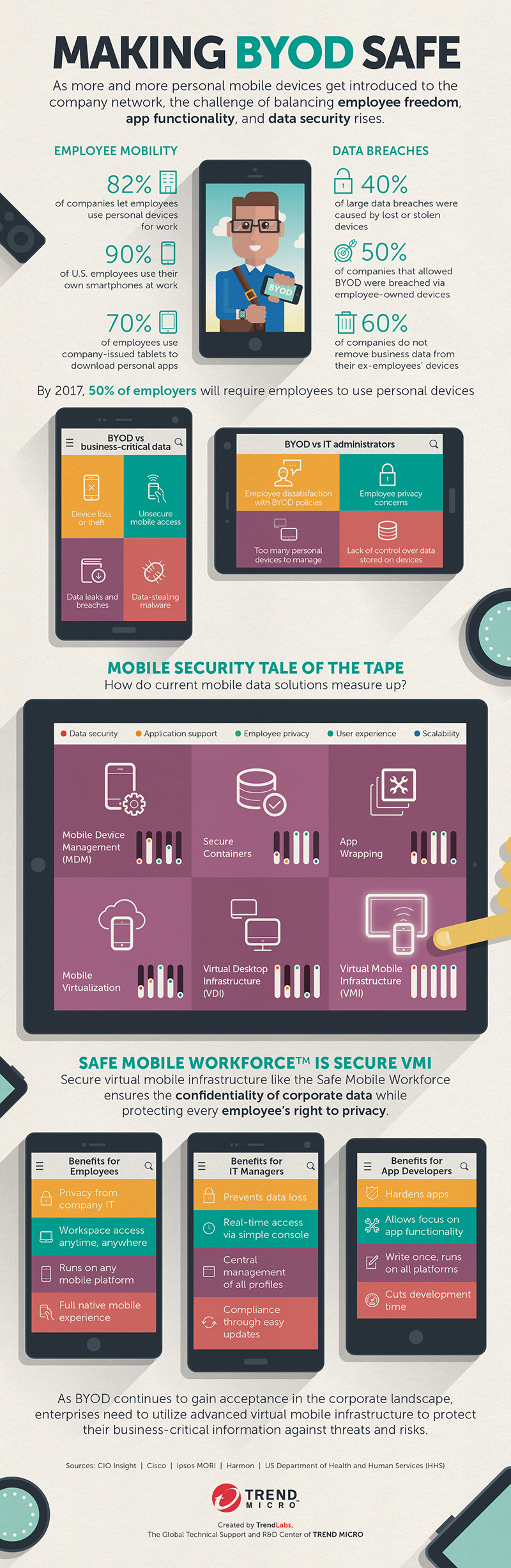
- Data Loss/Theft: One of the biggest risks in BYOD is the loss or theft of business-critical information. When employees use their personal device for work-related purposes, any work-related data stored in that device could be compromised if the device itself is lost and/or stolen. This could severely impact your business operations and finances, depending on the information lost. But that’s not the end of it, as a lost device could also set you up for a…
- Data Breach: Arguably the worst thing that can happen as a result of negligent BYOD practices. A data breach is what happens when a particularly malevolently-inclined individual gets hold of the stolen information and either publishes it online for everyone—and that includes your customers, investors and stakeholders—or sells it to the highest bidder. This is a net loss for any organization, both in terms of finances and in reputation.
- Network Intrusion: Negligent BYOD practices can also result in your office network being broken into. Depending on the type of information stolen in the scenarios mentioned above, attackers can use the stolen information to break through your network defenses and steal even more of your business-critical data. Once they’re inside, there is no stopping them from stealing anything from customer data to company secrets.
- Employee Distraction: It’s their personal device, and while they’re using it for work purposes, their non work-related apps will still be there for them to access. This could distract your employees from their work and therefore result in a loss of productivity.
These are only some of the other downsides of BYOD that a company could be beset with if they don’t adopt the practice with prudence and care. But don’t be fooled—these downsides, as potentially ruinous as they are—are also outweighed by the benefits, which you’ll see in full detail in the embedded Infographic Making BYOD Safe.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One